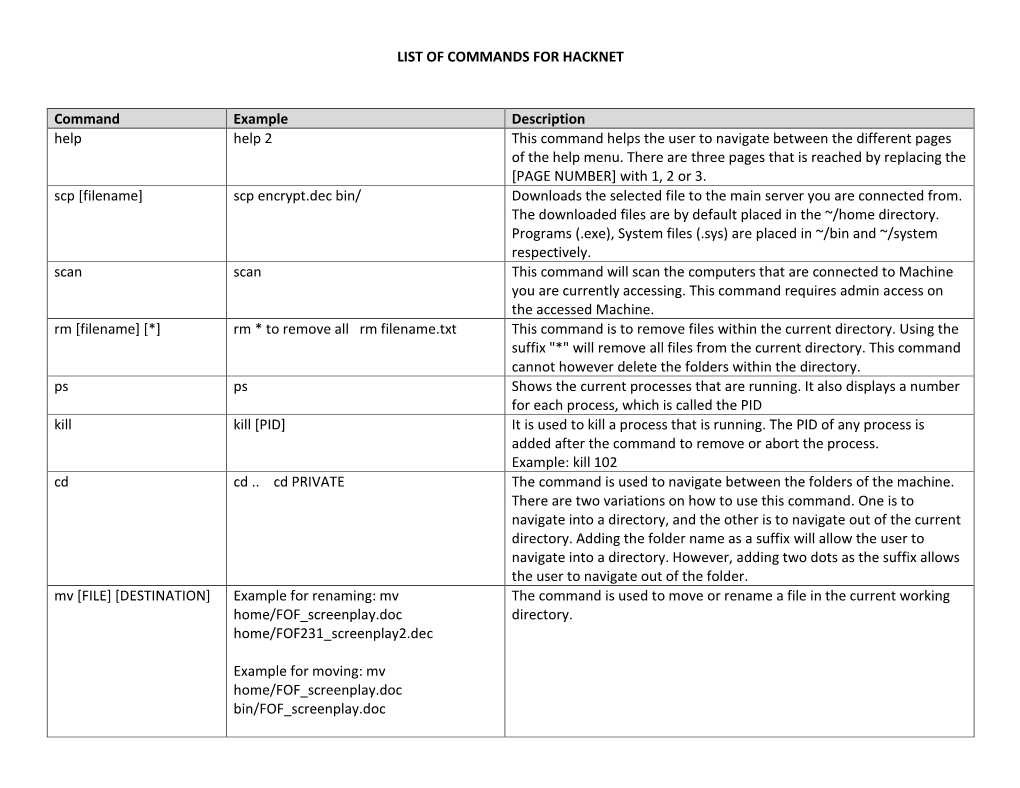
LIST of COMMANDS for HACKNET Command Example Description
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Many Slides Borrowed from Ben Zhao, Christo Wilson, & Others
12. Network Attacks Blase Ur and David Cash (many slides borrowed from Ben Zhao, Christo Wilson, & others) February 7th, 2020 CMSC 23200 / 33250 Network threat model • Network scanning • Attacks on confidentiality (e.g., eavesdropping) • Attacks on integrity (e.g., spoofing, packet injection) • Attacks on availability (e.g., denial of service (DoS)) Scanning and observing networks Network Scanning: Ping • Essential, low-level network utility • Sends a “ping” ICMP message to a host on the internet $ ping 66.66.0.255 PING 66.66.0.255 (66.66.0.255) 56(84) bytes of data. 64 bytes from 66.66.0.255: icmp_seq=1 ttl=58 time=41.2 ms • Destination host is supposed to respond with a “pong” – Indicating that it can receive packets • By default, ping messages are 56 bytes long (+ some header bytes) – Maximum size 65535 bytes • What if you send a ping that is >65535 bytes long? Ping of Death • $ ping –s 65535 66.66.0.255 – Attack identified in 1997 – IPv6 version identified/fixed in 2013 Network Scanning: Traceroute • traceroute — hops between me and host – Sends repeated ICMP reqs w/ increasing TTL Port Scanning • What services are running on a server? Nmap • 5 seconds to scan a single machine!! SYN scan Only send SYN Responses: • SYN-ACK — port open • RST — port closed • Nothing — filtered (e.g., firewall) Port Scanning on Steroids • How do you speed up scans for all IPv4? – Don’t wait for responses; pipeline – Parallelize: divide & conquer IPv4 ranges – Randomize permutations w/o collisions • Result: the zmap tool – Scan all of IPv4 in 45mins (w/ GigE cxn) – IPv4 in 5 mins w/ 10GigE Eavesdropping Tools: Wireshark, tcpdump, Bro, … Steps: 1. -

