Disappearing Hardware
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Building Blocks for Tomorrow's Mobile App Store
Building Blocks for Tomorrow’s Mobile App Store by Justin G. Manweiler Department of Computer Science Duke University Date: Approved: Romit Roy Choudhury, Supervisor Jeffrey S. Chase Landon P. Cox Victor Bahl Dissertation submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy in the Department of Computer Science in the Graduate School of Duke University 2012 Abstract (0984) Building Blocks for Tomorrow’s Mobile App Store by Justin G. Manweiler Department of Computer Science Duke University Date: Approved: Romit Roy Choudhury, Supervisor Jeffrey S. Chase Landon P. Cox Victor Bahl An abstract of a dissertation submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy in the Department of Computer Science in the Graduate School of Duke University 2012 Copyright c 2012 by Justin G. Manweiler All rights reserved Abstract In our homes and in the enterprise, in our leisure and in our professions, mobile computing is no longer merely “exciting;” it is becoming an essential, ubiquitous tool of the modern world. New and innovative mobile applications continue to inform, entertain, and surprise users. But, to make the daily use of mobile technologies more gratifying and worthwhile, we must move forward with new levels of sophistication. The Mobile App Stores of the future must be built on stronger foundations. This dissertation considers a broad view of the challenges and intuitions behind a diverse selection of such new primitives. Some of these primitives will mitigate exist- ing and fundamental challenges of mobile computing, especially relating to wireless communication. Others will take an application-driven approach, being designed to serve a novel purpose, and be adapted to the unique and varied challenges from their disparate domains. -

English Version
Deloitte Perspective Deloitte Can the Punch Bowl Really Be Taken Away? The Future of Shared Mobility in China Perspective Gradual Reform Across the Value Chain 2018 (Volume VII) 2018 (Volume VII) 2018 (Volume About Deloitte Global Deloitte refers to one or more of Deloitte Touche Tohmatsu Limited, a UK private company limited by guarantee (“DTTL”), its network of member firms, and their related entities. DTTL and each of its member firms are legally separate and independent entities. DTTL (also referred to as “Deloitte Global”) does not provide services to clients. Please see www.deloitte.com/about to learn more about our global network of member firms. Deloitte provides audit & assurance, consulting, financial advisory, risk advisory, tax and related services to public and private clients spanning multiple industries. Deloitte serves nearly 80 percent of the Fortune Global 500® companies through a globally connected network of member firms in more than 150 countries and territories bringing world-class capabilities, insights, and high-quality service to address clients’ most complex business challenges. To learn more about how Deloitte’s approximately 263,900 professionals make an impact that matters, please connect with us on Facebook, LinkedIn, or Twitter. About Deloitte China The Deloitte brand first came to China in 1917 when a Deloitte office was opened in Shanghai. Now the Deloitte China network of firms, backed by the global Deloitte network, deliver a full range of audit & assurance, consulting, financial advisory, risk advisory and tax services to local, multinational and growth enterprise clients in China. We have considerable experience in China and have been a significant contributor to the development of China's accounting standards, taxation system and local professional accountants. -

Toward Building a Safe, Secure, and Easy-To-Use Internet of Things
IOT CONNECTION Toward Building a Safe, Secure, and Easy-to-Use Sal glances at the display near her office door and sees that her next meeting is in 10 Internet of Things minutes. One participant is out of town and the other two people are running late, but the meeting room is still occupied Infrastructure by several people. The display also suggests it might be a Yuvraj Agarwal and Anind K. Dey, Carnegie Mellon University good time to get coffee because the lines are short at the cafe downstairs. Her good friend Joe Carnegie Mellon University is leading a happens to be at the cafe, too. multi-institutional effort to build an open Sal checks an app she recently built and sees that the coffee is infrastructure to support the Internet of Things. freshly brewed. “That simplifies things,” she thinks to herself as she heads toward the cafe. safe and secure world enabled by the Inter- This is the unique promise of a successful IoT, and is net of Things (IoT) promises to lead to truly what we are aiming for with GIoTTO, the IoT program connected environments, where people and at Carnegie Mellon University (CMU) named after the things collaborate to improve the overall famous Renaissance painter. qualityA of life. The IoT will give us actionable informa- tion at our fingertips, without us having to ask for it or NEED FOR AN OPEN INFRASTRUCTURE even recognizing that it might be needed. Consider this Although numerous commercial and academic programs example that combines many simple uses of the IoT to cu- focus on building IoT systems, it’s clear that for any IoT mulatively form an omnipotent assistant: stack to be widely adopted, it must be open—without a 40 COMPUTER PUBLISHED BY THE IEEE COMPUTER SOCIETY 0018-9162/16/$33.00 © 2016 IEEE EDITOR ROY WANT Google; [email protected] singular organization claiming own- ership. -

