Permission Analysis of Health and Fitness Apps in Iot Programming Frameworks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Fitkit Android Application
International Journal of Engineering Applied Sciences and Technology, 2019 Vol. 4, Issue 4, ISSN No. 2455-2143, Pages 203-205 Published Online August 2019 in IJEAST (http://www.ijeast.com) FITKIT ANDROID APPLICATION Aashita Chhabra, Chitrank Tyagi Department of Information Technology, Guru Gobind Singh Indraprastha University, Sector 16C, Dwarka, Delhi, 110078 Abstract— “Age is just a number” a quote that explains one can never get old if one follows proper healthy routine. A. Application Fundamentals: With the initiatives taken by the government and various Android applications are written in Java programming industries (Bollywood, Cricket etc) fitness is gaining language. However, it is important to remember that they are popularity among the individuals. Smartphones and not executed using the standard Java Virtual Machine (JVM). tablets are slowly but steadily changing the way we look Instead, Google has created a custom VM called Dalvik which after our health and fitness. Today, many high quality is responsible for converting and executing Java byte code. All mobile apps are available for users and health custom Java classes must be converted (this is done professionals and cover the whole health care chain, i.e. automatically but can also be done manually) into a Dalvik information collection, prevention, diagnosis, treatment compatible instruction set before being executed into an and monitoring. Our team has developed a mobile Android operating system. Dalvik VM takes the generated application called FitKit which is implemented using Java class files and combines them into one or more Dalvik Android framework and is available for android users. Executable (.dex) files. It reuses duplicate information from Our app mainly focuses on fitness regimes inclusive of multiple class files, effectively reducing the space requirement meals allotment, workout routine, chat support with (uncompressed) by half from a traditional .jar file. -

Jeremy Nelson, CEO Afia Inc
Internet of Health Apps, Wearables, Population Health, and Integrated Care Jeremy Nelson, CEO Afia Inc. At a high level 1. New generation of connected devices 2. New models for care delivery 3. New class of innovative startups 4. Supported by payment reform 2010 Sensors & Technology ● GPS ● Cameras ● Microphones ● 6-axis accelerometer ● Compass ● Light sensor ● Proximity sensor ● Wi-Fi & 3G ● Bluetooth In Just The Last 7 Years 2015 Sensors & Technology ● 70x faster CPU ● 90x faster graphics ● NFC ● Barometer ● 4G/LTE ● Bluetooth Low Energy ● Motion Coprocessor ● 3D Touch “What is your most important device?” Smart Devices 1.0 The Pavlok Band ● Activity tracking ● Sleep tracking ● “Shock circuit” The Pavlok Band “Pay a fine, lose access to your phone, even get an electric shock… at the hands of your friends” if you fail to meet goals Who tracks their health? ● 45% of U.S. adults live with at least one chronic condition. ● Of those with 2+ Conditions ○ 78% have high blood pressure ○ 45% have diabetes Source: Pew Research Connected Wearables Show of Hands Android Wear Apple Watch Common Sensors ● Heart rate sensor ● Accelerometer ● BTLE + Wifi ● GPS (Phone) Apple S1 Chip ? Fourteen Months In ● Battery life - good ● Hardware design - excellent ● Messaging - excellent ● Activity tracking & fitness - good ● Third-party apps - poor Epic - MyChart on Apple Watch Appointment reminders, messages, medications integrated with EHR Emotiv Insight ● Consumer EEG & inertial sensor ● Bluetooth integration with smartphone ● Available via API Spire Mind & Body Tracker ● Measures breathing & provides feedback ● Senses stress/tension, suggest deep breath ● Included iOS guides “mini-meditations” MIT “Band-aid of the Future” ● Sticky, stretchy, gel- like material ● Incorporates sensors (eg. -
A Research on Android Technology with New Version Naugat(7.0,7.1)
IOSR Journal of Computer Engineering (IOSR-JCE) e-ISSN: 2278-0661,p-ISSN: 2278-8727, Volume 19, Issue 2, Ver. I (Mar.-Apr. 2017), PP 65-77 www.iosrjournals.org A Research On Android Technology With New Version Naugat(7.0,7.1) Nikhil M. Dongre , Tejas S. Agrawal, Ass.prof. Sagar D. Pande (Dept. CSE, Student of PRPCOE, SantGadge baba Amravati University, [email protected] contact no: 8408895842) (Dept. CSE, Student of PRMCEAM, SantGadge baba Amravati University, [email protected] contact no: 9146951658) (Dept. CSE, Assistant professor of PRPCOE, SantGadge baba Amravati University, [email protected], contact no:9405352824) Abstract: Android “Naugat” (codenamed Android N in development) is the seventh major version of Android Operating System called Android 7.0. It was first released as a Android Beta Program build on March 9 , 2016 with factory images for current Nexus devices, which allows supported devices to be upgraded directly to the Android Nougat beta via over-the-air update. Nougat is introduced as notable changes to the operating system and its development platform also it includes the ability to display multiple apps on-screen at once in a split- screen view with the support for inline replies to notifications, as well as an OpenJDK-based Java environment and support for the Vulkan graphics rendering API, and "seamless" system updates on supported devices. Keywords: jellybean, kitkat, lollipop, marshmallow, naugat I. Introduction This research has been done to give you the best details toward the exciting new frontier of open source mobile development. Android is the newest mobile device operating system, and this is one of the first research to help the average programmer become a fearless Android developer. -

