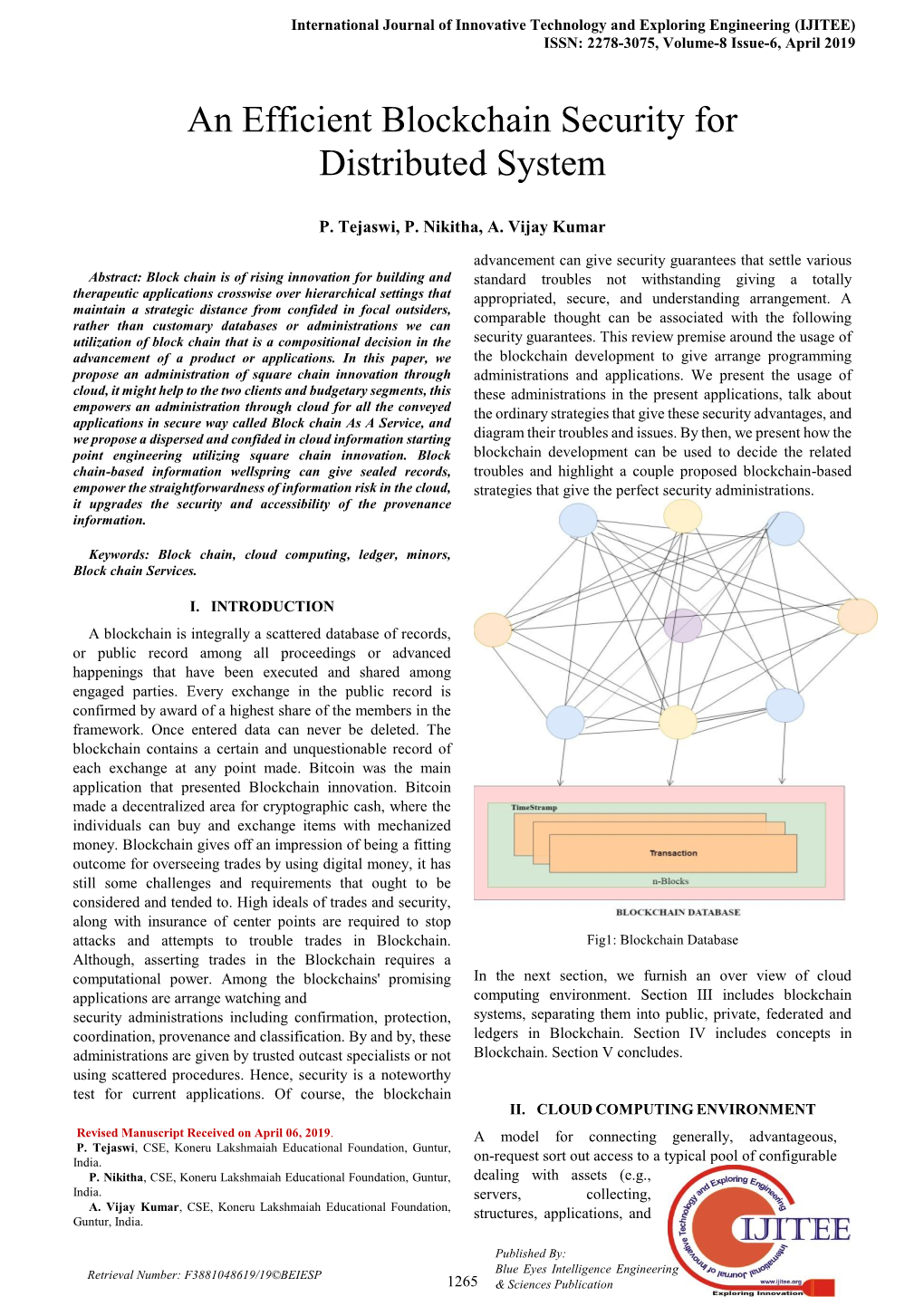
An Efficient Blockchain Security for Distributed System
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Using Blockchain Technology to Secure the Internet of Things
Using Blockchain Technology to Secure the Internet of Things Presented by the Blockchain/ Distributed Ledger Working Group © 2018 Cloud Security Alliance – All Rights Reserved. You may download, store, display on your computer, view, print, and link to Using Blockchain Technology to Secure the Internet of Things subject to the following: (a) the Document may be used solely for your personal, informational, non- commercial use; (b) the Report may not be modified or altered in any way; (c) the Document may not be redistributed; and (d) the trademark, copyright or other notices may not be removed. You may quote portions of the Document as permitted by the Fair Use provisions of the United States Copyright Act, provided that you attribute the portions to the Using Blockchain Technology to Secure the Internet of Things paper. Blockchain/Distributed Ledger Technology Working Group | Using Blockchain Technology to Secure the Internet of Things 2 © Copyright 2018, Cloud Security Alliance. All rights reserved. ABOUT CSA The Cloud Security Alliance is a not-for-profit organization with a mission to promote the use of best practices for providing security assurance within Cloud Computing, and to provide education on the uses of Cloud Computing to help secure all other forms of computing. The Cloud Security Alliance is led by a broad coalition of industry practitioners, corporations, associations and other key stakeholders. For further information, visit us at www.cloudsecurityalliance.org and follow us on Twitter @cloudsa. Blockchain/Distributed Ledger Technology Working Group | Using Blockchain Technology to Secure the Internet of Things 3 © Copyright 2018, Cloud Security Alliance. All rights reserved. -

