C:\Users\Petermenell\Desktop\BCLT Software Conference\Rise of The
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

IJIMAI20163 6.Pdf
INTERNATIONAL JOURNAL OF INTERACTIVE MULTIMEDIA AND ARTIFICIAL INTELLIGENCE ISSN: 1989-1660–VOL. III, NUMBER 6 IMAI RESEARCH GROUP COUNCIL Executive Director - Dr. Jesús Soto Carrión, Pontifical University of Salamanca, Spain Research Director - Dr. Rubén González Crespo, Universidad Internacional de La Rioja - UNIR, Spain Financial Director - Dr. Oscar Sanjuán Martínez, ElasticBox, USA Office of Publications Director - Lic. Ainhoa Puente, Universidad Internacional de La Rioja - UNIR, Spain Director, Latin-America regional board - Dr. Carlos Enrique Montenegro Marín, Francisco José de Caldas District University, Colombia EDITORIAL TEAM Editor-in-Chief Dr. Rubén González Crespo, Universidad Internacional de La Rioja – UNIR, Spain Associate Editors Dr. Jordán Pascual Espada, ElasticBox, USA Dr. Juan Pavón Mestras, Complutense University of Madrid, Spain Dr. Alvaro Rocha, University of Coimbra, Portugal Dr. Jörg Thomaschewski, Hochschule Emden/Leer, Emden, Germany Dr. Carlos Enrique Montenegro Marín, Francisco José de Caldas District University, Colombia Dr. Vijay Bhaskar Semwal, Indian Institute of Technology, Allahabad, India Editorial Board Members Dr. Rory McGreal, Athabasca University, Canada Dr. Abelardo Pardo, University of Sidney, Australia Dr. Hernán Sasastegui Chigne, UPAO, Perú Dr. Lei Shu, Osaka University, Japan Dr. León Welicki, Microsoft, USA Dr. Enrique Herrera, University of Granada, Spain Dr. Francisco Chiclana, De Montfort University, United Kingdom Dr. Luis Joyanes Aguilar, Pontifical University of Salamanca, Spain Dr. Ioannis Konstantinos Argyros, Cameron University, USA Dr. Juan Manuel Cueva Lovelle, University of Oviedo, Spain Dr. Pekka Siirtola, University of Oulu, Finland Dr. Francisco Mochón Morcillo, National Distance Education University, Spain Dr. Manuel Pérez Cota, University of Vigo, Spain Dr. Walter Colombo, Hochschule Emden/Leer, Emden, Germany Dr. Javier Bajo Pérez, Polytechnic University of Madrid, Spain Dr. -
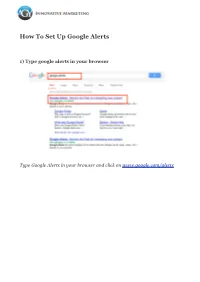
How to Set up Google Alerts
How To Set Up Google Alerts 1) Type google alerts in your browser Type Google Alerts in your browser and click on www.google.com/alerts 2) Set up your alerts In Search Query put in the topics you want google to source out for you. It might be of interest to have your name, your company domain, competitors domains, keywords you'd like to source information about or whatever you'd like to research. Enter the email address you want the alerts to go to. 3) Verify your alert Login into your email address that the alert is going to and verify it by clicking on the link. 4) Set up folders/labels so alerts skip your inbox (we will use Gmail for this example) 1) Tick the alerts that have come to your inbox. 2) Click on More, in the drop down menu choose 'Filter messages like these' 5) Create filter 1) Just click on 'create filter with this search' 6) Applying label/folder for alert to skip inbox. (Gmail calls folders labels, you can set them up under 'settings', 'labels'. 1) Tick skip the inbox (helps keep your inbox free) 2) Tick apply label 3) Choose what label (Here we have called it Alerts) 4) Tick to apply other alerts if found any 5) Create filter This is one easy way for information you are interested in to come to you. By setting up Alert Folders or Labels as Gmail calls them, they won't clog up your inbox, keeping it clear and leaving you to your choosing when you want to check your alerts for any useful information. -

