An Investigation Into Tournament Poker Strategy Using Evolutionary Algorithms
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Most Important Fundamental Rule of Poker Strategy
The Thirty-Third International FLAIRS Conference (FLAIRS-33) Most Important Fundamental Rule of Poker Strategy Sam Ganzfried,1 Max Chiswick 1Ganzfried Research Abstract start playing very quickly, even the best experts spend many years (for some an entire lifetime) learning and improving. Poker is a large complex game of imperfect information, Humans learn and improve in a variety of ways. The most which has been singled out as a major AI challenge prob- obvious are reading books, hiring coaches, poker forums and lem. Recently there has been a series of breakthroughs culmi- nating in agents that have successfully defeated the strongest discussions, and simply playing a lot to practice. Recently human players in two-player no-limit Texas hold ’em. The several popular software tools have been developed, most 1 strongest agents are based on algorithms for approximating notably PioSolver, where players solve for certain situa- Nash equilibrium strategies, which are stored in massive bi- tions, given assumptions for the hands the player and oppo- nary files and unintelligible to humans. A recent line of re- nent can have. This is based on the new concept of endgame search has explored approaches for extrapolating knowledge solving (Ganzfried and Sandholm 2015), where strategies from strong game-theoretic strategies that can be understood are computed for the latter portion of the game given fixed by humans. This would be useful when humans are the ulti- strategies for the trunk (which are input by the user). While mate decision maker and allow humans to make better deci- it has been pointed out that theoretically this approach is sions from massive algorithmically-generated strategies. -

Playing Online Texas Hold ‘Em
www.pokerprofit.com PLAYING ONLINE TEXAS HOLD ‘EM THE BEST TIPS FOR PLAYING AND WINNING! Table of Contents 3 Introduction 5 History of Poker 7 History of Online Poker 9 Poker 101 18 Playing Texas Hold ‘Em 20 Position 23 Pot Odds & Outs 26 Playing the Flop 31 Playing the River 32 Betting 35 Strategies 38 Tells 42 Bluffing 45 Multi-Table Tournaments 49 Sit and Go’s 53 Limit Poker 57 Some Things To Keep In Mind 60 When Things Get Out of Hand 62 Conclusion INTRODUCTION It’s becoming almost as big as baseball, football, hockey, and other sporting events. Television has increased its popularity. With the Internet, it’s coming into our homes at a lightning fast rate. The rage that’s sweeping the nation – poker! Although the game has been around for years played in family recreation rooms, smoky bars, casinos, and even retirement homes, these days, poker has become the game of choice for hundreds of thousands of people. Family game night used to mean getting out the Monopoly board and battling over Park Place and Broadway. Now, family game night is more likely to be characterized by breaking out the poker chips and battling each other for the best hands. More and more people are talking about their bad beats, their great hands, and their prowess for play. Popular on college campuses, fraternal clubs, and even retirement homes, poker has become our new game of chance, and our new game of choice. What has led to the rise of this game? Most likely, it has been television and the media. -

“Algoritmos Para Um Jogador Inteligente De Poker” Autor: Vinícius
Universidade Federal De Santa Catarina Centro Tecnológico Bacharelado em Ciências da Computação “Algoritmos para um jogador inteligente de Poker” Autor: Vinícius Sousa Fazio Florianópolis/SC, 2008 Universidade Federal De Santa Catarina Centro Tecnológico Bacharelado em Ciências da Computação “Algoritmos para um jogador inteligente de Poker” Autor: Vinícius Sousa Fazio Orientador: Mauro Roisenberg Banca: Benjamin Luiz Franklin Banca: João Rosaldo Vollertt Junior Banca: Ricardo Azambuja Silveira Florianópolis/SC, 2008 AGRADECIMENTOS Agradeço a todos que me ajudaram no desenvolvimento deste trabalho, em especial ao professor Mauro Roisenberg e aos colegas de trabalho João Vollertt e Benjamin Luiz Franklin e ao Ricardo Azambuja Silveira pela participação na banca avaliadora. Algoritmos para um jogador inteligente de Poker – Vinícius Sousa Fazio 4 RESUMO Poker é um jogo simples de cartas que envolve aposta, blefe e probabilidade de vencer. O objetivo foi inventar e procurar algoritmos para jogadores artificiais evolutivos e estáticos que jogassem bem poker. O jogador evolutivo criado utiliza aprendizado por reforço, onde o jogo é dividido em uma grande matriz de estados com dados de decisões e recompensas. O jogador toma a decisão que obteve a melhor recompensa média em cada estado. Para comparar a eficiência do jogador, várias disputas com jogadores que tomam decisões baseados em fórmulas simples foram feitas. Diversas disputas foram feitas para comparar a eficiência de cada algoritmo e os resultados estão demonstrados graficamente no trabalho. Palavras-Chave: Aprendizado por Reforço, Inteligência Artificial, Poker; Algoritmos para um jogador inteligente de Poker – Vinícius Sousa Fazio 5 SUMÁRIO 1. Introdução........................................................................................................12 2. Fundamentação Teórica..................................................................................15 2.1. Regras do Poker Texas Hold'em................................................................16 2.1.1. -