Models to Evaluate Service Provisioning Over Cloud
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Archives of the Faculty of Veterinary Medicine UFRGS Revista de Informatica´ Teorica´ e Aplicada - RITA - ISSN 2175-2745 Vol. 26, Num. 3 (2019) 65-74 RESEARCH ARTICLE Models to evaluate service Provisioning over Cloud Computing Environments - A Blockchain-As-A-Service case study Modelos para o provimento de Servic¸os em Ambientes de Computac¸ao˜ em Nuvem - Um estudo de caso aplicado a Blockchain como Servic¸o Carlos Melo1*, Jamilson Dantas2, Paulo Pereira3, Ronierison Maciel4, Paulo Maciel5 Abstract: The strictness of the Service Level Agreements (SLAs) is mainly due to a set of constraints related to performance and dependability attributes, such as availability. This paper shows that system’s availability values may be improved by deploying services over a private environment, which may obtain better availability values with improved management, security, and control. However, how much a company needs to afford to keep this improved availability? As an additional activity, this paper compares the obtained availability values with the infrastructure deployment expenses and establishes a cost × benefit relationship. As for the system’s evaluation technique, we choose modeling; while for the service used to demonstrate the models’ feasibility, the blockchain-as-a-service was the selected one. This paper proposes and evaluate four different infrastructures hosting blockchains: (i) baseline; (ii) double redundant; (iii) triple redundant, and (iv) hyper-converged. The obtained results pointed out that the hyper-converged architecture had an advantage over a full triple redundant environment regarding availability and deployment cost. -

A Scoping Review of Integrated Blockchain-Cloud (Bcc) Architecture for Healthcare: Applications, Challenges and Solutions
sensors Review A Scoping Review of Integrated Blockchain-Cloud (BcC) Architecture for Healthcare: Applications, Challenges and Solutions Leila Ismail 1,2,∗ , Huned Materwala 1,2 and Alain Hennebelle 3 1 Intelligent Distributed Computing and Systems Research Laboratory, Department of Computer Science and Software Engineering, College of Information Technology, United Arab Emirates University, Al Ain, Abu Dhabi 15551, United Arab Emirates; [email protected] 2 National Water and Energy Center, United Arab Emirates University, Al Ain, Abu Dhabi 15551, United Arab Emirates 3 Independent Researcher, Al Ain, Abu Dhabi 15551, United Arab Emirates; [email protected] * Correspondence: [email protected] Abstract: Blockchain is a disruptive technology for shaping the next era of a healthcare system striving for efficient and effective patient care. This is thanks to its peer-to-peer, secure, and transparent characteristics. On the other hand, cloud computing made its way into the healthcare system thanks to its elasticity and cost-efficiency nature. However, cloud-based systems fail to provide a secured and private patient-centric cohesive view to multiple healthcare stakeholders. In this situation, blockchain provides solutions to address security and privacy concerns of the cloud because of its decentralization feature combined with data security and privacy, while cloud provides solutions to the blockchain scalability and efficiency challenges. Therefore a novel paradigm of blockchain-cloud integration (BcC) emerges for the domain of healthcare. In this paper, we provide an in-depth Citation: Ismail, L.; Materwala, H.; analysis of the BcC integration for the healthcare system to give the readers the motivations behind Hennebelle, A. -

