A Comparative Study of Homomorphic and Searchable Encryption Schemes for Cloud Computing
Total Page:16
File Type:pdf, Size:1020Kb
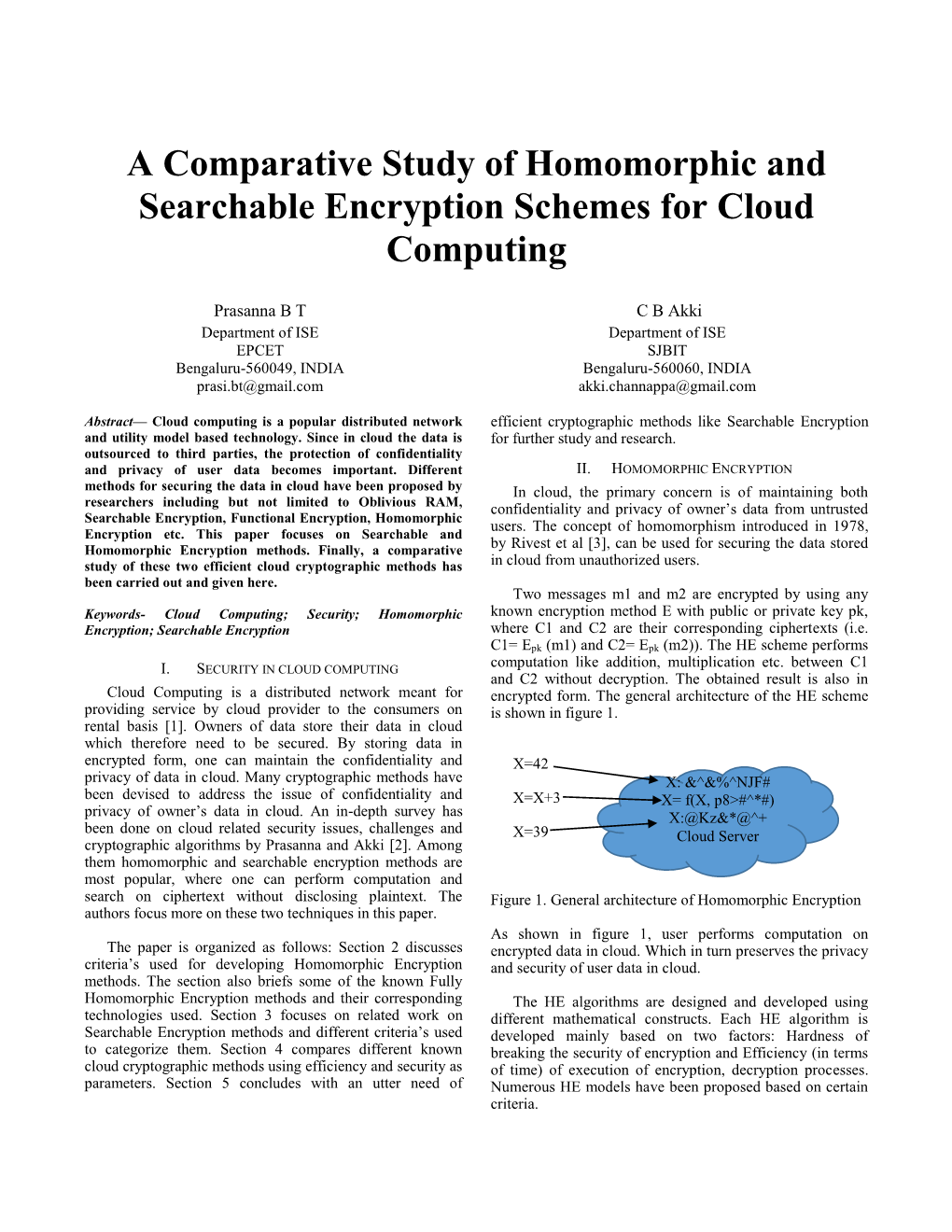
Load more
Recommended publications
-