Passing the Torch
From the Editor in Chief Editor in Chief: M. Satyanarayanan ■ Carnegie Mellon University ■ [email protected] Passing the Torch M. Satyanarayanan his issue marks the end of my sec- a highly portable information appliance LOOKING BACK, T ond two-year term as editor in that transforms nearby displays and LOOKING FORWARD chief. I am delighted to introduce my input devices into a transient personal- In August 2001, 10 years after the successor, Roy Want of Intel Research, computing environment. Roy has pub- publication of Mark Weiser’s seminal who will begin his term on 1 January lished extensively over his research career paper introducing the concept of ubiq- 2006. I will continue to serve as active and has over 50 patents to his credit. uitous computing,1 I summarized the editor in chief until that time and will It is hard to imagine a person more field’s progress and reflected on the work closely with Roy to ensure a qualified than Roy to be the next editor challenges ahead in a paper entitled smooth and efficient transition. My in chief of IEEE Pervasive Computing. “Pervasive Computing: Vision and involvement with this publication will In 2001, he was part of the founding edi- Challenges.”2 Looking back, it is grat- continue even after I step down, as I will torial board that created this publication ifying to see how much progress has remain on the editorial board. occurred in just four short years. Many forces have converged to make IN GOOD HANDS It is hard to this progress possible, one of which was Roy received his PhD from Cambridge imagine a substantial industry investment in prod- University in 1988, under the supervision person more uct development relevant to mobile and of Roger Needham. -
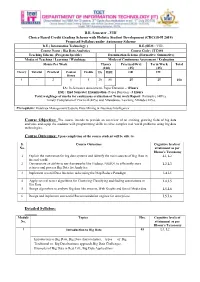
(CBCGS-H 2019) Proposed Syllabus Under Autonomy Scheme
B.E. Semester –VIII Choice Based Credit Grading Scheme with Holistic Student Development (CBCGS-H 2019) Proposed Syllabus under Autonomy Scheme B.E.( Information Technology ) B.E.(SEM : VIII) Course Name : Big Data Analytics Course Code : ITC801 Teaching Scheme (Program Specific) Examination Scheme (Formative/ Summative) Modes of Teaching / Learning / Weightage Modes of Continuous Assessment / Evaluation Hours Per Week Theory Practical/Oral Term Work Total (100) (25) (25) Theory Tutorial Practical Contact Credits IA ESE OR TW Hours 4 - 2 6 5 20 80 25 25 150 IA: In-Semester Assessment- Paper Duration – 1Hours ESE : End Semester Examination- Paper Duration - 3 Hours Total weightage of marks for continuous evaluation of Term work/Report: Formative (40%), Timely Completion of Practical (40%) and Attendance /Learning Attitude (20%). Prerequisite: Database Management System, Data Mining & Business Intelligence Course Objective: The course intends to provide an overview of an exciting growing field of big data analytics and equip the students with programming skills to solve complex real world problems using big data technologies. Course Outcomes: Upon completion of the course student will be able to: S. Course Outcomes Cognitive levels of No. attainment as per Bloom’s Taxonomy 1 Explain the motivation for big data systems and identify the main sources of Big Data in L1, L2 the real world. 2 Demonstrate an ability to use frameworks like Hadoop, NOSQL to efficiently store L2,L3 retrieve and process Big Data for Analytics. 3 Implement several Data Intensive tasks using the Map Reduce Paradigm L4,L5 4 Apply several newer algorithms for Clustering Classifying and finding associations in L4,L5 Big Data 5 Design algorithms to analyze Big data like streams, Web Graphs and Social Media data. -