A Centralized Ledger Database for Universal Audit and Verification
LedgerDB: A Centralized Ledger Database for Universal Audit and Verification Xinying Yangy, Yuan Zhangy, Sheng Wangx, Benquan Yuy, Feifei Lix, Yize Liy, Wenyuan Yany yAnt Financial Services Group xAlibaba Group fxinying.yang,yuenzhang.zy,sh.wang,benquan.ybq,lifeifei,yize.lyz,[email protected] ABSTRACT certain consensus protocol (e.g., PoW [32], PBFT [14], Hon- The emergence of Blockchain has attracted widespread at- eyBadgerBFT [28]). Decentralization is a fundamental basis tention. However, we observe that in practice, many ap- for blockchain systems, including both permissionless (e.g., plications on permissioned blockchains do not benefit from Bitcoin, Ethereum [21]) and permissioned (e.g., Hyperledger the decentralized architecture. When decentralized architec- Fabric [6], Corda [11], Quorum [31]) systems. ture is used but not required, system performance is often A permissionless blockchain usually offers its cryptocur- restricted, resulting in low throughput, high latency, and rency to incentivize participants, which benefits from the significant storage overhead. Hence, we propose LedgerDB decentralized ecosystem. However, in permissioned block- on Alibaba Cloud, which is a centralized ledger database chains, it has not been shown that the decentralized archi- with tamper-evidence and non-repudiation features similar tecture is indispensable, although they have been adopted to blockchain, and provides strong auditability. LedgerDB in many scenarios (such as IP protection, supply chain, and has much higher throughput compared to blockchains. It merchandise provenance). Interestingly, many applications offers stronger auditability by adopting a TSA two-way peg deploy all their blockchain nodes on a BaaS (Blockchain- protocol, which prevents malicious behaviors from both users as-a-Service) environment maintained by a single service and service providers. -

Accelerating Software Delivery with Cloudbees
BLOCKCHAIN-AS-A-SERVICE ACCELERATINGTaking POCs to production with SOFTWARE BlockApps and Red DELIVERY Hat WITH CLOUDBEES JENKINS & RED HAT OPENSTACK SOLUTION BRIEF SOLUTION BRIEF BLOCKAPPS EXPERIENCE BUILD AND TEST NEW ENTERPRISE BLOCKCHAIN APPS RAPIDLY • Over 1,000 BlockApps blockchain Pressure to meet the growing demands of international customers are driving financial services organi- projects in development zations to look for innovative software solutions to distinguish themselves in the marketplace. One of the • Over 100 enterprises building most significant technologies to emerge is the blockchain application, a disruptive shift in architecture solutions on BlockApps that will change how enterprises manage their data, applications, transactions, and business processes. • Contributing member of Ethereum developer community Until now, it has been costly to test and prove the value of blockchain applications in a secure, enterprise- ready environment built on proprietary software. Red Hat and BlockApps are removing those barriers. We have joined forces to help you build innovative proofs-of-concepts and enterprise-ready blockchain applications— RED HAT OPENSHIFT all running on Red Hat® Enterprise Linux® in an OpenShift container. BUSINESS VALUE According to IDC,1 Red Hat The BlockApps STRATO Blockchain Platform includes Ethereum-based features and tools that are designed OpenShift customers experienced: specifically for enterprise businesses to build proofs-of-concepts (POCs) quickly and cost-effectively. Using Red • 66% faster application Hat Enterprise Linux and Red Hat OpenShift Container Platform, you can seamlessly move from development development life cycles and test to full production of your blockchain applications. • 35% less IT staff per applications • 38% lower IT infrastructure costs per application BLOCKAPPPS STRATO BLOCKCHAIN PLATFORM The BlockApps STRATO Blockchain Platform offers customizable transaction processing capabilities and con- 1 IDC White Paper – “The Business Value of Red Hat OpenShift,” Oct. -

