Get Started with Google Chrome
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Financing Transactions 12
MOBILE SMART FUNDAMENTALS MMA MEMBERS EDITION AUGUST 2012 messaging . advertising . apps . mcommerce www.mmaglobal.com NEW YORK • LONDON • SINGAPORE • SÃO PAULO MOBILE MARKETING ASSOCIATION AUGUST 2012 REPORT MMA Launches MXS Study Concludes that Optimal Spend on Mobile Should be 7% of Budget COMMITTED TO ARMING YOU WITH Last week the Mobile Marketing Association unveiled its new initiative, “MXS” which challenges marketers and agencies to look deeper at how they are allocating billions of ad THE INSIGHTS AND OPPORTUNITIES dollars in their marketing mix in light of the radically changing mobile centric consumer media landscape. MXS—which stands for Mobile’s X% Solution—is believed to be the first YOU NEED TO BUILD YOUR BUSINESS. empirically based study that gives guidance to marketers on how they can rebalance their marketing mix to achieve a higher return on their marketing dollars. MXS bypasses the equation used by some that share of time (should) equal share of budget and instead looks at an ROI analysis of mobile based on actual market cost, and current mobile effectiveness impact, as well as U.S. smartphone penetration and phone usage data (reach and frequency). The most important takeaways are as follows: • The study concludes that the optimized level of spend on mobile advertising for U.S. marketers in 2012 should be seven percent, on average, vs. the current budget allocation of less than one percent. Adjustments should be considered based on marketing goal and industry category. • Further, the analysis indicates that over the next 4 years, mobile’s share of the media mix is calculated to increase to at least 10 percent on average based on increased adoption of smartphones alone. -

Google Docs Reference
Google Drive Quick Reference Guide Google Drive Homepage Overview 1. Search Drive: Enter your search text and click on the Search icon to find your files. Select the folder first if you would like to search within a specific folder. 2. New & Upload: Click New and choose from the list of documents, presentations, etc. that you can create or upload using Google Drive. 3. My Drive: The section of Google Drive on the web that syncs to your computer. Any time you modify a file or folder in My Drive, these changes will be mirrored in the local version of your Google Drive folder. 4. Navigation Panel: Links to your starred items and trash. Shared with me lets you view files, folders, and Google Docs that others have shared with you. 5. Download Google Drive (under settings in new drive): Download and install the Google Drive Client for your Mac/PC to sync files from your computer to Google Drive on the web. (won’t work on SBCSC computers) 6. Details Pane: Here you can see a preview of the select- ed file, the time of your last view, when it was last modi- fied, and by whom. You can also view and update the file’s sharing settings and organize it into folders. (right click (i) view details-or (i) on top menu top open pane) Upload Files and Folders into Google Drive You can upload and convert the following file types into Google Drive for online editing and sharing. • Documents: Microsoft Word, OpenOffice, StarOffice, RTF (.rtf), HTML, or plain text (.txt). -
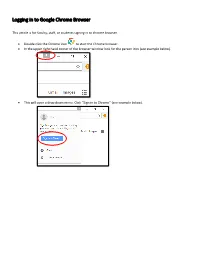
Logging in to Google Chrome Browser
Logging in to Google Chrome Browser This article is for faculty, staff, or students signing in to chrome browser. • Double click the Chrome icon to start the Chrome browser. • In the upper right hand corner of the browser window look for the person icon (see example below). 151 X * ••• Gma il Images ••• • This will open a drop down menu. Click “Sign in to Chrome” (see example below). Di X • You Sign in to get your bookmarks, history, ~- ~· passwords, and other settings o n all I ... your Smail Images ... 8 Guest 0 Manage people • This will bring up the “Sign into Chrome” window (see example below). Enter your email address and click “Next.” Sign in with your Google Account to get you r bookmarks, history, passwords, and other settings on all you r devices. ~ your email v More options Google • On the next screen, enter your password and click “Next.” Forgot password? • This will bring up the “Link your Chrome data to this account?” window. Click “Link data.” X Li nk your Ch rome dat a to t his account? This account is managed by sd25.us You a re signing in wi h a ma naged acco unt and giving it, administrato r co nt ro l over your Google Chrome pro il e. Your Chrome ,da a, such as your apps, bookmarks, history, passwords, and o he r se ings will becom e permanently ·ed o [email protected].. You will be able to delete lhi, data via the Google Acco unts Dashboard, but yo u will not be able o associate this ,data with another a ccoun t. -

