Security Analysis of Android Factory Resets
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Technology That Brings Together All Things Mobile
NFC – The Technology That Brings Together All Things Mobile Philippe Benitez Wednesday, June 4th, 2014 NFC enables fast, secure, mobile contactless services… Card Emulation Mode Reader Mode P2P Mode … for both payment and non-payment services Hospitality – Hotel room keys Mass Transit – passes and limited use tickets Education – Student badge Airlines – Frequent flyer card and boarding passes Enterprise & Government– Employee badge Automotive – car sharing / car rental / fleet management Residential - Access Payment – secure mobile payments Events – Access to stadiums and large venues Loyalty and rewards – enhanced consumer experience 3 h h 1996 2001 2003 2005 2007 2014 2014 2007 2005 2003 2001 1996 previous experiences experiences previous We are benefiting from from benefiting are We Barriers to adoption are disappearing ! NFC Handsets have become mainstream ! Terminalization is being driven by ecosystem upgrades ! TSM Provisioning infrastructure has been deployed Barriers to adoption are disappearing ! NFC Handsets have become mainstream ! Terminalization is being driven by ecosystem upgrades ! TSM Provisioning infrastructure has been deployed 256 handset models now in market worldwide Gionee Elife E7 LG G Pro 2 Nokia Lumia 1020 Samsung Galaxy Note Sony Xperia P Acer E320 Liquid Express Google Nexus 10 LG G2 Nokia Lumia 1520 Samsung Galaxy Note 3 Sony Xperia S Acer Liquid Glow Google Nexus 5 LG Mach Nokia Lumia 2520 Samsung Galaxy Note II Sony Xperia Sola Adlink IMX-2000 Google Nexus 7 (2013) LG Optimus 3D Max Nokia Lumia 610 NFC Samsung -
Your HTC One® VX User Guide 2 Contents Contents
Your HTC One® VX User guide 2 Contents Contents Unboxing HTC One VX 10 Back cover 11 SIM card 13 Storage card 14 Charging the battery 15 Switching the power on or off 15 Setting up your phone Setting up HTC One VX for the first time 17 Home screen 17 Getting contacts into HTC One VX 18 Transferring contacts from your old phone through Bluetooth 19 Getting photos, videos, and music on or off HTC One VX 19 Getting to know your settings 20 Updating the HTC One VX software 20 Your first week with your new phone Features you'll enjoy on HTC One VX 22 Touch gestures 24 Motion gestures 27 Sleep mode 29 Unlocking the screen 30 Making your first call 30 Sending your first text message 31 The HTC Sense keyboard 31 Notifications 31 Copying and sharing text 34 Capturing the HTC One VX screen 35 Switching between recently opened apps 35 Can't find the Menu button? 35 Checking battery usage 36 Camera Camera basics 37 Taking a photo 38 Recording video 38 Keeping the camera on standby 39 Taking continuous camera shots 39 3 Contents Camera scenes 40 Improving portrait shots 40 Taking a group shot 40 Taking a panoramic photo 40 Using HDR 41 Recording videos in slow motion 41 Improving video stability 41 Changing camera and video settings 42 Personalizing Making HTC One VX truly yours 43 Personalizing HTC One VX with scenes 43 Changing your wallpaper 44 Applying a new skin 45 Personalizing your Home screen with widgets 45 Adding apps and other shortcuts on your Home screen 46 Rearranging or removing widgets and icons on your Home screen 47 Personalizing -

Trusense: Information Leakage from Trustzone