Blue Coat SGOS Command Line Interface Reference, Version 4.2.3
Blue Coat® Systems ProxySG™ Command Line Interface Reference Version SGOS 4.2.3 Blue Coat ProxySG Command Line Interface Reference Contact Information Blue Coat Systems Inc. 420 North Mary Ave Sunnyvale, CA 94085-4121 http://www.bluecoat.com/support/contact.html [email protected] http://www.bluecoat.com For concerns or feedback about the documentation: [email protected] Copyright© 1999-2006 Blue Coat Systems, Inc. All rights reserved worldwide. No part of this document may be reproduced by any means nor modified, decompiled, disassembled, published or distributed, in whole or in part, or translated to any electronic medium or other means without the written consent of Blue Coat Systems, Inc. All right, title and interest in and to the Software and documentation are and shall remain the exclusive property of Blue Coat Systems, Inc. and its licensors. ProxySG™, ProxyAV™, CacheOS™, SGOS™, Spyware Interceptor™, Scope™, RA Connector™, RA Manager™, Remote Access™ are trademarks of Blue Coat Systems, Inc. and CacheFlow®, Blue Coat®, Accelerating The Internet®, WinProxy®, AccessNow®, Ositis®, Powering Internet Management®, The Ultimate Internet Sharing Solution®, Permeo®, Permeo Technologies, Inc.®, and the Permeo logo are registered trademarks of Blue Coat Systems, Inc. All other trademarks contained in this document and in the Software are the property of their respective owners. BLUE COAT SYSTEMS, INC. DISCLAIMS ALL WARRANTIES, CONDITIONS OR OTHER TERMS, EXPRESS OR IMPLIED, STATUTORY OR OTHERWISE, ON SOFTWARE AND DOCUMENTATION FURNISHED HEREUNDER INCLUDING WITHOUT LIMITATION THE WARRANTIES OF DESIGN, MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL BLUE COAT SYSTEMS, INC., ITS SUPPLIERS OR ITS LICENSORS BE LIABLE FOR ANY DAMAGES, WHETHER ARISING IN TORT, CONTRACT OR ANY OTHER LEGAL THEORY EVEN IF BLUE COAT SYSTEMS, INC. -

The Evolution of Gandcrab Ransomware
The Evolution of GandCrab Ransomware Tamas Boczan @tamas_boczan Sr. Threat Analyst Why? Why? Why? Business Model: RaaS Panel for Affiliates Mass Delivery Methods • Email attachments - Javascript - Doc - Encrypted doc • Drive- by download Delivery: RDP, Exploits Payload: Starting Point Data collection • System Info • External IP • AV? Payload: Starting Point Data collection Connect Home • System Info • nslookup • External IP • AV? Payload: Starting Point Data collection Connect Home Preparation • System Info • nslookup • Kill Processes • External IP • AV? Payload: Starting Point Data collection Connect Home Preparation Encryption • System Info • nslookup • Kill Processes • AES • External IP • *.GDCB • AV? Payload: Starting Point Data collection Connect Home Preparation Encryption Post-Infection • System Info • nslookup • Kill Processes • AES • Shadow Copies • External IP • *.GDCB • AV? Feb 28: Europol decryptor Data collection Connect Home Preparation Encryption Post-Infection • System Info • nslookup • Kill Processes • AES • Shadow Copies • External IP • *.GDCB • AV? 7 days later: v2 Data collection Connect Home Preparation Encryption Post-Infection • System Info • nslookup • Kill Processes • AES • Shadow Copies • External IP • *.CRAB • AV? • Kernel-AV 7 weeks later: v3 Post-Infection • Shadow Copies • Wallpaper v4 Data collection Connect Home Preparation Encryption Post-Infection • System Info • nslookup • Kill Processes • AES • Shadow Copies • External IP • Salsa • Wallpaper • AV? • *.KRAB • Self-removal • SMB shares v4.1 Data collection -