Practical Homomorphic Encryption and Cryptanalysis
Practical Homomorphic Encryption and Cryptanalysis Dissertation zur Erlangung des Doktorgrades der Naturwissenschaften (Dr. rer. nat.) an der Fakult¨atf¨urMathematik der Ruhr-Universit¨atBochum vorgelegt von Dipl. Ing. Matthias Minihold unter der Betreuung von Prof. Dr. Alexander May Bochum April 2019 First reviewer: Prof. Dr. Alexander May Second reviewer: Prof. Dr. Gregor Leander Date of oral examination (Defense): 3rd May 2019 Author's declaration The work presented in this thesis is the result of original research carried out by the candidate, partly in collaboration with others, whilst enrolled in and carried out in accordance with the requirements of the Department of Mathematics at Ruhr-University Bochum as a candidate for the degree of doctor rerum naturalium (Dr. rer. nat.). Except where indicated by reference in the text, the work is the candidates own work and has not been submitted for any other degree or award in any other university or educational establishment. Views expressed in this dissertation are those of the author. Place, Date Signature Chapter 1 Abstract My thesis on Practical Homomorphic Encryption and Cryptanalysis, is dedicated to efficient homomor- phic constructions, underlying primitives, and their practical security vetted by cryptanalytic methods. The wide-spread RSA cryptosystem serves as an early (partially) homomorphic example of a public- key encryption scheme, whose security reduction leads to problems believed to be have lower solution- complexity on average than nowadays fully homomorphic encryption schemes are based on. The reader goes on a journey towards designing a practical fully homomorphic encryption scheme, and one exemplary application of growing importance: privacy-preserving use of machine learning. -

A Survey on the Provable Security Using Indistinguishability Notion on Cryptographic Encryption Schemes
A SURVEY ON THE PROVABLE SECURITY USING INDISTINGUISHABILITY NOTION ON CRYPTOGRAPHIC ENCRYPTION SCHEMES A THESIS SUBMITTED TO THE GRADUATE SCHOOL OF APPLIED MATHEMATICS OF MIDDLE EAST TECHNICAL UNIVERSITY BY EMRE AYAR IN PARTIAL FULFILLMENT OF THE REQUIREMENTS FOR THE DEGREE OF MASTER OF SCIENCE IN CRYPTOGRAPHY FEBRUARY 2018 Approval of the thesis: A SURVEY ON THE PROVABLE SECURITY USING INDISTINGUISHABILITY NOTION ON CRYPTOGRAPHIC ENCRYPTION SCHEMES submitted by EMRE AYAR in partial fulfillment of the requirements for the degree of Master of Science in Department of Cryptography, Middle East Technical University by, Prof. Dr. Om¨ ur¨ Ugur˘ Director, Graduate School of Applied Mathematics Prof. Dr. Ferruh Ozbudak¨ Head of Department, Cryptography Assoc. Prof. Dr. Ali Doganaksoy˘ Supervisor, Cryptography, METU Dr. Onur Koc¸ak Co-supervisor, TUB¨ ITAK˙ - UEKAE, Istanbul˙ Examining Committee Members: Assoc. Prof. Dr. Murat Cenk Cryptography, METU Assoc. Prof. Dr. Ali Doganaksoy˘ Department of Mathematics, METU Assist. Prof. Dr. Fatih Sulak Department of Mathematics, Atılım University Date: I hereby declare that all information in this document has been obtained and presented in accordance with academic rules and ethical conduct. I also declare that, as required by these rules and conduct, I have fully cited and referenced all material and results that are not original to this work. Name, Last Name: EMRE AYAR Signature : v vi ABSTRACT A SURVEY ON THE PROVABLE SECURITY USING INDISTINGUISHABILITY NOTION ON CRYPTOGRAPHIC ENCRYPTION SCHEMES Ayar, Emre M.S., Department of Cryptography Supervisor : Assoc. Prof. Dr. Ali Doganaksoy˘ Co-Supervisor : Dr. Onur Koc¸ak February 2018, 44 pages For an encryption scheme, instead of Shannon’s perfect security definition, Goldwasser and Micali defined a realistic provable security called semantic security. -