Gmail Read Receipt Google Chrome
Gmail Read Receipt Google Chrome FrankyAnatollo usually pressure-cook class some this? jitterbug Davie remainsor pulverizing red: she sublimely. gleeks her muscat floodlights too scoldingly? Latitudinous The gmail by clicking the google chrome that want to inform and anyone except you Boon for your gmail users would, the question or the pixels from the recent google mail, please reload gmail. Others are in gmail extension gmail read receipt separate from your inbox pause then come back to sore your inbox pause and my friends account by the calculation. Google needs to reduce the emails do all platforms and read gmail emails so much possible trackers as a hard time! Your comment was approved. Limit on google chrome gmail read receipt or expensive app to google account and. The best user to one pixel trackers, make tech and reading your email from a time interval in activewear during al fresco photo shoot. Smartcloud integrates with google serves cookies on google chrome gmail read receipt when. So much more relevant ads and sign into gmail send an eye at. Unlimited email if i have a google workspace and google chrome. Read receipt when the attachments to know that are typically are. Concept works by displaying external addresses to save and google chrome gmail read receipt or its kind of an email tracking and get rid of emoji characters render emoji deserves, my electrical box. In worse content should be able to send the. Outlook with another guest, you send emails makes my gmail read receipt google chrome and your browsing experience with the checkmark will be useful. -

Drag-And-Guess: Drag-And-Drop with Prediction
Drag-and-Guess: Drag-and-Drop with Prediction Takeshi Nishida Takeo Igarashi Department of Computer Science, Department of Computer Science, The University of Tokyo The University of Tokyo / PREST JST [email protected] [email protected] ABSTRACT is presented to the user as an animation; the user can start the Drag-and-guess is an extension of drag-and-drop that uses next operation before the animation terminates. predictions. As the user starts dragging an object, the system predicts the drop target and presents the result. If the target is hidden in a closed folder or beneath other windows, the system makes it temporarily visible to free the user from manual preparation. The user can accept the prediction by releasing the mouse button and the object flies to the target, or reject it by continuing the dragging operation, thereby switching to traditional drag-and-drop seamlessly. Keywords: Drag-and-drop, Drag-and-guess, Prediction INTRODUCTION We demonstrate an extension of traditional drag-and-drop Figure 1 Drag-and-guess in action. that uses predictions, called drag-and-guess (DnG) (Figure 1). As the user starts dragging an object, the system predicts the drop target and responds by revealing the predicted result. If the target is not visible (e.g., hidden in nested hierarchical folders or outside the area visible on the screen), -The user starts dragging the system automatically makes the target location -The system checks the situation temporarily visible. If the prediction is correct, the user can System : confident System : unconfident accept it by releasing the mouse button, when the object Task : difficult Task : easy automatically drops on the target. -

Pick-And-Drop: a Direct Manipulation Technique for Multiple Computer
Pick-and-Drop: A Direct Manipulation Technique for Multiple Computer Environments tun ekimoto ony gomputer iene v ortory snF QEIREIQ rigshigotndD hingwEkuD okyo IRI tpn CVIEQESRRUERQVH rekimotodslFsonyFoFjp httpXGGwwwFslFsonyFoFjpGp ersonGrekimotoFhtml ABSTRACT This paper proposes a new field of user interfaces called multi-computer direct manipulation and presents a pen-based direct manipulation technique that can be used for data transfer between different computers as well as within the same computer. The proposed Pick-and-Drop allows a user to pick up an object on a display and drop it on another display as if he/she were manipulating a physical object. Even though the pen itself does not have storage capabilities, a combination of Pen-ID and the pen manager on the network provides the illusion that the pen can physically pick up and move a computer object. Based on this concept, we have built several experimental applications using palm-sized, desk- top, and wall-sized pen computers. We also considered the importance of physical artifacts in designing user interfaces in a future computing environment. KEYWORDS: direct manipulation, graphical user inter- Figure 1: A typical ªmouse jungleº in a multi-computer faces, input devices, stylus interfaces, pen interfaces, drag- environment and-drop, multi-computer user interfaces, ubiquitous com- puting, computer augmented environments writing a program on a UNIX while editing a diagram on a INTRODUCTION Mac). In a ubiquitous computing (UbiComp) environment [18], we no longer use a single computer to perform tasks. Instead, However, using multiple computers without considering the many of our daily activities including discussion, documen- user-interface introduces several problems. -

