A Comparison of Data Structures to Manage Uris on the Web of Data
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Lecture 04 Linear Structures Sort
Algorithmics (6EAP) MTAT.03.238 Linear structures, sorting, searching, etc Jaak Vilo 2018 Fall Jaak Vilo 1 Big-Oh notation classes Class Informal Intuition Analogy f(n) ∈ ο ( g(n) ) f is dominated by g Strictly below < f(n) ∈ O( g(n) ) Bounded from above Upper bound ≤ f(n) ∈ Θ( g(n) ) Bounded from “equal to” = above and below f(n) ∈ Ω( g(n) ) Bounded from below Lower bound ≥ f(n) ∈ ω( g(n) ) f dominates g Strictly above > Conclusions • Algorithm complexity deals with the behavior in the long-term – worst case -- typical – average case -- quite hard – best case -- bogus, cheating • In practice, long-term sometimes not necessary – E.g. for sorting 20 elements, you dont need fancy algorithms… Linear, sequential, ordered, list … Memory, disk, tape etc – is an ordered sequentially addressed media. Physical ordered list ~ array • Memory /address/ – Garbage collection • Files (character/byte list/lines in text file,…) • Disk – Disk fragmentation Linear data structures: Arrays • Array • Hashed array tree • Bidirectional map • Heightmap • Bit array • Lookup table • Bit field • Matrix • Bitboard • Parallel array • Bitmap • Sorted array • Circular buffer • Sparse array • Control table • Sparse matrix • Image • Iliffe vector • Dynamic array • Variable-length array • Gap buffer Linear data structures: Lists • Doubly linked list • Array list • Xor linked list • Linked list • Zipper • Self-organizing list • Doubly connected edge • Skip list list • Unrolled linked list • Difference list • VList Lists: Array 0 1 size MAX_SIZE-1 3 6 7 5 2 L = int[MAX_SIZE] -

Programmatic Testing of the Standard Template Library Containers
Programmatic Testing of the Standard Template Library Containers y z Jason McDonald Daniel Ho man Paul Stro op er May 11, 1998 Abstract In 1968, McIlroy prop osed a software industry based on reusable comp onents, serv- ing roughly the same role that chips do in the hardware industry. After 30 years, McIlroy's vision is b ecoming a reality. In particular, the C++ Standard Template Library STL is an ANSI standard and is b eing shipp ed with C++ compilers. While considerable attention has b een given to techniques for developing comp onents, little is known ab out testing these comp onents. This pap er describ es an STL conformance test suite currently under development. Test suites for all of the STL containers have b een written, demonstrating the feasi- bility of thorough and highly automated testing of industrial comp onent libraries. We describ e a ordable test suites that provide go o d co de and b oundary value coverage, including the thousands of cases that naturally o ccur from combinations of b oundary values. We showhowtwo simple oracles can provide fully automated output checking for all the containers. We re ne the traditional categories of black-b ox and white-b ox testing to sp eci cation-based, implementation-based and implementation-dep endent testing, and showhow these three categories highlight the key cost/thoroughness trade- o s. 1 Intro duction Our testing fo cuses on container classes |those providing sets, queues, trees, etc.|rather than on graphical user interface classes. Our approach is based on programmatic testing where the number of inputs is typically very large and b oth the input generation and output checking are under program control. -

4 Hash Tables and Associative Arrays
4 FREE Hash Tables and Associative Arrays If you want to get a book from the central library of the University of Karlsruhe, you have to order the book in advance. The library personnel fetch the book from the stacks and deliver it to a room with 100 shelves. You find your book on a shelf numbered with the last two digits of your library card. Why the last digits and not the leading digits? Probably because this distributes the books more evenly among the shelves. The library cards are numbered consecutively as students sign up, and the University of Karlsruhe was founded in 1825. Therefore, the students enrolled at the same time are likely to have the same leading digits in their card number, and only a few shelves would be in use if the leadingCOPY digits were used. The subject of this chapter is the robust and efficient implementation of the above “delivery shelf data structure”. In computer science, this data structure is known as a hash1 table. Hash tables are one implementation of associative arrays, or dictio- naries. The other implementation is the tree data structures which we shall study in Chap. 7. An associative array is an array with a potentially infinite or at least very large index set, out of which only a small number of indices are actually in use. For example, the potential indices may be all strings, and the indices in use may be all identifiers used in a particular C++ program.Or the potential indices may be all ways of placing chess pieces on a chess board, and the indices in use may be the place- ments required in the analysis of a particular game. -