Blockchain Deployment Toolkit
Redesigning Trust: Blockchain Deployment Toolkit Supply Chain Focus April 2020 EXPERIENCE THE INTERACTIVE VERSION AT: wef.ch/blockchain-toolkit World Economic Forum 91-93 route de la Capite CH-1223 Cologny/Geneva Switzerland Tel.: +41 (0)22 869 1212 Fax: +41 (0)22 786 2744 Email: [email protected] www.weforum.org © 2020 World Economic Forum. This publication has been published by the World Economic Forum All rights reserved. No part of this as a contribution to a project, insight areas or interaction. The publication may be reproduced findings, interpretations and conclusions expressed herein area or transmitted in any form or by result of a collaborative process facilitated and endorsed by the any means, including World Economic Forum, but whose results do not necessarily photocopying and recording, or represent the views of the World Economic Forum, nor the entirety of by any information storage and its Members, Partners or other stakeholders. retrieval system. Preface The emergence of blockchain technology holds great promise for supply-chain organisations, perhaps as much as any new development in the industry’s infrastructure since it switched to standardised containers decades ago. The case for blockchain is stronger as the COVID-19 pandemic underscores the need for more resilient global supply chains, trusted data and an economic recovery enabled through trade digitization. At the same time, blockchain may engender a fair share of puzzlement and anxiety among supply-chain leaders unfamiliar with it as a new and unfamiliar digitisation tool. This toolkit is designed to help with the deployment journey, whether your organisation is seeking to gain increased efficiency, greater trust with counterparties, or other potential benefits offered by blockchain technology. -

Blockchain As a Service for Iot Cloud Versus Fog
2016 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData) Blockchain as a Service for IoT Cloud versus Fog Mayra Samaniego, Uurtsaikh Jamsrandorj Ralph Deters Department of Computer Science Department of Computer Science University of Saskatchewan University of Saskatchewan Saskatoon, Canada Saskatoon, Canada [email protected], [email protected] [email protected] Abstract—A blockchain is a distributed and decentralized ledger that preceding block is entered. Once a new block is formed, any contains connected blocks of transactions. Unlike other ledger changes to a previous block would result in different hashcode approaches, blockchain guarantees tamper proof storage of approved transactions. Due to its distributed and decentralized organization, and would thus be immediately visible to all participants in the blockchain is beeing used within IoT e.g. to manage device configuration, blockchain. Consequently, blockchains are considered store sensor data and enable micro-payments. A key challenge in the tamperproof distributed transaction ledgers. Originally deployment of blockchain technology is the hosting location. This paper designed as the distributed transaction ledger for BitCoin [3], evaluates the use of cloud and fog as hosting platforms. the idea of using blockchains has spread. Keywords—IoT, Virtual Resource, Software-Defined IoT, Edge The ability to create/store/transfer digital assets in a distributed, Computing, Multi-Tenancy decentralized and tamper-proof way is of a large practical value for IoT systems. While micro-payments in IoT may be the most obvious use of blockchain technology, we consider the I. -

