Windows 10 for Enterprises Security Benefits of Timely Adoption
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Through the Looking Glass: Webcam Interception and Protection in Kernel
VIRUS BULLETIN www.virusbulletin.com Covering the global threat landscape THROUGH THE LOOKING GLASS: and WIA (Windows Image Acquisition), which provides a WEBCAM INTERCEPTION AND still image acquisition API. PROTECTION IN KERNEL MODE ATTACK VECTORS Ronen Slavin & Michael Maltsev Reason Software, USA Let’s pretend for a moment that we’re the bad guys. We have gained control of a victim’s computer and we can run any code on it. We would like to use his camera to get a photo or a video to use for our nefarious purposes. What are our INTRODUCTION options? When we talk about digital privacy, the computer’s webcam The simplest option is just to use one of the user-mode APIs is one of the most relevant components. We all have a tiny mentioned previously. By default, Windows allows every fear that someone might be looking through our computer’s app to access the computer’s camera, with the exception of camera, spying on us and watching our every move [1]. And Store apps on Windows 10. The downside for the attackers is while some of us think this scenario is restricted to the realm that camera access will turn on the indicator LED, giving the of movies, the reality is that malware authors and threat victim an indication that somebody is watching him. actors don’t shy away from incorporating such capabilities A sneakier method is to spy on the victim when he turns on into their malware arsenals [2]. the camera himself. Patrick Wardle described a technique Camera manufacturers protect their customers by incorporating like this for Mac [8], but there’s no reason the principle into their devices an indicator LED that illuminates when can’t be applied to Windows, albeit with a slightly different the camera is in use. -

Latest Features Available from the Windows 10 Updates That Could Be Beneficial for Students & Businesses Based Within the Milwaukee Area
Latest features available from the windows 10 updates that could be beneficial for students & businesses based within the Milwaukee area By: Jeremy Konetz | November 20, 2018 | Informative Article What are some of the benefits that the latest windows 10 updates provide to students and Milwaukee area-based businesses? Note the last three updates made available through windows 10 updates are windows 10 version 1709 (Released: January 23, 2018), windows 10 version 1803 (Released: July 6, 2018), and windows 10 version 1809 (Released: October 1, 2018). What are some of the beneficial updates provided in the Windows 10 update version 1709 released on January 23, 2018, one of the first updates Windows 10 released this year. What are the areas that this update has improved on? 1) Deployment a. Launching the autopilot application. i. Accomplished through a zero-touch experience. Example shown in figure 1. Figure 1 Resource link: https://docs.microsoft.com/en-us/windows/whats-new/whats-new-windows-10- version-1709 ii. Client or organization profile configuration can be accomplished at the vendor with the devices sent directly to them upon completion. Example shown in figure 2. Figure 2 1 Resource link: https://docs.microsoft.com/en-us/windows/whats-new/whats-new-windows-10- version-1709 b. Activation on subscription to windows 10. i. Feature allows for Windows 10 enterprise to be deployed within an organizational networks structure without applying any keys or rebooting of devices or components within an organizations operational system. See figure 3. Figure 3 1 Resource link: https://docs.microsoft.com/en-us/windows/whats-new/whats-new-windows-10- version-1709 ii. -

MAXPRO Microsoft Windows Patches.Book
MAXPRO® VMS and NVR Approved Microsoft® Windows Patches Technical Notes MICROSOFT® WINDOWS PATCHES TESTED WITH MAXPRO®NVR AND MAXPRO®VMS Overview The purpose of this document is to identify the patches that have been delivered by Microsoft® Windows and which have been tested against the current shipping ver- sions of MAXPRO®NVR and MAXPRO®VMS with no adverse effects being observed. If you have questions concerning the information in this document, please contact Honeywell Technical Support. See the back cover for contact information. Windows Patches Tested with MAXPRO®NVR till the Month of: June, 2020 Windows Patches Tested with MAXPRO®VMS till the Month of: June, 2020 This document contains: Section See... • June - 2020- Microsoft® Windows Patches Tested with MAXPRO®NVR on page 5 Windows 10 (Enterprise) • June - 2020- Microsoft® Windows Patches Tested with MAXPRO®VMS Server/ Client on Windows 2016 Standard and Windows 10 (Enterprise) page 5 • May - 2020- Microsoft® Windows Patches Tested with MAXPRO®NVR on page 5 Windows 10 (Enterprise) • May - 2020- Microsoft® Windows Patches Tested with MAXPRO®VMS Server/ Client on Windows 2016 Standard and Windows 10 (Enterprise) page 5 • April - 2020- Microsoft® Windows Patches Tested with MAXPRO®VMS Server/ page 7 Client on Windows 2016 Standard and Windows 10 (Enterprise) • April - 2020- Microsoft® Windows Patches Tested with MAXPRO®NVR on Windows 10 (Enterprise) page 7 • March - 2020- Microsoft® Windows Patches Tested with MAXPRO®VMS Server/ page 8 Client on Windows 2016 Standard and Windows 10 (Enterprise) • March - 2020- Microsoft® Windows Patches Tested with MAXPRO®NVR on Windows 10 (Enterprise) page 8 • February - 2020- Microsoft® Windows Patches Tested with MAXPRO®VMS Server/ page 8 Client on Windows 2016 Standard and Windows 10 (Enterprise) • February - 2020- Microsoft® Windows Patches Tested with MAXPRO®NVR on Windows 10 (Enterprise) page 8 800-19154V9-K_Microsoft Windows Patches 1 Section See.. -