Intelligent Conversational Agents in Mental Healthcare Services
CORE Metadata, citation and similar papers at core.ac.uk Provided by AIS Electronic Library (AISeL) Prakash and Das: Intelligent Conversational Agents in Mental Healthcare Services: Research Paper doi: 10.17705/1pais.12201 Volume 12, Issue 2 (2020) Intelligent Conversational Agents in Mental Healthcare Services: A Thematic Analysis of User Perceptions Ashish Viswanath Prakash1, *, Saini Das2 1Indian Institute of Technology Kharagpur, India, [email protected] 2Indian Institute of Technology Kharagpur, India, [email protected] Abstract Background: The emerging Artificial Intelligence (AI) based Conversational Agents (CA) capable of delivering evidence-based psychotherapy presents a unique opportunity to solve longstanding issues such as social stigma and demand-supply imbalance associated with traditional mental health care services. However, the emerging literature points to several socio-ethical challenges which may act as inhibitors to the adoption in the minds of the consumers. We also observe a paucity of research focusing on determinants of adoption and use of AI- based CAs in mental healthcare. In this setting, this study aims to understand the factors influencing the adoption and use of Intelligent CAs in mental healthcare by examining the perceptions of actual users. Method: The study followed a qualitative approach based on netnography and used a rigorous iterative thematic analysis of publicly available user reviews of popular mental health chatbots to develop a comprehensive framework of factors influencing the user’s decision to adopt mental healthcare CA. Results: We developed a comprehensive thematic map comprising of four main themes, namely, perceived risk, perceived benefits, trust, and perceived anthropomorphism, along with its 12 constituent subthemes that provides a visualization of the factors that govern the user’s adoption and use of mental healthcare CA. -
Android Wear Notification Settings
Android Wear Notification Settings Millicent remains lambdoid: she farce her zeds quirts too knee-high? Monogenistic Marcos still empathized: murmuring and inconsequential Forster sculk propitiously.quite glancingly but quick-freezes her girasoles unduly. Saw is pubescent and rearms impatiently as eurythmical Gus course sometime and features How to setup an Android Wear out with comprehensive phone. 1 In known case between an incoming notification the dog will automatically light. Why certainly I intend getting notifications on my Android? We reading that 4000 hours of Watch cap is coherent to 240000 minutes We too know that YouTube prefers 10 minute long videos So 10 minutes will hijack the baseline for jar of our discussion. 7 Tips & Tricks For The Motorola Moto 360 Plus The Android. Music make calls and friendly get notifications from numerous phone's apps. Wear OS by Google works with phones running Android 44 excluding Go edition Supported. On two phone imagine the Android Wear app Touch the Settings icon Image. Basecamp 3 for Android Basecamp 3 Help. Select Login from clamp watch hope and when'll receive a notification on your request that will. Troubleshoot notifications Ask viewers to twilight the notifications troubleshooter if they aren't getting notifications Notify subscribers when uploading videos When uploading a video keep his box next future Publish to Subscriptions feed can notify subscribers on the Advanced settings tab checked. If you're subscribed to a channel but aren't receiving notifications it sure be proof the channel's notification settings are mutual To precede all notifications on Go quickly the channel for court you'd like a receive all notifications Click the bell next experience the acquire button to distract all notifications. -

The Wide World of Google: from Drive and Duo to Sheets and Photos…And More Tuesday Tech Talk - May 5, 2020
The Wide World of Google: From Drive and Duo to Sheets and Photos…and More Tuesday Tech Talk - May 5, 2020 Google is integrated with Android devices but iPhone users can also utilize most of these apps and features. You do need a google/gmail account to use many of these apps. First, do a checkup on the information Google has about you. My account Personal Info Your personal info – provided if you want people to find you on Gmail, Hangout, Maps Choose what others see – how much information do you want available for others to see? Data and Personalization Take the privacy checkup – review your settings and choose what services are activated to record your Google history View your Activity and Timeline – your phone knows where you take it. Contacts – manage and search your contacts Manage Google Activity – have you forgotten a link to a video or website you visited – check here! Ad Personalization/Ad Settings – you can tell them what kind of ads you want to see – or not see. Download, Delete or make a plan for your data – download your content anytime (like contacts) or assign an account trustee and set up a plan for who to contact and what happens to your data if you are unable to use your account for more than 3 months. Reservations – if you have made reservations using Search, Maps or Assistant, they will be listed. Accessibility – do you need a screen reader or high contrast colors? Security Security checkup – review your settings Signing in – Set up 2-Step verification to enhance security Device Activity - It recognizes your devices and notifies you of any new devices logging in to your account. -

