Retrofitting Fine Grain Isolation in the Firefox Renderer
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Technical Intelligence ISSUE: 19.04.21
Technical Intelligence ISSUE: 19.04.21 The CyberScotland Technical Threat Intelligence Bulletin is designed to provide you with information about updates, exploits and countermeasures. We hope that you benefit from this resource and we ask that you circulate this information to your networks, adapting where you see fit. Jump To TECHNICAL THREAT AWARENESS AND HUNTING Microsoft Patch Tuesday (April 2021) Adobe Patches Slew of Critical Security Bugs Patch Chrome to Remediated In-The-Wild 0-Day Exploits F5 urges customers to patch critical BIG-IP pre-auth RCE bug Wordpress Privilege-Escalation and Authentication Bypass Apple rushes to patch zero‑day flaw in iOS, iPadOS Cisco Will Not Patch Critical RCE Flaw Affecting End-of-Life Business Routers Threat Intelligence Bulletin Technical Threat Awareness and Hunting Microsoft Patch Tuesday (April 2021) Microsoft released its monthly security update Tuesday 13th April 2021, disclosing 114 vulnerabilities across its suite of products1. Four new remote code execution vulnerabilities in Microsoft Exchange Server are included, beyond those that were release out-of-band last month. The detection of the vulnerabilities which led to these patches has been attributed to the US’s National Security Agency (NSA)2. Given the recent focus on Microsoft Exchange by varying threat actors, NCSC has produced an alert encouraging organisations to install the critical updates immediately3. More patches are likely to follow for Microsoft’s Exchange servers as, at a recent hacking contest called pwn2own a team called DEVCORE combined an authentication bypass and a local privilege escalation to complete take over the Exchange server. As a result they won $200,000.4 In all, there are 20 critical vulnerabilities as part of this release and one considered of “moderate” severity. -

Draft SP 800-125A Rev. 1, Security Recommendations for Server
The attached DRAFT document (provided here for historical purposes), released on April 11, 2018, has been superseded by the following publication: Publication Number: NIST Special Publication (SP) 800-125A Rev. 1 Title: Security Recommendations for Server-based Hypervisor Platforms Publication Date: June 2018 • Final Publication: https://doi.org/10.6028/NIST.SP.800-125Ar1 (which links to https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-125Ar1.pdf). • Related Information on CSRC: Final: https://csrc.nist.gov/publications/detail/sp/800-125a/rev-1/final 1 Draft NIST Special Publication 800-125A 2 Revision 1 3 4 Security Recommendations for 5 Hypervisor Deployment on 6 ServersServer-based Hypervisor 7 Platforms 8 9 10 11 12 Ramaswamy Chandramouli 13 14 15 16 17 18 19 20 21 22 23 C O M P U T E R S E C U R I T Y 24 25 Draft NIST Special Publication 800-125A 26 Revision 1 27 28 29 30 Security Recommendations for 31 Server-based Hypervisor Platforms 32 33 Hypervisor Deployment on Servers 34 35 36 37 Ramaswamy Chandramouli 38 Computer Security Division 39 Information Technology Laboratory 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 April 2018 56 57 58 59 60 61 U.S. Department of Commerce 62 Wilbur L. Ross, Jr., Secretary 63 64 National Institute of Standards and Technology 65 Walter Copan, NIST Director and Under Secretary of Commerce for Standards and Technology 66 67 Authority 68 69 This publication has been developed by NIST in accordance with its statutory responsibilities under the 70 Federal Information Security Modernization Act (FISMA) of 2014, 44 U.S.C. -

CA Network Flow Analysis Release Notes
CA Network Flow Analysis Release Notes Release 9.1.3 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the “Documentation”) is for your informational purposes only and is subject to change or withdrawal by CA at any time. This Documentation may not be copied, transferred, reproduced, disclosed, modified or duplicated, in whole or in part, without the prior written consent of CA. This Documentation is confidential and proprietary information of CA and may not be disclosed by you or used for any purpose other than as may be permitted in (i) a separate agreement between you and CA governing your use of the CA software to which the Documentation relates; or (ii) a separate confidentiality agreement between you and CA. Notwithstanding the foregoing, if you are a licensed user of the software product(s) addressed in the Documentation, you may print or otherwise make available a reasonable number of copies of the Documentation for internal use by you and your employees in connection with that software, provided that all CA copyright notices and legends are affixed to each reproduced copy. The right to print or otherwise make available copies of the Documentation is limited to the period during which the applicable license for such software remains in full force and effect. Should the license terminate for any reason, it is your responsibility to certify in writing to CA that all copies and partial copies of the Documentation have been returned to CA or destroyed. TO THE EXTENT PERMITTED BY APPLICABLE LAW, CA PROVIDES THIS DOCUMENTATION “AS IS” WITHOUT WARRANTY OF ANY KIND, INCLUDING WITHOUT LIMITATION, ANY IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, OR NONINFRINGEMENT. -