Freebsd Command Reference
FreeBSD command reference Command structure Each line you type at the Unix shell consists of a command optionally followed by some arguments , e.g. ls -l /etc/passwd | | | cmd arg1 arg2 Almost all commands are just programs in the filesystem, e.g. "ls" is actually /bin/ls. A few are built- in to the shell. All commands and filenames are case-sensitive. Unless told otherwise, the command will run in the "foreground" - that is, you won't be returned to the shell prompt until it has finished. You can press Ctrl + C to terminate it. Colour code command [args...] Command which shows information command [args...] Command which modifies your current session or system settings, but changes will be lost when you exit your shell or reboot command [args...] Command which permanently affects the state of your system Getting out of trouble ^C (Ctrl-C) Terminate the current command ^U (Ctrl-U) Clear to start of line reset Reset terminal settings. If in xterm, try Ctrl+Middle mouse button stty sane and select "Do Full Reset" exit Exit from the shell logout ESC :q! ENTER Quit from vi without saving Finding documentation man cmd Show manual page for command "cmd". If a page with the same man 5 cmd name exists in multiple sections, you can give the section number, man -a cmd or -a to show pages from all sections. man -k str Search for string"str" in the manual index man hier Description of directory structure cd /usr/share/doc; ls Browse system documentation and examples. Note especially cd /usr/share/examples; ls /usr/share/doc/en/books/handbook/index.html cd /usr/local/share/doc; ls Browse package documentation and examples cd /usr/local/share/examples On the web: www.freebsd.org Includes handbook, searchable mailing list archives System status Alt-F1 .. -

System Calls & Signals
CS345 OPERATING SYSTEMS System calls & Signals Panagiotis Papadopoulos [email protected] 1 SYSTEM CALL When a program invokes a system call, it is interrupted and the system switches to Kernel space. The Kernel then saves the process execution context (so that it can resume the program later) and determines what is being requested. The Kernel carefully checks that the request is valid and that the process invoking the system call has enough privilege. For instance some system calls can only be called by a user with superuser privilege (often referred to as root). If everything is good, the Kernel processes the request in Kernel Mode and can access the device drivers in charge of controlling the hardware (e.g. reading a character inputted from the keyboard). The Kernel can read and modify the data of the calling process as it has access to memory in User Space (e.g. it can copy the keyboard character into a buffer that the calling process has access to) When the Kernel is done processing the request, it restores the process execution context that was saved when the system call was invoked, and control returns to the calling program which continues executing. 2 SYSTEM CALLS FORK() 3 THE FORK() SYSTEM CALL (1/2) • A process calling fork()spawns a child process. • The child is almost an identical clone of the parent: • Program Text (segment .text) • Stack (ss) • PCB (eg. registers) • Data (segment .data) #include <sys/types.h> #include <unistd.h> pid_t fork(void); 4 THE FORK() SYSTEM CALL (2/2) • The fork()is one of the those system calls, which is called once, but returns twice! Consider a piece of program • After fork()both the parent and the child are .. -

Networking TCP/IP Troubleshooting 7.1
IBM IBM i Networking TCP/IP troubleshooting 7.1 IBM IBM i Networking TCP/IP troubleshooting 7.1 Note Before using this information and the product it supports, read the information in “Notices,” on page 79. This edition applies to IBM i 7.1 (product number 5770-SS1) and to all subsequent releases and modifications until otherwise indicated in new editions. This version does not run on all reduced instruction set computer (RISC) models nor does it run on CISC models. © Copyright IBM Corporation 1997, 2008. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents TCP/IP troubleshooting ........ 1 Server table ............ 34 PDF file for TCP/IP troubleshooting ...... 1 Checking jobs, job logs, and message logs .. 63 Troubleshooting tools and techniques ...... 1 Verifying that necessary jobs exist .... 64 Tools to verify your network structure ..... 1 Checking the job logs for error messages Netstat .............. 1 and other indication of problems .... 65 Using Netstat from a character-based Changing the message logging level on job interface ............. 2 descriptions and active jobs ...... 65 Using Netstat from System i Navigator .. 4 Other job considerations ....... 66 Ping ............... 7 Checking for active filter rules ...... 67 Using Ping from a character-based interface 7 Verifying system startup considerations for Using Ping from System i Navigator ... 10 networking ............ 68 Common error messages ....... 13 Starting subsystems ........ 68 PING parameters ......... 14 Starting TCP/IP .......... 68 Trace route ............ 14 Starting interfaces ......... 69 Using trace route from a character-based Starting servers .......... 69 interface ............ 15 Timing considerations ........ 70 Using trace route from System i Navigator 15 Varying on lines, controllers, and devices . -

