Reverse Engineering the Huawei Health Android App
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

How Applications Are Run on Android ?
How applications are run on Android ? Jean-Loup Bogalho & Jérémy Lefaure [email protected] [email protected] Table of contents 1. Dalvik and ART 2. Executable files 3. Memory management 4. Compilation What is Dalvik ? ● Android’s Virtual Machine ● Designed to run on embedded systems ● Register-based (lower memory consumption) ● Run Dalvik Executable (.dex) files What is ART ? ● Android RunTime ● Dalvik’s successor ● ART Is Not a JVM ● Huge performance gain thanks to ahead-of-time (AOT) compilation ● Available in Android 4.4 What is ART ? Executable files Dalvik: .dex files ● Not the same bytecode as classical Java bytecode ● .class files are converted in .dex files at build time ● Optimized for minimal memory footprint Dalvik: .dex files Dalvik: application installation ● Verification: ○ bytecode check (illegal instructions, valid indices,...) ○ checksum on files ● Optimization: ○ method inlining ○ byte swapping and padding ○ static linking ART: OAT file ● Generated during installation (dex2oat) ● ELF format ● Classes metadata Memory management Zygote ● Daemon started at boot time ● Loads and initializes core libraries ● Forks to create new Dalvik instance ● Startup time of new VM is reduced ● Memory layouts are shared across processes Dalvik: memory management ● Memory is garbage collected ● Automatic management avoids programming errors ● Objects are not freed as soon as they become unused Dalvik: memory allocation ● Allocation profiling: ○ allocation count (succeeded or failed) ○ total allocated size (succeeded or failed) ● malloc -

Android (Operating System) 1 Android (Operating System)
Android (operating system) 1 Android (operating system) Android Home screen displayed by Samsung Nexus S with Google running Android 2.3 "Gingerbread" Company / developer Google Inc., Open Handset Alliance [1] Programmed in C (core), C++ (some third-party libraries), Java (UI) Working state Current [2] Source model Free and open source software (3.0 is currently in closed development) Initial release 21 October 2008 Latest stable release Tablets: [3] 3.0.1 (Honeycomb) Phones: [3] 2.3.3 (Gingerbread) / 24 February 2011 [4] Supported platforms ARM, MIPS, Power, x86 Kernel type Monolithic, modified Linux kernel Default user interface Graphical [5] License Apache 2.0, Linux kernel patches are under GPL v2 Official website [www.android.com www.android.com] Android is a software stack for mobile devices that includes an operating system, middleware and key applications.[6] [7] Google Inc. purchased the initial developer of the software, Android Inc., in 2005.[8] Android's mobile operating system is based on a modified version of the Linux kernel. Google and other members of the Open Handset Alliance collaborated on Android's development and release.[9] [10] The Android Open Source Project (AOSP) is tasked with the maintenance and further development of Android.[11] The Android operating system is the world's best-selling Smartphone platform.[12] [13] Android has a large community of developers writing applications ("apps") that extend the functionality of the devices. There are currently over 150,000 apps available for Android.[14] [15] Android Market is the online app store run by Google, though apps can also be downloaded from third-party sites. -

