A Safety-Oriented Platform for Web Applications
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Testing in Webkit-EFL from 0% to 99% in 6 Months
Testing in WebKit-EFL From 0% to 99% in 6 months Leandro Pereira ProFUSION Embedded Systems http://profusion.mobi February 04, 2012 WebKit WebKit I Good standards compliance I Comprised of WebCore, JavaScriptCore, one WebKit for each port WebKit I Heart of Epiphany, Chromium, Safari, Konqueror, and Eve I Comprised of WebCore, JavaScriptCore, one WebKit for each port WebKit I Heart of Epiphany, Chromium, Safari, Konqueror, and Eve I Good standards compliance , JavaScriptCore, one WebKit for each port WebKit I Heart of Epiphany, Chromium, Safari, Konqueror, and Eve I Good standards compliance I Comprised of WebCore , one WebKit for each port WebKit I Heart of Epiphany, Chromium, Safari, Konqueror, and Eve I Good standards compliance I Comprised of WebCore, JavaScriptCore WebKit I Heart of Epiphany, Chromium, Safari, Konqueror, and Eve I Good standards compliance I Comprised of WebCore, JavaScriptCore, one WebKit for each port WebKit I Heart of Epiphany, Chromium, Safari, Konqueror, and Eve I Good standards compliance I Comprised of WebCore, JavaScriptCore, one WebKit for each port, and WTF. I New feature ! new test I Over 9000 28000 tests I Some imported from other test suites (W3C, Mozilla, etc) I Some written by WebKit contributors I One of the reasons WebKit repo is so large (1.8GiB just for tests and expected results) I Most tests are port-independent I Test results are mostly port-dependent Testing in WebKit I Bug fixed ! new test I Over 9000 28000 tests I Some imported from other test suites (W3C, Mozilla, etc) I Some written by WebKit -

What Is Konqueror the Problem Solution
http://www.linuxhowtos.org/Network/fastkonqueror.pdf What is Konqueror Konqueror is the default browser/file manager for KDE. As time of this writing this is one of only 4 browsers who correctly display the acid2 test (http://www.webstandards.org/act/acid2/) correctly. The Problem One problem of this browser is the lack of an internal dns cache, that means for every http request (each image on a web page) it sends a dns query. Depending on your internet connection and speed of your dns servers, this can slow things down. Solution pdnsd pdnsd is a tiny dns proxy. pdnsd should be available on most distributions. Just install the tool via apt-get, rpm, emerge or whatever your distribution uses. configuring you can use the default example configuration and modify the cache size and dns server ip. My config reads this: global { perm_cache=2048; # cachesize in kB. cache_dir="/var/cache/pdnsd"; run_as="pdnsd"; server_ip = 127.0.0.1; status_ctl = on; paranoid=on; min_ttl=900; # store cache at least 15 minutes. max_ttl=604800; # store cache maximum one week. timeout=10; } server { label= "myisp"; ip = 192.168.0.1; # enter IP of your dns server proxy_only=on; timeout=4; uptest=if; interface=eth0; interval=600; purge_cache=off; } modify /etc/resolv domain yourdomain server 127.0.0.1 start the dns proxy /etc/init.d/pdnsd start page 1 of 2 http://www.linuxhowtos.org/Network/fastkonqueror.pdf check if the server works by pinging a server ping www.linuxhowtos.org if everything works, add the pdnsd to the started services and you are done. -

