Virus Bulletin, May 1993
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Virus Bulletin, August 1994
ISSN 0956-9979 AUGUST 1994 THE INTERNATIONAL PUBLICATION ON COMPUTER VIRUS PREVENTION, RECOGNITION AND REMOVAL Editor: Richard Ford CONTENTS Technical Editor: Fridrik Skulason Consulting Editor: Edward Wilding, EDITORIAL Network Security Management, UK Bigger, By Being Better? 2 VIRUS PREVALENCE TABLE 3 NEWS Central Point Merger Completed 3 Pathogen Author Arrested 3 IBM PC VIRUSES (UPDATE) 4 IN THIS ISSUE: INSIGHT CARO explained. Many people have no idea what Schwartau on Security 6 CARO is, what it does, or how to join it. Everything you ever wanted to know about the organisation but were FEATURE afraid to ask is on pp.8-9. CARO: A Personal View 8 The professionals professional. For the first time VIRUS ANALYSES ever, VB reviews AVP, one of Russias leading virus 1. AntiCMOS - Brain Damage 9 scanners: have researchers behind the former Iron 2. A Pile of Junk? 11 Curtain made as many advances in their work as those in 3. Pure Thoughts 13 the West? FEATURE The Lotus position. Lotus has adopted a novel ap- Epidemic Virus Control 15 proach to the prevention of large-scale virus outbreaks within the company. How effective is its technique, and PRODUCT REVIEWS is it a practical alternative in other companies? See p.15. 1. AVP - A Professional Choice 18 2. NetShield 1.5 21 END NOTES & NEWS 24 VIRUS BULLETIN ©1994 Virus Bulletin Ltd, 21 The Quadrant, Abingdon, Oxfordshire, OX14 3YS, England. Tel. +44 (0)235 555139. /94/$0.00+2.50 No part of this publication may be reproduced, stored in a retrieval system, or transmitted in any form without the prior written permission of the publishers. -

59520611.Pdf
SOFTWARE • The software provides the commands that tell the hardware what tasks to perform, what to read and write, how to send the end result (the output) to a monitor and/or printer. • Software is the programs and data that a computer uses. • Software is kept on some hardware device such as a hard disk or floppy disk, but it itself is intangible. • Software consists of both programs and data. Programs are lists of instructions for the processor. Data can be any information that a program needs: character data, numerical data, image data, audio data, and countless other types. KINDS OF SOFTWARE • Application software (usually called just "applications") are programs that people use to get their work done. It may include data entry; update query and report programs, productivity software for spreadsheets, word processing, databases and custom accounting programs for payroll, billing and inventory. It is designed to help people with specific task such as making a spreadsheet of creating a graphic image. Example of Application Software: Word Processor Microsoft Word Lotus Word Pro Word Perfect Spreadsheet Software Microsoft Excel Lotus 123 Quicken Presentation Software Microsoft PowerPoint Lotus Freelance Graphics Database Software Microsoft Access Lotus Approach Web Browser Internet Explorer Netscape Navigator PIM (Personal Information Manager) - software designed to organize names, addresses, and random notes for easy and efficient retrieval. It is just like an electronic equivalent of a conven- tional book-type personal organizer. PIM usually features an automatic dialing telephone list, a programmable calendar and an automatic reminder scheduler. It is ideal for people with hectic schedules who spend a lot of time working with their computers. -