Parallelization of Bulk Operations for STL Dictionaries
Parallelization of Bulk Operations for STL Dictionaries Leonor Frias1?, Johannes Singler2 [email protected], [email protected] 1 Dep. de Llenguatges i Sistemes Inform`atics,Universitat Polit`ecnicade Catalunya 2 Institut f¨urTheoretische Informatik, Universit¨atKarlsruhe Abstract. STL dictionaries like map and set are commonly used in C++ programs. We consider parallelizing two of their bulk operations, namely the construction from many elements, and the insertion of many elements at a time. Practical algorithms are proposed for these tasks. The implementation is completely generic and engineered to provide best performance for the variety of possible input characteristics. It features transparent integration into the STL. This can make programs profit in an easy way from multi-core processing power. The performance mea- surements show the practical usefulness on real-world multi-core ma- chines with up to eight cores. 1 Introduction Multi-core processors bring parallel computing power to the customer at virtu- ally no cost. Where automatic parallelization fails and OpenMP loop paralleliza- tion primitives are not strong enough, parallelized algorithms from a library are a sensible choice. Our group pursues this goal with the Multi-Core Standard Template Library [6], a parallel implementation of the C++ STL. To allow best benefit from the parallel computing power, as many operations as possible need to be parallelized. Sequential parts could otherwise severely limit the achievable speedup, according to Amdahl’s law. Thus, it may be profitable to parallelize an operation even if the speedup is considerably less than the number of threads. The STL contains four kinds of generic dictionary types, namely set, map, multiset, and multimap. -

Prefix Hash Tree an Indexing Data Structure Over Distributed Hash
Prefix Hash Tree An Indexing Data Structure over Distributed Hash Tables Sriram Ramabhadran ∗ Sylvia Ratnasamy University of California, San Diego Intel Research, Berkeley Joseph M. Hellerstein Scott Shenker University of California, Berkeley International Comp. Science Institute, Berkeley and and Intel Research, Berkeley University of California, Berkeley ABSTRACT this lookup interface has allowed a wide variety of Distributed Hash Tables are scalable, robust, and system to be built on top DHTs, including file sys- self-organizing peer-to-peer systems that support tems [9, 27], indirection services [30], event notifi- exact match lookups. This paper describes the de- cation [6], content distribution networks [10] and sign and implementation of a Prefix Hash Tree - many others. a distributed data structure that enables more so- phisticated queries over a DHT. The Prefix Hash DHTs were designed in the Internet style: scala- Tree uses the lookup interface of a DHT to con- bility and ease of deployment triumph over strict struct a trie-based structure that is both efficient semantics. In particular, DHTs are self-organizing, (updates are doubly logarithmic in the size of the requiring no centralized authority or manual con- domain being indexed), and resilient (the failure figuration. They are robust against node failures of any given node in the Prefix Hash Tree does and easily accommodate new nodes. Most impor- not affect the availability of data stored at other tantly, they are scalable in the sense that both la- nodes). tency (in terms of the number of hops per lookup) and the local state required typically grow loga- Categories and Subject Descriptors rithmically in the number of nodes; this is crucial since many of the envisioned scenarios for DHTs C.2.4 [Comp. -