HTTP Cookie - Wikipedia, the Free Encyclopedia 14/05/2014
HTTP cookie - Wikipedia, the free encyclopedia 14/05/2014 Create account Log in Article Talk Read Edit View history Search HTTP cookie From Wikipedia, the free encyclopedia Navigation A cookie, also known as an HTTP cookie, web cookie, or browser HTTP Main page cookie, is a small piece of data sent from a website and stored in a Persistence · Compression · HTTPS · Contents user's web browser while the user is browsing that website. Every time Request methods Featured content the user loads the website, the browser sends the cookie back to the OPTIONS · GET · HEAD · POST · PUT · Current events server to notify the website of the user's previous activity.[1] Cookies DELETE · TRACE · CONNECT · PATCH · Random article Donate to Wikipedia were designed to be a reliable mechanism for websites to remember Header fields Wikimedia Shop stateful information (such as items in a shopping cart) or to record the Cookie · ETag · Location · HTTP referer · DNT user's browsing activity (including clicking particular buttons, logging in, · X-Forwarded-For · Interaction or recording which pages were visited by the user as far back as months Status codes or years ago). 301 Moved Permanently · 302 Found · Help 303 See Other · 403 Forbidden · About Wikipedia Although cookies cannot carry viruses, and cannot install malware on 404 Not Found · [2] Community portal the host computer, tracking cookies and especially third-party v · t · e · Recent changes tracking cookies are commonly used as ways to compile long-term Contact page records of individuals' browsing histories—a potential privacy concern that prompted European[3] and U.S. -
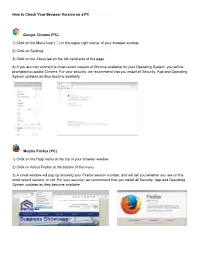
How to Check Your Browser Version on a PC
How to Check Your Browser Version on a PC Google Chrome (PC) 1) Click on the Menu Icon ( ) in the upper right corner of your browser window. 2) Click on Settings 3) Click on the About tab on the left-hand side of the page. 4) If you are not running the most recent version of Chrome available for your Operating System, you will be prompted to update Chrome. For your security, we recommend that you install all Security, App and Operating System updates as they become available. Mozilla Firefox (PC) 1) Click on the Help menu at the top of your browser window. 2) Click on About Firefox at the bottom of the menu. 3) A small window will pop up showing your Firefox version number, and will tell you whether you are on the most recent version, or not. For your security, we recommend that you install all Security, App and Operating System updates as they become available. Internet Explorer (PC) 1) Click on the Gear Icon at the top of your browser window. 2) Click on the About Internet Explorer option. 3) A window will pop up showing you your Internet Explorer version. 4) If you are using Internet Explorer 9 or 10, you will need to make sure that you have TLS 1.2 enabled by: A) Clicking on the Gear Icon again. B) Click on Internet Options. C) Click on the Advanced Tab and scroll down to the option titled “Use TLS 1.2”. (This should be found at the bottome of the list of options.) The box next to this should be checked. -

Designing and Implementing the OP and OP2 Web Browsers
Designing and Implementing the OP and OP2 Web Browsers CHRIS GRIER, SHUO TANG and SAMUEL T. KING, University of Illinois at Urbana-Champaign Current web browsers are plagued with vulnerabilities, providing hackers with easy access to computer systems via browser-based attacks. Browser security efforts that retrofit existing browsers have had lim- ited success because the design of modern browsers is fundamentally flawed. To enable more secure web browsing, we design and implement a new browser, called the OP web browser, that attempts to improve the state-of-the-art in browser security. We combine operating system design principles with formal methods to design a more secure web browser by drawing on the expertise of both communities. Our design philosophy is to partition the browser into smaller subsystems and make all communication between subsystems sim- ple and explicit. At the core of our design is a small browser kernel that manages the browser subsystems and interposes on all communications between them to enforce our new browser security features. To show the utility of our browser architecture, we design and implement three novel security features. First, we develop flexible security policies that allow us to include browser plugins within our security framework. Second, we use formal methods to prove useful security properties including user interface invariants and browser security policy. Third, we design and implement a browser-level information-flow tracking system to enable post-mortem analysis of browser-based attacks. In addition to presenting the OP browser architecture, we discuss the design and implementation of a second version of OP, OP2, that includes features from other secure web browser designs to improve on the overall security and performance of OP. -

