The Biometric Student Identification Finger Scanning Process
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Experiment: Latent Fingerprinting
EXPERIMENT: DUSTED! Operating Guide Dusted! Visitors press their fingertips onto a clean Plexiglas sheet. Their fingerprints are then revealed as visitors dust over the print with fingerprint powder. OBJECTIVES: Visitors will learn that every person has a unique set of fingerprints. Visitors will understand how fingerprints are revealed on surfaces. SCIENCE TOPICS PROCESS SKILLS VOCABULARY Properties of Matter Observing Fingerprint Properties of Electrons Comparing/Contrasting Latent UNIT 7 CRIME SCENE CHEMISTRY U7.1 EXPERIENCING CHEMISTRY ©2006 OMSI EXPERIMENT: DUSTED!! Operating Guide Dusted! Procedure: 1. Always wear safety goggles. 2. Use the towel to clean and dry the plastic Plexiglas. 3. Firmly press one of your fingertips, fingerprint side down, anywhere on the Plexiglas. Try not to smudge your print. Can you see your print? 4. Take the same finger and dab it gently onto the oil sponge, then press firmly onto the Plexiglas near your other print. Can you see your print? 5. Pull the brush out of the powder container. 6. Carefully brush over where you left your fingerprints until you see clear prints. What do you see? Is one print more visible than the other? 7. Push the brush back into the powder container. 8. Take a piece of tape and press it down onto one of your prints and rub firmly. 9. Lift the tape off and place it onto a square of the black paper. U7.2 UNIT 7 CRIME SCENE CHEMISTRY EXPERIENCING CHEMISTRY ©2006 OMSI EXPERIMENT: DUSTED! Operating Guide Does all the powder lift with the tape? How does your lifted print compare to the original? Why do we leave fingerprints behind? How can we collect them? A Closer Look: In this experiment, you left your fingerprint on a Plexiglas surface. -

Nature Flaunts Her Glory
Volume 34, Number 1 ■ January, 2019 Center for the Study of the First Americans Department of Anthropology Texas A&M University 4352 TAMU College Station, TX 77843-4352 www.centerfirstamericans.com - Nature flaunts her glory Near Vik, Iceland, a geologic formation known as a columnar basalt rose spectacularly showcases University of Oregon anthropologist Jon Erlandson, who takes time off from his research on the California Channel Islands to explore Viking-age sites (and engage his Nordic roots). His principal goal is to marshal convincing evidence for the coastal-entry route, one of several competing hypotheses that explain how the First Americans entered North America. See part 1 of our series on how the First Americans got here on page 13. To learn more about Erlandson’s work and career, see his profile on page 17. Photo by Erik Erlandson he Center for the Study of the First Americans fosters research and public T interest in the Peopling of the Americas. The Center, an integral part of the Department of Anthropology at Texas A&M University, pro motes inter disciplinary scholarly dialogue among physical, geological, biological and social scientists. The Mammoth Trumpet, news magazine of the Center, seeks to involve you in the peopling of the Americas by report- ing on developments in all pertinent areas of knowledge. JoinJoin inin thethe SearchSearch for the First Americans! Become a member of the Center for the Study of the First Americans on Center publications plus additional benefits according to the level of and explore the origin, lifeways, artifacts, and other aspects of the membership support you choose. -

Fingerprint Capture Challenges and Opportunities
Fingerprint Capture Challenges and Opportunities Dr. Rama Krishnan IDENT - Biometrics Quality Lead Presentation Overview □ Importance of Fingerprint Quality • Impacts on identification system □ Fingerprint Capture Challenges • Factors that will affect/impact fingerprint capture process □ Fingerprint Capture Opportunities • Possible approaches/solutions to enhance fingerprint capture quality Importance of Fingerprint Quality in an AFIS System □ Fingerprint Quality Impact on AFIS •NIST studies have shown that image quality has a direct impact on identification match accuracy □ Poor Fingerprint Image Quality Can Have the Following Negative Impacts in an AFIS System such as US-VISIT •Potential missed identification/verification of a subject •Additional secondary workload process •Additional fingerprint examiner workload Factors of Poor Fingerprint Quality Physiological • Dry fingers due to natural aging process • Worn ridge structure due to occupation • Finer ridge structure specific to a demographic group Behavioral • Uncooperative subject • Nervous Subject Environmental • Humidity / Temperature • Seasonal Change • Ambient Light Operational • High Throughput/ Reduced Capture Time • Unclean Scanner Platen Technological • Application Graphical User Interface (GUI) • Ease of Scanner Use / Interaction Poor Quality Image Illustrations Dry Finger Moist Finger Light Print Dark Print Poor Finger Worn Ridge Placement Structure Image Quality – User Demographics □ Male – Female • Female subjects have worse image quality □ Right Hand – Left Hand 41,000 Subjects • Left hand fingerprint quality is worse than right 24,000 Males hand 17,000 Females □ By Age of Subject • Image Quality worsens as subject age increases Image Quality Assurance Monitoring/Reporting 1 Application Identifies if there is an application-specific image quality issue - scanner, fingerprint capture GUI etc. 2 Site/Terminal Identifies if there is a site/terminal/operator-specific image quality issue within the application. -