Recent Developments in Cybersecurity Melanie J
American University Business Law Review Volume 2 | Issue 2 Article 1 2013 Fiddling on the Roof: Recent Developments in Cybersecurity Melanie J. Teplinsky Follow this and additional works at: http://digitalcommons.wcl.american.edu/aublr Part of the Law Commons Recommended Citation Teplinsky, Melanie J. "Fiddling on the Roof: Recent Developments in Cybersecurity." American University Business Law Review 2, no. 2 (2013): 225-322. This Article is brought to you for free and open access by the Washington College of Law Journals & Law Reviews at Digital Commons @ American University Washington College of Law. It has been accepted for inclusion in American University Business Law Review by an authorized administrator of Digital Commons @ American University Washington College of Law. For more information, please contact [email protected]. ARTICLES FIDDLING ON THE ROOF: RECENT DEVELOPMENTS IN CYBERSECURITY MELANIE J. TEPLINSKY* TABLE OF CONTENTS Introduction .......................................... ..... 227 I. The Promise and Peril of Cyberspace .............. ........ 227 II. Self-Regulation and the Challenge of Critical Infrastructure ......... 232 III. The Changing Face of Cybersecurity: Technology Trends ............ 233 A. Mobile Technology ......................... 233 B. Cloud Computing ........................... ...... 237 C. Social Networking ................................. 241 IV. The Changing Face of Cybersecurity: Cyberthreat Trends ............ 244 A. Cybercrime ................................. ..... 249 1. Costs of Cybercrime -

The Performance Paradox of the JVM: Why More Hardware Means More
Expert Tip The Performance Paradox of the JVM: Why More Hardware Means More As computer hardware gets cheaper and faster, administrators managing Java based servers are frequently encountering serious problems when managing their runtime environments. JVM handles the task of garbage collection for the developer - cleaning up the space a developer has allocated for objects once an instance no longer has any references pointing to it. Some garbage collection is done quickly and invisibly. But certain sanitation tasks, which fortunately occur with minimal frequency, take significantly longer, causing the JVM to pause, and raising the ire of end users and administrators alike. Read this TheServerSide.com Expert Tip to better understand the JVM performance problem, how the JVM manages memory and how best to approach JVM Performance. Sponsored By: TheServerSide.com Expert Tip The Performance Paradox of the JVM: Why More Hardware Means More Expert Tip The Performance Paradox of the JVM: Why More Hardware Means More Table of Contents The Performance Paradox of the JVM: Why More Hardware Means More Failures Resources from Azul Systems Sponsored By: Page 2 of 8 TheServerSide.com Expert Tip The Performance Paradox of the JVM: Why More Hardware Means More The Performance Paradox of the JVM: Why More Hardware Means More Failures By Cameron McKenzie The Problem of the Unpredictable Pause As computer hardware gets cheaper and faster, administrators managing Java based servers are frequently encountering serious problems when managing their runtime environments. While our servers are getting decked out with faster and faster hardware, the Java Virtual Machines (JVMs) that are running on them can't effectively leverage the extra hardware without hitting a wall and temporarily freezing. -