Prohibited Agreements with Huawei, ZTE Corp, Hytera, Hangzhou Hikvision, Dahua and Their Subsidiaries and Affiliates
Prohibited Agreements with Huawei, ZTE Corp, Hytera, Hangzhou Hikvision, Dahua and their Subsidiaries and Affiliates. Code of Federal Regulations (CFR), 2 CFR 200.216, prohibits agreements for certain telecommunications and video surveillance services or equipment from the following companies as a substantial or essential component of any system or as critical technology as part of any system. • Huawei Technologies Company; • ZTE Corporation; • Hytera Communications Corporation; • Hangzhou Hikvision Digital Technology Company; • Dahua Technology company; or • their subsidiaries or affiliates, Entering into agreements with these companies, their subsidiaries or affiliates (listed below) for telecommunications equipment and/or services is prohibited, as doing so could place the university at risk of losing federal grants and contracts. Identified subsidiaries/affiliates of Huawei Technologies Company Source: Business databases, Huawei Investment & Holding Co., Ltd., 2017 Annual Report • Amartus, SDN Software Technology and Team • Beijing Huawei Digital Technologies, Co. Ltd. • Caliopa NV • Centre for Integrated Photonics Ltd. • Chinasoft International Technology Services Ltd. • FutureWei Technologies, Inc. • HexaTier Ltd. • HiSilicon Optoelectronics Co., Ltd. • Huawei Device Co., Ltd. • Huawei Device (Dongguan) Co., Ltd. • Huawei Device (Hong Kong) Co., Ltd. • Huawei Enterprise USA, Inc. • Huawei Global Finance (UK) Ltd. • Huawei International Co. Ltd. • Huawei Machine Co., Ltd. • Huawei Marine • Huawei North America • Huawei Software Technologies, Co., Ltd. • Huawei Symantec Technologies Co., Ltd. • Huawei Tech Investment Co., Ltd. • Huawei Technical Service Co. Ltd. • Huawei Technologies Cooperative U.A. • Huawei Technologies Germany GmbH • Huawei Technologies Japan K.K. • Huawei Technologies South Africa Pty Ltd. • Huawei Technologies (Thailand) Co. • iSoftStone Technology Service Co., Ltd. • JV “Broadband Solutions” LLC • M4S N.V. • Proven Honor Capital Limited • PT Huawei Tech Investment • Shanghai Huawei Technologies Co., Ltd. -

K1 LEVEL QUESTIONS 17PMC640 ANDROID PROGRAMMING Unit:1
K1 LEVEL QUESTIONS 17PMC640 ANDROID PROGRAMMING Unit:1 1) Dalvik Virtual Machine (DVM) actually uses core features of A. Windows B. Mac C. Linux D. Contiki 2) A type of service provided by android that allows sharing and publishing of data to other applications is A. View System B. Content Providers C. Activity Manager D. Notifications Manager 3) Android library that provides access to UI pre-built elements such as buttons, lists, views etc. is A. android.text B. android.os C. android.view D. android.webkit 4) A type of service provided by android that shows messages and alerts to user is A. Content Providers B. View System C. Notifications Manager D. Activity Manager 5) A type of service provided by android that controls application lifespan and activity pile is A. Activity Manager B. View System C. Notifications Manager D. Content Providers 6) One of application component, that manages application's background services is called A. Activities B. Broadcast Receivers C. Services D. Content Providers 7) In android studio, callback that is called when activity interaction with user is started is A. onStart B. onStop C. onResume D. onDestroy 8) Tab that can be used to do any task that can be done from DOS window is A. TODO B. messages C. terminal D. comments 9) Broadcast that includes information about battery state, level, etc. is A. android.intent.action.BATTERY_CHANGED B. android.intent.action.BATTERY_LOW C. android.intent.action.BATTERY_OKAY D. android.intent.action.CALL_BUTTON 10) OHA stands for a) Open Host Application b) Open Handset -

Android Operating System
Software Engineering ISSN: 2229-4007 & ISSN: 2229-4015, Volume 3, Issue 1, 2012, pp.-10-13. Available online at http://www.bioinfo.in/contents.php?id=76 ANDROID OPERATING SYSTEM NIMODIA C. AND DESHMUKH H.R. Babasaheb Naik College of Engineering, Pusad, MS, India. *Corresponding Author: Email- [email protected], [email protected] Received: February 21, 2012; Accepted: March 15, 2012 Abstract- Android is a software stack for mobile devices that includes an operating system, middleware and key applications. Android, an open source mobile device platform based on the Linux operating system. It has application Framework,enhanced graphics, integrated web browser, relational database, media support, LibWebCore web browser, wide variety of connectivity and much more applications. Android relies on Linux version 2.6 for core system services such as security, memory management, process management, network stack, and driver model. Architecture of Android consist of Applications. Linux kernel, libraries, application framework, Android Runtime. All applications are written using the Java programming language. Android mobile phone platform is going to be more secure than Apple’s iPhone or any other device in the long run. Keywords- 3G, Dalvik Virtual Machine, EGPRS, LiMo, Open Handset Alliance, SQLite, WCDMA/HSUPA Citation: Nimodia C. and Deshmukh H.R. (2012) Android Operating System. Software Engineering, ISSN: 2229-4007 & ISSN: 2229-4015, Volume 3, Issue 1, pp.-10-13. Copyright: Copyright©2012 Nimodia C. and Deshmukh H.R. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited. -