On Notions of Security for Deterministic Encryption, and Efficient Constructions Without Random Oracles
A preliminary version of this paper appears in Advances in Cryptology - CRYPTO 2008, 28th Annual International Cryptology Conference, D. Wagner ed., LNCS, Springer, 2008. This is the full version. On Notions of Security for Deterministic Encryption, and Efficient Constructions without Random Oracles Alexandra Boldyreva∗ Serge Fehr† Adam O’Neill∗ Abstract The study of deterministic public-key encryption was initiated by Bellare et al. (CRYPTO ’07), who provided the “strongest possible” notion of security for this primitive (called PRIV) and con- structions in the random oracle (RO) model. We focus on constructing efficient deterministic encryption schemes without random oracles. To do so, we propose a slightly weaker notion of security, saying that no partial information about encrypted messages should be leaked as long as each message is a-priori hard-to-guess given the others (while PRIV did not have the latter restriction). Nevertheless, we argue that this version seems adequate for certain practical applica- tions. We show equivalence of this definition to single-message and indistinguishability-based ones, which are easier to work with. Then we give general constructions of both chosen-plaintext (CPA) and chosen-ciphertext-attack (CCA) secure deterministic encryption schemes, as well as efficient instantiations of them under standard number-theoretic assumptions. Our constructions build on the recently-introduced framework of Peikert and Waters (STOC ’08) for constructing CCA-secure probabilistic encryption schemes, extending it to the deterministic-encryption setting and yielding some improvements to their original results as well. Keywords: Public-key encryption, deterministic encryption, lossy trapdoor functions, leftover hash lemma, standard model. ∗ College of Computing, Georgia Institute of Technology, 266 Ferst Drive, Atlanta, GA 30332, USA. -

Formalizing Public Key Cryptography
Cryptography CS 555 Topic 29: Formalizing Public Key Cryptography 1 Recap • Key Management • Diffie Hellman Key Exchange • Password Authenticated Key Exchange (PAKEs) 2 Public Key Encryption: Basic Terminology • Plaintext/Plaintext Space • A message m c • Ciphertext ∈ ℳ • Public/Private Key Pair , ∈ ∈ 3 Public Key Encryption Syntax • Three Algorithms • Gen(1 , ) (Key-generation algorithm) • Input: Random Bits R Alice must run key generation • Output: , algorithm in advance an publishes the public key: pk • Enc ( ) (Encryption algorithm) pk ∈ • Decsk( ) (Decryption algorithm) • Input: Secret∈ key sk and a ciphertex c • Output: a plaintext message m Assumption: Adversary only gets to see pk (not sk) ∈ ℳ • Invariant: Decsk(Encpk(m))=m 4 Chosen-Plaintext Attacks • Model ability of adversary to control or influence what the honest parties encrypt. • Historical Example: Battle of Midway (WWII). • US Navy cryptanalysts were able to break Japanese code by tricking Japanese navy into encrypting a particular message • Private Key Cryptography 5 Recap CPA-Security (Symmetric Key Crypto) m0,1,m1,1 c1 = EncK(mb,1) m0,2,m1,2 c2 = EncK(mb,2) m0,3,m1,3 c3 = EncK(mb,3) … b’ Random bit b (negligible) s. t K = Gen(.) 1 Pr = + ( ) ∀ ∃ 2 6 ′ ≤ Chosen-Plaintext Attacks • Model ability of adversary to control or influence what the honest parties encrypt. • Private Key Crypto • Attacker tricks victim into encrypting particular messages • Public Key Cryptography • The attacker already has the public key pk • Can encrypt any message s/he wants! • CPA Security is critical! 7 CPA-Security (PubK , n ) Public Key:LR pk−cpa , A Π 1 1 = 0 1 , = 2 , 2 0 1 3 3 = 0 1 … b’ Random bit b (negligible) s. -