$Hell on Earth: from Browser to System Compromise
$hell on Earth: From Browser to System Compromise Matt Molinyawe, Abdul-Aziz Hariri, and Jasiel Spelman A Zero Day Initiative Research Paper TREND MICRO LEGAL DISCLAIMER The information provided herein is for general information Contents and educational purposes only. It is not intended and should not be construed to constitute legal advice. The information contained herein may not be applicable to all situations and may not reflect the most current situation. 3 Nothing contained herein should be relied on or acted upon without the benefit of legal advice based on the particular facts and circumstances presented and nothing Introduction herein should be construed otherwise. Trend Micro reserves the right to modify the contents of this document at any time without prior notice. Translations of any material into other languages are 4 intended solely as a convenience. Translation accuracy is not guaranteed nor implied. If any questions arise related to the accuracy of a translation, please refer to Mitigation Evolution the original language official version of the document. Any discrepancies or differences created in the translation are not binding and have no legal effect for compliance or enforcement purposes. 6 Although Trend Micro uses reasonable efforts to include accurate and up-to-date information herein, Trend Micro History and Anatomy makes no warranties or representations of any kind as to its accuracy, currency, or completeness. You agree of Pwn2Own Remote that access to and use of and reliance on this document and the content thereof is at your own risk. Trend Micro Browser to Super-User disclaims all warranties of any kind, express or implied. -

Security Analysis of Firefox Webextensions
6.857: Computer and Network Security Due: May 16, 2018 Security Analysis of Firefox WebExtensions Srilaya Bhavaraju, Tara Smith, Benny Zhang srilayab, tsmith12, felicity Abstract With the deprecation of Legacy addons, Mozilla recently introduced the WebExtensions API for the development of Firefox browser extensions. WebExtensions was designed for cross-browser compatibility and in response to several issues in the legacy addon model. We performed a security analysis of the new WebExtensions model. The goal of this paper is to analyze how well WebExtensions responds to threats in the previous legacy model as well as identify any potential vulnerabilities in the new model. 1 Introduction Firefox release 57, otherwise known as Firefox Quantum, brings a large overhaul to the open-source web browser. Major changes with this release include the deprecation of its initial XUL/XPCOM/XBL extensions API to shift to its own WebExtensions API. This WebExtensions API is currently in use by both Google Chrome and Opera, but Firefox distinguishes itself with further restrictions and additional functionalities. Mozilla’s goals with the new extension API is to support cross-browser extension development, as well as offer greater security than the XPCOM API. Our goal in this paper is to analyze how well the WebExtensions model responds to the vulnerabilities present in legacy addons and discuss any potential vulnerabilities in the new model. We present the old security model of Firefox extensions and examine the new model by looking at the structure, permissions model, and extension review process. We then identify various threats and attacks that may occur or have occurred before moving onto recommendations. -

Isolation, Resource Management, and Sharing in Java
Processes in KaffeOS: Isolation, Resource Management, and Sharing in Java Godmar Back, Wilson C. Hsieh, Jay Lepreau School of Computing University of Utah Abstract many environments for executing untrusted code: for example, applets, servlets, active packets [41], database Single-language runtime systems, in the form of Java queries [15], and kernel extensions [6]. Current systems virtual machines, are widely deployed platforms for ex- (such as Java) provide memory protection through the ecuting untrusted mobile code. These runtimes pro- enforcement of type safety and secure system services vide some of the features that operating systems pro- through a number of mechanisms, including namespace vide: inter-application memory protection and basic sys- and access control. Unfortunately, malicious or buggy tem services. They do not, however, provide the ability applications can deny service to other applications. For to isolate applications from each other, or limit their re- example, a Java applet can generate excessive amounts source consumption. This paper describes KaffeOS, a of garbage and cause a Web browser to spend all of its Java runtime system that provides these features. The time collecting it. KaffeOS architecture takes many lessons from operating To support the execution of untrusted code, type-safe system design, such as the use of a user/kernel bound- language runtimes need to provide a mechanism to iso- ary, and employs garbage collection techniques, such as late and manage the resources of applications, analogous write barriers. to that provided by operating systems. Although other re- The KaffeOS architecture supports the OS abstraction source management abstractions exist [4], the classic OS of a process in a Java virtual machine. -