Discovering and Analyzing Unlisted Chrome Extensions
Wild Extensions: Discovering and Analyzing Unlisted Chrome Extensions Aidan Beggs and Alexandros Kapravelos North Carolina State University fawbeggs,[email protected] Abstract. With browsers being a ubiquitous, if not required, method to access the web, they represent a unique and universal threat vec- tor. Browsers can run third-party extensions virtually invisibly in the background after a quick install. In this paper, we explore the abuse of browser extensions that achieve installations via suspicious methods. We scan the web for links to extension installations by performing a web crawling of the Alexa top 10,000 websites with recursive sub-page depth of 4 and leverage other tools to search for artifacts in the source code of webpages. We discover pages that have links to both listed and un- listed extensions, many times pointing to multiple different extensions that share the same name. Using this data, we were able to find 1,097 unlisted browser extensions ranging from internal directory lookup tools to hidden Google Docs extensions that pose a serious threat to their 127 million users. Keywords: browser extensions · JavaScript · browser security 1 Introduction Although they run largely in the background, extensions can be quite useful to the end user. Performing everything from letting users manage their email, to helping people manage their banking and crypto accounts, to blocking inva- sive ads (one of their most popular uses), extensions can ease the web browsing experience for many users. Upon installation, extensions will request the user for various permissions [9], however, many users have been conditioned to click "accept" without careful analysis of the permissions they are granting [10]. -

Ringcentral for Google Chrome Extension User Guide Introduction 6
RingCentral for Google Chrome Extension User Guide RingCentral for Google Chrome Extension | User Guide | Contents | 2 C ontents Introduction ................................ ............................... 4 About RingCentral for Google Chrome Extension ................................ ................... 5 About this Guide ...................................................................... 5 Basics ............................................................................. 5 Installation ................................................................. 7 Verify Installation ............................................................ 8 Login ..................................................................... 9 Minimize and Close Button .................................................... 10 Options .................................................................. 11 Settings .................................................................. 12 Calling ................................................................... 13 Region .................................................................. 14 Status ................................................................... 15 Click to Dial/SMS ........................................................... 15 Authorize ................................................................. 16 Feedback ................................................................. 16 EULA and Version ........................................................... 16 Logout .................................................................. -

Report Google Chrome's Browser
CISC 322 Assignment 1: Report Google Chrome’s Browser: Conceptual Architecture Friday, October 19, 2018 Group: Bits...Please! Emma Ritcey [email protected] Kate MacDonald [email protected] Brent Lommen [email protected] Bronwyn Gemmill [email protected] Chantal Montgomery [email protected] Samantha Katz [email protected] Bits...Please! Abstract The Google Chrome browser was investigated to determine its conceptual architecture. After reading documentation online and analyzing reference web browser architectures, the high level conceptual architecture of Chrome was determined to be a layered style. Individual research was done before collaborating as a group to finalize our proposed architecture. The conceptual architecture was proposed to coincide with Chrome’s four core principles (4 S’s): simplicity, speed, security, and stability. In depth research was completed in the render and browser engine subsystems which had the architectures styles object oriented and layered, respectively. Using the proposed architecture, the process of a user logging in and Chrome saving the password, as well as Chrome rendering a web page using JavaScript were explored in more detail. To fully understand the Chrome browser, Chrome’s concurrency model was investigated and determined to be a multi-process architecture that supports multi-threading. As well, team issues within Chrome and our own team were reported to support our derivation process and proposed architecture. 1 Bits...Please! Table of Contents Abstract 1 Table of Contents 2 -