TruSense: Information Leakage from TrustZone Ning Zhang∗, Kun Suny, Deborah Shandsz Wenjing Lou∗z, Y. Thomas Hou∗ ∗Virginia Polytechnic Institute and State University, VA yGeorge Mason University, Fairfax, VA zNational Science Foundation, Arlington, VA Abstract—With the emergence of Internet of Things, mobile Unlike software exploitations that target vulnerabilities in devices are generating more network traffic than ever. TrustZone the system, side-channel attacks target information leakage of is a hardware-enabled trusted execution environment for ARM a physical implementation via its interactions with the execu- processors. While TrustZone is effective in providing the much- needed memory isolation, we observe that it is possible to derive tion environment. Side-channel information can be obtained secret information from secure world using the cache contention, from different types of physical features, such as power [10], due to its high-performance cache sharing design. electromagnetic wave [11], acoustic [12] and time [13], [14], In this work, we propose TruSense to study the timing-based [15]. Among these side channels, the cache-based timing cache side-channel information leakage of TrustZone. TruSense attack is one of the most important areas of research [14], can be launched from not only the normal world operating system but also a non-privileged user application. Without access [15], [16], [8], [17], [18]. to virtual-to-physical address mapping in user applications, we Processor cache is one of the basic components in mod- devise a novel method that uses the expected channel statistics ern memory architecture to bridge the gap between the fast to allocate memory for cache probing. -

Software Update for the MOTOROLA DEFY™+ Introduction This Is An
Software update for the MOTOROLA DEFY™+ Introduction This is an update to the 45.0.2310 software for the MOTOROLA DEFY+. This update includes several improvements to device performance. For optimal future device performance, we encourage you to download and install this latest software update. For more information on your MOTOROLA DEFY+, visit http://www.motorola.com/mydefyplus Who can use this release? MOTOROLA DEFY+ Owners Highlights After downloading and installing the software, you will notice the following improvements to your device: Summary of updates Improved connection stability Latest standard Google applications (GMS R9) Google security updates Better image viewer user interface Instructions for installing software For a successful installation, we recommend installing this update while the battery in your phone is at least 50% charged. Make sure you have an active SIM card installed in your phone. If you have received a notification message for this update: 1. Select "Download" 2. After the software is downloaded, select "Install now" 3. After the software is installed, your phone will re-start automatically 4. Your phone is now updated with 45.0.2310 software If you have not received a notification message for this update: 1. Select the Settings icon in the main menu 2. Select "About phone" 3. Select "System updates" 4. Select "Download" 5. After the software is downloaded, select "Install" 6. After the software is installed, your phone will re-start automatically 7. Your phone is now updated with 45.0.2310 software If you have difficulty with this update, visit http://www.motorola.com/mydefyplus Additional information Certain features, services and applications are network-dependent and may not be available in all areas; additional terms, conditions and/or charges may apply. -