Exercise 1. RNA-Seq Alignment and Quantification Part 1. Prepare the Working Directory. Part 2. Examine Qualities of the RNA-Seq
Exercise 1. RNA-seq alignment and quantification Part 1. Prepare the working directory. 1. Connect to your assigned computer. If you do not know how, follow the instruction at http://cbsu.tc.cornell.edu/lab/doc/Remote_access.pdf (Read the section under “Connection by ssh”. There are separate instructions for Windows and Mac users) 2. Use the following commands to create a working directory, and copy Arabidopsis genome FASTA file (TAIR10.fa) and rice annotation file (TAIR10.gff3) for this homework to the working directory (replace “xxxxxx” with your user ID) mkdir /workdir/xxxxx mkdir /workdir/xxxxx/exercise1 cd /workdir/xxxxx/exercise1 cp /shared_data/RNAseq/exercise1/* ./ ls Part 2. Examine qualities of the RNA-seq data files 1. Run fastqc on the fastq file fastqc MUa.fastq.gz 2. The fastqc software would create a new file called “MUa_fastqc.html”. You can download this file to your laptop. To do this, you need the software called FileZilla. Instruction to use FileZilla within Cornell campus: Host name: cbsuzzzzz.biohpc.cornell.edu (cbsuzzzzz is the name of your assigned computer) UserName and Password: your user ID and password Port: 22 After click “Quickconnect”, the left panel show files in your laptop, the right panel show files in the remote BioHPC computer. Next to “Remote site” on top of the right panel, enter “/workdir/xxxxx/” and press “return”. You will see the “MUa_fastqc.html” file and drag it into the left panel. Instruction to use FileZilla outside Cornell campus: User VPN. 3. On your laptop by double clicking the file “MUa_fastqc.html” to open the page. -

Processes in Linux/Unix
Processes in Linux/Unix A program/command when executed, a special instance is provided by the system to the process. This instance consists of all the services/resources that may be utilized by the process under execution. • Whenever a command is issued in unix/linux, it creates/starts a new process. For example, pwd when issued which is used to list the current directory location the user is in, a process starts. • Through a 5 digit ID number unix/linux keeps account of the processes, this number is call process id or pid. Each process in the system has a unique pid. • Used up pid’s can be used in again for a newer process since all the possible combinations are used. • At any point of time, no two processes with the same pid exist in the system because it is the pid that Unix uses to track each process. Initializing a process A process can be run in two ways: 1. Foreground Process : Every process when started runs in foreground by default, receives input from the keyboard and sends output to the screen. When issuing pwd command $ ls pwd Output: $ /home/geeksforgeeks/root When a command/process is running in the foreground and is taking a lot of time, no other processes can be run or started because the prompt would not be available until the program finishes processing and comes out. 2. Backround Process : It runs in the background without keyboard input and waits till keyboard input is required. Thus, other processes can be done in parallel with the process running in background since they do not have to wait for the previous process to be completed. -

Controlling Gpios on Rpi Using Ping Command
Ver. 3 Department of Engineering Science Lab – Controlling PI Controlling Raspberry Pi 3 Model B Using PING Commands A. Objectives 1. An introduction to Shell and shell scripting 2. Starting a program at the Auto-start 3. Knowing your distro version 4. Understanding tcpdump command 5. Introducing tshark utility 6. Interfacing RPI to an LCD 7. Understanding PING command B. Time of Completion This laboratory activity is designed for students with some knowledge of Raspberry Pi and it is estimated to take about 5-6 hours to complete. C. Requirements 1. A Raspberry Pi 3 Model 3 2. 32 GByte MicroSD card à Give your MicroSD card to the lab instructor for a copy of Ubuntu. 3. USB adaptor to power up the Pi 4. Read Lab 2 – Interfacing with Pi carefully. D. Pre-Lab Lear about ping and ICMP protocols. F. Farahmand 9/30/2019 1 Ver. 3 Department of Engineering Science Lab – Controlling PI E. Lab This lab has two separate parts. Please make sure you read each part carefully. Answer all the questions. Submit your codes via Canvas. 1) Part I - Showing IP Addresses on the LCD In this section we learn how to interface an LCD to the Pi and run a program automatically at the boot up. a) Interfacing your RPI to an LCD In this section you need to interface your 16×2 LCD with Raspberry Pi using 4-bit mode. Please note that you can choose any type of LCD and interface it to your PI, including OLED. Below is the wiring example showing how to interface a 16×2 LCD to RPI. -