Curriculum Vitae: Roy Want
Curriculum Vitae: Roy Want E-mail: roywant AT google.com ; roywant AT acm.org Google Inc, Mail-Stop: US-MTV-B43 1600 Amphitheatre Parkway Mountain View, CA 94043, USA Office/Cell: (650) 691 3600 Date: January, 2019 Up-to-date CV: http://www.roywant.com/cv/vita.htm Research Interests Mobile & ubiquitous computing, location & context-aware systems, electronic tagging(RFID/NFC/BLE), hardware design, electronic commerce, smart cards, distributed systems, multimedia systems, cellular automata, novel UI, and MEMS. Professional ACM Fellow: 2005, and ACM (Association of Computer Machinery) member since 1996. IEEE Fellow: 2005 and IEEE (Institute for Electrical and Electronic Engineers) member since 1991. Lillian Gilbreth lectureship, National Academy of Engineering (NAE), Washington DC, Oct 12th, 2003 Education Ph.D. Cambridge University UK, Churchill College, Computer Science, Advisor: Roger Needham, 1983-88 o Thesis title: "Reliable Management of Voice in a Distributed System" BA hons. Cambridge University UK, Churchill College, Nat. Science/Computer Science, Tutor: Frank King, 1980-83 o Dissertation title: “A Local Area Network (LAN) Based on the Domestic Mains Supply” High School: William Ellis Grammar School, London UK, 1972-79 Experience Google Inc. (2011-present) o Senior Research Scientist: Google Research and Android Location & Context Team Intel Corporation (2001-2011) o Senior Principal Engineer (SPE) 2008-2011 -Assoc. Director: ILSC (2009-10) & Director (NPL) 2010-11 o Principal Engineer (PE) 2000-2007 Xerox - Palo Alto Research Center (PARC). Computer Science Laboratory (CSL). 1991 - 2001 (reporting to Mark Weiser, Laboratory Manager for CSL; CTO) o Principal Scientist 2000-2001 o Area Manager for Embedded Systems Area 1992-1999 o Member of Research Staff II 1991-1992. -

Solving Human Centric Challenges in Ambient Intelligence Environments to Meet Societal Needs
Solving Human Centric Challenges in Ambient Intelligence Environments to Meet Societal Needs A Dissertation Presented to the Faculty of the School of Engineering and Applied Science University of Virginia In Partial Fulfillment of the requirements for the Degree Doctor of Philosophy (Computer Science) by Erin Griffiths December 2019 © 2019 Erin Griffiths Approval Sheet This dissertation is submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy (Computer Science) Erin Griffiths This dissertation has been read and approved by the Examining Committee: Kamin Whitehouse, Adviser Jack Stankovic, Committee Chair Mary Lou Soffa A.J. Brush John Lach Accepted for the School of Engineering and Applied Science: Dean, School of Engineering and Applied Science December 2019 i To everyone who has helped me along the way. ii Abstract In the world today there exists a large number of problems that are of great societal concern, but suffer from a problem called the tragedy of the commons where there isn`t enough individual incentive for people to change their behavior to benefit the whole. One of the biggest examples of this is in energy consumption where research has shown that we can reduce 20-50% of the energy used in buildings if people would consistently modify their behavior. However, consistent behavior modification to meet societal goals that are often low priority on a personal level is often prohibitively difficult in the long term. Even systems design to assist in meeting these needs may be unused or disabled if they require too much effort, infringe on privacy, or are frustratingly inaccurate. -