Hash Tables & Searching Algorithms
Search Algorithms and Tables Chapter 11 Tables • A table, or dictionary, is an abstract data type whose data items are stored and retrieved according to a key value. • The items are called records. • Each record can have a number of data fields. • The data is ordered based on one of the fields, named the key field. • The record we are searching for has a key value that is called the target. • The table may be implemented using a variety of data structures: array, tree, heap, etc. Sequential Search public static int search(int[] a, int target) { int i = 0; boolean found = false; while ((i < a.length) && ! found) { if (a[i] == target) found = true; else i++; } if (found) return i; else return –1; } Sequential Search on Tables public static int search(someClass[] a, int target) { int i = 0; boolean found = false; while ((i < a.length) && !found){ if (a[i].getKey() == target) found = true; else i++; } if (found) return i; else return –1; } Sequential Search on N elements • Best Case Number of comparisons: 1 = O(1) • Average Case Number of comparisons: (1 + 2 + ... + N)/N = (N+1)/2 = O(N) • Worst Case Number of comparisons: N = O(N) Binary Search • Can be applied to any random-access data structure where the data elements are sorted. • Additional parameters: first – index of the first element to examine size – number of elements to search starting from the first element above Binary Search • Precondition: If size > 0, then the data structure must have size elements starting with the element denoted as the first element. In addition, these elements are sorted. -

FORSCHUNGSZENTRUM JÜLICH Gmbh Programming in C++ Part II
FORSCHUNGSZENTRUM JÜLICH GmbH Jülich Supercomputing Centre D-52425 Jülich, Tel. (02461) 61-6402 Ausbildung von Mathematisch-Technischen Software-Entwicklern Programming in C++ Part II Bernd Mohr FZJ-JSC-BHB-0155 1. Auflage (letzte Änderung: 19.09.2003) Copyright-Notiz °c Copyright 2008 by Forschungszentrum Jülich GmbH, Jülich Supercomputing Centre (JSC). Alle Rechte vorbehalten. Kein Teil dieses Werkes darf in irgendeiner Form ohne schriftliche Genehmigung des JSC reproduziert oder unter Verwendung elektronischer Systeme verarbeitet, vervielfältigt oder verbreitet werden. Publikationen des JSC stehen in druckbaren Formaten (PDF auf dem WWW-Server des Forschungszentrums unter der URL: <http://www.fz-juelich.de/jsc/files/docs/> zur Ver- fügung. Eine Übersicht über alle Publikationen des JSC erhalten Sie unter der URL: <http://www.fz-juelich.de/jsc/docs> . Beratung Tel: +49 2461 61 -nnnn Auskunft, Nutzer-Management (Dispatch) Das Dispatch befindet sich am Haupteingang des JSC, Gebäude 16.4, und ist telefonisch erreich- bar von Montag bis Donnerstag 8.00 - 17.00 Uhr Freitag 8.00 - 16.00 Uhr Tel.5642oder6400, Fax2810, E-Mail: [email protected] Supercomputer-Beratung Tel. 2828, E-Mail: [email protected] Netzwerk-Beratung, IT-Sicherheit Tel. 6440, E-Mail: [email protected] Rufbereitschaft Außerhalb der Arbeitszeiten (montags bis donnerstags: 17.00 - 24.00 Uhr, freitags: 16.00 - 24.00 Uhr, samstags: 8.00 - 17.00 Uhr) können Sie dringende Probleme der Rufbereitschaft melden: Rufbereitschaft Rechnerbetrieb: Tel. 6400 Rufbereitschaft Netzwerke: Tel. 6440 An Sonn- und Feiertagen gibt es keine Rufbereitschaft. Fachberater Tel. +49 2461 61 -nnnn Fachgebiet Berater Telefon E-Mail Auskunft, Nutzer-Management, E. -