Government Institute of Forensic Science, Aurangabad M.Sc
DR. BABASAHEB AMBEDKAR MARATHWADA UNIVERSITY, AURANGABAD SYLLABUS Of M.Sc. II (Semester III and IV) (Forensic Science) Effective from Academic Year 2013-2014 onwards 1 Government Institute Of Forensic Science, Aurangabad M.Sc. II Year (Finger print and Questioned Document) Preamble M.Sc.-II (Sem-III & IV) (Forensic Science) Ordinance ------------:- Title of the Program: - M.Sc.-II (Sem-III & IV) (Forensic Science) Ordinance ------------:-- Eligibility: - M.Sc.-I (Forensic Science) Regulation no. ----------- : Specializations :- Four Specializations viz. Finger print and Questioned Document, Forensic Chemistry and Toxicology, Forensic Biology, Serology and DNA Finger Printing, Cyber Space, IT Security and Cyber Forensic may be offered subject to the availability of students as mentioned in the preceding Para/ regulation. Regulation no. -----------:- Minimum intake capacity for each specialization: - There shall be minimum 25% of the intake capacity of the students for each specialization. Regulation no. ----------- :-Allotment of specialization :- The specialization to the students will be allotted on the basis of choice and merit (M.Sc.-I) of the students. However, if the criterion of minimum intake capacity for a particular specialization as mentioned above is not full filled, in such case the students will be diverted to other specialization strictly based on the marks obtained by him/her at M.Sc.-I examination. In such situation the decision of the Head of the concerned Institution shall be final. Regulation no.-------------- :- Course structure Each semester will have four theory papers and two theory based practical papers. In the fourth semester students will carry out Dissertation instead of one practical paper. Each paper shall be of 75 marks. -

L-1 Identity Solutions Fingerprint Reader
L-1 Identity Solutions Fingerprint Reader Savance Phone: 248-478-2555 | Fax: 248-478-3270 www.eioboard.com | [email protected] | www.savance.com © 2014 L-1 Identity Solutions Fingerprint Reader Table of Contents Fingerprint Reader Hardware Installation (4G V-Flex) 3 Fingerprint Reader Hardware Installation (4G V-Flex Lite) 5 Kiosk/Punch RS-232 Wiring Installation (Option 1) 9 Kiosk/Punch RS-485 Wiring Installation (Option 2) 13 Infinias Door Module Wiegand Wiring Installation (Option 3) 14 SecureAdmin Software Installation 19 SecureAdmin Software Configuration 30 EIOBoard Kiosk Software Configuration 37 Savance EIOBoard • www.eioboard.com • Phone: 248-478-2555 • Fax: 248-478-3270 2 1111 W. Oakley Park Rd., Ste 103 Commerce Township, MI 48390 L-1 Identity Solutions Fingerprint Reader Fingerprint Reader Hardware Installation (4G V-Flex) Here are the instructions for setting up the fingerprint reader to the computer. This applies to the 4G V-Flex model only. 1. Unbox your L-1 Identity Solutions Fingerprint Reader. 2. Connect the power adapter into the back of the unit in the round connector. Plug the other end into the wall. The unit’s lights should turn on. Savance EIOBoard • www.eioboard.com • Phone: 248-478-2555 • Fax: 248-478-3270 3 1111 W. Oakley Park Rd., Ste 103 Commerce Township, MI 48390 L-1 Identity Solutions Fingerprint Reader 3. One option for communicating between the fingerprint reader and the SecureAdmin fingerprint software is to use an Ethernet cable. You would plug one end of the Ethernet cable into the back of the unit, and the other end into a router or switch on your network. -