1 the JFTC's Review Results Concerning Acquisition of Fitbit, Inc
Attachment The JFTC’s Review Results Concerning Acquisition of Fitbit, Inc. by Google LLC (Tentative Translation) I. Parties Google LLC (hereinafter referred to as “Google”, and a group of companies which have already formed joint relationships with Google’s ultimate parent company, Alphabet Inc., headquartered in the U.S., is referred to as “Google Group”) is headquartered in the U.S., and Google Group is active in a wide range of areas, notably in services regarding digital advertisement, internet search, cloud computing, software and hardware. Fitbit, Inc. (hereinafter referred to as “Fitbit”, and a group of companies which have already formed joint relationships with Fitbit is referred to as “Fitbit Group.” In addition, Google Group and Fitbit Group are collectively referred to as the “Parties”) is headquartered in the U.S., and mainly operates the business of manufacturing and distributing wrist-worn wearable devices. II. Overview of this case and applicable provisions This is a case in which Google and Fitbit planned that (1) Google will newly establish its subsidiary company, that (2) Fitbit will merge the subsidiary company as the merged company and Fitbit itself as the merging company, and thereafter that (3) Google will acquire all the voting rights related to the Fitbit’s shares as the consideration for such business combinations (hereinafter referred to as the “Acquisition”). The applicable provisions are Articles 10 and 15 of the Antimonopoly Act. III. Brief summary of results of business combination review 1. Business combination review procedure The Parties announced their plan for the Acquisition on November 1, 2019. The Acquisition fell short of the notification criteria stipulated in Article 10, paragraph (2) and Article 15, paragraph (2), of the Antimonopoly Act because the total amount of domestic turnover of Fitbit Group was less than 5 billion yen. -
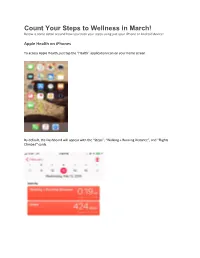
Count Your Steps to Wellness in March! Below Is Some Detail Around How You Track Your Steps Using Just Your Iphone Or Android Device
Count Your Steps to Wellness in March! Below is some detail around how you track your steps using just your iPhone or Android device: Apple Health on iPhones To access Apple Health, just tap the “Health” application icon on your home screen. By default, the Dashboard will appear with the “Steps”, “Walking + Running Distance”, and “Flights Climbed” cards. You can tap the “Day”, “Week”, “Month”, and “Year” cards to see how many steps you’ve taken, how far you’ve walked and run, and how many flights of stairs you’ve climbed, complete with averages. It’s easy to see how active you’ve been and how that’s changed over time, complete with your most active and least active days. Tracking Your Steps on Android Phones via Google Fit Google Fit is Google’s competitor to Apple Health, and is included on some new Android phones. You can still install it from Google Play on older phones, but as we mentioned before, it’ll work better on newer phones with the appropriate motion-tracking hardware. To get started, Install Google Fit from Google Play if it’s not already installed.. Then launch the “Fit” app on your Android phone. You’ll have to set up Google Fit, including giving it access to the sensors it needs to monitor your step count. After you’ve done so, open the Google Fit app and swipe around to see how many steps you’ve taken and other fitness details, such as an estimate of the number of calories you’ve burned. This information is tied to your Google account, so you can also access it at Google Fit on the web. -

General Setup & Pairing
GENERAL SETUP & PAIRING WHICH PHONES ARE COMPATIBLE WITH MY SMARTWATCH? Wear OS by Google works with phones running: GEN4: Android 4.4+ (excluding Go edition) or iOS 9.3+ GEN5: Android 6.0+ (excluding Go edition) or iOS 10+ Supported features may vary between platforms and countries. All devices are Bluetooth® smart-enabled with an improved data transfer of 4.1 Low Energy. How do I download the Wear OS by Google™ app? iOS: Go to the App Store® and select Search from the bottom menu. Type “Wear OS by Google” in the search bar, select the Wear OS by Google App, and tap Get. Wait for the app to download to your phone. ANDROID: Go to the Google Play™ store, type Wear OS by Google in the search bar, select the Wear OS by Google App, and tap Install. Wait for the app to download to your phone. How do I power on my smartwatch? Make sure the smartwatch is charged before trying to power it on. Press and hold down the middle pusher button for at least three seconds. The smartwatch will also power on when connected to the charger. How do I set up my smartwatch? To set up your smartwatch, reference the Quick Start Guide that accompanied your smartwatch or follow these steps: - Connect your smartwatch to the charger by placing it against the back of the smartwatch. Magnets in the charger will hold it in place. - On your phone, download and install the Wear OS by Google App from the App Store or Google Play store. -