Dalvik - Virtual Machine
Review Indian Journal of Engineering, Volume 1, Number 1, November 2012 REVIEW Indian Journal of 7765 – ngineering 7757 EISSN 2319 E – ISSN 2319 Dalvik - Virtual Machine Ashish Yadav J1, Abhishek Vats J2, Aman Nagpal J3, Avinash Yadav J4 1.Department of Computer Science, Dronacharya college of Engineering, Gurgaon, India, E-mail: [email protected] 2.Department of Computer Science, Dronacharya college of Engineering, Gurgaon, India, E-mail: [email protected] 3.Department of Computer Science, Dronacharya college of Engineering, Gurgaon, India, E-mail: [email protected] 4.Department of Computer Science, Dronacharya college of Engineering, Gurgaon, India, E-mail: [email protected] Received 26 September; accepted 19 October; published online 01 November; printed 16 November 2012 ABSTRACT Android is a software stack for mobile devices that contains an operating system, middleware and key applications. Android is a software platform and operating system for mobile devices based on the Linux operating system and developed by Google and the Open Handset Alliance. It allows developers to Write handle code in a Java-like language that utilizes Google-developed Java libraries, but does not support programs developed in native code. The presentation of the Android platform on 5 November 2007 was announced with the founding of the Open Handset Alliance, a consortium of 34 hardware, software and telecom companies devoted to advancing open standards for mobile devices. When released in 2008, most of the Android platform will be made obtainable under the Apache free-software and open-source license. Open Android provide the permission to access core mobile device functionality through standard API calls. -

Dexmedetomidine Mitigates LPS-Induced Acute Lung Injury in Rats Through HMGB1-Mediated Anti- Inflammatory and Antioxidant Mechanisms
Revista Argentina de Clínica Psicológica 2020, Vol. XXIX, N°4, 377-383 377 DOI: 10.24205/03276716.2020.837 Dexmedetomidine Mitigates LPS-Induced Acute Lung Injury in Rats Through HMGB1-Mediated Anti- Inflammatory and Antioxidant Mechanisms Ning Lva*,XiaoYun Lib ABSTRACT Purpose: To investigate the effect of dexmedetomidine on lipopolysaccharide (LPS)- induced acute lung injury in rats, and the underlying mechanism. Methods: Healthy male SD rats (n=54) were randomly divided into three groups: normal, model and dexmedetomidine groups, with 18 rats in each group. Rats in the model and dexmedetomidine groups were given LPS at a dose of 8 mg/kg, to establish a model of acute lung injury. Rats in the dexmedetomidine group were injected intraperitoneallywith dexmedetomidine at a dose of 50 μg/kg prior to establishment of the model, while rats in the normal group received intraperitoneal injection of normal saline in place of dexmedetomidine. Hematoxylin and eosin (H&E) staining was used to observe changes in lung tissue in each group.Changes in wet/dry weight ratio of lung tissue were compared among the groups. Enzyme-linked immunosorbent assay was used to determine the expressions of inflammation indices i.e. interleukin-6 (IL-6), tumor necrosis factor-α (TNF- α), and interleukin-1β (L-1β)] in lung tissue. Levels of MDA were measured with thiobarbituric acid method. Superoxide dismutase (SOD) activity was assayed through enzyme rate method, while nitric oxide was measured using nitrate reductase assay.The expression levels of high mobility group protein B1 (HMGB1), p-PI3K, p-Akt, p-IκB, p-NF- κB, and Toll-like receptor 4 (TLR4) in lung tissue were determined with Western blotting. -

TCL 科技集团股份有限公司 TCL Technology Group Corporation
TCL Technology Group Corporation Annual Report 2019 TCL 科技集团股份有限公司 TCL Technology Group Corporation ANNUAL REPORT 2019 31 March 2020 1 TCL Technology Group Corporation Annual Report 2019 Table of Contents Part I Important Notes, Table of Contents and Definitions .................................................. 8 Part II Corporate Information and Key Financial Information ........................................... 11 Part III Business Summary .........................................................................................................17 Part IV Directors’ Report .............................................................................................................22 Part V Significant Events ............................................................................................................51 Part VI Share Changes and Shareholder Information .........................................................84 Part VII Directors, Supervisors, Senior Management and Staff .......................................93 Part VIII Corporate Governance ..............................................................................................113 Part IX Corporate Bonds .......................................................................................................... 129 Part X Financial Report............................................................................................................. 138 2 TCL Technology Group Corporation Annual Report 2019 Achieve Global Leadership by Innovation and Efficiency Chairman’s -

