Copyrighted Material
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

List of NMAP Scripts Use with the Nmap –Script Option
List of NMAP Scripts Use with the nmap –script option Retrieves information from a listening acarsd daemon. Acarsd decodes ACARS (Aircraft Communication Addressing and Reporting System) data in real time. The information retrieved acarsd-info by this script includes the daemon version, API version, administrator e-mail address and listening frequency. Shows extra information about IPv6 addresses, such as address-info embedded MAC or IPv4 addresses when available. Performs password guessing against Apple Filing Protocol afp-brute (AFP). Attempts to get useful information about files from AFP afp-ls volumes. The output is intended to resemble the output of ls. Detects the Mac OS X AFP directory traversal vulnerability, afp-path-vuln CVE-2010-0533. Shows AFP server information. This information includes the server's hostname, IPv4 and IPv6 addresses, and hardware type afp-serverinfo (for example Macmini or MacBookPro). Shows AFP shares and ACLs. afp-showmount Retrieves the authentication scheme and realm of an AJP service ajp-auth (Apache JServ Protocol) that requires authentication. Performs brute force passwords auditing against the Apache JServ protocol. The Apache JServ Protocol is commonly used by ajp-brute web servers to communicate with back-end Java application server containers. Performs a HEAD or GET request against either the root directory or any optional directory of an Apache JServ Protocol ajp-headers server and returns the server response headers. Discovers which options are supported by the AJP (Apache JServ Protocol) server by sending an OPTIONS request and lists ajp-methods potentially risky methods. ajp-request Requests a URI over the Apache JServ Protocol and displays the result (or stores it in a file). -

Development Production Line the Short Story
Development Production Line The Short Story Jene Jasper Copyright © 2007-2018 freedumbytes.dev.net (Free Dumb Bytes) Published 3 July 2018 4.0-beta Edition While every precaution has been taken in the preparation of this installation manual, the publisher and author assume no responsibility for errors or omissions, or for damages resulting from the use of the information contained herein. This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License. To get an idea of the Development Production Line take a look at the following Application Integration overview and Maven vs SonarQube Quality Assurance reports comparison. 1. Operating System ......................................................................................................... 1 1.1. Windows ........................................................................................................... 1 1.1.1. Resources ................................................................................................ 1 1.1.2. Desktop .................................................................................................. 1 1.1.3. Explorer .................................................................................................. 1 1.1.4. Windows 7 Start Menu ................................................................................ 2 1.1.5. Task Manager replacement ........................................................................... 3 1.1.6. Resource Monitor ..................................................................................... -

Oracle Internet Application Server 8I
Oracle Internet Application Server 8i Migrating from Oracle Application Server Release 1.0 June, 2000 Part No. A83709-01 Oracle Internet Application Server Migrating from Oracle Application Server, Release 1.0 Part No. A83709-01 Copyright © 2000, Oracle Corporation. All rights reserved. The Programs (which include both the software and documentation) contain proprietary information of Oracle Corporation; they are provided under a license agreement containing restrictions on use and disclosure and are also protected by copyright, patent, and other intellectual and industrial property laws. Reverse engineering, disassembly, or decompilation of the Programs is prohibited. The information contained in this document is subject to change without notice. If you find any problems in the documentation, please report them to us in writing. Oracle Corporation does not warrant that this document is error free. Except as may be expressly permitted in your license agreement for these Programs, no part of these Programs may be reproduced or transmitted in any form or by any means, electronic or mechanical, for any purpose, without the express written permission of Oracle Corporation. If the Programs are delivered to the U.S. Government or anyone licensing or using the programs on behalf of the U.S. Government, the following notice is applicable: Restricted Rights Notice Programs delivered subject to the DOD FAR Supplement are "commercial computer software" and use, duplication, and disclosure of the Programs, including documentation, shall be subject to the licensing restrictions set forth in the applicable Oracle license agreement. Otherwise, Programs delivered subject to the Federal Acquisition Regulations are "restricted computer software" and use, duplication, and disclosure of the Programs shall be subject to the restrictions in FAR 52.227-19, Commercial Computer Software - Restricted Rights (June, 1987). -