Java (Programming Langua a (Programming Language)
Java (programming language) From Wikipedia, the free encyclopedialopedia "Java language" redirects here. For the natural language from the Indonesian island of Java, see Javanese language. Not to be confused with JavaScript. Java multi-paradigm: object-oriented, structured, imperative, Paradigm(s) functional, generic, reflective, concurrent James Gosling and Designed by Sun Microsystems Developer Oracle Corporation Appeared in 1995[1] Java Standard Edition 8 Update Stable release 5 (1.8.0_5) / April 15, 2014; 2 months ago Static, strong, safe, nominative, Typing discipline manifest Major OpenJDK, many others implementations Dialects Generic Java, Pizza Ada 83, C++, C#,[2] Eiffel,[3] Generic Java, Mesa,[4] Modula- Influenced by 3,[5] Oberon,[6] Objective-C,[7] UCSD Pascal,[8][9] Smalltalk Ada 2005, BeanShell, C#, Clojure, D, ECMAScript, Influenced Groovy, J#, JavaScript, Kotlin, PHP, Python, Scala, Seed7, Vala Implementation C and C++ language OS Cross-platform (multi-platform) GNU General Public License, License Java CommuniCommunity Process Filename .java , .class, .jar extension(s) Website For Java Developers Java Programming at Wikibooks Java is a computer programming language that is concurrent, class-based, object-oriented, and specifically designed to have as few impimplementation dependencies as possible.ble. It is intended to let application developers "write once, run ananywhere" (WORA), meaning that code that runs on one platform does not need to be recompiled to rurun on another. Java applications ns are typically compiled to bytecode (class file) that can run on anany Java virtual machine (JVM)) regardless of computer architecture. Java is, as of 2014, one of tthe most popular programming ng languages in use, particularly for client-server web applications, witwith a reported 9 million developers.[10][11] Java was originallyy developed by James Gosling at Sun Microsystems (which has since merged into Oracle Corporation) and released in 1995 as a core component of Sun Microsystems'Micros Java platform. -
R, the Software, Finds Fans
R, the Software, Finds Fans in Data Analysts - NYTimes.com http://www.nytimes.com/2009/01/07/technology/business-computing/0... W elcom e to Get Started TimesPeople Lets You Share and Discover the Best of NYTimes.com 12:48 PM Tim esPeople No, thanks W hat‘s this? HOME PAGE TODAY'S PAPER VIDEO MOST POPULAR TIMES TOPICS My Account W elcome, corostat Log Out Help Search All NYTimes.com Business Com puting WORLD U.S. N.Y. / REGION BUSINESS TECHNOLOGY SCIENCE HEALTH SPORTS OPINION ARTS STYLE TRAVEL JOBS REAL ESTATE AUTOS Search Technology Inside Technology Bits Personal Tech » Internet Start-Ups Business Computing Companies Blog » Cellphones, Cameras, Computers and more Data Analysts Captivated by R‘s Power More Articles in Technology » Stuart Isett for The New York Times R first appeared in 1996, when the statistics professors Robert Gentleman, left, and Ross Ihaka released the code as a free software package. By ASHLEE VANCE Published: January 6, 2009 E-MAIL To some people R is just the 18th letter of the alphabet. To others, PRINT it‘s the rating on racy movies, a measure of an attic‘s insulation or SINGLE PAGE Advertise on NYTimes.com what pirates in movies say. REPRINTS SAVE Breaking News Alerts by E-Mail R is also the name of a popular SHARE Sign up to be notified when important news breaks. Related programming language used by a colombi@ unibg.it Bits: R You Ready for R? growing number of data analysts Change E-mail Address | Privacy Policy The R Project for Statistical inside corporations and academia. -

The Java® Language Specification Java SE 8 Edition
The Java® Language Specification Java SE 8 Edition James Gosling Bill Joy Guy Steele Gilad Bracha Alex Buckley 2015-02-13 Specification: JSR-337 Java® SE 8 Release Contents ("Specification") Version: 8 Status: Maintenance Release Release: March 2015 Copyright © 1997, 2015, Oracle America, Inc. and/or its affiliates. 500 Oracle Parkway, Redwood City, California 94065, U.S.A. All rights reserved. Oracle and Java are registered trademarks of Oracle and/or its affiliates. Other names may be trademarks of their respective owners. The Specification provided herein is provided to you only under the Limited License Grant included herein as Appendix A. Please see Appendix A, Limited License Grant. To Maurizio, with deepest thanks. Table of Contents Preface to the Java SE 8 Edition xix 1 Introduction 1 1.1 Organization of the Specification 2 1.2 Example Programs 6 1.3 Notation 6 1.4 Relationship to Predefined Classes and Interfaces 7 1.5 Feedback 7 1.6 References 7 2 Grammars 9 2.1 Context-Free Grammars 9 2.2 The Lexical Grammar 9 2.3 The Syntactic Grammar 10 2.4 Grammar Notation 10 3 Lexical Structure 15 3.1 Unicode 15 3.2 Lexical Translations 16 3.3 Unicode Escapes 17 3.4 Line Terminators 19 3.5 Input Elements and Tokens 19 3.6 White Space 20 3.7 Comments 21 3.8 Identifiers 22 3.9 Keywords 24 3.10 Literals 24 3.10.1 Integer Literals 25 3.10.2 Floating-Point Literals 31 3.10.3 Boolean Literals 34 3.10.4 Character Literals 34 3.10.5 String Literals 35 3.10.6 Escape Sequences for Character and String Literals 37 3.10.7 The Null Literal 38 3.11 Separators -