The Fingerprint Sourcebook
CHAPTER HISTORY Jeffery G. Barnes CONTENTS 3 1.1 Introduction 11 1.6 20th Century 3 1.2 Ancient History 17 1.7 Conclusion 4 1.3 221 B.C. to A.D. 1637 17 1.8 Reviewers 5 1.4 17th and 18th Centuries 17 1.9 References 6 1.5 19th Century 18 1.10 Additional Information 1–5 History C H A P T E R 1 CHAPTER 1 HISTORY 1.1 Introduction The long story of that inescapable mark of identity has Jeffery G. Barnes been told and retold for many years and in many ways. On the palm side of each person’s hands and on the soles of each person’s feet are prominent skin features that single him or her out from everyone else in the world. These fea- tures are present in friction ridge skin which leaves behind impressions of its shapes when it comes into contact with an object. The impressions from the last finger joints are known as fingerprints. Using fingerprints to identify indi- viduals has become commonplace, and that identification role is an invaluable tool worldwide. What some people do not know is that the use of friction ridge skin impressions as a means of identification has been around for thousands of years and has been used in several cultures. Friction ridge skin impressions were used as proof of a person’s identity in China perhaps as early as 300 B.C., in Japan as early as A.D. 702, and in the United States since 1902. 1.2 Ancient History Earthenware estimated to be 6000 years old was discov- ered at an archaeological site in northwest China and found to bear clearly discernible friction ridge impressions. -
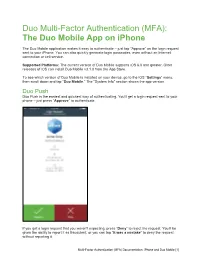
(MFA): the Duo Mobile App on Iphone
Duo Multi-Factor Authentication (MFA): The Duo Mobile App on iPhone The Duo Mobile application makes it easy to authenticate – just tap “Approve” on the login request sent to your iPhone. You can also quickly generate login passcodes, even without an Internet connection or cell service. Supported Platforms: The current version of Duo Mobile supports iOS 6.0 and greater. Older releases of iOS can install Duo Mobile v3.1.0 from the App Store. To see which version of Duo Mobile is installed on your device, go to the iOS “Settings” menu, then scroll down and tap “Duo Mobile.” The "System Info" section shows the app version. Duo Push Duo Push is the easiest and quickest way of authenticating. You'll get a login request sent to your phone – just press “Approve” to authenticate. If you get a login request that you weren't expecting, press “Deny” to reject the request. You’ll be given the ability to report it as fraudulent, or you can tap “It was a mistake” to deny the request without reporting it. Multi-Factor Authentication (MFA) Documentation: iPhone and Duo Mobile [1] Touch ID Duo Mobile for iOS also supports Touch ID for Duo Push-based logins; an additional layer of security to verify your users’ identities. If you're using a Touch ID capable iOS device, you'll see a Touch ID prompt each time you authenticate via Duo Mobile (if required by your administrator). If you're not able to scan your fingerprint using the TouchID sensor you can also approve the Duo authentication request using the device's passcode (the same one you use on the iOS lock screen). -

Security and Accuracy of Fingerprint-Based Biometrics: a Review
S S symmetry Review Security and Accuracy of Fingerprint-Based Biometrics: A Review Wencheng Yang 1,* , Song Wang 2 , Jiankun Hu 3, Guanglou Zheng 1 and Craig Valli 1 1 Security Research Institute, Edith Cowan University, Joondalup, WA 6207, Australia; [email protected] (G.Z.); [email protected] (C.V.) 2 Department of Engineering, La Trobe University, Victoria 3083, Australia; [email protected] 3 School of Engineering and Information Technology, University of New South Wales, Canberra, ACT 2600, Australia; [email protected] * Correspondence: [email protected]; Tel.: +61-8-6304-5210 Received: 2 December 2018; Accepted: 23 January 2019; Published: 28 January 2019 Abstract: Biometric systems are increasingly replacing traditional password- and token-based authentication systems. Security and recognition accuracy are the two most important aspects to consider in designing a biometric system. In this paper, a comprehensive review is presented to shed light on the latest developments in the study of fingerprint-based biometrics covering these two aspects with a view to improving system security and recognition accuracy. Based on a thorough analysis and discussion, limitations of existing research work are outlined and suggestions for future work are provided. It is shown in the paper that researchers continue to face challenges in tackling the two most critical attacks to biometric systems, namely, attacks to the user interface and template databases. How to design proper countermeasures to thwart these attacks, thereby providing strong security and yet at the same time maintaining high recognition accuracy, is a hot research topic currently, as well as in the foreseeable future. -

J. R. MCNEILL AHA Presidential Address Peak Document and the Future of History
Downloaded from https://academic.oup.com/ahr/article-abstract/125/1/1/5721569 by Loyola University Chicago user on 03 March 2020 J. R. MCNEILL AHA Presidential Address Peak Document and the Future of History J. R. MCNEILL Downloaded from https://academic.oup.com/ahr/article-abstract/125/1/1/5721569 by Loyola University Chicago user on 03 March 2020 SOME YEARS AGO,IHAD the good fortune to join a small troop of geologists tramping around northeastern Iceland on the trail of a jökulhlaup.Tofind traces of a jökulhlaup, you hunt for rounded “erratics.” In Iceland, those erratics—boulders that look out of place—with craggy edges were probably pushed along by glaciers, and those with rounded edges probably tumbled into position in giant floods that resulted when volca- nic eruptions melted ice dams holding back sub-glacial lakes—in other words, in a jökulhlaup. My colleagues and I focused on erratics tossed around by a monster flood that, it seems, for two or three days had carried water equivalent to one hundred times the av- erage flow of the Amazon.1 By chiseling off chips from each boulder and sending them to a lab for something called cosmogenic radionuclide exposure dating, we learned that this jökulhlaup happened about seven to ten thousand years ago, a keen disappointment to me.2 I was hoping for a date recent enough to register in the human history of Ice- land, which began only about 1,150 years ago, and for a research project to which his- torians might be able to contribute. -