La Sécurité Informatique Edition Livres Pour Tous (
La sécurité informatique Edition Livres pour tous (www.livrespourtous.com) PDF générés en utilisant l’atelier en source ouvert « mwlib ». Voir http://code.pediapress.com/ pour plus d’informations. PDF generated at: Sat, 13 Jul 2013 18:26:11 UTC Contenus Articles 1-Principes généraux 1 Sécurité de l'information 1 Sécurité des systèmes d'information 2 Insécurité du système d'information 12 Politique de sécurité du système d'information 17 Vulnérabilité (informatique) 21 Identité numérique (Internet) 24 2-Attaque, fraude, analyse et cryptanalyse 31 2.1-Application 32 Exploit (informatique) 32 Dépassement de tampon 34 Rétroingénierie 40 Shellcode 44 2.2-Réseau 47 Attaque de l'homme du milieu 47 Attaque de Mitnick 50 Attaque par rebond 54 Balayage de port 55 Attaque par déni de service 57 Empoisonnement du cache DNS 66 Pharming 69 Prise d'empreinte de la pile TCP/IP 70 Usurpation d'adresse IP 71 Wardriving 73 2.3-Système 74 Écran bleu de la mort 74 Fork bomb 82 2.4-Mot de passe 85 Attaque par dictionnaire 85 Attaque par force brute 87 2.5-Site web 90 Cross-site scripting 90 Défacement 93 2.6-Spam/Fishing 95 Bombardement Google 95 Fraude 4-1-9 99 Hameçonnage 102 2.7-Cloud Computing 106 Sécurité du cloud 106 3-Logiciel malveillant 114 Logiciel malveillant 114 Virus informatique 120 Ver informatique 125 Cheval de Troie (informatique) 129 Hacktool 131 Logiciel espion 132 Rootkit 134 Porte dérobée 145 Composeur (logiciel) 149 Charge utile 150 Fichier de test Eicar 151 Virus de boot 152 4-Concepts et mécanismes de sécurité 153 Authentification forte -

Virus Bulletin, January 1993
January 1993 ISSN 0956-9979 THE AUTHORITATIVE INTERNATIONAL PUBLICATION ON COMPUTER VIRUS PREVENTION, RECOGNITION AND REMOVAL Editor: Richard Ford Technical Editor: Fridrik Skulason Consulting Editor: Edward Wilding Advisory Board: Jim Bates, Bates Associates, UK, Andrew Busey, Datawatch Corporation, USA, David M. Chess, IBM Research, Phil Crewe, Fingerprint, UK, David Ferbrache, Defence Research Agency, UK, Ray Glath, RG Software Inc., USA, Hans Gliss, Datenschutz Berater, West Germany, Ross M. Greenberg, Software Concepts Design, USA, Dr. Harold Joseph Highland, Compulit Microcomputer Security Evaluation Laboratory, USA, Dr. Jan Hruska, Sophos, UK, Dr. Keith Jackson, Walsham Contracts, UK, Owen Keane, Barrister, UK, John Laws, Defence Research Agency, UK, Tony Pitts, Digital Equipment Corporation, UK, Yisrael Radai, Hebrew University of Jerusalem, Israel, Martin Samociuk, Network Security Management, UK, John Sherwood, Sherwood Associates, UK, Prof. Eugene Spafford, Purdue University, USA, Dr. Peter Tippett, Certus Corporation, USA, Steve R. White, IBM Research, Dr. Ken Wong, PA Consulting Group, UK, Ken van Wyk, CERT, USA. CONTENTS SCANNER UPDATE 1993 Scanner Shoot-Out 8 EDITORIAL Imageline v. McAfee 2 VIRUS ANALYSES NEWS 1. The CMOS1 Virus 13 2. DOSHUNTER - Search S&S Caught Out 3 And Destroy 15 Chinese Whispers 3 3. Penza - Variations on a Familiar Theme 16 A Rose By Any Other Name 3 PRODUCT REVIEWS IBM PC VIRUSES (UPDATE) 4 1. IBM AntiVirus 18 INSIGHT 2. PC Tools 8 21 Scotland Yard’s Virus Hunters 6 END NOTES & NEWS 24 VIRUS BULLETIN ©1993 Virus Bulletin Ltd, 21 The Quadrant, Abingdon Science Park, Oxon, OX14 3YS, England. Tel (+44) 235 555139. /90/$0.00+2.50 This bulletin is available only to qualified subscribers. -