Introduction to Hash Table and Hash Function
Introduction to Hash Table and Hash Function This is a short introduction to Hashing mechanism Introduction Is it possible to design a search of O(1)– that is, one that has a constant search time, no matter where the element is located in the list? Let’s look at an example. We have a list of employees of a fairly small company. Each of 100 employees has an ID number in the range 0 – 99. If we store the elements (employee records) in the array, then each employee’s ID number will be an index to the array element where this employee’s record will be stored. In this case once we know the ID number of the employee, we can directly access his record through the array index. There is a one-to-one correspondence between the element’s key and the array index. However, in practice, this perfect relationship is not easy to establish or maintain. For example: the same company might use employee’s five-digit ID number as the primary key. In this case, key values run from 00000 to 99999. If we want to use the same technique as above, we need to set up an array of size 100,000, of which only 100 elements will be used: Obviously it is very impractical to waste that much storage. But what if we keep the array size down to the size that we will actually be using (100 elements) and use just the last two digits of key to identify each employee? For example, the employee with the key number 54876 will be stored in the element of the array with index 76. -

Balanced Search Trees and Hashing Balanced Search Trees
Advanced Implementations of Tables: Balanced Search Trees and Hashing Balanced Search Trees Binary search tree operations such as insert, delete, retrieve, etc. depend on the length of the path to the desired node The path length can vary from log2(n+1) to O(n) depending on how balanced or unbalanced the tree is The shape of the tree is determined by the values of the items and the order in which they were inserted CMPS 12B, UC Santa Cruz Binary searching & introduction to trees 2 Examples 10 40 20 20 60 30 40 10 30 50 70 50 Can you get the same tree with 60 different insertion orders? 70 CMPS 12B, UC Santa Cruz Binary searching & introduction to trees 3 2-3 Trees Each internal node has two or three children All leaves are at the same level 2 children = 2-node, 3 children = 3-node CMPS 12B, UC Santa Cruz Binary searching & introduction to trees 4 2-3 Trees (continued) 2-3 trees are not binary trees (duh) A 2-3 tree of height h always has at least 2h-1 nodes i.e. greater than or equal to a binary tree of height h A 2-3 tree with n nodes has height less than or equal to log2(n+1) i.e less than or equal to the height of a full binary tree with n nodes CMPS 12B, UC Santa Cruz Binary searching & introduction to trees 5 Definition of 2-3 Trees T is a 2-3 tree of height h if T is empty (height 0), OR T is of the form r TL TR Where r is a node that contains one data item and TL and TR are 2-3 trees, each of height h-1, and the search key of r is greater than any in TL and less than any in TR, OR CMPS 12B, UC Santa Cruz Binary searching & introduction to trees 6 Definition of 2-3 Trees (continued) T is of the form r TL TM TR Where r is a node that contains two data items and TL, TM, and TR are 2-3 trees, each of height h-1, and the smaller search key of r is greater than any in TL and less than any in TM and the larger search key in r is greater than any in TM and smaller than any in TR. -

Getting to the Root of Concurrent Binary Search Tree Performance
Getting to the Root of Concurrent Binary Search Tree Performance Maya Arbel-Raviv, Technion; Trevor Brown, IST Austria; Adam Morrison, Tel Aviv University https://www.usenix.org/conference/atc18/presentation/arbel-raviv This paper is included in the Proceedings of the 2018 USENIX Annual Technical Conference (USENIX ATC ’18). July 11–13, 2018 • Boston, MA, USA ISBN 978-1-939133-02-1 Open access to the Proceedings of the 2018 USENIX Annual Technical Conference is sponsored by USENIX. Getting to the Root of Concurrent Binary Search Tree Performance Maya Arbel-Raviv Trevor Brown Adam Morrison Technion IST Austria Tel Aviv University Abstract reason about data structure performance. Given that real- Many systems rely on optimistic concurrent search trees life search tree workloads operate on trees with millions for multi-core scalability. In principle, optimistic trees of items and do not suffer from high contention [3, 26, 35], have a simple performance story: searches are read-only it is natural to assume that search performance will be and so run in parallel, with writes to shared memory oc- a dominating factor. (After all, most of the time will be curring only when modifying the data structure. However, spent searching the tree, with synchronization—if any— this paper shows that in practice, obtaining the full perfor- happening only at the end of a search.) In particular, we mance benefits of optimistic search trees is not so simple. would expect two trees with similar structure (and thus We focus on optimistic binary search trees (BSTs) similar-length search paths), such as balanced trees with and perform a detailed performance analysis of 10 state- logarithmic height, to perform similarly. -