Redefine Work: the Untapped Opportunity for Expanding Value
A report from the Deloitte Center for the Edge Redefine work The untapped opportunity for expanding value Deloitte Consulting LLP’s Human Capital practice focuses on optimizing and sustaining organiza- tional performance through their most important asset: their workforce. We do this by advising our clients on a core set of issues including: how to successfully navigate the transition to the future of work; how to create the “simply irresistible” experience; how to activate the digital orga- nization by instilling a digital mindset—and optimizing their human capital balance sheet, often the largest part of the overall P&L. The practice’s work centers on transforming the organization, workforce, and HR function through a comprehensive set of services, products, and world-class Bersin research enabled by our proprietary Human Capital Platform. The untapped opportunity for expanding value Contents Introduction: Opportunity awaits—down a different path | 2 A broader view of value | 4 Redefining work everywhere: What does the future of human work look like? | 6 Breaking from routine: Work that draws on human capabilities | 11 Focusing on value for others | 18 Making work context-specific | 21 Giving and exercising latitude | 25 How do we get started? | 31 Endnotes | 34 1 Redefine work Introduction: Opportunity awaits—down a different path Underneath the understandable anxiety about the future of work lies a significant missed opportunity. That opportunity is to return to the most basic question of all: What is work? If we come up with a creative answer to that, we have the potential to create significant new value for the enterprise. -

SOUL: an Edge-Cloud System for Mobile Applications in a Sensor-Rich World
2016 IEEE/ACM Symposium on Edge Computing SOUL: An Edge-cloud System for Mobile Applications in a Sensor-rich World Minsung Jang∗, HyunJong Lee†, Karsten Schwan‡, Ketan Bhardwaj‡ ∗AT&T Labs - Research, [email protected] †University of Michigan, [email protected] ‡Georgia Institute of Technology, {karsten, ketanbj}@gatech.edu Abstract—With the Internet of Things, sensors are becoming In order for such apps to efficiently interact with and ever more ubiquitous, but interacting with them continues manage the dynamic sets of currently accessible sensors with to present numerous challenges, particularly for applications the associated actuators and software services, SOUL (Sensors running on resource-constrained devices like smartphones. The Of Ubiquitous Life) SOUL abstractions in this paper address two issues faced • by such applications: (1) access to sensors with the levels of externalizes sensor & actuator interactions and process- convenience needed for their ubiquitous, dynamic use, and only ing from the resource-constrained device to edge- and by parties authorized to do so, and (2) scalability in sensor remote-cloud resources, to leverage their computational and access, given today’s multitude of sensors. Toward this end, storage abilities for running the complex sensor processing SOUL, first, introduces a new abstraction for the applications to functionality; transparently and uniformly access both on-device and ambient • sensors with associated actuators. Second, potentially expensive automates reconfiguration of these interactions when sensor-related processing needs not just occur on smartphones, better-matched sensors and actuators become physically but can also leverage edge- and remote-cloud resources. Finally, available; SOUL provides access control methods that permit users to easily • supports existing sensor-based applications allowing define access permissions for sensors, which leverages users’ social ties and captures the context in which access requests them to use SOUL’s capabilities without requiring modi- are made. -

Ambient Intelligence
Ambient intelligence Ambient intelligence is closely related to the long term vision of an intelligent service system in which technolo- gies are able to automate a platform embedding the re- quired devices for powering context aware, personalized, adaptive and anticipatory services. Where in other me- dia environment the interface is clearly distinct, in an ubiquitous environment 'content' differs. Artur Lugmayr defined such a smart environment by describing it as ambient media. It is constituted of the communication of information in ubiquitous and pervasive environments. The concept of ambient media relates to ambient media form, ambient media content, and ambient media tech- nology. Its principles have been established by Artur Lug- mayr and are manifestation, morphing, intelligence, and experience.[1][2] An (expected) evolution of computing from 1960–2010. A typical context of ambient intelligence environment is In computing, ambient intelligence (AmI) refers to a Home environment (Bieliková & Krajcovic 2001). electronic environments that are sensitive and respon- sive to the presence of people. Ambient intelligence is a vision on the future of consumer electronics, 1 Overview telecommunications and computing that was originally developed in the late 1990s for the time frame 2010– 2020. In an ambient intelligence world, devices work in More and more people make decisions based on the effect concert to support people in carrying out their everyday their actions will have on their own inner, mental world. life activities, tasks and rituals in an easy, natural way us- This experience-driven way of acting is a change from ing information and intelligence that is hidden in the net- the past when people were primarily concerned about the work connecting these devices (see Internet of Things). -