CA Network Flow Analysis Release Notes
CA Network Flow Analysis Release Notes Release 9.1.3 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the “Documentation”) is for your informational purposes only and is subject to change or withdrawal by CA at any time. This Documentation may not be copied, transferred, reproduced, disclosed, modified or duplicated, in whole or in part, without the prior written consent of CA. This Documentation is confidential and proprietary information of CA and may not be disclosed by you or used for any purpose other than as may be permitted in (i) a separate agreement between you and CA governing your use of the CA software to which the Documentation relates; or (ii) a separate confidentiality agreement between you and CA. Notwithstanding the foregoing, if you are a licensed user of the software product(s) addressed in the Documentation, you may print or otherwise make available a reasonable number of copies of the Documentation for internal use by you and your employees in connection with that software, provided that all CA copyright notices and legends are affixed to each reproduced copy. The right to print or otherwise make available copies of the Documentation is limited to the period during which the applicable license for such software remains in full force and effect. Should the license terminate for any reason, it is your responsibility to certify in writing to CA that all copies and partial copies of the Documentation have been returned to CA or destroyed. TO THE EXTENT PERMITTED BY APPLICABLE LAW, CA PROVIDES THIS DOCUMENTATION “AS IS” WITHOUT WARRANTY OF ANY KIND, INCLUDING WITHOUT LIMITATION, ANY IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, OR NONINFRINGEMENT. -

Copyrighted Material
05_096970 ch01.qxp 4/20/07 11:27 PM Page 3 1 Introducing Cascading Style Sheets Cascading style sheets is a language intended to simplify website design and development. Put simply, CSS handles the look and feel of a web page. With CSS, you can control the color of text, the style of fonts, the spacing between paragraphs, how columns are sized and laid out, what back- ground images or colors are used, as well as a variety of other visual effects. CSS was created in language that is easy to learn and understand, but it provides powerful control over the presentation of a document. Most commonly, CSS is combined with the markup languages HTML or XHTML. These markup languages contain the actual text you see in a web page — the hyperlinks, paragraphs, headings, lists, and tables — and are the glue of a web docu- ment. They contain the web page’s data, as well as the CSS document that contains information about what the web page should look like, and JavaScript, which is another language that pro- vides dynamic and interactive functionality. HTML and XHTML are very similar languages. In fact, for the majority of documents today, they are pretty much identical, although XHTML has some strict requirements about the type of syntax used. I discuss the differences between these two languages in detail in Chapter 2, and I also pro- vide a few simple examples of what each language looks like and how CSS comes together with the language to create a web page. In this chapter, however, I discuss the following: ❑ The W3C, an organization that plans and makes recommendations for how the web should functionCOPYRIGHTED and evolve MATERIAL ❑ How Internet documents work, where they come from, and how the browser displays them ❑ An abridged history of the Internet ❑ Why CSS was a desperately needed solution ❑ The advantages of using CSS 05_096970 ch01.qxp 4/20/07 11:27 PM Page 4 Part I: The Basics The next section takes a look at the independent organization that makes recommendations about how CSS, as well as a variety of other web-specific languages, should be used and implemented. -

Security Analysis of Firefox Webextensions
6.857: Computer and Network Security Due: May 16, 2018 Security Analysis of Firefox WebExtensions Srilaya Bhavaraju, Tara Smith, Benny Zhang srilayab, tsmith12, felicity Abstract With the deprecation of Legacy addons, Mozilla recently introduced the WebExtensions API for the development of Firefox browser extensions. WebExtensions was designed for cross-browser compatibility and in response to several issues in the legacy addon model. We performed a security analysis of the new WebExtensions model. The goal of this paper is to analyze how well WebExtensions responds to threats in the previous legacy model as well as identify any potential vulnerabilities in the new model. 1 Introduction Firefox release 57, otherwise known as Firefox Quantum, brings a large overhaul to the open-source web browser. Major changes with this release include the deprecation of its initial XUL/XPCOM/XBL extensions API to shift to its own WebExtensions API. This WebExtensions API is currently in use by both Google Chrome and Opera, but Firefox distinguishes itself with further restrictions and additional functionalities. Mozilla’s goals with the new extension API is to support cross-browser extension development, as well as offer greater security than the XPCOM API. Our goal in this paper is to analyze how well the WebExtensions model responds to the vulnerabilities present in legacy addons and discuss any potential vulnerabilities in the new model. We present the old security model of Firefox extensions and examine the new model by looking at the structure, permissions model, and extension review process. We then identify various threats and attacks that may occur or have occurred before moving onto recommendations. -