Hash Tables Hash Tables a "Faster" Implementation for Map Adts
Hash Tables Hash Tables A "faster" implementation for Map ADTs Outline What is hash function? translation of a string key into an integer Consider a few strategies for implementing a hash table linear probing quadratic probing separate chaining hashing Big Ohs using different data structures for a Map ADT? Data Structure put get remove Unsorted Array Sorted Array Unsorted Linked List Sorted Linked List Binary Search Tree A BST was used in OrderedMap<K,V> Hash Tables Hash table: another data structure Provides virtually direct access to objects based on a key (a unique String or Integer) key could be your SID, your telephone number, social security number, account number, … Must have unique keys Each key is associated with–mapped to–a value Hashing Must convert keys such as "555-1234" into an integer index from 0 to some reasonable size Elements can be found, inserted, and removed using the integer index as an array index Insert (called put), find (get), and remove must use the same "address calculator" which we call the Hash function Hashing Can make String or Integer keys into integer indexes by "hashing" Need to take hashCode % array size Turn “S12345678” into an int 0..students.length Ideally, every key has a unique hash value Then the hash value could be used as an array index, however, Ideal is impossible Some keys will "hash" to the same integer index Known as a collision Need a way to handle collisions! "abc" may hash to the same integer array index as "cba" Hash Tables: Runtime Efficient Lookup time does not grow when n increases A hash table supports fast insertion O(1) fast retrieval O(1) fast removal O(1) Could use String keys each ASCII character equals some unique integer "able" = 97 + 98 + 108 + 101 == 404 Hash method works something like… Convert a String key into an integer that will be in the range of 0 through the maximum capacity-1 Assume the array capacity is 9997 hash(key) AAAAAAAA 8482 zzzzzzzz 1273 hash(key) A string of 8 chars Range: 0 .. -
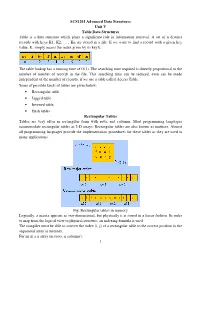
SCS1201 Advanced Data Structures Unit V Table Data Structures Table Is a Data Structure Which Plays a Significant Role in Information Retrieval
SCS1201 Advanced Data Structures Unit V Table Data Structures Table is a data structure which plays a significant role in information retrieval. A set of n distinct records with keys K1, K2, …., Kn are stored in a file. If we want to find a record with a given key value, K, simply access the index given by its key k. The table lookup has a running time of O(1). The searching time required is directly proportional to the number of number of records in the file. This searching time can be reduced, even can be made independent of the number of records, if we use a table called Access Table. Some of possible kinds of tables are given below: • Rectangular table • Jagged table • Inverted table. • Hash tables Rectangular Tables Tables are very often in rectangular form with rows and columns. Most programming languages accommodate rectangular tables as 2-D arrays. Rectangular tables are also known as matrices. Almost all programming languages provide the implementation procedures for these tables as they are used in many applications. Fig. Rectangular tables in memory Logically, a matrix appears as two-dimensional, but physically it is stored in a linear fashion. In order to map from the logical view to physical structure, an indexing formula is used. The compiler must be able to convert the index (i, j) of a rectangular table to the correct position in the sequential array in memory. For an m x n array (m rows, n columns): 1 Each row is indexed from 0 to m-1 Each column is indexed from 0 to n – 1 Item at (i, j) is at sequential position i * n + j Row major order: Assume that the base address is the first location of the memory, so the th Address a ij =storing all the elements in the first(i-1) rows + the number of elements in the i th row up to the j th coloumn = (i-1)*n+j Column major order: Address of a ij = storing all the elements in the first(j-1)th column + The number of elements in the j th column up to the i th rows.