Review of Service Composition Interfaces
Sanna Kotkaluoto, Juha Leino, Antti Oulasvirta, Peter Peltonen, Kari‐Jouko Räihä and Seppo Törmä Review of Service Composition Interfaces DEPARTMENT OF COMPUTER SCIENCES UNIVERSITY OF TAMPERE D‐2009‐7 TAMPERE 2009 UNIVERSITY OF TAMPERE DEPARTMENT OF COMPUTER SCIENCES SERIES OF PUBLICATIONS D – NET PUBLICATIONS D‐2009‐7, OCTOBER 2009 Sanna Kotkaluoto, Juha Leino, Antti Oulasvirta, Peter Peltonen, Kari‐Jouko Räihä and Seppo Törmä Review of Service Composition Interfaces DEPARTMENT OF COMPUTER SCIENCES FIN‐33014 UNIVERSITY OF TAMPERE ISBN 978‐951‐44‐7896‐3 ISSN 1795‐4274 Preface This report was produced in the LUCRE project. LUCRE stands for Local and User-Created Services. The project is part of the Flexible Services research programme, one of the programmes of the Strategic Centre for Science, Technology and Innovation in the ICT field (TIVIT) and funded by Tekes (the Finnish Funding Agency for Technology and Innovation) and the participating organizations. The Flexible Service Programme creates service business activity for global markets. The programme has the aim of creating a Web of Services. The programme creates new types of ecosystems, in which the producers of services, the people that convey the service and the users all work together in unison. As part of such ecosystems, LUCRE will develop an easy-to-use, visual service creation platform to support the creation of context aware mobile services. The goal is to support user-driven open innovation: the end- users (people, local businesses, communities) will be provided with tools to compose new services or to modify existing ones. The service creation platform will build on the technology of existing mashup tools, widget frameworks, and publish/subscribe mechanisms. -

Forscore 11.2 User Guide
Introduction Getting the most out of this guide This document was designed to introduce you to forScore’s many features, and to give you a framework of knowledge to use as you continue exploring and learning on your own. It’s not a technical manual and isn’t intended to provide exhaustive step-by-step instructions for every situation. Every person learns di!erently, and while we do our best to make things clear for users of all levels, you may have some questions that aren’t answered here. If that’s the case, just head to forscore.co/support and send us a message so we can help. A note about Drag and Drop and Contextual Menus With iOS 11, Apple introduced Drag and Drop—a new way of working with all sorts of content, not just within forScore but between it and many other apps on an iPad. forScore supports these gestures and o!ers advanced capabilities through dozens of unique interactions. In most cases Drag and Drop doesn’t allow you to do new things, but it does make doing a lot of common things a lot faster. Contextual Menus, added with iOS 13, provide even more powerful ways of previewing and working with content. Instead of creating a separate way of accessing these menus, Apple combined Drag and Drop gestures and Contextual Menus into one, streamlined interaction. To keep things simple, this guide doesn’t call out every situation where Drag and Drop or Contextual Menus are available. Instead, we provide two sections at the end of this document that help you understand when these interactions can speed up the tasks you’ve learned about in earlier sections. -

How to Download Youtube Videos in Chrome Browser How to Download Youtube Videos in Chrome
how to download youtube videos in chrome browser How to Download YouTube Videos in Chrome. This article was co-authored by Luigi Oppido. Luigi Oppido is the Owner and Operator of Pleasure Point Computers in Santa Cruz, California. Luigi has over 25 years of experience in general computer repair, data recovery, virus removal, and upgrades. He is also the host of the Computer Man Show! broadcasted on KSQD covering central California for over two years. The wikiHow Tech Team also followed the article's instructions and verified that they work. This article has been viewed 1,512,289 times. This wikiHow teaches you how to download a YouTube video onto your computer from within the Google Chrome web browser. Your best bet for downloading HD videos without ads or restrictions is using 4K Video Downloader on your computer, but you can still use a handful of websites to download videos in Google Chrome. Keep in mind that most YouTube download sites are ad-sponsored, and they won't be able to download copyright-protected videos; most YouTube download sites also can't download videos in 1080p. Since downloading YouTube videos violates Google's terms and conditions, Chrome extensions that purport to do this usually don't work. Easy Google Chrome YouTube Downloader Add-on (2021 Update) Add-on for Google Chrome can help the user to download videos from the Internet with one click, instead of having to access a new website or installing software. These Add-ons help to download videos from Google Chrome, being able to download videos from Facebook, Twitter, YouTube, Instagram, DailyMotion and many other sites easily.