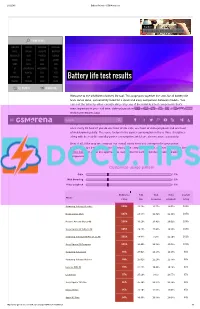
Battery Life Test Results HUAWEI TOSHIBA INTEX PLUM
2/12/2015 Battery life tests GSMArena.com Starborn SAMSUNG GALAXY S6 EDGE+ REVIEW PHONE FINDER SAMSUNG LENOVO VODAFONE VERYKOOL APPLE XIAOMI GIGABYTE MAXWEST MICROSOFT ACER PANTECH CELKON NOKIA ASUS XOLO GIONEE SONY OPPO LAVA VIVO LG BLACKBERRY MICROMAX NIU HTC ALCATEL BLU YEZZ MOTOROLA ZTE SPICE PARLA Battery life test results HUAWEI TOSHIBA INTEX PLUM ALL BRANDS RUMOR MILL Welcome to the GSMArena battery life tool. This page puts together the stats for all battery life tests we've done, conveniently listed for a quick and easy comparison between models. You can sort the table by either overall rating or by any of the individual test components that's most important to you call time, video playback or web browsing.TIP US 828K 100K You can find all about our84K 137K RSS LOG IN SIGN UP testing procedures here. SearchOur overall rating gives you an idea of how much battery backup you can get on a single charge. An overall rating of 40h means that you'll need to fully charge the device in question once every 40 hours if you do one hour of 3G calls, one hour of video playback and one hour of web browsing daily. The score factors in the power consumption in these three disciplines along with the reallife standby power consumption, which we also measure separately. Best of all, if the way we compute our overall rating does not correspond to your usage pattern, you are free to adjust the different usage components to get a closer match. Use the sliders below to adjust the approximate usage time for each of the three battery draining components. -

Response Data 910 14
Count of Type Desc. Total [40 (DUMMY) DISPLAY PHONES] 1 [BLACKBERRY] 2 [CHARGER] 1 [COVERS] 1 [FLIPTOP PHONE] 1 [HC1] 1 [HDCI M8 MOBILE PHONE] 1 [HUAWEI] 1 [I PHONE 4] 2 [I PHONE 5] 2 [I PHONE 5C] 1 [I PHONE 5S] 1 [I PHONE] 1 [IPHONE 5 WHITE IN COLOUR] 1 [IPHONE 5S] 1 [IPHONE 6] 1 [IPHONE CHARGER] 2 [IPHONE CHARGERS] 1 [IPHONE PHONE CHARGER] 1 [IPHONE] 2 [MOBILE PHONE AND CHARGED] 1 [MOBILE PHONE BATTERY] 1 [MOBILE PHONE CASE] 1 [MOBILE PHONE FOR SENIOR] 1 [MOBILE PHONE] 16 [MOBILE TELEPHONE - UNKNOWN DETAILS] 1 [MOBILE TELEPHONE] 4 [MOTOROLA] 1 [NOKIA LUMINA 530 MOBILE PHONE] 1 [NOKIA MOBILE] 1 [PHONE CHARGER] 1 [PHONE SIM CARD] 1 [SAMSUNG GALAXY S3 MINI] 1 [SAMSUNG] 1 [SIM CARD] 2 [SMART PHONE] 1 [SONY XPERIA Z1] 1 [SONY XPERIA Z2] 1 [TABLET] 1 [TELEPHONE CABLE] 1 [TESCO MOBILE PHONE] 1 [TESCO] 1 [UNKNOWN MAKE OF MOBILE PHONE] 1 [WORKS AND PERSONAL] 1 1PHONE 4S 1 3 [3 SIM CARD] 1 3G 1 4 [I PHONE] 1 4S 1 ACCESSORIES [CHARGER AND PHONE COVER] 1 ACER 2 ACER LIQUID 1 ACER LIQUID 3 1 ACER LIQUID 4Z [MOBILE TELEPHONE] 1 ACER LIQUID E 1 ACER LIQUID E2 1 ACER LIQUID E3 1 ACTEL [MOBILE PHONE] 1 ALCATEL 6 ALCATEL [MOBILE PHONE] 3 ALCATEL ITOUCH [ALCATEL ITOUCH] 1 ALCATEL ONE 232 1 ALCATEL ONE TOUCH 6 ALCATEL ONE TOUCH [TRIBE 30GB] 1 ALCATEL ONE TOUCH TRIBE 3040 1 ALCATELL 1 ANDROID [TABLET] 1 APHONE 5 1 APLE IPHONE 5C 1 APLLE I PHONE 5S 2 APLLE IPHONE 4 1 APPL I PHONE 4 1 APPLE 11 APPLE [I PHONE] 1 APPLE [IPHONE] 1 APPLE [MOBILE PHONE CHARGER] 1 APPLE 1 PHONE 4 1 APPLE 1 PHONE 5 1 APPLE 1 PHONE 5 [I PHONE] 1 APPLE 3GS [3GS] 1 APPLE 4 3 APPLE 4 -