TIMWE – Born Global Firm Case Study
CATÓLICA-LISBON, SCHOOL OF BUSINESS & ECONOMICS TIMWE – Born Global Firm Case Study Frederico José Castro Reis Marques December 2012 A Dissertation submitted in partial fulfillment of the requirements for the degree of MSc in Business Administration, at CLSBE – Católica-Lisbon, School of Business & Economics. ABSTRACT Title: TIMWE – Born Global Firm Author: Frederico José Castro Reis Marques TIMWE is the Portuguese based company chosen to illustrate and serve as background to support the creation of a teaching case in Strategy, exploring the internationalization of a real company and the challenges undertaken by the process of being a born global firm, followed by a Teaching Note that can be used as a tool to help solving the case. TIMWE is a Portuguese owned company, founded in 2002, that offers mobile monetization solutions and services (entertainment, marketing and money) to its global clients (brands, end-consumers, media groups, mobile carriers and governments), by leveraging its in- house developed intellectual proprietary technology, wide network of connections, mobile expertise and local presence. The main focus of the business strategy always has been B2O (business-to-operators), and since the beginning of its foundation the company aimed to build a global reach. In 2011, it had 26 offices, employing more than 300 people, operating in 75 countries across the 5 continents, as well as partnerships with over 280 mobile carriers spread all over the world giving access to 3 billion mobile subscribers. The case was prepared with the intent of providing useful insights about an IT services Portuguese company that managed to internationalize and operate in several countries, on top of giving a generic overview of the industry where it acts and is doing business. -
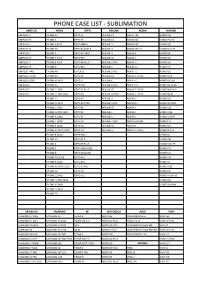
Qikink Product & Price List
PHONE CASE LIST - SUBLIMATION ONEPLUS APPLE OPPO REALME NOKIA HUAWEI ONEPLUS 3 IPHONE SE OPPO F3 REALME C1 NOKIA 730 HONOR 6X ONEPLUS 3T IPHONE 6 OPPO F5 REALME C2 NOKIA 640 HONOR 9 LITE ONEPLUS 5 IPHONE 6 PLUS OPPO FIND X REALME 3 NOKIA 540 HONOR Y9 ONEPLUS 5T IPHONE 6S OPPO REALME X REALME 3i NOKIA 7 PLUS HONOR 10 LITE ONEPLUS 6 IPHONE 7 OPPO F11 PRO REALME 5i NOKIA 8 HONOR 8C ONEPLUS 6T IPHONE 7 PLUS OPPO F15 REALME 5S NOKIA 6 HONOR 8X ONEPLUS 7 IPHONE 8 PLUS OPPO RENO 2F REALME 2 PRO NOKIA 3.1 HONOR 10 ONEPLUS 7T IPHONE X OPPO F11 REALME 3 NOKIA 2.1 HONOR 7C ONEPLUS 7PRO IPHONE XR OPPOF13 REALME 3 PRO NOKIA 7.1 HONOR 5C ONEPLUS 7T PRO IPHONE XS OPPO F1 REALME C3 NOKIA 3.1 PLUS HONOR P20 ONEPLUS NORD IPHONE XS MAX OPPO F7 REALME 6 NOKIA 5.1 HONOR 6PLUS ONEPLUS X IPHONE 11 OPPO A57 REALME 6 PRO NOKIA 7.2 HONOR PLAY 8A ONEPLUS 2 IPHONE 11 PRO OPPO F1 PLUS REALME X2 NOKIA 7.1 PLUS HONOR NOVA 3i ONEPLUS 1 IPHONE 11 PRO MAX OPPO F9 REALME X2 PRO NOKIA 6.1 PLUS HONOR PLAY IPHONE 12 OPPO A7 REALME 5 NOKIA 6.1 HONOR 8X IPHONE 12 MINI OPPO R17 PRO REALME 5 PRO NOKIA 8.1 HONOR 8X MAX IPHONE 12 PRO OPPO K1 REALME XT NOKIA 2 HONOR 20i IPHONE 12 PRO MAX OPPO F9 REALME 1 NOKIA 3 HONOR V20 IPHONE X LOGO OPPO F3 REALME X NOKIA 5 HONOR 6 PLAY IPHONE 7 LOGO OPPO A3 REALME 7 PRO NOKIA 6 (2018) HONOR 7X IPHONE 6 LOGO OPPO A5 REALME 5S NOKIA 8 HONOR 5X IPHONE XS MAX LOGO OPPO A9 REALME 5i NOKIA 2.1 PLUS HONOR 8 LITE IPHONE 8 LOGO OPPO R98 HONOR 8 IPHONE 5S OPPO F1 S HONOR 9N IPHONE 4 OPPO F3 PLUS HONOR 10 LITE IPHONE 5 OPPO A83 (2018) HONOR 7S IPHONE 8 -