Models to Evaluate Service Provisioning Over
Revista de Informatica´ Teorica´ e Aplicada - RITA - ISSN 2175-2745 Vol. 26, Num. 3 (2019) 65-74 RESEARCH ARTICLE Models to evaluate service Provisioning over Cloud Computing Environments - A Blockchain-As-A-Service case study Modelos para o provimento de Servic¸os em Ambientes de Computac¸ao˜ em Nuvem - Um estudo de caso aplicado a Blockchain como Servic¸o Carlos Melo1*, Jamilson Dantas2, Paulo Pereira3, Ronierison Maciel4, Paulo Maciel5 Abstract: The strictness of the Service Level Agreements (SLAs) is mainly due to a set of constraints related to performance and dependability attributes, such as availability. This paper shows that system’s availability values may be improved by deploying services over a private environment, which may obtain better availability values with improved management, security, and control. However, how much a company needs to afford to keep this improved availability? As an additional activity, this paper compares the obtained availability values with the infrastructure deployment expenses and establishes a cost × benefit relationship. As for the system’s evaluation technique, we choose modeling; while for the service used to demonstrate the models’ feasibility, the blockchain-as-a-service was the selected one. This paper proposes and evaluate four different infrastructures hosting blockchains: (i) baseline; (ii) double redundant; (iii) triple redundant, and (iv) hyper-converged. The obtained results pointed out that the hyper-converged architecture had an advantage over a full triple redundant environment regarding availability and deployment cost. Keywords: Availability — Blockchain-as-a-Service — Hyper-converged — Virtualization Resumo: O rigor nos Acordos de N´ıvel de Servic¸o (ANS) deve-se a um conjunto de restric¸oes˜ nos principais atributos de desempenho e dependabilidade de sistemas. -

NOAH Berlin 2018
Table of Contents Program 6 Venture Capital 10 Growth 107 Buyout 124 Debt 137 Trading Comparables 143 2 Table of Contents Venture Capital Buyout 3TS Capital Partners 11 Frog Capital 50 SevenVentures 90 Apax 125 83North 12 General Catalyst 51 Speedinvest 91 Ardian 126 Accel Partners 13 German Media Pool 52 SpeedUp Venture Capital 92 Bain Capital 127 Acton Capital Partners 14 German Startup Group 53 Group Capvis Equity Partners 128 Astutia Ventures 15 Global Founders Capital 54 STS Ventures 93 EQT Partners 129 Atlantic Labs 16 GPS Ventures 55 Swisscom Ventures 94 FSN Capital Partners 130 AVentures Capital 17 GR Capital 56 TA Ventures 95 GENUI 131 AXA Venture Partners 18 Griffon Capital 57 Target Partners 96 KKR 132 b10 I Venture Capital 19 High-Tech Gruenderfonds 58 Tengelmann Ventures 97 Macquarie Capital 133 BackBone Ventures 20 HV Holtzbrinck Ventures 59 Unternehmertum Venture 98 Maryland 134 Balderton Capital 21 IBB 60 Capital Partners Oakley Capital 135 Berlin Technologie Holding 22 Beteiligungsgesellschaft Vealerian Capital Partners 99 Permira 136 idinvest Partners 61 Ventech 100 Bessemer Venture 23 Partners InMotion Ventures 62 Via ID 101 BCG Digital Ventures 24 Innogy Ventures 63 Vito Ventures 102 BFB Brandenburg Kapital 25 Inovo.vc 64 Vorwerk Ventures 103 Intel Capital 65 W Ventures 104 BMW iVentures 26 Iris Capital 66 WestTech Ventures 105 Boerste Stuttgart - Digital 27 Kizoo Technology Capital 67 XAnge 106 Ventures Debt btov Partners 28 Kreos Capital 68 LeadX Capital Partners 69 Buildit Accelerator 29 Lakestar 70 CapHorn Invest -

Blockchain Technology Adoption Status and Strategies
Journal of International Technology and Information Management Volume 26 Issue 2 Article 4 2017 Blockchain Technology Adoption Status and Strategies Joseph M. Woodside Stetson University, [email protected] Fred K. Augustine Jr. Stetson University Will Giberson Stetson University Follow this and additional works at: https://scholarworks.lib.csusb.edu/jitim Part of the Management Information Systems Commons, Strategic Management Policy Commons, and the Technology and Innovation Commons Recommended Citation Woodside, Joseph M.; Augustine, Fred K. Jr.; and Giberson, Will (2017) "Blockchain Technology Adoption Status and Strategies," Journal of International Technology and Information Management: Vol. 26 : Iss. 2 , Article 4. Available at: https://scholarworks.lib.csusb.edu/jitim/vol26/iss2/4 This Article is brought to you for free and open access by CSUSB ScholarWorks. It has been accepted for inclusion in Journal of International Technology and Information Management by an authorized editor of CSUSB ScholarWorks. For more information, please contact [email protected]. Blockchain Technology Adoption Status and Strategies Joseph M. Woodside et al BLOCKCHAIN TECHNOLOGY ADOPTION STATUS AND STRATEGIES Joseph M. Woodside [email protected], Stetson University Fred K. Augustine Jr. Stetson University Will Giberson Stetson University ABSTRACT Purpose: The purpose of this paper is to review the acceptance and future use of blockchain technology. Given the rapid technological changes, this paper focuses on a managerial overview and framework of how the blockchain, including its implementations such as Bitcoin have advanced and how blockchain can be utilized in large-scale, enterprise environments. The paper begins with a technological overview that covers the history of the technology, as well as describing the computational, cryptographic theory that serves as the basis for its notable security features. -