Guide to Hardening Windows 10 Technical Guide
NOVEMBER 2020 Guide to Hardening Windows 10 For Administrators, Developers and Office Workers TABLE OF CONTENTS Introduction .......................................................................................................................... 4 Prerequisites ............................................................................................................................ 4 User roles ................................................................................................................................. 4 EFI (BIOS) Configuration ...................................................................................................... 5 To be enabled: ......................................................................................................................... 5 To be disabled: ......................................................................................................................... 5 Windows Defender Firewall .................................................................................................. 6 Enable logging of dropped packets ............................................................................................. 6 Disable enforcement of local rules and disable notifications .......................................................... 7 Block outbound connections by default ....................................................................................... 8 Secure potentially vulnerable protocols ...................................................................................... -

Security Assessment Security Policy Assessment
Security Assessment Security Policy Assessment Prepared for: Jonathan Doe Prepared by: Austin Archer 3/23/2018 CONFIDENTIALITY NOTE: The information contained in this report is for the exclusive use of the client specified above and may contain confidential, privileged and non-disclosable information. If the recipient of this report is not the client or addressee, such recipient is strictly prohibited from reading, photocopying, distributing or otherwise using this report or its contents in any way. Scan Date: 4/1/2014 Security Policy Assessment SECURITY ASSESSMENT Table of Contents 1 - Summary 1.1 - Sampled Systems 2 - Local Security Settings (Sampled Systems) 2.1 - Account Policies 2.1.1 - Password Policy 2.1.2 - Account Lockout Policy 2.2 - Local Policies 2.2.1 - Audit Policy 2.2.2 - User Rights Assignment 2.2.3 - Security Options PROPRIETARY & CONFIDENTIAL Page 2 of 14 Security Policy Assessment SECURITY ASSESSMENT 1 - Summary 1.1 - Sampled Systems IP Addresses Computer Name Operating System 10.0.7.28 tandem Windows 7 Enterprise 172.20.1.3, 10.0.1.3 DC01 Windows Server 2012 Standard PROPRIETARY & CONFIDENTIAL Page 3 of 14 Security Policy Assessment SECURITY ASSESSMENT 2 - Local Security Settings (Sampled Systems) 2.1 - Account Policies 2.1.1 - Password Policy Policy Setting Computers Enforce password history 0 passwords remembered TANDEM 24 passwords remembered DC01 Maximum password age 42 days All Sampled Minimum password age 1 days All Sampled Minimum password length 7 characters All Sampled Password must meet complexity requirements -

Implementing Remote Credential Guard and Remote Admin Mode on Domain-Joined Windows 10 Clients
INF258x: Implementing Remote Credential Guard and Remote Admin mode on Domain-joined Windows 10 Clients Estimated Time: 30 minutes You have a domain-joined Windows 10 client computer. You plan to take advantage of the Remote Desktop Credential Guard and Restrict Admin mode to protect credentials during Remote Desktop sessions between Windows 10 client and Windows Server 2016 computers. Objectives After completing this lab, students will be able to: • Implement Remote Credential Guard. • Implement the Restricted Admin mode. • Verify functionality of Remote Credential Guard and the Restricted Admin mode. Lab environment The lab consists of the following computers: • LON-DC1 – a Windows Server 2016 domain controller in the adatum.com single-domain forest. • LON-SVR1 – a Windows Server 2016 domain member server • LON-CL1 – a Windows 10 Pro or Enterprise version 1607 (or newer) domain member computer with Remote Server Administration Tools for Windows 10 All computers have Windows PowerShell Remoting enabled and have Internet connectivity Remote Desktop connections protected with Credential Guard have the following characteristics: • Require Windows 10 version 1607 (or newer) or Windows Server 2016 • Enforce of Kerberos authentication (NTLM is not allowed). • Require that both computers (a Remote Desktop client and a Remote Desktop host) are members of the same Active Directory domain or trusted Active Directory domains (Kerberos is enforced) • Support connecting with non-Administrative credentials (as a member of the Remote Desktop Users group) -