Mobile Code Anti-Reversing Scheme Based on Bytecode Trapping in ART
sensors Article Mobile Code Anti-Reversing Scheme Based on Bytecode Trapping in ART Geonbae Na 1, Jongsu Lim 1, Sunjun Lee 2 and Jeong Hyun Yi 2,* 1 School of Computer Science and Engineering, Soongsil University, Seoul 06978, Korea; [email protected] (G.N.); [email protected] (J.L.) 2 School of Software, Soongsil University, Seoul 06978, Korea; [email protected] * Correspondence: [email protected] Received: 31 March 2019; Accepted: 6 June 2019; Published: 10 June 2019 Abstract: As interest in Internet of Things environments rapidly increases throughout the IT convergence field, compatibility with mobile devices must be provided to enable personalized services. The security of mobile platforms and applications is critical because security vulnerabilities of mobile devices can be spread to all things in these environments. Android, the leading open mobile platform, has long used the Dalvik virtual machine as its runtime system. However, it has recently been completely replaced by a new runtime system, namely Android Runtime (ART). The change from Android’s Dalvik to ART means that the existing Dalvik bytecode-based application execution structure has been changed to a machine code-based application execution structure. Consequently, a detailed understanding of ART, such as new file formats and execution switching methods between codes, is required from the viewpoint of application security. In this paper, we demonstrate that an existing Dalvik-based application vulnerability can be exploited as-is in ART. This is because existing Dalvik executable files coexist in the ART executable file, and these Dalvik bytecodes and compiled machine codes have one-to-one mapping relationships. -

Nacldroid: Native Code Isolation for Android Applications
NaClDroid: Native Code Isolation for Android Applications Elias Athanasopoulos1, Vasileios P. Kemerlis2, Georgios Portokalidis3, and Angelos D. Keromytis4 1 Vrije Universiteit Amsterdam, The Netherlands [email protected] 2 Brown University, Providence, RI, USA [email protected] 3 Stevens Institute of Technology, Hoboken, NJ, USA [email protected] 4 Columbia University, New York, NY, USA [email protected] Abstract. Android apps frequently incorporate third-party libraries that contain native code; this not only facilitates rapid application develop- ment and distribution, but also provides new ways to generate revenue. As a matter of fact, one in two apps in Google Play are linked with a library providing ad network services. However, linking applications with third-party code can have severe security implications: malicious libraries written in native code can exfiltrate sensitive information from a running app, or completely modify the execution runtime, since all native code is mapped inside the same address space with the execution environment, namely the Dalvik/ART VM. We propose NaClDroid, a framework that addresses these problems, while still allowing apps to include third-party code. NaClDroid prevents malicious native-code libraries from hijacking Android applications using Software Fault Isolation. More specifically, we place all native code in a Native Client sandbox that prevents uncon- strained reads, or writes, inside the process address space. NaClDroid has little overhead; for native code running inside the NaCl sandbox the slowdown is less than 10% on average. Keywords: SFI, NaCl, Android 1 Introduction Android is undoubtedly the most rapidly growing platform for mobile devices, with estimates predicting one billion Android-based smartphones shipping in 2017 [12].