Inlined Information Flow Monitoring for Javascript
Inlined Information Flow Monitoring for JavaScript Andrey Chudnov David A. Naumann Stevens Institute of Technology Stevens Institute of Technology Hoboken, NJ 07030 USA Hoboken, NJ 07030 USA [email protected] [email protected] ABSTRACT JS engines are highly engineered for performance, which has Extant security mechanisms for web apps, notably the\same- led some researchers to argue for inlined monitoring for IFC. origin policy", are not sufficient to achieve confidentiality The main contribution of this paper is an inlined IFC mon- and integrity goals for the many apps that manipulate sen- itor that enforces non-interference for apps written in JS. sitive information. The trend in web apps is \mashups" We present the main design decisions and rationale, together which integrate JavaScript code from multiple providers in with technical highlights and a survey of state of the art al- ways that can undercut existing security mechanisms. Re- ternatives. The tool is evaluated using synthetic case studies searchers are exploring dynamic information flow controls and performance benchmarks. (IFC) for JavaScript, but there are many challenges to achiev- ing strong IFC without excessive performance cost or im- On IFC. Browsers and other platforms currently provide practical browser modifications. This paper presents an in- isolation mechanisms and access controls. Pure isolation lined IFC monitor for ECMAScript 5 with web support, goes against integration of app code from multiple providers. using the no-sensitive-upgrade (NSU) technique, together Access controls can be more nuanced, but it is well-known with experimental evaluation using synthetic mashups and that access control policies are safety properties whereas IF performance benchmarks. -
Dashboard Comparing To: Site
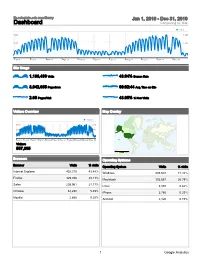
lib.colostate.edu non-library Jan 1, 2010 - Dec 31, 2010 Dashboard Comparing to: Site Visits 7,000 7,000 3,500 3,500 0 0 Jan 4 Feb 6 Mar 11 Apr 13 May 16 Jun 18 Jul 21 Aug 23 Sep 25 Oct 28 Nov 30 Site Usage 1,133,439 Visits 43.94% Bounce Rate 3,042,655 Pageviews 00:02:44 Avg. Time on Site 2.68 Pages/Visit 43.05% % New Visits Visitors Overview Map Overlay Visitors 5,000 5,000 2,500 2,500 0 0 Jan 4 Feb 6 Mar 11 Apr 13 May 16 Jun 18 Jul 21 Aug 23 Sep 25 Oct 28 Nov 30 Visitors 507,395 Visits 1 1,041,862 Browsers Operating Systems Browser Visits % visits Operating System Visits % visits Internet Explorer 492,315 43.44% Windows 808,603 71.34% Firefox 329,946 29.11% Macintosh 303,667 26.79% Safari 239,961 21.17% Linux 9,330 0.82% Chrome 62,280 5.49% iPhone 3,780 0.33% Mozilla 2,866 0.25% Android 2,120 0.19% 1 Google Analytics Screen Resolutions All Traffic Sources Screen Resolution Visits % visits Source/Medium Visits % visits 1280x800 484,793 42.77% (direct) / (none) 472,874 41.72% 1024x768 130,790 11.54% google / organic 230,016 20.29% 1280x1024 118,462 10.45% colostate.edu / referral 195,328 17.23% 1440x900 100,667 8.88% search.colostate.edu / referral 32,475 2.87% 1366x768 63,310 5.59% bing / organic 17,244 1.52% Keywords Top Content Keyword Visits % visits Page Pageviews % visits csu library 45,783 17.07% / 1,089,490 35.81% colorado state university library 15,477 5.77% /databases/ 246,518 8.10% csu libraries 6,841 2.55% /databases/path-to-existing- 192,972 6.34% colostate library 4,943 1.84% /404.html?page=/databases/pat 88,922 2.92% lib.colostate.edu -
Designing a Browser to Benefit from Multi-Core Silicon
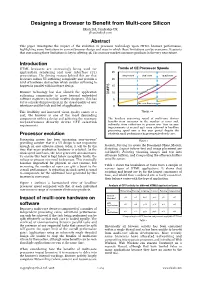
Designing a Browser to Benefit from Multi-core Silicon Ekioh Ltd, Cambridge UK. [email protected] Abstract This paper investigates the impact of the evolution in processor technology upon HTML browser performance, highlighting some limitations in current browser design and ways in which these limitations can be overcome. It asserts that overcoming these limitations is key to offering 4K UIs on mass-market consumer products in the very near future. Introduction HTML browsers are increasingly being used for Trends of CE Processor Speeds application rendering and user interface (UI) 25 presentation. The driving reasons behind this are that single core dual core quad core browsers reduce UI authoring complexity and provide a 20 level of hardware abstraction which enables authoring to happen in parallel with hardware design. 15 Browser technology has also allowed the application 10 authoring community to grow beyond embedded DMIPS Headline Performance software engineers to include creative designers. This has 5 led to a marked improvement in the visual quality of user Per core Performance interfaces and the look and feel of applications. 0 This flexibility and increased visual quality comes at a Time → cost; the browser is one of the most demanding components within a device and achieving the necessary The headline processing speed of multi-core devices responsiveness directly drives CPU selection benefits from increases in the number of cores and, requirements. indirectly, from reductions in process size. Year on year improvements of around 30% were achieved in headline processing speed over a five year period despite the Processor evolution relatively small performance improvements of each core. -