Electronic 3D Models Catalogue (On July 26, 2019)
Electronic 3D models Catalogue (on July 26, 2019) Acer 001 Acer Iconia Tab A510 002 Acer Liquid Z5 003 Acer Liquid S2 Red 004 Acer Liquid S2 Black 005 Acer Iconia Tab A3 White 006 Acer Iconia Tab A1-810 White 007 Acer Iconia W4 008 Acer Liquid E3 Black 009 Acer Liquid E3 Silver 010 Acer Iconia B1-720 Iron Gray 011 Acer Iconia B1-720 Red 012 Acer Iconia B1-720 White 013 Acer Liquid Z3 Rock Black 014 Acer Liquid Z3 Classic White 015 Acer Iconia One 7 B1-730 Black 016 Acer Iconia One 7 B1-730 Red 017 Acer Iconia One 7 B1-730 Yellow 018 Acer Iconia One 7 B1-730 Green 019 Acer Iconia One 7 B1-730 Pink 020 Acer Iconia One 7 B1-730 Orange 021 Acer Iconia One 7 B1-730 Purple 022 Acer Iconia One 7 B1-730 White 023 Acer Iconia One 7 B1-730 Blue 024 Acer Iconia One 7 B1-730 Cyan 025 Acer Aspire Switch 10 026 Acer Iconia Tab A1-810 Red 027 Acer Iconia Tab A1-810 Black 028 Acer Iconia A1-830 White 029 Acer Liquid Z4 White 030 Acer Liquid Z4 Black 031 Acer Liquid Z200 Essential White 032 Acer Liquid Z200 Titanium Black 033 Acer Liquid Z200 Fragrant Pink 034 Acer Liquid Z200 Sky Blue 035 Acer Liquid Z200 Sunshine Yellow 036 Acer Liquid Jade Black 037 Acer Liquid Jade Green 038 Acer Liquid Jade White 039 Acer Liquid Z500 Sandy Silver 040 Acer Liquid Z500 Aquamarine Green 041 Acer Liquid Z500 Titanium Black 042 Acer Iconia Tab 7 (A1-713) 043 Acer Iconia Tab 7 (A1-713HD) 044 Acer Liquid E700 Burgundy Red 045 Acer Liquid E700 Titan Black 046 Acer Iconia Tab 8 047 Acer Liquid X1 Graphite Black 048 Acer Liquid X1 Wine Red 049 Acer Iconia Tab 8 W 050 Acer -
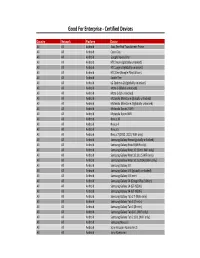
MMS Copy of Supported Devices
Good For Enterprise ‐ Certified Devices Country Network Platform Device All All Android Asus Eee Pad Transformer Prime All All Android Cisco Cius All All Android Google Nexus One All All Android HTC Desire (globally unlocked) All All Android HTC Legend (globally unlocked) All All Android HTC One (Google Play Edition) All All Android Kindle Fire All All Android LG Optimus 2X (globally unlocked) All All Android Moto G (Global unlocked) All All Android Moto G (US unlocked) All All Android Motorola Milestone (globally unlocked) All All Android Motorola Milestone 2 (globally unlocked) All All Android Motorola Xoom 2 WiFi All All Android Motorola Xoom WiFi All All Android Nexus 10 All All Android Nexus 4 All All Android Nexus 5 All All Android Nexus 7 (2012, 2013, WiFi only) All All Android Samsung Galaxy Nexus (globally unlocked) All All Android Samsung Galaxy Note 8 (WiFi only) All All Android Samsung Galaxy Note 10.1 (Intl. WiFi only) All All Android Samsung Galaxy Note 10.1 (U.S WiFi only) All All Android Samsung Galaxy Note 10.1 (2014) (WiFi only) All All Android Samsung Galaxy S II All All Android Samsung Galaxy S III (globally unlocked) All All Android Samsung Galaxy S III mini All All Android Samsung Galaxy S4 (Google Play Edition) All All Android Samsung Galaxy S4 (GT‐I9500) All All Android Samsung Galaxy S4 (GT‐I9505) All All Android Samsung Galaxy Tab 2 7 (WiFi only) All All Android Samsung Galaxy Tab 3 (7‐inch) All All Android Samsung Galaxy Tab 3 (8‐inch) All All Android Samsung Galaxy Tab 10.1 (WiFi only) All All Android Samsung -

Udynamo Compatibility List