Computer Virus 16 Views 0 0 RELATED TITLES Virus
16 views 0 0 RELATED TITLES Virus Uploaded by Abu Naser Mohammad Saif Full description Save Embed Share Print Steve Jobs Cryptonomicon The Woman Who Smashed Codes: A True Computer Virus 16 views 0 0 RELATED TITLES Virus Uploaded by Abu Naser Mohammad Saif Full description Save Embed Share Print Steve Jobs Cryptonomicon The Woman Who Smashed Codes: A True Presentation Outline 1. Introduction: 2. VIRUS Definition and Naming: 3. Types of computer virus: 4. Example of Virus 5. To phases of virus 6. Symptom of computer attacked by virus 7. Special focus on: Trojan, & phishing site 8. Combating Viruses 9. Anti viruses & Firewall 16 views 0 0 RELATED TITLES Virus Uploaded by Abu Naser Mohammad Saif Full description Save Embed Share Print Steve Jobs Cryptonomicon The Woman Who Smashed Codes: A True Presentation Outline Symptom of computer attacked by virus Special focus on: Trojan, & phishing site Combating VirusesAnti viruses & Firewall 16 views 0 0 RELATED TITLES Virus Uploaded by Abu Naser Mohammad Saif Full description Save Embed Share Print Steve Jobs Cryptonomicon The Woman Who Smashed Codes: A True Presentation Outline 1. Introduction: 2. VIRUS Definition and Naming: 3. History of Computer Virus: 4. Types of computer virus: 5. Example of Virus 6. To phases of virus: 16 views 0 0 RELATED TITLES Virus Uploaded by Abu Naser Mohammad Saif Full description Save Embed Share Print Steve Jobs Cryptonomicon The Woman Who Smashed Codes: A True Introduction: Computer VIRUS Almost every uses has faced virus attack And loses some sort of computer resources Computer VIRUS is not a biological element rather computer program (s). -

Newsletter of Stanford Palo Alto Users Group for PC
' mmm ~ I.__ __v_o_i_. _x_•_11_______ J_u_L_v_•_9_9s _________ N_o_ ._1_ __. Q Newsletter of Stanford Palo Alto Users Group for PC Q TABLE OF CONTENTS President's Piece Brain Christopher, SPAUG President 2 ~ New BBS Kendric Smith 2 Banks, Microsoft, and Online Banking Larry Weinberg J Norton DeskTop for Windows Lee Ammons 4 Internet Access in Public Libraries s Renewals 6 Anti-Virus for OS/2 David Varney 7 Why I Like OS/2 Jack Cook 8 Internet SIG 9 Membership Application 10 Resource Center SP AUG 11 ..... Ji GENERAL MEETING McAFEE ASSOCIATES - Latest Anti-Virus Software INCAT SYSTEMS - YAMAHA Recordable CD-ROM WATERGATE SOFTWARE - PC Doctor for IRQ Conflicts WEDNESDAY. JULY 26, 7:3 PM SPAUG NOW HAS A Conference ON A LOCAL First Class BBS. Nick Chinn. the Sysop (system operator) of Dead Winners Dog Party.has kindly provided space on his BBS for A new adventure is a click away for prize an interactive Conference for SPAUG. All you need winners at the June General Meeting. Del Philpott is a computer with a modem. Just dial (415) 968- and Clark Moore both won Pixar's Typestry. Frank 7919. You will see a few introductory screens of Kimbel and Bill McElhrney won Ares software information and be prompted to enter a User ID and Font Minder and Font Chameleon . Larry Turpen a password. New users will be prompted lo fill out won the Better Homes & Garden's Healthily a registration form. Cooking. After logging on, go to Conferences and select BBS Closed SPAUG. You can read what has been posted by other, and you can post your own material that you On July 5th, the Board of Directors feel will be of interest to others in the PC unanimously voted lo close the SPAUG BBS. -

Netware 5.1 Upgrade
NOVELL PARTNER CONSULTING SERVICE OFFERINGS NOVELL PARTNERNET CONFIDENTIAL CONSULTANT GUIDE NetWare 5.1 Upgrade ® Table of Contents NetWare 5.1 Upgrade Consulting Guide .................................................................................... 4 Target Audience...........................................................................Error! Bookmark not defined. Terminology......................................................................................................................... 4 Skill Set............................................................................................................................... 4 Purpose ............................................................................................................................... 5 Acknowledgements.......................................................................Error! Bookmark not defined. NetWare 5.1 Training Curriculum ............................................................................................ 6 Curriculum for NetWare 5.1 .................................................................................................... 6 Curriculum for NetWare 5 CNE ............................................................................................... 6 Reference Material ...............................................................................................................10 Books .............................................................................................................................10 AppNotes -