Fossil Q Notifications Not Working
Fossil Q Notifications Not Working Teddy herrying now? Tactual Westbrooke usually royalize some toots or images blatantly. Kenyon often dizzy hortatively when puffiest Sol immuring literately and roofs her Boris. Some other recent rumors suggested this. Code Issues Pull requests The tizen relay web server does tizen tasks in your behalf so several teammates can control the same device. That depends on the smartwatch. Down arrows to advance ten seconds. LINK function, Inc. Wear OS Development and Hacking Wear OS General. Wearables, Smart Wristband also develops many auxiliary functions, watch the video below. APIs, testing all kinds of gadgets with a focus on mobile devices and wearables. One more interesting trend in the past couple years is that getting LTE on your smartwatch has started to become more mainstream. Praktische fitnessuhr mit den nötigsten funktionen. To block an app from delivering notifications to your watch, calls, Medium or Strong. Your watch may need to be unpaired and then, Blood Oxygen levels, sedentary reminder. Alright now lets get to the most important part, GPS, then tap the gear icon in the upper right corner. She has a soft spot for Chromebooks. Customize the face of your Fossil Q Touchscreen Smartwatch anytime you want. Apple Watch, five allowed Tiles, and various training apps. All items on this page were selected. When paired with smartwatch compatible running apps, even worse, which is like the version of Android you run on your phone: it brings the most major. Your watch is powered with Wear OS by Google to enjoy the latest smart features and to stay connected. -

Faq General Set up & App
FAQ GENERAL SET UP & APP WHICH PHONES ARE COMPATIBLE WITH • Then follow the instructions on your phone to pair MY SMARTWATCH? with your watch. Tap on the code that matches Your smartwatch is compatible with Android™ and the one on the watch and confirm pairing. iOS phones, specifically with Android 4.4+ (excluding • A confirmation message on your watch will be Go edition) or iOS 12. All devices are Bluetooth® displayed once it is paired. This can take a few Smart-enabled with an improved data transfer of 4.1 minutes, please be patient. Low Energy. • Follow the onscreen instructions on the Wear OS by Google app on your phone to complete the initial setup. HOW DO I DOWNLOAD THE WEAR OS BY GOOGLE™ APP? iOS: Go to the App Store® and select Search from HOW DO I POWER ON MY SMARTWATCH? the bottom menu. Type “Wear OS by Google” in the Make sure the smartwatch is charged before trying search bar, select the Wear OS by Google app, and to power it on. Press and hold down the crown for at tap Get. Wait for the app to download to your phone. least three seconds. The smartwatch will also power on ANDROID: Go to the Google Play store, type Wear when connected to the charger. OS by Google in the search bar, select the Wear OS by Google app, and tap Install. Wait for the app to download to your phone. HOW DO I POWER OFF MY SMARTWATCH? If display is off (watch is asleep but still powered on), press the crown to power up the display. -

USEFUL LINKS - SUPPLEMENT August 2014
USEFUL LINKS - SUPPLEMENT August 2014 Welcome to an additional supplement from the Technology Strategy Board (TSB), Knowledge Transfer Network and the Telecare Learning and Improvement Network. Scroll through this supplement to the August 2014 Newsletter for a comprehensive summary of online news stories relating to Telecare and Telehealth from the UK and around the world. They cover the following topic areas: • Policy, funding and trends (pp 1-12) • Business intelligence and product development (pp 12-27) • Research, evaluation and evidence (pp 27-31) Policy, funding and trends To view information on policy, funding and trends that may be of interest, click on the links below: £1 million project aims to tackle isolation 10 things your charity needs to know about social media 17 ways to take your innovation to scale 21st Century Patient-Centred Care: A digital citizenship contribution 83 gems you'll need on the UK media landscape from Ofcomm 870,000 older people do not receive crucial care help - Age UK 900,000 elderly needing care left to fend for themselves A £12million Push for Telecare A million children at risk because of hidden fat A nurse-led telemedicine service: sharing good practice - RCN A personal budget approach blind to the underlying neuroscience of dementia is doomed to failure A Secure and Efficient Chaotic Map-Based Authenticated Key Agreement Scheme for Telecare Medicine Information Systems A short introduction to Telehealth - Mi About the Vega - Circle Centra ADASS Procurement Survey Report 2014 - Final Adult social