Licensing Information User Manual Mysql Enterprise Monitor 3.4
Licensing Information User Manual MySQL Enterprise Monitor 3.4 Table of Contents Licensing Information .......................................................................................................................... 4 Licenses for Third-Party Components .................................................................................................. 5 Ant-Contrib ............................................................................................................................... 10 ANTLR 2 .................................................................................................................................. 11 ANTLR 3 .................................................................................................................................. 11 Apache Commons BeanUtils v1.6 ............................................................................................. 12 Apache Commons BeanUtils v1.7.0 and Later ........................................................................... 13 Apache Commons Chain .......................................................................................................... 13 Apache Commons Codec ......................................................................................................... 13 Apache Commons Collections .................................................................................................. 14 Apache Commons Daemon ...................................................................................................... 14 Apache -

Final-Thesis.Pdf (1.648Mb)
VYSOKÉ UČENÍ TECHNICKÉ V BRNĚ BRNO UNIVERSITY OF TECHNOLOGY FAKULTA INFORMAČNÍCH TECHNOLOGIÍ FACULTY OF INFORMATION TECHNOLOGY ÚSTAV INTELIGENTNÍCH SYSTÉMŮ DEPARTMENT OF INTELLIGENT SYSTEMS ZPŘÍSTUPNĚNÍ OBRAZU Z IP KAMER V PROHLÍŽEČI WEB BROWSER FOR IP CAMERAS BAKALÁŘSKÁ PRÁCE BACHELOR’S THESIS AUTOR PRÁCE PAVEL ČERNÝ AUTHOR VEDOUCÍ PRÁCE doc. Ing. FRANTIŠEK ZBOŘIL, Ph.D. SUPERVISOR BRNO 2020 Vysoké učení technické v Brně Fakulta informačních technologií Ústav inteligentních systémů (UITS) Akademický rok 2019/2020 Zadání bakalářské práce Student: Černý Pavel Program: Informační technologie Název: Zpřístupnění obrazu z IP kamer v prohlížeči Web Browser for IP Cameras Kategorie: Umělá inteligence Zadání: 1. Prozkoumejte způsob přenosu obrazu z IP kamer a možnosti přenosu a zobrazení obrazu (videa) do webových prohlížečů. Věnujte pozornost možnostem HTML5 (např. použití tagu <video>). Seznamte se s problematikou používaných kodeků. 2. Na základě průzkumu navrhněte systém, který bude umožňovat především zobrazit živý obraz z kamer, včetně jednoduchého administračního rozhraní (správa kamer a přístupových práv uživatelů). 3. Systém implementujte pomocí vhodných programovacích jazyků. Použijte volně dostupné knihovny a programy (licencované pod GNU GPL, Apache a podobně). Webové rozhraní nechť je funkční v aktuálních verzích nejrozšířenějších prohlížečů (Firefox, Chrome, MS Edge). 4. Zhodnoťte dosažený výsledek a navrhněte možnosti dalšího vývoje. Literatura: Russel, S., Norvig, P.: Artificial Intelligence, A Modern Approach, Pearson, 2009 Podrobné -

Hyperion System 9 Products
HYPERION® SYSTEM™ 9 RELEASE 9.2.0.3 CONFIGURING HYPERION® SYSTEM™ 9 IN SSL-ENABLED ENVIRONMENTS CONTENTS IN BRIEF About This Document .................................................. 2 Assumptions ......................................................... 2 Information Sources .................................................... 2 Identifying SSL Points for Hyperion System 9 Products .......................... 3 Common Activities ..................................................... 9 Deploying Hyperion System 9 Products for SSL ............................... 10 Shared Services ....................................................... 12 Analytic Administration Services .......................................... 15 Planning ........................................................... 16 Financial Management ................................................. 16 BI+ ............................................................... 18 Performance Scorecard ................................................. 28 P/N: DH98892030 About This Document This document describes how to deploy Hyperion® System™ 9 in Secure Sockets Layer (SSL)- enabled environments. SSL is a cryptographic protocol used to secure data exchange over the network. The procedures in this document are designed for users who intend to use SSL in their Web environments to secure communication with Hyperion System 9 products. Assumptions l You know how to SSL-enable the following: m Application servers: Apache Tomcat, BEA WebLogic, Oracle 10g, and IBM WebSphere m Web Servers: Apache, -