Arx: an Encrypted Database Using Semantically Secure Encryption
Arx: An Encrypted Database using Semantically Secure Encryption Rishabh Poddar Tobias Boelter Raluca Ada Popa UC Berkeley UC Berkeley UC Berkeley [email protected] [email protected] [email protected] ABSTRACT some of which are property-preserving by design (denoted In recent years, encrypted databases have emerged as a PPE schemes), e.g., order-preserving encryption (OPE) [8, promising direction that provides data confidentiality with- 9, 71] or deterministic encryption (DET). OPE and DET out sacrificing functionality: queries are executed on en- are designed to reveal the order and the equality relation crypted data. However, many practical proposals rely on a between data items, respectively, to enable fast order and set of weak encryption schemes that have been shown to leak equality operations. However, while these PPE schemes con- sensitive data. In this paper, we propose Arx, a practical fer protection in some specific settings, a series of recent and functionally rich database system that encrypts the data attacks [26, 37, 61] have shown that given certain auxiliary only with semantically secure encryption schemes. We show information, an attacker can extract significant sensitive in- that Arx supports real applications such as ShareLaTeX with formation from the order and equality relations revealed by a modest performance overhead. these schemes. These works demonstrate offline attacks in which the attacker steals a PPE-encrypted database and PVLDB Reference Format: analyzes it offline. Rishabh Poddar, Tobias Boelter, and Raluca Ada Popa. Arx: Leakage from queries refers to what an (online) attacker An Encrypted Database using Semantically Secure Encryption. PVLDB, 12(11): 1664-1678, 2019. -

Chapter 4 Symmetric Encryption
Chapter 4 Symmetric Encryption The symmetric setting considers two parties who share a key and will use this key to imbue communicated data with various security attributes. The main security goals are privacy and authenticity of the communicated data. The present chapter looks at privacy, Chapter ?? looks at authenticity, and Chapter ?? looks at providing both together. Chapters ?? and ?? describe tools we shall use here. 4.1 Symmetric encryption schemes The primitive we will consider is called an encryption scheme. Such a scheme speci¯es an encryption algorithm, which tells the sender how to process the plaintext using the key, thereby producing the ciphertext that is actually transmitted. An encryption scheme also speci¯es a decryption algorithm, which tells the receiver how to retrieve the original plaintext from the transmission while possibly performing some veri¯cation, too. Finally, there is a key-generation algorithm, which produces a key that the parties need to share. The formal description follows. De¯nition 4.1 A symmetric encryption scheme SE = (K; E; D) consists of three algorithms, as follows: ² The randomized key generation algorithm K returns a string K. We let Keys(SE) denote the set of all strings that have non-zero probability of be- ing output by K. The members of this set are called keys. We write K Ã$ K for the operation of executing K and letting K denote the key returned. ² The encryption algorithm E takes a key K 2 Keys(SE) and a plaintext M 2 f0; 1g¤ to return a ciphertext C 2 f0; 1g¤ [ f?g. -

Security II: Cryptography
Security II: Cryptography Markus Kuhn Computer Laboratory Lent 2012 { Part II http://www.cl.cam.ac.uk/teaching/1213/SecurityII/ 1 Related textbooks Jonathan Katz, Yehuda Lindell: Introduction to Modern Cryptography Chapman & Hall/CRC, 2008 Christof Paar, Jan Pelzl: Understanding Cryptography Springer, 2010 http://www.springerlink.com/content/978-3-642-04100-6/ http://www.crypto-textbook.com/ Douglas Stinson: Cryptography { Theory and Practice 3rd ed., CRC Press, 2005 Menezes, van Oorschot, Vanstone: Handbook of Applied Cryptography CRC Press, 1996 http://www.cacr.math.uwaterloo.ca/hac/ 2 Private-key (symmetric) encryption A private-key encryption scheme is a tuple of probabilistic polynomial-time algorithms (Gen; Enc; Dec) and sets K; M; C such that the key generation algorithm Gen receives a security parameter ` and outputs a key K Gen(1`), with K 2 K, key length jKj ≥ `; the encryption algorithm Enc maps a key K and a plaintext m message M 2 M = f0; 1g to a ciphertext message C EncK (M); the decryption algorithm Dec maps a key K and a ciphertext n C 2 C = f0; 1g (n ≥ m) to a plaintext message M := DecK (C); ` m for all `, K Gen(1 ), and M 2 f0; 1g : DecK (EncK (M)) = M. Notes: A \probabilistic algorithm" can toss coins (uniformly distributed, independent). Notation: assigns the output of a probabilistic algorithm, := that of a deterministic algorithm. A \polynomial-time algorithm" has constants a; b; c such that the runtime is always less than a · `b + c if the input is ` bits long. (think Turing machine) Technicality: we supply the security parameter ` to Gen here in unary encoding (as a sequence of ` \1" bits: 1`), merely to remain compatible with the notion of \input size" from computational ` complexity theory. -