Run-Commands-Windows-10.Pdf
Run Commands Windows 10 by Bettertechtips.com Command Action Command Action documents Open Documents Folder devicepairingwizard Device Pairing Wizard videos Open Videos Folder msdt Diagnostics Troubleshooting Wizard downloads Open Downloads Folder tabcal Digitizer Calibration Tool favorites Open Favorites Folder dxdiag DirectX Diagnostic Tool recent Open Recent Folder cleanmgr Disk Cleanup pictures Open Pictures Folder dfrgui Optimie Drive devicepairingwizard Add a new Device diskmgmt.msc Disk Management winver About Windows dialog dpiscaling Display Setting hdwwiz Add Hardware Wizard dccw Display Color Calibration netplwiz User Accounts verifier Driver Verifier Manager azman.msc Authorization Manager utilman Ease of Access Center sdclt Backup and Restore rekeywiz Encryption File System Wizard fsquirt fsquirt eventvwr.msc Event Viewer calc Calculator fxscover Fax Cover Page Editor certmgr.msc Certificates sigverif File Signature Verification systempropertiesperformance Performance Options joy.cpl Game Controllers printui Printer User Interface iexpress IExpress Wizard charmap Character Map iexplore Internet Explorer cttune ClearType text Tuner inetcpl.cpl Internet Properties colorcpl Color Management iscsicpl iSCSI Initiator Configuration Tool cmd Command Prompt lpksetup Language Pack Installer comexp.msc Component Services gpedit.msc Local Group Policy Editor compmgmt.msc Computer Management secpol.msc Local Security Policy: displayswitch Connect to a Projector lusrmgr.msc Local Users and Groups control Control Panel magnify Magnifier -

Windows 10 Enterprise E3 in CSP - Windows Deployment | Microsoft Docs
07/01/2020 Windows 10 Enterprise E3 in CSP - Windows Deployment | Microsoft Docs Windows 10 Enterprise E3 in CSP 08/23/2017 • 16 minutes to read • +5 In this article Compare Windows 10 Pro and Enterprise editions Deployment of Windows 10 Enterprise E3 licenses Deploy Windows 10 Enterprise features Related topics Windows 10 Enterprise E3 launched in the Cloud Solution Provider (CSP) channel on September 1, 2016. Windows 10 Enterprise E3 in CSP is a new offering that delivers, by subscription, exclusive features reserved for Windows 10 Enterprise edition. This offering is available through the Cloud Solution Provider (CSP) channel via the Partner Center as an online service. Windows 10 Enterprise E3 in CSP provides a flexible, per- user subscription for small- and medium-sized organizations (from one to hundreds of users). To take advantage of this offering, you must have the following: Windows 10 Pro, version 1607 (Windows 10 Anniversary Update) or later, installed and activated, on the devices to be upgraded Azure Active Directory (Azure AD) available for identity management Starting with Windows 10, version 1607 (Windows 10 Anniversary Update), you can move from Windows 10 Pro to Windows 10 Enterprise more easily than ever before— no keys and no reboots. After one of your users enters the Azure AD credentials associated with a Windows 10 Enterprise E3 license, the operating system turns from Windows 10 Pro to Windows 10 Enterprise and all the appropriate Windows 10 Enterprise features are unlocked. When a subscription license expires or is transferred to another user, the Windows 10 Enterprise device seamlessly steps back down to Windows 10 Pro. -

Feature Description
NTLM Feature Description UPDATED: 19 March 2021 NTLM Copyright Notices Copyright © 2002-2021 Kemp Technologies, Inc. All rights reserved. Kemp Technologies and the Kemp Technologies logo are registered trademarks of Kemp Technologies, Inc. Kemp Technologies, Inc. reserves all ownership rights for the LoadMaster and Kemp 360 product line including software and documentation. Used, under license, U.S. Patent Nos. 6,473,802, 6,374,300, 8,392,563, 8,103,770, 7,831,712, 7,606,912, 7,346,695, 7,287,084 and 6,970,933 kemp.ax 2 Copyright 2002-2021, Kemp Technologies, All Rights Reserved NTLM Table of Contents 1 Introduction 4 1.1 Document Purpose 6 1.2 Intended Audience 6 1.3 Related Firmware Version 6 2 Configure NTLM Authentication 7 2.1 Configure Internet Options on the Client Machine 7 2.2 Configure the LoadMaster 11 2.2.1 Enable NTLM Proxy Mode 13 2.2.2 Configure the Server Side SSO Domain 13 2.2.3 Configure the Client Side SSO Domain 15 2.2.4 Configure the Virtual Service 15 2.3 Configure Firefox to Allow NTLM (if needed) 17 2.4 Troubleshooting 18 References 19 Last Updated Date 20 kemp.ax 3 Copyright 2002-2021, Kemp Technologies, All Rights Reserved NTLM 1 Introduction 1 Introduction NT LAN Manager (NTLM) is a Windows Challenge/Response authentication protocol that is often used on networks that include systems running the Windows operating system and Active Directory. Kerberos authentication adds greater security than NTLM systems on a network and provides Windows-based systems with an integrated single sign-on (SSO) mechanism. -