uDynamo Compatibility List Reader Manuf. Device Name Alt. Model Info Model Info OS OS Version Carrier Date Added Date Tested Type iDynamo 5 Apple iPad Air 2 Lightning N/A iOS N/A N/A Tablet iDynamo 5 Apple iPad Air* Lightning N/A iOS N/A N/A Tablet iDynamo 5 Apple iPad with Retina Display* Lightning N/A iOS N/A N/A Tablet iDynamo 5 Apple iPad mini 3 Lightning N/A iOS N/A N/A Tablet iDynamo 5 Apple iPad mini 2 Lightning N/A iOS N/A N/A Tablet iDynamo 5 Apple iPad mini* Lightning N/A iOS N/A N/A Tablet iDynamo 5 Apple iPhone 5c* Lightning N/A iOS N/A N/A Phone iDynamo 5 Apple iPhone 5s* Lightning N/A iOS N/A N/A Phone iDynamo 5 Apple iPhone 5* Lightning N/A iOS N/A N/A Phone iDynamo 5 Apple iPod touch (5th* generation) Lightning N/A iOS N/A N/A iPod iDynamo 5 Apple iPhone 6* Lightning N/A iOS N/A N/A Phone iDynamo 5 Apple iPhone 6 Plus* Lightning N/A iOS N/A N/A Phone iDynamo Apple iPad (3rd generation) 30 PIN N/A iOS N/A N/A Tablet iDynamo Apple iPad 2 30 PIN N/A iOS N/A N/A Tablet iDynamo Apple iPad 30 PIN N/A iOS N/A N/A Tablet iDynamo Apple iPhone 4s 30 PIN N/A iOS N/A N/A Phone iDynamo Apple iPhone 4 30 PIN N/A iOS N/A N/A Phone iDynamo Apple iPhone 3GS 30 PIN N/A iOS N/A N/A Phone iDynamo Apple iPod touch (3rd and 4th generation) 30 PIN N/A iOS N/A N/A iPod uDynamo Acer liquid MT liquid MT Android 2.3.6 101.18 1/24/14 1/24/14 uDynamo Alcatel Alcatel OneTouch Fierce 7024W Android 4.2.2 101.18 3/6/14 3/6/14 uDynamo ALCATEL Megane ALCATEL ONE TOUCH 5020T Android 4.1.2 101.18 8/10/15 8/10/15 uDynamo ALCATEL ALCATEL ONE TOUCH IDOL X ALCATEL -
Winnovative HTML to PDF Converter for .NET
Convert iTunes Movies to Android Tablets &Phones TunesKit for Mac For Windows Buy Resource Tutorial Support How to Convert iTunes Movies to Android Phones and Tablets Posted by Andy Miller on August 22, 2014 11:05:35 AM. iTunes as the world's biggest digital content store, also attracts many android fans to buy or rent movies, songs or iBooks here. However, the problems come up when they realized the DRM protection existing. All Apple movies are copy protected by Fairplay DRM protection. The consumers are not allowed to transfer their purchased or rented movies to any Non‐apple devices, of course including the Android phones and tablets. What to do if the android fans want to watch the iTunes movies to their Samsung Galaxy S5 or Galaxy Tab/Note, orHTC one M8, or even Amazon Kindle Fire? You know all these Android devices' screen is larger than iPhone. Crack iTunes DRM and Convert iTunes Movies to Android Devices To convert and transfer the iTunes purchased or rented movies to our android phones or tablets, we have to remove the DRM from iTunes movies at first. TunesKit iTunes DRM Media Converter is a great choice to help you accomplish your task. With TunesKit DRM Media Converter, we can easily get rid of the Fairplay DRM protection from both iTunes purchased and rented movies/TV shows. It converts iTunes DRMed M4V to common MP4 format which can be supported by any android phones and tablets well. The important reason we recommend it is that it can do this work very fast, nearly 20x faster than other similar application. -

Phone Compatibility