Google Wave Failure: Lesson Learned for Diffusion of an Online Collaboration Tool
GOOGLE WAVE FAILURE: LESSON LEARNED FOR DIFFUSION OF AN ONLINE COLLABORATION TOOL Laddawan Kaewkitipong Peter Ractham Department of Management Information Systems Thammasat Business School, Thammasat University Thailand INTRODUCTION Background and Motivation Collaboration has become increasingly important to the success of today’s enterprises. Modern organizations have been attempting to capitalize on their ability to collaborate between business units and manufacturing facilities to develop better products and services [17]. To achieve their goals, they no longer rely only on internal collaboration within their organization, but also on working closely and exchanging ideas with external partners. In other words, collaboration is viewed as a critical success factor in achieving a sustainable competitive advantage [2]. The need to collaborate is also seen in everyday’s life. A family, which has one or more family members who live abroad, might need to find a way to plan their holiday together. A group of friends who want to organize a party may need a tool to help them obtain common decisions more efficiently. As a result, many collaboration tools have been implemented to facilitate this kind of information sharing as well as decision-making tasks. Nevertheless, little has been reported on adoption success of such tools. In fact, diffusion of collaboration tools still remains as one of the most challenging problems in the area of IS research [31, 43]. Challenged by the problems and considering collaboration important activities, Google has launched many online tools to promote collaboration. Some of their popular tools are Gmail, Google Docs, and Google Calendar. An infamous tool, Google Wave, was one of the most ambitious products which many features that can help to facilitate online collaboration. -

From Safe Harbor to Choppy Waters: Youtube, the Digital Millennium Copyright Act,And a Much Needed Change of Course
Vanderbilt Journal of Entertainment & Technology Law Volume 10 Issue 1 Issue 1 - Fall 2007 Article 3 2007 From Safe Harbor to Choppy Waters: YouTube, the Digital Millennium Copyright Act,and a Much Needed Change of Course Lauren B. Patten Follow this and additional works at: https://scholarship.law.vanderbilt.edu/jetlaw Part of the Intellectual Property Law Commons, and the Internet Law Commons Recommended Citation Lauren B. Patten, From Safe Harbor to Choppy Waters: YouTube, the Digital Millennium Copyright Act,and a Much Needed Change of Course, 10 Vanderbilt Journal of Entertainment and Technology Law 179 (2020) Available at: https://scholarship.law.vanderbilt.edu/jetlaw/vol10/iss1/3 This Note is brought to you for free and open access by Scholarship@Vanderbilt Law. It has been accepted for inclusion in Vanderbilt Journal of Entertainment & Technology Law by an authorized editor of Scholarship@Vanderbilt Law. For more information, please contact [email protected]. From Safe Harbor to Choppy Waters: YouTube, the Digital Millennium Copyright Act, and a Much Needed Change of Course ABSTRACT YouTube.com, named Time magazine's "Invention of the Year" for 2006 and widely recognized as the most-visited video site on the Internet, has changed the face of online entertainment. With the site's acquisition by Google in October 2006, the possibilities for YouTube's growth became truly endless. However, there is a darker side to the story of the Internet sensation, one that is grounded in its potential liability for copyright infringement. The issue is that many of the most-viewed and most-popular videos on the site are copyrighted. -