Copyrighted Material
11_783269 bindex.qxp 11/10/06 11:15 AM Page 209 Index applications (defined), 205. See also programs Numerics arranging windows, 43–44 100% button (Internet Explorer 7), 99–100 assigning sounds to program events, 24 audio visualizations, 186 A Windows Media Player 11, 183, 185–186 accessibility options, 156 audio CDs. See CDs accessories, 205 Audio Description feature, 157 account types, 169 AutoComplete feature (Internet Explorer 7), 101 accounts (administrative), 169 automatic updates with Windows Update, 161–162, 167 accounts (e-mail), 124 AutoPlay, 13, 148, 151 accounts (user) Autosearching feature (Internet Explorer 7), 113 account types, 169 adding, 169 creating, 169 B deleting, 170 backgrounds for desktop, 24 managing, 168, 170 Backup and Restore Center, 140–143, 146 names, 169 Backup Files dialog box, 141 Parental Controls, 170 backups passwords, 169 CompletePC Backup utility, 140–142 pictures, 169–170 DVD discs, 142 switching, 74 File and Folder Backup utility, 140–142 User Account Control (UAC), 170 Send To shortcut menu command, 64–65 activity reporting, 165 stopping, 141 activity reports, 166 BitLocker drive encryption, 163–164 Add Printer Wizard, 149–151 blocking Add to Library dialog box, 187 computer use, 165 adding Web sites, 165 bookmarks to Favorites Center, 102 blog, 208 gadgets, 31–32 bookmarks (Internet Explorer 7) icons, 35 adding to Favorites Center, 102 languages, 155–156 deleting, 104 music, 187 importing, 101 printers, 149–151 moving, 103–105 user accounts, 169 organizing, 103–105 address bar, 15–16 renaming, 104 address book, 128–130 selecting, 103 Address toolbar, 41 browser (defined), 208. See also Internet Explorer 7 adjusting volume, 152 browsing offline. -

3 Deployment Options
Prior to the parties indicating final agreement by signing a Work Order, the information contained in this document represents the current view of CB5 Solutions, LLC on the issues discussed as of the date of publication and is subject to change. Furthermore, because CB5 must respond to changing market conditions, this document should not be interpreted as an invitation to contract or a commitment on the part of CB5. Changes to this document will be managed through a Change Management Process. CB5 MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. Without limiting the rights under copyright, no part of this document may be reproduced, stored in or introduced into a retrieval system, or transmitted in any form or by any means (electronic, mechanical, photocopying, recording, or otherwise), or for any purpose, without the express written permission of CB5 Solutions, LLC. CB5 may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from CB5, our provision of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. The descriptions of other companies’ products in this document, if any, are provided only as a convenience to you. Any such references should not be considered an endorsement or support by CB5. CB5 cannot guarantee their accuracy, and the products may change over time. Also, the descriptions are intended as brief highlights to aid understanding, rather than as thorough coverage. -
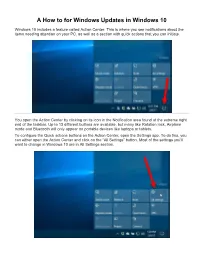
A How to for Windows Updates in Windows 10
A How to for Windows Updates in Windows 10 Windows 10 includes a feature called Action Center. This is where you see notifications about the items needing attention on your PC, as well as a section with quick actions that you can initiate. You open the Action Center by clicking on its icon in the Notification area found at the extreme right end of the taskbar. Up to 13 different buttons are available, but many like Rotation lock, Airplane mode and Bluetooth will only appear on portable devices like laptops or tablets. To configure the Quick actions buttons on the Action Center, open the Settings app. To do this, you can either open the Action Center and click on the “All Settings” button. Most of the settings you'll want to change in Windows 10 are in All Settings section. or you can open the Start menu and click the “Settings” button on the lower-left side of the menu. Windows settings is organized into various categories: System, Devices, Network & Internet, Personalization, Apps, Accounts, Time & language, Ease of Access, Privacy, and Update & security. You click on a category to view and change more settings for that category. Settings in Windows 10 – alternatively use Win () + I key combination. The Settings app from Windows 10 holds almost all the settings governing the way your computer or device works. The traditional way of getting to one setting or to another is to open the appropriate settings category and browse through it until you find what you’re looking for. The Setting app from Windows 10 is very well organized, a lot better than the old Control Panel used to be.