Wescott TX State CV Aug 2020
Wescott CV (PPS 8.10 Form 1A) Updated: 07/20/2020 TEXAS STATE VITA I. Academic/Professional Background A. Name and Title Daniel J. Wescott, Professor of Anthropology and Director of the Forensic Anthropology Center at Texas State (FACTS) B. Educational Background Doctor of Philosophy, 2001, University of Tennessee-Knoxville, Anthropology (Biological), Structural Variation in the Humerus and Femur in the American Great Plains and Adjacent Regions: Differences in Subsistence Strategy and Physical Terrain Master of Arts, 1996, Wichita State University, Anthropology, Effect of Age on Sexual Dimorphism in the Adult Cranial Base and Upper Cervical Region Bachelor of Arts, 1994, Wichita State University, Anthropology with minors in Biology and Chemistry, Magna Cum Laude C. University Experience Professor: Department of Anthropology, Texas State University, September 2017 - present Associate Professor: Department of Anthropology, Texas State University, September 2011 – August 2017 (Tenure: September 1, 2014) Senior Lecturer: Department of Biological Sciences, Florida International University, August 2010 – May 2011 Lecturer: Department of Biological Sciences, Florida International University, August 2009 – August 2010 Faculty: International Forensic Research Institute, Florida International University, May 2010 – May 2011 Research Associate: Department of Anthropology, Florida Atlantic University, January 2010 – May 2011 Associate Professor: Department of Anthropology, University of Missouri-Columbia, May 2009 (Tenure: May 2009) Assistant Professor: -

Exact Same DNA
DNA, or Deoxyribonucleic Acid, is the genetic material in our cells. • No two people (except identical twins) have the exact same DNA. DNA patterns from four sets of twins – which are identical? DNA fingerprinting is also known as DNA profiling. It is a technique used by scientists to distinguish between individuals of the same species using only samples of their DNA. i. The process of DNA fingerprinting was invented by English geneticist Alec Jeffreys at the University of Leicester in 1985. DNA fingerprinting has been used to help solve crimes by linking suspects to crimes and by helping identify bodies of victims. In addition to crime investigation, DNA fingerprinting can also be used to: 1.establish paternity and parentage DNA paternity testing can indicate that a man is highly likely to be the father with about 99.9% accuracy or that he is excluded as being the father with 100% accuracy. In addition to crime investigation, DNA fingerprinting can also be used to: 1.establish paternity and parentage 2.identify victims of war and large scale disasters 3.study biodiversity of species 4.track genetically modified crops 5.settle immigration disputes Most lab techniques used for DNA fingerprinting were not intended for these purposes, but instead were developed for use in the medical field for diagnosis and treatment of diseases. Small amounts of biological evidence left at crime scenes, called trace evidence, are the source of DNA needed for DNA fingerprinting. • Biological evidence includes saliva, blood, semen, skin, hair roots, body tissue cells, and even urine. DNA is a nucleic acid, found in chromosomes, in the nucleus of your cells. -

Personal Mobile Banking - Setting up Touch Id® & Fingerprint Login
PERSONAL MOBILE BANKING - SETTING UP TOUCH ID® & FINGERPRINT LOGIN Keeping customer information confidential and secure is a vital part of our responsibility to you and we take this responsibility seriously. We offer touch login with our Umpqua Bank Mobile Banking app for select devices to keep your mobile access simple and secure. Remember, in order to use touch login with our app, you must first have the feature set up on your device. APPLE TOUCH ID® Log in to Mobile Banking Make sure you have downloaded our Umpqua Bank Mobile Banking app to your Apple device. When you log in to the app, use your existing Login ID and Password. You must select to Register Device during this or a prior login from your mobile device. Touch ID Enrollment 1. If your app is enabled for Touch ID, the app displays the Touch ID fingerprint prompt to authenticate into the app. If it doesn’t display, tap Touch ID from under the Log in button. 2. If your app is not enabled, select Touch ID from under the Log in button to enroll. 3. The What Is This Feature page will display. Review message and select Enroll Now. 1 20181215 TOUCH ID ENROLLMENT, CONTINUED 4. You will be prompted to re-enter your Login ID and Password to confirm and authorize activation of Touch ID. Then tap Authorize. 5. When prompted, touch your finger to the Home button (use the finger you normally use for Touch ID authentication). 6. Once your fingerprint is authenticated, the Touch ID option in Security Preferences will show as On.