Design for Use
Research-Technology Management ISSN: 0895-6308 (Print) 1930-0166 (Online) Journal homepage: http://www.tandfonline.com/loi/urtm20 Design for Use Don Norman & Jim Euchner To cite this article: Don Norman & Jim Euchner (2016) Design for Use, Research-Technology Management, 59:1, 15-20 To link to this article: http://dx.doi.org/10.1080/08956308.2016.1117315 Published online: 08 Jan 2016. Submit your article to this journal View related articles View Crossmark data Full Terms & Conditions of access and use can be found at http://www.tandfonline.com/action/journalInformation?journalCode=urtm20 Download by: [Donald Norman] Date: 10 January 2016, At: 13:57 CONVERSATIONS Design for Use An Interview with Don Norman Don Norman talks with Jim Euchner about the design of useful things, from everyday objects to autonomous vehicles. Don Norman and Jim Euchner Don Norman has studied everything from refrigerator the people we’re designing for not only don’t know about thermostats to autonomous vehicles. In the process, he all of these nuances; they don’t care. They don’t care how has derived a set of principles that govern what makes much effort we put into it, or the kind of choices we made, designed objects usable. In this interview, he discusses some or the wonderful technology behind it all. They simply care of those principles, how design can be effectively integrated that it makes their lives better. This requires us to do a into technical organizations, and how designers can work design quite differently than has traditionally been the case. as part of product development teams. -

Getmobile MOBILE COMPUTING & COMMUNICATIONS REVIEW
GetMobile MOBILE COMPUTING & COMMUNICATIONS REVIEW Volume 21, Issue 2 • June 2017 CONTENTS 3 Message from the Editor-in-Chief 16 22 (ALMOST) UNPUBLISHABLE HIGHLIGHTS 5 RESULTS 22 EmotionCheck: A Wearable Device 16 Experiences Deploying an to Regulate Anxiety through False EXPERIMENTAL METHODS Always-On Farm Network Heart Rate Feedback 5 How Do You Know If 85% Accuracy Is Good Enough for Your Application? 26 9 31 26 HemaApp: Noninvasive Blood Screening of Hemoglobin Using Smartphone Cameras MOBILE PLATFORMS 9 Beyond Reality: Head-Mounted 31 Who Are the Smartphone Users? Displays for Mobile Systems Identifying User Groups with Researchers Apps Usage Behaviors 35 Interpretable Machine Learning for Mobile Notification Management: An Overview of PrefMiner 35 2 GetMobile June 2017 | Volume 21, Issue 2 MESSAGE FROM THE EDITOR-IN-CHIEF CONTRIBUTORS EDITOR-IN-CHIEF IN THIS ISSUE, we highlight four papers Eyal de Lara, University of Toronto from ACM UbiComp 2016. MANAGING EDITOR Donna Paris “EmotionCheck: A Wearable Device DESIGNER JoAnn McHardy to Regulate Anxiety through False Heart SENIOR ADVISORS (Past Editors-in-Chief) Rate Feedback,” by Jean Costa, Alexander Paramvir Bahl, Microsoft Research T. Adams, Malte F. Jung, François Suman Banerjee, University of Wisconsin, Madison Guimbretière, and Tanzeem Choudhury, Srikanth Krishnamurthy, University of California, Riverside describes a device that generates subtle Jason Redi, BBN Technologies vibrations on the wrist to resemble a pulse, Mani Srivastava, University of California, Los Angeles which helps users regulate their anxiety Eyal de Lara Nitin Vaidya, University of Illinois, Urbana-Champaign through false feedback of a slow heart rate. SECTION EDITORS In “HemaApp: Noninvasive Blood Screening of Hemoglobin Ardalan Amiri Sami, University of California, Irvine Using Smartphone Cameras,” Edward Jay Wang, William Li, Doug Aruna Balasubramanian, Stony Brook University Nilanjan Banerjee, University of Maryland, Hawkins, Terry Gernsheimer, Colette Norby-Slycord, and Shwetak N.