Blockchain for Dummies
Blockchain For Dummies® Published by: John Wiley & Sons, Inc., 111 River Street, Hoboken, NJ 07030-5774, www.wiley.com Copyright © 2017 by John Wiley & Sons, Inc., Hoboken, New Jersey Published simultaneously in Canada No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without the prior written permission of the Publisher. Requests to the Publisher for permission should be addressed to the Permissions Department, John Wiley & Sons, Inc., 111 River Street, Hoboken, NJ 07030, (201) 748-6011, fax (201) 748-6008, or online at http://www.wiley.com/go/permissions . Trademarks: Wiley, For Dummies, the Dummies Man logo, Dummies.com, Making Everything Easier, and related trade dress are trademarks or registered trademarks of John Wiley & Sons, Inc. and may not be used without written permission. All other trademarks are the property of their respective owners. John Wiley & Sons, Inc. is not associated with any product or vendor mentioned in this book. LIMIT OF LIABILITY/DISCLAIMER OF WARRANTY: THE PUBLISHER AND THE AUTHOR MAKE NO REPRESENTATIONS OR WARRANTIES WITH RESPECT TO THE ACCURACY OR COMPLETENESS OF THE CONTENTS OF THIS WORK AND SPECIFICALLY DISCLAIM ALL WARRANTIES, INCLUDING WITHOUT LIMITATION WARRANTIES OF FITNESS FOR A PARTICULAR PURPOSE. NO WARRANTY MAY BE CREATED OR EXTENDED BY SALES OR PROMOTIONAL MATERIALS. THE ADVICE AND STRATEGIES CONTAINED HEREIN MAY NOT BE SUITABLE FOR EVERY SITUATION. THIS WORK IS SOLD WITH THE UNDERSTANDING THAT THE PUBLISHER IS NOT ENGAGED IN RENDERING LEGAL, ACCOUNTING, OR OTHER PROFESSIONAL SERVICES. -

Microsoft Blockchain Strategy and Roadmap
Microsoft Blockchain in Healthcare David Houlding MASc CISSP CIPP Principal Healthcare Lead | Microsoft Chair | HIMSS Blockchain Task Force Advisor | British Blockchain Association Blockchain in Healthcare - Layered View Healthcare Healthcare Blockchain Architecture Key Org A Org B Blockchain Node Decentralized Ledger Enterprise System Enterprise Internal Firewall Blockchain Network Secure “B2B Middleware” Link (Private / Consortium, Org C Permissioned, Validated) Org D Blockchain Node Deployment On premises In cloud Heterogeneous deployment options Consistent consensus Organization A Today Private Blockchain Organization A Data Common Blockchain Data Node A Private Organization B Data Organization B Blockchain Blockchain Common Node B Shared Ledger for Private Data Common Data Data Private Organization C Data Blockchain Node C Common Data Private Organization C Data Private • Redundant Maintenance of Common Data Data • Common Data Maintained by Consortium • Inconsistencies, Causing Friction • Update Once, Near Realtime Visibility Across Is Blockchain a Missing Cog in Health IT? • Major healthcare benefits in secure, targeted sharing of patient data • Today enterprise systems and data siloed within healthcare organizations • Only limited sharing of healthcare data • Blockchain • Enables secure targeted sharing of healthcare information • Co-exists and integrates with enterprise systems • Can provide the “missing cog” for secure exchange of data • Enables new levels of collaboration to reduce costs and improve outcomes, engagement,