WSGI from Start to Finish
WSGI from Start to Finish EuroPython 2010. Gustavo Narea Who's speaking ● ¡Hola! ● Web Application Developer. ● Contributes to WSGI projects. Goals ● Explain what your framework does under- the-hood. ● More efficient troubleshooting. ● Integrate third party libraries and applications. ● Write framework-independent libraries and applications. ● Learn about existing WSGI-based software. Updates after the tutorial ● This presentation was modified to refer to working examples and fix errata. ● You probably downloaded this presentation with the examples. If not, go to gustavonarea.net/talks/ to get them. ● Read the instructions on how to install some of them. ● They are not essential to understand the presentation. The big picture 1.Introduction. 2.HTTP and WSGI. 3.WSGI applications. 4.WSGI middleware. 5.Testing and debugging. 6.Embedded Web applications. 7.Deployment. 8.Limitations. 9.Conclusion. Introduction What's WSGI? HTTP = HyperText Transfer Protocol WSGI = Web Server Gateway Interface Key facts about WSGI ● Python “Standard” (PEP-333). ● Created in 2003. ● Inspired by CGI. ● Officially supported by all the popular frameworks. ● Applications can run on virtually any HTTP server. Servers and gateways ● Server with Python embedded: ● Python-powered gateway: Requests and responses HTTP and WSGI HTTP requests and responses Response Request HTTP/1.1 200 OK Server: EP2010 Server GET /greeting HTTP/1.1 Content-Length: 12 Host: example.org Content-Type: text/plain User-Agent: EP2010 Client empty line Hello world! Request Response POST /login -

Aris Server Update Installation Guide
ARIS SERVER UPDATE INSTALLATION GUIDE VERSION 10.0 - SERVICE RELEASE 14 April 2021 SOFTWARE AG This document applies to ARIS Version 10.0 and to all subsequent releases. Specifications contained herein are subject to change and these changes will be reported in subsequent release notes or new editions. Copyright © 2010 - 2021 Software AG, Darmstadt, Germany and/or Software AG USA Inc., Reston, VA, USA, and/or its subsidiaries and/or its affiliates and/or their licensors. The name Software AG and all Software AG product names are either trademarks or registered trademarks of Software AG and/or Software AG USA Inc. and/or its subsidiaries and/or its affiliates and/or their licensors. Other company and product names mentioned herein may be trademarks of their respective owners. Detailed information on trademarks and patents owned by Software AG and/or its subsidiaries is located at https://softwareag.com/licenses. Use of this software is subject to adherence to Software AG's licensing conditions and terms. These terms are part of the product documentation, located at https://softwareag.com/licenses and/or in the root installation directory of the licensed product(s). This software may include portions of third-party products. For third-party copyright notices, license terms, additional rights or restrictions, please refer to "License Texts, Copyright Notices and Disclaimers of Third Party Products". For certain specific third-party license restrictions, please refer to section E of the Legal Notices available under "License Terms and Conditions for Use of Software AG Products / Copyright and Trademark Notices of Software AG Products". These documents are part of the product documentation, located at https://softwareag.com/licenses and/or in the root installation directory of the licensed product(s). -
(DIS) Installation Guide
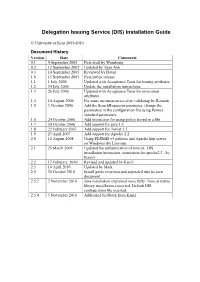
Delegation Issuing Service (DIS) Installation Guide © University of Kent 2005-2010 Document History Version Date Comments 0.1 9 September 2005 First draft by Wensheng 0.2 12 September 2005 Updated by Tuan Anh 0.3 14 September 2005 Reviewed by David 1.0 15 September 2005 First public release 1.1 1 July 2006 Updated with Acceptance Tests for issuing attributes 1.2 24 July 2006 Update the installation instructions 1.3 26 July 2006 Updated with Acceptance Tests for revocation attributes 1.4 14 August 2006 Fix some inconsistencies after validating by Romain 1.5 3 October 2006 Add the SearchRequestor parameter, change the parameters in the configuration file using Permis standard parameters. 1.6 24 October 2006 Add instruction for using policy stored in a file 1.7 24 October 2006 Add support for java 1.5 1.8 22 February 2007 Add support for Tomat 5.5 1.9 23 April 2007 Add support for Apache 2.2 2.0 12 August 2008 Using PERMIS v5 policies and Apache http server on Windows (by Linying) 2.1 25 March 2009 Updated the authentication of tomcat, DIS installation instruction, instruction for apache2.2 (by Kaniz) 2.2 17 February 2010 Revised and updated by Kaniz 2.3 16 April 2010 Updated by Mark 2.5 26 October 2010 Install guide rewritten and separated into its own document 2.5.2 2 November 2010 Java installation explained more fully. Tomcat native library installation corrected. Default DIS configuration file inserted. 2.5.4 5 November 2010 Addressed feedback from Kaniz System Requirements For the DIS Web Service A recent Java Runtime Environment (JRE). -