Public Key Encryption with Equality Test in the Standard Model
Public Key Encryption with Equality Test in the Standard Model Hyung Tae Lee1, San Ling1, Jae Hong Seo2, Huaxiong Wang1, and Taek-Young Youn3 1 Division of Mathematical Sciences, School of Physical and Mathematical Sciences, Nanyang Technological University, Singapore fhyungtaelee,lingsan,[email protected] 2 Myongji University, Korea [email protected] 3 Electonics and Telecommunications Research Institute, Korea [email protected] Abstract. Public key encryption with equality test (PKEET) is a cryp- tosystem that allows a tester who has trapdoors issued by one or more users Ui to perform equality tests on ciphertexts encrypted using public key(s) of Ui. Since this feature has a lot of practical applications in- cluding search on encrypted data, several PKEET schemes have been proposed so far. However, to the best of our knowledge, all the existing proposals are proven secure only under the hardness of number-theoretic problems and the random oracle heuristics. In this paper, we show that this primitive can be achieved not only generically from well-established other primitives but also even with- out relying on the random oracle heuristics. More precisely, our generic construction for PKEET employs a two-level hierarchical identity-based encryption scheme, which is selectively secure against chosen plaintext attacks, a strongly unforgeable one-time signature scheme and a cryp- tographic hash function. Our generic approach toward PKEET has sev- eral advantages over all the previous works; it directly leads the first standard model construction and also directly implies the first lattice- based construction. Finally, we show how to extend our approach to the identity-based setting. -

Better Security for Deterministic Public-Key Encryption: the Auxiliary-Input Setting
Better Security for Deterministic Public-Key Encryption: The Auxiliary-Input Setting Zvika Brakerski1 and Gil Segev2 1 Department of Computer Science and Applied Mathematics Weizmann Institute of Science, Rehovot 76100, Israel [email protected] 2 Microsoft Research, Mountain View, CA 94043, USA [email protected] Abstract. Deterministic public-key encryption, introduced by Bellare, Boldyreva, and O'Neill (CRYPTO '07), provides an alternative to ran- domized public-key encryption in various scenarios where the latter ex- hibits inherent drawbacks. A deterministic encryption algorithm, how- ever, cannot satisfy any meaningful notion of security when the plaintext is distributed over a small set. Bellare et al. addressed this difficulty by requiring semantic security to hold only when the plaintext has high min-entropy from the adversary's point of view. In many applications, however, an adversary may obtain auxiliary infor- mation that is related to the plaintext. Specifically, when deterministic encryption is used as a building block of a larger system, it is rather likely that plaintexts do not have high min-entropy from the adversary's point of view. In such cases, the framework of Bellare et al. might fall short from providing robust security guarantees. We formalize a framework for studying the security of deterministic public-key encryption schemes with respect to auxiliary inputs. Given the trivial requirement that the plaintext should not be efficiently re- coverable from the auxiliary input, we focus on hard-to-invert auxil- iary inputs. Within this framework, we propose two schemes: the first is based on the decisional Diffie-Hellman (and, more generally, on the d-linear) assumption, and the second is based on a rather general class of subgroup indistinguishability assumptions (including, in particular, quadratic residuosity and Paillier's composite residuosity). -