On the Disparity of Display Security in Mobile and Traditional Web Browsers
On the Disparity of Display Security in Mobile and Traditional Web Browsers Chaitrali Amrutkar, Kapil Singh, Arunabh Verma and Patrick Traynor Converging Infrastructure Security (CISEC) Laboratory Georgia Institute of Technology Abstract elements. The difficulty in efficiently accessing large pages Mobile web browsers now provide nearly equivalent fea- on mobile devices makes an adversary capable of abusing tures when compared to their desktop counterparts. How- the rendering of display elements particularly acute from a ever, smaller screen size and optimized features for con- security perspective. strained hardware make the web experience on mobile In this paper, we characterize a number of differences in browsers significantly different. In this paper, we present the ways mobile and desktop browsers render webpages that the first comprehensive study of the display-related security potentially allow an adversary to deceive mobile users into issues in mobile browsers. We identify two new classes of performing unwanted and potentially dangerous operations. display-related security problems in mobile browsers and de- Specifically, we examine the handling of user interaction vise a range of real world attacks against them. Addition- with overlapped display elements, the ability of malicious ally, we identify an existing security policy for display on cross-origin elements to affect the placement of honest el- desktop browsers that is inappropriate on mobile browsers. ements and the ability of malicious cross-origin elements Our analysis is comprised of eight mobile and five desktop to alter the navigation of honest parent and descendant el- browsers. We compare security policies for display in the ements. We then perform the same tests against a number candidate browsers to infer that desktop browsers are signif- of desktop browsers and find that the majority of desktop icantly more compliant with the policies as compared to mo- browsers are not vulnerable to the same rendering issues. -