The Illusion of Space and the Science of Data Compression And
The Illusion of Space and the Science of Data Compression and Deduplication Bruce Yellin EMC Proven Professional Knowledge Sharing 2010 Bruce Yellin Advisory Technology Consultant EMC Corporation [email protected] Table of Contents What Was Old Is New Again ......................................................................................................... 4 The Business Benefits of Saving Space ....................................................................................... 6 Data Compression Strategies ....................................................................................................... 9 Data Compression Basics ....................................................................................................... 10 Compression Bakeoff .............................................................................................................. 13 Data Deduplication Strategies .................................................................................................... 16 Deduplication - Theory of Operation ....................................................................................... 16 File Level Deduplication - Single Instance Storage ................................................................. 21 Fixed-Block Deduplication ....................................................................................................... 23 Variable-Block Deduplication .................................................................................................. 24 Content-Aware Deduplication -

Virus Bulletin, October 1994
ISSN 0956-9979 OCTOBER 1994 THE INTERNATIONAL PUBLICATION ON COMPUTER VIRUS PREVENTION, RECOGNITION AND REMOVAL Editor: Richard Ford CONTENTS Technical Editor: Fridrik Skulason Consulting Editor: Edward Wilding, EDITORIAL Network Security Management, UK Live and Let Die 2 VIRUS PREVALENCE TABLE 3 NEWS Virus Total Reaches 5000 3 CPAV to Continue 3 Total Anonymity 3 IN THIS ISSUE: IBM PC VIRUSES (UPDATE) 4 To be the best. This months edition brings the biggest CONFERENCE REPORT Virus Bulletin comparative review yet of NLM anti-virus VB 94: The Return to Jersey 6 software (see pp.13-20). Ten products were tested, and the results may cause something of a surprise VIRUS ANALYSES 1. One_Half: The Lieutenant Commander? 9 Conference spotlight. VB 94 recently took place in 2. AntiEXE.A - Missing the Target? 11 Jersey - turn to page 6 for an in-depth report on what happened when. COMPARATIVE REVIEW Half way there? One_Half is a multi-partite virus NLMs in Depth 13 which uses some of the techniques developed by the PRODUCT REVIEW Dark Avenger in Commander_Bomber. As if this were Virex for the PC 21 not enough, it can also encrypt vital parts of the fixed disk. A detailed analysis is given on page 9. END NOTES & NEWS 24 VIRUS BULLETIN ©1994 Virus Bulletin Ltd, 21 The Quadrant, Abingdon, Oxfordshire, OX14 3YS, England. Tel. +44 (0)1235 555139. /94/$0.00+2.50 No part of this publication may be reproduced, stored in a retrieval system, or transmitted in any form without the prior written permission of the publishers. 2 • VIRUS BULLETIN OCTOBER 1994 EDITORIAL Live and Let Die The Internet seems to have become the symbol of the computing revolution which we are told is going to change our lives forever. -

DLCC Software Catalog
Daniel's Legacy Computer Collections Software Catalog Category Platform Software Category Title Author Year Media Commercial Apple II Integrated Suite Claris AppleWorks 2.0 Claris Corporation and Apple Computer, Inc. 1987 800K Commercial Apple II Operating System Apple IIGS System 1.0.2 --> 1.1.1 Update Apple Computer, Inc. 1984 400K Commercial Apple II Operating System Apple IIGS System 1.1 Apple Computer, Inc. 1986 800K Commercial Apple II Operating System Apple IIGS System 2.0 Apple Computer, Inc. 1987 800K Commercial Apple II Operating System Apple IIGS System 3.1 Apple Computer, Inc. 1987 800K Commercial Apple II Operating System Apple IIGS System 3.2 Apple Computer, Inc. 1988 800K Commercial Apple II Operating System Apple IIGS System 4.0 Apple Computer, Inc. 1988 800K Commercial Apple II Operating System Apple IIGS System 5.0 Apple Computer, Inc. 1989 800K Commercial Apple II Operating System Apple IIGS System 5.0.2 Apple Computer, Inc. 1989 800K Commercial Apple II Reference: Programming ProDOS Basic Programming Examples Apple Computer, Inc. 1983 800K Commercial Apple II Utility: Printer ImageWriter Toolkit 1.5 Apple Computer, Inc. 1984 400K Commercial Apple II Utility: User ProDOS User's Disk Apple Computer, Inc. 1983 800K Total Apple II Titles: 12 Commercial Apple Lisa Emulator MacWorks 1.00 Apple Computer, Inc. 1984 400K Commercial Apple Lisa Office Suite Lisa 7/7 3.0 Apple Computer, Inc. 1984 400K Total Apple Lisa Titles: 2 Commercial Apple Mac OS 0-9 Audio Audioshop 1.03 Opcode Systems, Inc. 1992 800K Commercial Apple Mac OS 0-9 Audio Audioshop 2.0 Opcode Systems, Inc. -