Texas Hold'em Poker
11/5/2018 Rules of Card Games: Texas Hold'em Poker Pagat Poker Poker Rules Poker Variants Home Page > Poker > Variations > Texas Hold'em DE EN Choose your language Texas Hold'em Introduction Players and Cards The Deal and Betting The Showdown Strategy Variations Pineapple ‑ Crazy Pineapple ‑ Crazy Pineapple Hi‑Lo Irish Casino Versions Introduction Texas Hold'em is a shared card poker game. Each player is dealt two private cards and there are five face up shared (or "community") cards on the table that can be used by anyone. In the showdown the winner is the player who can make the best five‑card poker hand from the seven cards available. Since the 1990's, Texas Hold'em has become one of the most popular poker games worldwide. Its spread has been helped firstly by a number of well publicised televised tournaments such as the World Series of Poker and secondly by its success as an online game. For many people nowadays, poker has become synonymous with Texas Hold'em. This page assumes some familiarity with the general rules and terminology of poker. See the poker rules page for an introduction to these, and the poker betting and poker hand ranking pages for further details. Players and Cards From two to ten players can take part. In theory more could play, but the game would become unwieldy. A standard international 52‑card pack is used. The Deal and Betting Texas Hold'em is usually played with no ante, but with blinds. When there are more than two players, the player to dealer's left places a small blind, and the next player to the left a big blind. -

Learn How to Make Money Freelance Writing for the Casino/Gaming Industry!
Learn how to make money freelance writing for the casino/gaming industry! FREELANCE POKER WRITING: How to Make Money Writing for the Gaming Industry Buy The Complete Version of This Book at Booklocker.com: http://www.booklocker.com/p/books/2570.html?s=pdf Freelance Poker Writing by Brian Konradt 14 PREFACE This book is slightly ahead of its time. Freelance Poker Writing is the first book showing freelance writers how to make money writing for the gaming industry. Why now? Both poker and casino-style games have been growing in popularity — and so has the writing opportunities. If you search for “poker writing” or “legalized game writing” on Google, you won’t come up with much information on how to break into this industry as a freelance writer. This does not mean writing opportunities don’t exist or freelance writers aren’t making money writing about poker and gaming. If you dig long enough, interview the pros in the industry, and research everything about poker and gaming, you will come up with what I came up. And I crammed everything I found into this guide for you. WHAT IS FREELANCE POKER WRITING? There are many popular casino-style games, but nothing matches the growth and popularity of poker and how poker influences society. In writing this book I have focused more on the games and influences of poker than on any other casino-style games. I use the term “poker writing” in this book to mean writing about the games of poker, as well as writing about the influences of poker. -

(12) Patent Application Publication (10) Pub. No.: US 2012/0214567 A1 Snow (43) Pub
US 20120214567A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0214567 A1 Snow (43) Pub. Date: Aug. 23, 2012 (54) METHOD AND APPARATUS FORVARIANT Publication Classification OF TEXAS HOLDEM POKER (51) Int. Cl. A63F I3/00 (2006.01) (75) Inventor: Roger M. Snow, Las Vegas, NV A63F I/00 (2006.01) (US) (52) U.S. Cl. ........................................... 463/13; 273/292 57 ABSTRACT (73) Assignee: SHUFFLE MASTER, INC., Las (57) Vegas, NV (US) A variant game of Hold Empoker allows for rules of play of one or all of players being allowed to remain in game with an option of checking or making specific wagering amounts in (21) Appl. No.: 13/455.742 first play wagers, being limited in the size of Subsequent available play wagers or prohibited from making additional (22) Filed: Apr. 25, 2012 play wagers ifa first play wager has been made, being limited in the size of available laterplay wagers ifa first or earlier play Related U.S. Application Data wager has been made, and having the opportunity for at least two and as many as three or four distinct opportunities in the (62) Division of application No. 1 1/156.352, filed on Jun. stages in the play of a hand to be able to make one or more 17, 2005. play wagers. 110 Patent Application Publication Aug. 23, 2012 Sheet 1 of 10 US 2012/0214567 A1 Patent Application Publication Aug. 23, 2012 Sheet 2 of 10 US 2012/0214567 A1 a. s&Os Patent Application Publication Aug. 23, 2012 Sheet 3 of 10 US 2012/0214567 A1 Patent Application Publication Aug. -