Phone Compatibility • Compatible with iPhone models 4S and above using iOS versions 7 or higher. Last Updated: February 14, 2017 • Compatible with phone models using Android versions 4.1 (Jelly Bean) or higher, and that have the following four sensors: Accelerometer, Gyroscope, Magnetometer, GPS/Location Services. • Phone compatibility information is provided by phone manufacturers and third-party sources. While every attempt is made to ensure the accuracy of this information, this list should only be used as a guide. As phones are consistently introduced to market, this list may not be all inclusive and will be updated as new information is received. Please check your phone for the required sensors and operating system. Brand Phone Compatible Non-Compatible Acer Acer Iconia Talk S • Acer Acer Jade Primo • Acer Acer Liquid E3 • Acer Acer Liquid E600 • Acer Acer Liquid E700 • Acer Acer Liquid Jade • Acer Acer Liquid Jade 2 • Acer Acer Liquid Jade Primo • Acer Acer Liquid Jade S • Acer Acer Liquid Jade Z • Acer Acer Liquid M220 • Acer Acer Liquid S1 • Acer Acer Liquid S2 • Acer Acer Liquid X1 • Acer Acer Liquid X2 • Acer Acer Liquid Z200 • Acer Acer Liquid Z220 • Acer Acer Liquid Z3 • Acer Acer Liquid Z4 • Acer Acer Liquid Z410 • Acer Acer Liquid Z5 • Acer Acer Liquid Z500 • Acer Acer Liquid Z520 • Acer Acer Liquid Z6 • Acer Acer Liquid Z6 Plus • Acer Acer Liquid Zest • Acer Acer Liquid Zest Plus • Acer Acer Predator 8 • Alcatel Alcatel Fierce • Alcatel Alcatel Fierce 4 • Alcatel Alcatel Flash Plus 2 • Alcatel Alcatel Go Play • Alcatel Alcatel Idol 4 • Alcatel Alcatel Idol 4s • Alcatel Alcatel One Touch Fire C • Alcatel Alcatel One Touch Fire E • Alcatel Alcatel One Touch Fire S • 1 Phone Compatibility • Compatible with iPhone models 4S and above using iOS versions 7 or higher. -

130 Demystifying Arm Trustzone: a Comprehensive Survey
Demystifying Arm TrustZone: A Comprehensive Survey SANDRO PINTO, Centro Algoritmi, Universidade do Minho NUNO SANTOS, INESC-ID, Instituto Superior Técnico, Universidade de Lisboa The world is undergoing an unprecedented technological transformation, evolving into a state where ubiq- uitous Internet-enabled “things” will be able to generate and share large amounts of security- and privacy- sensitive data. To cope with the security threats that are thus foreseeable, system designers can find in Arm TrustZone hardware technology a most valuable resource. TrustZone is a System-on-Chip and CPU system- wide security solution, available on today’s Arm application processors and present in the new generation Arm microcontrollers, which are expected to dominate the market of smart “things.” Although this technol- ogy has remained relatively underground since its inception in 2004, over the past years, numerous initiatives have significantly advanced the state of the art involving Arm TrustZone. Motivated by this revival ofinter- est, this paper presents an in-depth study of TrustZone technology. We provide a comprehensive survey of relevant work from academia and industry, presenting existing systems into two main areas, namely, Trusted Execution Environments and hardware-assisted virtualization. Furthermore, we analyze the most relevant weaknesses of existing systems and propose new research directions within the realm of tiniest devices and the Internet of Things, which we believe to have potential to yield high-impact contributions in the future. CCS Concepts: • Computer systems organization → Embedded and cyber-physical systems;•Secu- rity and privacy → Systems security; Security in hardware; Software and application security; Additional Key Words and Phrases: TrustZone, security, virtualization, TEE, survey, Arm ACM Reference format: Sandro Pinto and Nuno Santos.