Inlined Information Flow Monitoring for Javascript
Inlined Information Flow Monitoring for JavaScript Andrey Chudnov David A. Naumann Stevens Institute of Technology Stevens Institute of Technology Hoboken, NJ 07030 USA Hoboken, NJ 07030 USA [email protected] [email protected] ABSTRACT JS engines are highly engineered for performance, which has Extant security mechanisms for web apps, notably the\same- led some researchers to argue for inlined monitoring for IFC. origin policy", are not sufficient to achieve confidentiality The main contribution of this paper is an inlined IFC mon- and integrity goals for the many apps that manipulate sen- itor that enforces non-interference for apps written in JS. sitive information. The trend in web apps is \mashups" We present the main design decisions and rationale, together which integrate JavaScript code from multiple providers in with technical highlights and a survey of state of the art al- ways that can undercut existing security mechanisms. Re- ternatives. The tool is evaluated using synthetic case studies searchers are exploring dynamic information flow controls and performance benchmarks. (IFC) for JavaScript, but there are many challenges to achiev- ing strong IFC without excessive performance cost or im- On IFC. Browsers and other platforms currently provide practical browser modifications. This paper presents an in- isolation mechanisms and access controls. Pure isolation lined IFC monitor for ECMAScript 5 with web support, goes against integration of app code from multiple providers. using the no-sensitive-upgrade (NSU) technique, together Access controls can be more nuanced, but it is well-known with experimental evaluation using synthetic mashups and that access control policies are safety properties whereas IF performance benchmarks. -

Cali: Compiler-Assisted Library Isolation
Cali: Compiler-Assisted Library Isolation Markus Bauer Christian Rossow CISPA Helmholtz Center for Information Security CISPA Helmholtz Center for Information Security Saarbrücken, Saarland, Germany Saarbrücken, Saarland, Germany [email protected] [email protected] ABSTRACT the full program’s privileges and address space. This lack of privi- Software libraries can freely access the program’s entire address lege separation and memory isolation has led to numerous critical space, and also inherit its system-level privileges. This lack of sepa- security incidents. ration regularly leads to security-critical incidents once libraries We can significantly reduce this threat surface by isolating the contain vulnerabilities or turn rogue. We present Cali, a compiler- library from the main program. In most cases, a library (i) neither assisted library isolation system that fully automatically shields a requires access to the entire program’s address space, (ii) nor needs program from a given library. Cali is fully compatible with main- the full program’s privileges to function properly. In fact, even line Linux and does not require supervisor privileges to execute. We complex libraries such as parsers require only limited interaction compartmentalize libraries into their own process with well-defined with the program and/or system. Conceptually, there is thus little security policies. To preserve the functionality of the interactions need to grant an untrusted library access to the program or to between program and library, Cali uses a Program Dependence critical system privileges. Basic compartmentalization principles Graph to track data flow between the program and the library dur- thus help to secure a program from misuse by untrusted code. -

One Page Series: Mac OS X -- Ipv6 and Browsing the Web Via Firefox, Camino, Opera and Safari
One Page Series: Mac OS X -- IPv6 and Browsing the Web Via Firefox, Camino, Opera and Safari [If you haven t already done so, begin with One Page Series: Mac OS X -- Enabling Native IPv6 Via Stateless Autoconfiguration ] If you don t already have Firefox on your Mac, you can download it for free from http://www.mozilla.com/firefox/ If you don t already have Camino on your Mac, you can download it for free from http://caminobrowser.org/ If you don t already have Opera on your Mac, you can download it for free from http://www.opera.com/ Safari is another option, bundled for free with Mac OS X. You can find Safari in your Mac s Applications folder. Browsing the IPv6 Web With Firefox (or Camino) Firefox (and Camino) are both IPv6 aware, but need one tweak to work properly with IPv6. Launch Firefox (or Camino) and go to about:config Filter on ipv6 Click on network.dns.disableIPv6 to set the value for that preference item to false You only need to adjust this setting once -- it will be remembered from then on Now try using IPv6 by going to http://ipv6.google.com/ You should see a dancing Google Browsing the IPv6 Web With Opera Opera is all set to work with IPv6 web sites, just launch Opera and stick in an IPv6 URL and Opera will go to that site. Browsing the IPv6 Web With Safari There is one key thing to know about Safari and IPv6, and that is that in some versions of OS X and Safari, it likes IPv4 more than it likes IPv6.