How to Restart Marmoset Buildservers During a Term by Omar Nafees @ CSCF
How to restart Marmoset buildservers during a term by Omar Nafees @ CSCF The Marmoset buildservers are special programs that do the work of testing student submissions to the Marmoset submitserver (https://marmoset.student.cs.uwaterloo.ca) safely in the linux.student.cs environment. Due to the unpredictable nature of student code and instructor supplied tests, sometimes the buildservers hang or experience problems. You can see the status of currently running buildservers at https://marmoset.student.cs.uwaterloo.ca/status/QueryBuildServerStatus A reasonable solution during hanging situations is to simply restart the buildservers. This article outlines the steps you need to take to restart a course’s Marmoset buildservers. Keep in mind, that restarting the buildservers stops any testing that might have been going on at the time. This means students will see no results for submissions. That submission would either have to be retested (which is tricky) or simply ignored and the student would have to resubmit. As an example, let’s restart cs241’s buildservers. Step 1: Log into [email protected] from the cs241 account. ubuntu1204002:~> whoami cs241 ubuntu1204002:~> ssh [email protected] You have mail. Last login: Sat Mar 15 20:45:49 2014 ... ubuntu1204002:~> whoami cs241t ubuntu1204002:~> Step 2: Take a look inside the “buildserver” directory : Note: The “buildserver” directory is very important and you shouldn’t modify it in any way. ubuntu1204002:~> ls ~/buildserver bs10.cs241t.ubuntu1204004.student.cs bs1.cs241t.ubuntu1204004.student.cs -

Useful Linux Commands
Useful Linux Commands Arnon Erba Agricultural & Resource Economics Updated October 25, 2019 Contents 1 Command Structure & Manual Pages2 1.1 Command Structure...................................2 1.2 Manual Pages.......................................2 2 File & Directory Management3 2.1 ls { List Files.......................................3 2.2 cd { Change Directory..................................3 2.3 pwd { Print Working Directory..............................3 2.4 rm { Remove Files....................................3 2.5 cp { Copy Files & Directories..............................3 2.6 mv { Move or Rename Files & Directories........................4 2.7 mkdir { Make New Directories..............................4 2.8 rmdir { Remove Empty Directories...........................4 3 Resource & Process Management4 3.1 ps { Process Status....................................4 3.2 kill { Kill Process....................................4 3.3 free { Show Memory Usage...............................4 3.4 df { Show Free Disk Space................................5 3.5 du { Estimate Disk Usage of Files............................5 3.6 htop { Interactive Resource Monitor..........................5 4 File Manipulation5 4.1 cat { Concatenate Files.................................5 4.2 grep { Search Inside Files................................6 4.3 vim { Text Editor.....................................6 4.4 vi { Text Editor.....................................6 4.5 nano { Text Editor....................................6 1 Abstract This document explains -

From DOS/Windows to Linux HOWTO from DOS/Windows to Linux HOWTO
From DOS/Windows to Linux HOWTO From DOS/Windows to Linux HOWTO Table of Contents From DOS/Windows to Linux HOWTO ........................................................................................................1 By Guido Gonzato, ggonza at tin.it.........................................................................................................1 1.Introduction...........................................................................................................................................1 2.For the Impatient...................................................................................................................................1 3.Meet bash..............................................................................................................................................1 4.Files and Programs................................................................................................................................1 5.Using Directories .................................................................................................................................2 6.Floppies, Hard Disks, and the Like ......................................................................................................2 7.What About Windows?.........................................................................................................................2 8.Tailoring the System.............................................................................................................................2 9.Networking: