Каталог Продукции Quest Software 2020
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Netvault Backup Plug-In for Domino User’S Guide Updated - February 2020 Software Version - 12.4 Contents
Quest® NetVault® Backup Plug-in for Domino 12.4 User’s Guide © 2020 Quest Software Inc. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this guide is furnished under a software license or nondisclosure agreement. This software may be used or copied only in accordance with the terms of the applicable agreement. No part of this guide may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying and recording for any purpose other than the purchaser’s personal use without the written permission of Quest Software Inc. The information in this document is provided in connection with Quest Software products. No license, express or implied, by estoppel or otherwise, to any intellectual property right is granted by this document or in connection with the sale of Quest Software products. EXCEPT AS SET FORTH IN THE TERMS AND CONDITIONS AS SPECIFIED IN THE LICENSE AGREEMENT FOR THIS PRODUCT, QUEST SOFTWARE ASSUMES NO LIABILITY WHATSOEVER AND DISCLAIMS ANY EXPRESS, IMPLIED OR STATUTORY WARRANTY RELATING TO ITS PRODUCTS INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, OR NON-INFRINGEMENT. IN NO EVENT SHALL QUEST SOFTWARE BE LIABLE FOR ANY DIRECT, INDIRECT, CONSEQUENTIAL, PUNITIVE, SPECIAL OR INCIDENTAL DAMAGES (INCLUDING, WITHOUT LIMITATION, DAMAGES FOR LOSS OF PROFITS, BUSINESS INTERRUPTION OR LOSS OF INFORMATION) ARISING OUT OF THE USE OR INABILITY TO USE THIS DOCUMENT, EVEN IF QUEST SOFTWARE HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. Quest Software makes no representations or warranties with respect to the accuracy or completeness of the contents of this document and reserves the right to make changes to specifications and product descriptions at any time without notice. -

Netvault Backup for Network-Attached Storage
NetVault for Network-Attached Storage Get flexible, scalable protection for data Optimize backups — Optimize your BENEFITS: stored on network-attached storage (NAS) backups with selectable index options. • Fast indexing of backup data devices with Quest NetVault. Using a Enhanced options include writing the specialized plug-in that supports Network index to media or the NetVault database • Disk-to-disk backup Data Management Protocol (NDMP), after a backup completes. • Support for all five NDMP NetVault maximizes data transfer over the transfer models network while maintaining centralized Operate seamlessly between multiple backup administration. It not only provides platforms — NetVault supports mixed • Directory-level relocation fast, online data backup and recovery, server environments with integrated data protection for UNIX, Windows, • Simple point-and-click it also provides efficient backup and installation and configuration recovery options regardless of the NDMP Linux and NAS devices. network configuration model in use. • Local backup and restore Choose from multiple backup The solution also offers advanced configuration options — Increase NAS • Filer-to-filer backup and restore and network availability by defining features, including browsable volume • NetVault Backup client-to- selection and direct access restore (DAR) NDMP-based backup functions to meet filer backup and restore support, which lets you quickly find your existing storage environment. exactly what must be restored to provide NetVault supports all five NDMP data • Dynamic drive sharing on a rapid time to recovery. Altogether, with transfer models. It also supports storage area network (SAN) between filers and NetVault NetVault, you’ll be able to optimize dynamic sharing of tape devices in Backup servers and clients operating efficiency, minimize impact to a NAS/ SAN storage environment, users and reduce your storage window. -

Netvault Backup
NetVault ® Backup Enterprise-class data protection for diverse IT environments The success of your business depends FEATURES on your ability to protect, access and Physical and virtual support — Protect NetVault Backup provides leverage your mission-critical data on a both physical and virtual servers comprehensive data daily basis — and to restore it quickly in (VMware and Hyper-V) with a single protection for hybrid IT the event of an unexpected outage. Yet solution and gain consistent, reliable, many enterprises use data protection environments from one point-and-click backup and restore. By intuitive console. software that sacrifices functionality for running the VMware plug-in on any avail- simplicity, or scalability for versatility. able proxy, you can back up all virtual machines with a single unified view that With Quest® NetVault® Backup, high- BENEFITS: growth organizations can benefit from scales to thousands of VMs. enterprise-class, cross-platform data • Lower total cost of ownership Enterprisewide control — Configure, protection that's easy to use right out of and simplified administration manage and monitor your backup and using a single solution to manage the box and that scales easily to accom- recovery operations from a web-based complex, hybrid data centers modate data growth. user interface. Convenient wizards guide • Significant storage cost savings with you through common tasks, such as With this software, you can protect a client-side deduplication and the creating backup jobs, assigning policies, massive number of servers contain- ability to use lower cost storage ing petabytes of data — from one configuring storage devices and gener- • More granular recovery points web-based console. -

Network and Workload
Dell Enterprise Backup & Recovery NetVault Backup At a Glance Pain Points Why NetVault Backup Rising Capital & Operating Expenses Easy to Deployment, Management, & Upgrade What is NetVault Backup? • Many organizations are struggling to keep up with • Get up and running in a matter of hours Dell NetVault Backup is a cross-platform data growth • Modular architecture makes it easy to upgrade to backup and recovery solution that delivers the • Many backup solutions require constant attention, meet your growing environment and changing breadth of coverage organizations need for all raising operating costs recovery objectives. of their platforms and applications. It provides • Upgrades are costly, requiring professional • Requires minimal training to become an expert unsurpassed ease of use, advanced functionality services and a lot of hardware and built-in scalability to manage resources Comprehensive Protection across a diverse range of physical and virtual Unreliable Recovery • Protect many different platforms, applications, platforms. • Today more data is considered mission critical, yet databases, processors, and storage devices many organizations aren’t confident they can • Support for Linux & Mac OS, plus many other NetVault Backup supports most major operating recover lost data platforms systems (physical and virtual) and processor • Organizations demand more aggressive recovery • “Best in Class’ protection for MySQL and Oracle architectures. It also supports many different objectives (recovery points, recovery times, and • Excellent -
Dell Netvault Backup Plug-In for NDMP 10.0.5 User's Guide
Dell™ NetVault™ Backup Plug-in for NDMP 10.0.5 User’s Guide © 2015 Dell Inc. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this guide is furnished under a software license or nondisclosure agreement. This software may be used or copied only in accordance with the terms of the applicable agreement. No part of this guide may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying and recording for any purpose other than the purchaser’s personal use without the written permission of Dell Inc. The information in this document is provided in connection with Dell products. No license, express or implied, by estoppel or otherwise, to any intellectual property right is granted by this document or in connection with the sale of Dell products. EXCEPT AS SET FORTH IN THE TERMS AND CONDITIONS AS SPECIFIED IN THE LICENSE AGREEMENT FOR THIS PRODUCT, DELL ASSUMES NO LIABILITY WHATSOEVER AND DISCLAIMS ANY EXPRESS, IMPLIED OR STATUTORY WARRANTY RELATING TO ITS PRODUCTS INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, OR NON-INFRINGEMENT. IN NO EVENT SHALL DELL BE LIABLE FOR ANY DIRECT, INDIRECT, CONSEQUENTIAL, PUNITIVE, SPECIAL OR INCIDENTAL DAMAGES (INCLUDING, WITHOUT LIMITATION, DAMAGES FOR LOSS OF PROFITS, BUSINESS INTERRUPTION OR LOSS OF INFORMATION) ARISING OUT OF THE USE OR INABILITY TO USE THIS DOCUMENT, EVEN IF DELL HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. Dell makes no representations or warranties with respect to the accuracy or completeness of the contents of this document and reserves the right to make changes to specifications and product descriptions at any time without notice. -

Toad™ Data Modeler
Toad ™ Data Modeler Powerful and cost-effective database modeling and design Whether you’re a data modeler, DBA organization can afford. This powerful or developer, you need a simple-to- data modeling solution supports “I’ve used quite a few use data modeling tool for database everyday design and modification tasks, other tools, and I can design, data structure modification making it easier than ever to: only conclude that Toad and document creation. Enterprise • Create high-quality logical and physical Data Modeler is without solutions are too expensive and so data models question the killer app in complicated they often require in- • Visualize and understand data structures this category.” depth training, which interferes with and relationships Steve Callan productivity. • Deploy accurate changes to the databasejournal.com data structure Toad™ Data Modeler simplifies • Document projects for better database design, maintenance and team communication Benefits: documentation — at a price your • Supports both forward and reverse engineering • Offers compare and sync (model to model, model to database and database to model) • Supports multiple databases, including Oracle®, IBM® DB2®, SQL Server®, MySQL® and SAP® • Provides an intuitive interface • Requires minimal space and designed for easy installation Enable extensibility Database server (continued) Toad Data Modeler v5.5 Modify every object in the “scriptable” System requirements SAP SQL Anywhere® 11 application. Toad Data Modeler is a ® highly customizable program that Processor Teradata 13 adjusts to your organization’s needs 1GHz or faster 32-bit (x86) or Cloud database server or requirements. 64-bit (x64) CPU Oracle databases running on Edit on screen Amazon EC2® Memory Select a database object from the Minimum 1GB, 4GB SQL Server running on Microsoft physical model and simply change recommended Azure it on the screen for significant time- MySQL database running on savings. -