Deterministic Public-Key Encryption Under Continual Leakage
Deterministic Public-Key Encryption under Continual Leakage Venkata Koppula∗ Omkant Pandeyy Yannis Rouselakisz Brent Watersx Abstract Deterministic public-key encryption, introduced by Bellare, Boldyreva, and O'Neill (CRYPTO 2007), is an important technique for searchable encryption; it allows quick, logarithmic-time, search over encrypted data items. The technique is most effective in scenarios where frequent search queries are performed over a huge database of unpredictable data items. We initiate the study of deterministic public-key encryption (D-PKE) in the presence of leakage. We formulate appropriate security notions for leakage-resilient D-PKE, and present constructions that achieve them in the standard model. We work in the continual leakage model, where the secret-key is updated at regular intervals and an attacker can learn arbitrary but bounded leakage on the secret key during each time interval. We, however, do not consider leakage during the updates. Our main construction is based on the (standard) linear assumption in bilinear groups, tolerat- ing up to 0:5 − o(1) fraction of arbitrary leakage. The leakage rate can be improved to 1 − o(1) by relying on the SXDH assumption. At a technical level, we propose and construct a \continual leakage resilient" version of the all-but-one lossy trapdoor functions, introduced by Peikert and Waters (STOC 2008). Our formulation and construction of leakage-resilient lossy-TDFs is of independent general interest for leakage-resilient cryptography. 1 Introduction The notion of semantic security for public key encryption schemes was introduced in the seminal work of Goldwasser and Micali [GM84]. While this strong notion of security is desirable in many applications, it requires that the encryption algorithm must be a random process. -

Assignment 4 – Due Friday, October 14
The University of North Carolina at Greensboro Handout 3 CSC 580: Cryptography and Security in Computing October 7, 2011 Prof. Stephen R. Tate Assignment 4 – Due Friday, October 14 The first two problems are from the book, and deal with error propagation in two block cipher modes. 1. Page 216, Problem 6.4 2. Page 216, Problem 6.8 The remaining problems explore the security models that we discussed in class, in particular the notion of indistinguishability under chosen plaintext attack. First, let’s review the ideas and define some notation. We define security in terms of a “game” that an adversary plays against “oracles” — if you can define an adversary that wins the game with probability significantly better than making a random guess, then the scheme is insecure. Conversely, if no adversary can win the game with probability non-negligibly higher than guessing then the scheme is secure. Note that it’s much easier to prove a scheme is insecure than to prove that one is secure! The “IND-CPA game” is as follows. At the beginning of the game the oracle(s) randomly choose a key for the encryption scheme that is being attacked. During the game, there are two oracles that the adversary can interact with, called Encrypt and Challenge. If the ad- versary calls Encrypt(M) for some message M, the oracle encrypts M using the key that it selected at the beginning of the game and returns the ciphertext. The other oracle takes two plaintext inputs, chosen however the adversary wants, and is called by Challenge(M0, M1). -

Paxson Spring 2017 CS 161 Computer Security Discussion 5
Paxson CS 161 Discussion 5 Spring 2017 Computer Security Week of February 27, 2017 Question 1 Activity: Cryptographic security levels (20 min) Say Alice has a randomly-chosen symmetric key S 2 f0; 1g128 (that is, a 128-bit key) that she uses to encrypt her messages to Bob. Eve is very suspicious of these messages and would like to brute-force guess the key. She does this by getting a pair (M; C) where she knows that C is Alice's encryption of M. She keeps guessing keys k until Ek(M) = C. (a) Probability review. How many attempts does Eve expect to have to try in order to guess Alice's key, if she guesses keys completely at random (with repetition)? What about if she guesses in order (without repetition)? (b) Eve sits down at her computer and starts brute-forcing the key. If her computer can attempt 1 billion keys per second, how much time does Eve expect to wait? How long of a time is this? (c) Eve decides to enlist the help of her friend Ed, who works at the NSA and has access to a cluster of 1,000,000 servers1 running in parallel that can each guess 10 billion keys per second. Now how long will Eve be waiting? How much faster is this? (d) Alice starts getting worried about Eve and decides to increase the key size to 256 bits. Bob claims this is pointless since the key is only twice as big as before, and so Eve needs only double as much time as before.