Tulane Journal of Technology and Intellectual Property
TULANE JOURNAL OF TECHNOLOGY AND INTELLECTUAL PROPERTY VOLUME 10 FALL 2007 Increasing Access to Knowledge Through Fair Use—Analyzing the Google Litigation To Unleash Developing Countries Douglas L. Rogers* I. ACCESS TO KNOWLEDGE ...................................................................... 3 II. IN SPITE OF THE COPYING OF COMPLETE WORKS, THE PROVISION OF LIMITED INFORMATION FROM THE GOOGLE DATABASE MAKES THE LIBRARY PROJECT A FAIR USE ........................ 7 A. The Google Library Litigation ................................................... 7 B. Fair Use Is a Crucial Element of the Copyright Balance ........ 11 C. Increasing Access Favors Fair Use ........................................... 21 1. Sony: Time-Shifting Is a Fair Use ................................... 21 2. Campbell: Increasing Access Through Transformative Works Favors Fair Use ........................... 27 3. Summary .......................................................................... 30 D. It Is the End Result that Counts in Determining Fair Use ............................................................................................. 31 1. Fair Use Seeks a Balanced Result ................................... 31 2. Interim Scanning of a Picture and Then Modifying It ...................................................................... 33 a. Kelly v. Arriba Soft Corp. ....................................... 33 b. Bill Graham Archives v. Dorling Kindersley Ltd. ............................................................................ 35 * © 2007 -

3. Internet – Participating in the Knowledge Society
3. Internet – Participating in the knowledge society “Knowledge is power. Information is liberating. Education is the premise of progress, in every society, in every family.” Kofi Annan, former Secretary General of the United Nations, January 1997-December 2006 CHECKLIST FACT SHEET 10 – SEARCHING FOR INFORMATION Do you read the disclaimer when you are consulting a website? How can you be sure the information you find is factual and objective? Do you consult several websites to check your facts? CHECKLIST FACT SHEET 11 – FINDING QUALITY INFORMATION ON THE WEB Before downloading files, do you check that your anti-virus software is active? If you get your news from the Internet, do you seek multiple perspectives on the same story? Clean out your cookies from time to time to avoid being “profiled” by search engines. CHECKLIST FACT SHEET 12 – DISTANCE LEARNING AND MOOCs Choose a method of distance learning that is appropriate for you: determine what type of learning (synchronous, asynchronous, open schedule, hybrid distance learning) will best help you reach your goals. Before selecting a distance learning course, research the reviews – both from students and teachers. Take adequate precautions to ensure that your computer equipment and software is secure from hackers, viruses and other threats. CHECKLIST FACT SHEET 13 – SHOPPING ONLINE Do not make online purchases on unsecure Internet connections. Understand and agree to the key information provided about the product or service. Disable in-app purchases on your smartphone or tablet. Do not believe all user recommendations you see, creating “user” recommendations can also be a money-making business. Fact sheet 11 Finding quality information on the Web he original idea behind the creation of the Internet1 was to develop an electronic library for the Teasy access and distribution of information2. -

Efficient Monitoring Algorithm for Fast News Alerts
1 Efficient Monitoring Algorithm for Fast News Alerts Ka Cheung Sia, Junghoo Cho, and Hyun-Kyu Cho Abstract— Recently, there has been a dramatic increase in and its appearance at the aggregator? Note that the aggregation the use of XML data to deliver information over the Web. can be done either at a desktop (e.g., RSS feed readers) or at Personal weblogs, news Web sites, and discussion forums are a central server (e.g., Personalized Yahoo/Google homepage). now publishing RSS feeds for their subscribers to retrieve new postings. As the popularity of personal weblogs and the RSS While some of our developed techniques can be applied to the feeds grow rapidly, RSS aggregation services and blog search desktop-based aggregation, in this paper we primarily focus on engines have appeared, which try to provide a central access the server-based aggregation scenario. This problem is similar point for simpler access and discovery of new content from a to the index refresh problem for Web-search engines [7], [9], large number of diverse RSS sources. In this paper, we study how [11], [13], [15], [30], [31], [40], but two important properties the RSS aggregation services should monitor the data sources to retrieve new content quickly using minimal resources and to of the information in the RSS domain make this problem provide its subscribers with fast news alerts. We believe that unique and interesting: the change characteristics of RSS sources and the general user • The information in the RSS domain is often time sensi- access behavior pose distinct requirements that make this task significantly different from the traditional index refresh problem tive.