Apachecon 2004 November 13-17, 2004 Las Vegas Nevada
ApacheCon 2004 November 13-17, 2004 Las Vegas Nevada CLICK SESSION TITLE FOR PRESENTATION TUTORIALS MONDAY TUESDAY WEDNESDAY T01 Introduction to the Apache Web Server T02 mod_perl 2.0 by Example T03 Apache Portable Runtime 1.0 Tutorial T06 Mangling data with XSLT T07 Test-Driven Apache Module Development T08 Tapestry In Action T09 SpamAssassin Tutorial T10 Everything You Always Wanted to Know About XML Parsing T11 Scalable Internet Architectures T12 Apache Derby/Cloudscape: Embed This! T13 Struts: the good, the bad, and the ugly T14 Subversion Tutorial T15 Digging deep into XML Schema with Apache XMLBeans T16 PHP Security T17 Taming Apache Cocoon T18 Lucene in Action Search Next Help ApacheCon 2004 November 13-17, 2004 Las Vegas Nevada CLICK SESSION TITLE FOR PRESENTATION TUTORIALS MONDAY TUESDAY WEDNESDAY MO01 Behind the Scenes of the Apache Software Foundation MO02 Apache 2.0 on Windows MO03 The State of Apache Geronimo MO04 Advanced Topics in Module Design: Threadsafety and Portability MO05 The Incubator: Starting a Successful Apache Open Source Project MO06 Apache authentication MO07 Comparing Web Frameworks: Struts, Spring MVC, WebWork, Tapestry & JSF MO08 WebDAV and Apache MO09 New and upcoming features in SpamAssassin v3 MO10 What's so great about Apache 2.0? MO11 Embedding Tomcat 5 into Applications Servers MO12 Logging and Configuration - Demystifying the banes of App development MO13 Storing SpamAssassin User Data in SQL Databases MO14 Shoehorning Apache Onto Your Box: System Sizing Tips MO15 Highly available web sites with Tomcat -