Best Practices for Setting up Netvault Smartdisk on a DR Disk Backup Appliance
Best Practices for Setting up NetVault SmartDisk on a DR Disk Backup Appliance A Dell Technical White Paper © 2013 Dell Inc. All Rights Reserved. Dell and the Dell logo, and other Dell names and marks are trademarks of Dell Inc. in the US and worldwide. NetVault is a trademark of Dell-Quest. 2 Setting up NetVault SmartDisk on the Dell™ DR4X00 Disk Backup Appliance Table of contents Introduction ....................................................................................................................................................................................... 4 Executive Summary .......................................................................................................................................................................... 5 1 Technical Setup/configuration Best Practices ..................................................................................................................... 6 1.1 General Setup /configuration Best Practices ............................................................................................................. 6 1.2 DR4X00 Setup/configuration Best Practices ............................................................................................................. 6 1.3 NetVault Setup /configuration Best Practices ........................................................................................................... 6 2 Install and Configure the DR4X00 ......................................................................................................................................... -

Dell Netvault Backup DR Series Backup Appliance Application Note
Dell™ DR Series Appliance Virtual Tape Library Best Practices Topics covered: - Dell DR VTL Container - NetVault nVTL A Dell Technical White Paper © 2014 Dell Inc. All Rights Reserved. Dell, the Dell logo, and NetVault are trademarks of Dell Inc. Linux is a registered trademark of Linus Torvalds in the United States, other countries, or both. UNIX is a registered trademark of The Open Group in the United States and other countries. VMware and vSphere are registered trademarks of VMware, Inc. in the United States and/or other jurisdictions. Hyper-V and Windows are registered trademarks of Microsoft Corporation in the United States and/or other countries. Table of contents Introduction .................................................................................................................................................................3 Executive Summary ....................................................................................................................................................5 Pros and Cons of each VTL Technique .................................................................................................................6 Technical setup and configuration – DR VTL Container .................................................................................... 7 General setup and configuration – DR VTL Container ......................................................................... 7 DR Series appliance setup and configuration – DR VTL Container .................................................. 7 NetVault -

Toad for Oracle 12.11 Editions Installation Guide
Toad for Oracle 12.11 Editions Installation Guide © 2017 Quest Software Inc. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this guide is furnished under a software license or nondisclosure agreement. This software may be used or copied only in accordance with the terms of the applicable agreement. No part of this guide may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying and recording for any purpose other than the purchaser’s personal use without the written permission of Quest Software Inc. The information in this document is provided in connection with Quest Software products. No license, express or implied, by estoppel or otherwise, to any intellectual property right is granted by this document or in connection with the sale of Quest Software products. EXCEPT AS SET FORTH IN THE TERMS AND CONDITIONS AS SPECIFIED IN THE LICENSE AGREEMENT FOR THIS PRODUCT, QUEST SOFTWARE ASSUMES NO LIABILITY WHATSOEVER AND DISCLAIMS ANY EXPRESS, IMPLIED OR STATUTORY WARRANTY RELATING TO ITS PRODUCTS INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, OR NON-INFRINGEMENT. IN NO EVENT SHALL QUEST SOFTWARE BE LIABLE FOR ANY DIRECT, INDIRECT, CONSEQUENTIAL, PUNITIVE, SPECIAL OR INCIDENTAL DAMAGES (INCLUDING, WITHOUT LIMITATION, DAMAGES FOR LOSS OF PROFITS, BUSINESS INTERRUPTION OR LOSS OF INFORMATION) ARISING OUT OF THE USE OR INABILITY TO USE THIS DOCUMENT, EVEN IF QUEST SOFTWARE HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. Quest Software makes no representations or warranties with respect to the accuracy or completeness of the contents of this document and reserves the right to make changes to specifications and product descriptions at any time without notice. -