Move Your Ie Favorites to Firefox Bookmarks
MOVE YOUR IE FAVORITES TO FIREFOX BOOKMARKS If you are moving to Linux from Windows, you will likely want to keep at least some of your Internet Explorer (IE) "Favorites." Here is how to move them to "Bookmarks" for the Firefox and Konqueror browsers on your Linux PC. (If you have been using Firefox under Windows, see this article instead.) Export Your IE Favorites To start, you will need to export the favorites as an HTML file. 1. From the IE File menu, select Import/Export. (If you are using IE 7 and you don't see the menu bar, just tap the <Alt>key once to make it appear.) 2. When the Import Export Wizard launches, click Next. 3. Select Export Favorites and click Next. 4. Select the folder you wish to export and click Next. 5. Choose to export to a file. (Use the default "bookmark.htm" and save it in My Documents.) 6. Click Next. 7. Click Finish to close the wizard. 8. Copy the file to a CD or other media that you can open on your Linux system. Import Your Bookmarks Next, you import the bookmarks into Firefox or Konqueror using the file bookmark.htm file. Firefox 1. In Firefox, select the Bookmarks menu, then Organize Bookmarks. 2. In the Bookmarks Manager select File, Import. 3. Choose From File, then click Next. 4. Select the file from the CD or other location where you put it, and click Open to complete the import. Konqueror 1. In Konqueror, select the Bookmarks menu, then Edit Bookmarks. 2. -

Giant List of Web Browsers
Giant List of Web Browsers The majority of the world uses a default or big tech browsers but there are many alternatives out there which may be a better choice. Take a look through our list & see if there is something you like the look of. All links open in new windows. Caveat emptor old friend & happy surfing. 1. 32bit https://www.electrasoft.com/32bw.htm 2. 360 Security https://browser.360.cn/se/en.html 3. Avant http://www.avantbrowser.com 4. Avast/SafeZone https://www.avast.com/en-us/secure-browser 5. Basilisk https://www.basilisk-browser.org 6. Bento https://bentobrowser.com 7. Bitty http://www.bitty.com 8. Blisk https://blisk.io 9. Brave https://brave.com 10. BriskBard https://www.briskbard.com 11. Chrome https://www.google.com/chrome 12. Chromium https://www.chromium.org/Home 13. Citrio http://citrio.com 14. Cliqz https://cliqz.com 15. C?c C?c https://coccoc.com 16. Comodo IceDragon https://www.comodo.com/home/browsers-toolbars/icedragon-browser.php 17. Comodo Dragon https://www.comodo.com/home/browsers-toolbars/browser.php 18. Coowon http://coowon.com 19. Crusta https://sourceforge.net/projects/crustabrowser 20. Dillo https://www.dillo.org 21. Dolphin http://dolphin.com 22. Dooble https://textbrowser.github.io/dooble 23. Edge https://www.microsoft.com/en-us/windows/microsoft-edge 24. ELinks http://elinks.or.cz 25. Epic https://www.epicbrowser.com 26. Epiphany https://projects-old.gnome.org/epiphany 27. Falkon https://www.falkon.org 28. Firefox https://www.mozilla.org/en-US/firefox/new 29. -

Web Browsers
WEB BROWSERS Page 1 INTRODUCTION • A Web browser acts as an interface between the user and Web server • Software application that resides on a computer and is used to locate and display Web pages. • Web user access information from web servers, through a client program called browser. • A web browser is a software application for retrieving, presenting, and traversing information resources on the World Wide Web Page 2 FEATURES • All major web browsers allow the user to open multiple information resources at the same time, either in different browser windows or in different tabs of the same window • A refresh and stop buttons for refreshing and stopping the loading of current documents • Home button that gets you to your home page • Major browsers also include pop-up blockers to prevent unwanted windows from "popping up" without the user's consent Page 3 COMPONENTS OF WEB BROWSER 1. User Interface • this includes the address bar, back/forward button , bookmarking menu etc 1. Rendering Engine • Rendering, that is display of the requested contents on the browser screen. • By default the rendering engine can display HTML and XML documents and images Page 4 HISTROY • The history of the Web browser dates back in to the late 1980s, when a variety of technologies laid the foundation for the first Web browser, WorldWideWeb, by Tim Berners-Lee in 1991. • Microsoft responded with its browser Internet Explorer in 1995 initiating the industry's first browser war • Opera first appeared in 1996; although it have only 2% browser usage share as of April 2010, it has a substantial share of the fast-growing mobile phone Web browser market, being preinstalled on over 40 million phones.