Intro to Load-Balancing Tomcat with Httpd and Mod Jk
Intro to Load-Balancing Tomcat with httpd and mod_jk Christopher Schultz Chief Technology Officer Total Child Health, Inc. * Slides available on the Linux Foundation / ApacheCon2015 web site and at http://people.apache.org/~schultz/ApacheCon NA 2015/Load-balancing with mod_jk.odp Intro to Load-Balancing Tomcat with httpd and mod_jk ● Covering – Load balancing ● Not covering – Clustering* * See Mark's 3-part presentation(s) today starting at 10:00 in this room Tomcat ● Tomcat as a web server – Capable ● HTTP, HTTPS, WebSocket, NIO ● Virtual hosting, CGI, URL-rewriting ● Authentication (RDBMS, LDAP, file) ● Styled directory listings ● Arbitrary data filtering – Fast ● Static throughput can be comparable to httpd* * See Jean-Frederic's presentation today at 15:15 in this room Tomcat ● Tomcat as an application server – Java servlets, JSPs – Sky is the limit Image credit: Stan Shebs CC BY-SA 3.0 via Wikimedia Commons Tomcat ● Tomcat as an application server – Java servlets, JSPs – Sky is the limit* Image credit: Stan Shebs CC BY-SA 3.0 via Wikimedia Commons * Okay, heap size is the limit Scalability ● More memory Scalability ● More memory ● More deployed applications – without complex URLs Scalability ● More memory ● More deployed applications – without complex URLs ● Better fault-tolerance – fail-over Scalability ● More memory ● More deployed applications – without complex URLs ● Better fault-tolerance – fail-over ● Easier maintenance – bring-down a server without bringing down a service Scalability Load Balancing ● Client sees a single “service” ● “Server” is really an army of servers ● This army runs behind a façade: the load-balancer (lb) ● The load-balancer is also called a reverse proxy* * Because forward proxy was already taken Balancing versus Clustering ● Balancing is basic – Route incoming requests – Pushes bytes around ● Clustering* is complex – Relies on balancing as a building block – Configuration – Communication – Replication * See Mark's 3-part presentation(s) today starting at 10:00 in this room Reverse Proxying ● Necessary components 1. -

Abkürzungs-Liste ABKLEX
Abkürzungs-Liste ABKLEX (Informatik, Telekommunikation) W. Alex 1. Juli 2021 Karlsruhe Copyright W. Alex, Karlsruhe, 1994 – 2018. Die Liste darf unentgeltlich benutzt und weitergegeben werden. The list may be used or copied free of any charge. Original Point of Distribution: http://www.abklex.de/abklex/ An authorized Czechian version is published on: http://www.sochorek.cz/archiv/slovniky/abklex.htm Author’s Email address: [email protected] 2 Kapitel 1 Abkürzungen Gehen wir von 30 Zeichen aus, aus denen Abkürzungen gebildet werden, und nehmen wir eine größte Länge von 5 Zeichen an, so lassen sich 25.137.930 verschiedene Abkür- zungen bilden (Kombinationen mit Wiederholung und Berücksichtigung der Reihenfol- ge). Es folgt eine Auswahl von rund 16000 Abkürzungen aus den Bereichen Informatik und Telekommunikation. Die Abkürzungen werden hier durchgehend groß geschrieben, Akzente, Bindestriche und dergleichen wurden weggelassen. Einige Abkürzungen sind geschützte Namen; diese sind nicht gekennzeichnet. Die Liste beschreibt nur den Ge- brauch, sie legt nicht eine Definition fest. 100GE 100 GBit/s Ethernet 16CIF 16 times Common Intermediate Format (Picture Format) 16QAM 16-state Quadrature Amplitude Modulation 1GFC 1 Gigabaud Fiber Channel (2, 4, 8, 10, 20GFC) 1GL 1st Generation Language (Maschinencode) 1TBS One True Brace Style (C) 1TR6 (ISDN-Protokoll D-Kanal, national) 247 24/7: 24 hours per day, 7 days per week 2D 2-dimensional 2FA Zwei-Faktor-Authentifizierung 2GL 2nd Generation Language (Assembler) 2L8 Too Late (Slang) 2MS Strukturierte