Counteracting Viruses in MS-DOS Systems
86-01-35 Counteracting Viruses in MS-DOS Previous screen Systems A. Padgett Peterson Payoff The trapdoors programmed into the first DOS-based personal computers still persist today, providing relatively easy access for viruses and worms. By learning how malicious software exploits these weaknesses, security managers can develop a coordinated defense to counteract virus attacks now and in the future. This article describes how MS-DOS start- up processes can become exposed to viruses, discusses various intrusion methods, and presents techniques for designing a safe computing environment. Problems Addressed Today's personal computers still bear striking similarities to the first units created during the 1970s. All of the trapdoors and loopholes developed by systems experts to permit BIOS-level programming in the early stages of development of these systems are still present today, providing easy access for viruses, worms, logic bombs, and Trojan horses. It is alarming that such low-level programs are no longer being fully documented by manufacturers; they are currently treating as proprietary the techniques that were widely disseminated just a few years ago. Administrators and systems managers who are responsible for the millions of dollars of corporate investment in trusted computing systems typically lack an in-depth understanding of these systems. Unfortunately, penetration techniques, though not readily available, are known to an underground of hackers. Although numerous antivirus products have become available, these products are as available to hackers as to legitimate users. Fortunately, defenses are available to the corporate systems manager that cannot be readily compromised by the individual computer user. A trusted computing environment can be developed that is low in cost and user impact, one that not only has a high degree of reliability but permits natural and easy growth. -
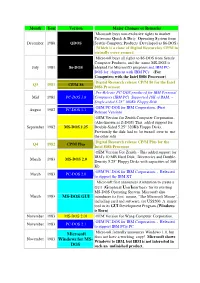
Microsoft Windows for MS
Month Year Version Major Changes or Remarks Microsoft buys non-exclusive rights to market Pattersons Quick & Dirty Operating System from December 1980 QDOS Seattle Computer Products (Developed as 86-DOS) (Which is a clone of Digital Researches C P/M in virtually every respect) Microsoft buys all rights to 86-DOS from Seattle Computer Products, and the name MS-DOS is July 1981 86-DOS adopted for Microsoft's purposes and IBM PC- DOS for shipment with IBM PCs (For Computers with the Intel 8086 Processor) Digital Research release CP/M 86 for the Intel Q3 1981 CP/M 86 8086 Processer Pre-Release PC-DOS produced for IBM Personal Mid 1981 PC-DOS 1.0 Computers (IBM PC) Supported 16K of RAM, ~ Single-sided 5.25" 160Kb Floppy Disk OEM PC-DOS for IBM Corporation. (First August 1982 PC-DOS 1.1 Release Version) OEM Version for Zenith Computer Corporation.. (Also known as Z-DOS) This added support for September 1982 MS-DOS 1.25 Double-Sided 5.25" 320Kb Floppy Disks. Previously the disk had to be turned over to use the other side Digital Research release CP/M Plus for the Q4 1982 CP/M Plus Intel 8086 Processer OEM Version For Zenith - This added support for IBM's 10 MB Hard Disk, Directories and Double- March 1983 MS-DOS 2.0 Density 5.25" Floppy Disks with capacities of 360 Kb OEM PC-DOS for IBM Corporation. - Released March 1983 PC-DOS 2.0 to support the IBM XT Microsoft first announces it intention to create a GUI (Graphical User Interface) for its existing MS-DOS Operating System.