Netvault Backup
Quest® NetVault® Backup 12.1 Release Notes September 2018 These release notes provide information about the Quest® NetVault® Backup release. Topics: • About this release • New Features • Enhancements • Resolved issues • Known issues • System requirements • Product licensing • Upgrade and installation instructions • More resources • Globalization • About us About this release Quest NetVault Backup (NetVault Backup) offers the most advanced, cross-platform data protection capabilities on the market and unsurpassed ease of use, out-of-the-box deployment, and pain-free scalability. NetVault Backup allows you to safeguard your data and applications in both physical and virtual environments from one intuitive user interface and to protect a massive number of servers that contain many petabytes of data. NetVault Backup also features heterogeneous support, so you can safeguard data on a wide range of operating systems, applications, databases, processor architectures, and networked storage devices. Such cross-platform versatility makes it easy for you to tailor NetVault Backup to match the ever-changing and growing landscape of your IT infrastructure. NetVault Backup 12.1 is a minor release, with enhanced features and functionality. For complete product documentation, visit https://support.quest.com/technical-documents. Quest NetVault Backup 12.1 1 Release Notes New Features New feature in NetVault Backup 12.1: • Added support for Quest® Foglight® for Virtualization, Enterprise Edition 8.8 or later. • Added support for push installation on Linux-based machines. (DNAD-703) • Added support for using as a managed service provider (MSP). (NVBU-17607) • Added support for Active Directory (AD) integration with Linux using Lightweight Directory Access Protocol (LDAP). (DNAD-707, DNAD-315) • Added a Secure Mode feature for AD user management. -
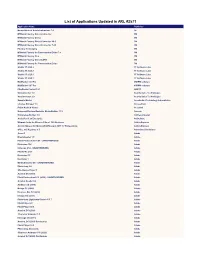
List of Applications Updated in ARL #2571
List of Applications Updated in ARL #2571 Application Name Publisher Nomad Branch Admin Extensions 7.0 1E M*Modal Fluency Direct Connector 3M M*Modal Fluency Direct 3M M*Modal Fluency Direct Connector 10.0 3M M*Modal Fluency Direct Connector 7.85 3M Fluency for Imaging 3M M*Modal Fluency for Transcription Editor 7.6 3M M*Modal Fluency Flex 3M M*Modal Fluency Direct CAPD 3M M*Modal Fluency for Transcription Editor 3M Studio 3T 2020.2 3T Software Labs Studio 3T 2020.8 3T Software Labs Studio 3T 2020.3 3T Software Labs Studio 3T 2020.7 3T Software Labs MailRaider 3.69 Pro 45RPM software MailRaider 3.67 Pro 45RPM software FineReader Server 14.1 ABBYY VoxConverter 3.0 Acarda Sales Technologies VoxConverter 2.0 Acarda Sales Technologies Sample Master Accelerated Technology Laboratories License Manager 3.5 AccessData Prizm ActiveX Viewer AccuSoft Universal Restore Bootable Media Builder 11.5 Acronis Knowledge Builder 4.0 ActiveCampaign ActivePerl 5.26 Enterprise ActiveState Ultimate Suite for Microsoft Excel 18.5 Business Add-in Express Add-in Express for Microsoft Office and .NET 7.7 Professional Add-in Express Office 365 Reporter 3.5 AdminDroid Solutions Scout 1 Adobe Dreamweaver 1.0 Adobe Flash Professional CS6 - UNAUTHORIZED Adobe Illustrator CS6 Adobe InDesign CS6 - UNAUTHORIZED Adobe Fireworks CS6 Adobe Illustrator CC Adobe Illustrator 1 Adobe Media Encoder CC - UNAUTHORIZED Adobe Photoshop 1.0 Adobe Shockwave Player 1 Adobe Acrobat DC (2015) Adobe Flash Professional CC (2015) - UNAUTHORIZED Adobe Acrobat Reader DC Adobe Audition CC (2018) -

Toad® Data Modeler 6.5.5
Toad® Data Modeler 6.5.5 Release Notes Wednesday, November 7, 2018 These release notes provide information about the Toad® Data Modeler release. About Toad Data Modeler New in Toad Data Modeler 6.5.5 Resolved issues Known issues System requirements Supported database platforms Product licensing Getting started with Toad Data Modeler 6.5.5 Globalization About Us About Toad Data Modeler Toad Data Modeler helps organizations create, maintain and document their database systems with an easy-to- use graphical interface into new or existing database structures. Toad Data Modeler enables users to reverse engineer database structures, update models, design and generate SQL, compare models and generate alter scripts, create HTML or RTF reports, in addition to versioning of database designs and creation of to-do lists. Toad Data Modeler 6.5.5 is a patch release. It is a replacement of the previous 6.5 release that contains extra resolved issues. See New in Toad Data Modeler 6.5.5 and Resolved issues for more information. Toad Data Modeler is released in 32-bit and 64-bit versions. The 64-bit version of the application has a significantly higher memory limit which should resolve several common issues incl. out of memory errors, which occurred when working with complex models. However, in order to reverse engineer databases that require a client you need a corresponding version of the client, i.e. 32-bit or 64-bit. Toad Data Modeler 6.5.5 1 Release Notes New in Toad Data Modeler 6.5.5 Database features Support for Oracle 18c l Oracle 18c is now fully