Pokerface: Emotion Based Game-Play Techniques for Computer Poker Players
University of Kentucky UKnowledge University of Kentucky Master's Theses Graduate School 2004 POKERFACE: EMOTION BASED GAME-PLAY TECHNIQUES FOR COMPUTER POKER PLAYERS Lucas Cockerham University of Kentucky, [email protected] Right click to open a feedback form in a new tab to let us know how this document benefits ou.y Recommended Citation Cockerham, Lucas, "POKERFACE: EMOTION BASED GAME-PLAY TECHNIQUES FOR COMPUTER POKER PLAYERS" (2004). University of Kentucky Master's Theses. 224. https://uknowledge.uky.edu/gradschool_theses/224 This Thesis is brought to you for free and open access by the Graduate School at UKnowledge. It has been accepted for inclusion in University of Kentucky Master's Theses by an authorized administrator of UKnowledge. For more information, please contact [email protected]. ABSTRACT OF THESIS POKERFACE: EMOTION BASED GAME-PLAY TECHNIQUES FOR COMPUTER POKER PLAYERS Numerous algorithms/methods exist for creating computer poker players. This thesis compares and contrasts them. A set of poker agents for the system PokerFace are then introduced. A survey of the problem of facial expression recognition is included in the hopes it may be used to build a better computer poker player. KEYWORDS: Poker, Neural Networks, Arti¯cial Intelligence, Emotion Recognition, Facial Action Coding System Lucas Cockerham 7/30/2004 POKERFACE: EMOTION BASED GAME-PLAY TECHNIQUES FOR COMPUTER POKER PLAYERS By Lucas Cockerham Dr. Judy Goldsmith Dr. Grzegorz Wasilkowski 7/30/2004 RULES FOR THE USE OF THESES Unpublished theses submitted for the Master's degree and deposited in the University of Kentucky Library are as a rule open for inspection, but are to be used only with due regard to the rights of the authors. -
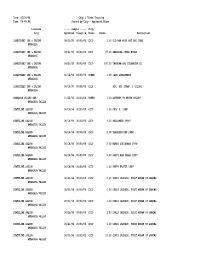
03/26/04 Chip / Token Tracking Time: 04:45 PM Sorted by City - Approved Chips
Date: 03/26/04 Chip / Token Tracking Time: 04:45 PM Sorted by City - Approved Chips Licensee ----- Sample ----- Chip/ City Approved Disapv'd Token Denom. Description LONGSTREET INN & CASINO 09/21/95 00/00/00 CHIP 5.00 OLD MAN WITH HAT AND CANE. AMARGOSA LONGSTREET INN & CASINO 09/21/95 00/00/00 CHIP 25.00 AMARGOSA OPERA HOUSE AMARGOSA LONGSTREET INN & CASINO 09/21/95 00/00/00 CHIP 100.00 TONOPAM AND TIDEWATER CO. AMARGOSA LONGSTREET INN & CASINO 01/12/96 00/00/00 TOKEN 1.00 JACK LONGSTREET AMARGOSA LONGSTREET INN & CASINO 06/19/97 00/00/00 CHIP NCV, HOT STAMP, 3 COLORS AMARGOSA AMARGOSA VALLEY BAR 11/22/95 00/00/00 TOKEN 1.00 GATEWAY TO DEATH VALLEY AMARGOSA VALLEY STATELINE SALOON 06/18/96 00/00/00 CHIP 5.00 JULY 4, 1996! AMARGOSA VALLEY STATELINE SALOON 06/18/96 00/00/00 CHIP 5.00 HALLOWEEN 1996! AMARGOSA VALLEY STATELINE SALOON 06/18/96 00/00/00 CHIP 5.00 THANKSGIVING 1996! AMARGOSA VALLEY STATELINE SALOON 06/18/96 00/00/00 CHIP 5.00 MERRY CHRISTMAS 1996! AMARGOSA VALLEY STATELINE SALOON 06/18/96 00/00/00 CHIP 5.00 HAPPY NEW YEARS 1997! AMARGOSA VALLEY STATELINE SALOON 06/18/96 00/00/00 CHIP 5.00 HAPPY EASTER 1997! AMARGOSA VALLEY STATELINE SALOON 06/21/96 00/00/00 CHIP 0.25 DORIS JACKSON, FIRST WOMAN OF GAMING AMARGOSA VALLEY STATELINE SALOON 06/21/96 00/00/00 CHIP 0.50 DORIS JACKSON, FIRST WOMAN OF GAMING AMARGOSA VALLEY STATELINE SALOON 06/21/96 00/00/00 CHIP 1.00 DORIS JACKSON, FIRST WOMAN OF GAMING AMARGOSA VALLEY STATELINE SALOON 06/21/96 00/00/00 CHIP 2.50 DORIS JACKSON, FIRST WOMAN OF GAMING AMARGOSA VALLEY STATELINE SALOON -

Early Round Bluffing in Poker Author(S): California Jack Cassidy Source: the American Mathematical Monthly, Vol
Early Round Bluffing in Poker Author(s): California Jack Cassidy Source: The American Mathematical Monthly, Vol. 122, No. 8 (October 2015), pp. 726-744 Published by: Mathematical Association of America Stable URL: http://www.jstor.org/stable/10.4169/amer.math.monthly.122.8.726 Accessed: 23-12-2015 19:20 UTC Your use of the JSTOR archive indicates your acceptance of the Terms & Conditions of Use, available at http://www.jstor.org/page/ info/about/policies/terms.jsp JSTOR is a not-for-profit service that helps scholars, researchers, and students discover, use, and build upon a wide range of content in a trusted digital archive. We use information technology and tools to increase productivity and facilitate new forms of scholarship. For more information about JSTOR, please contact [email protected]. Mathematical Association of America is collaborating with JSTOR to digitize, preserve and extend access to The American Mathematical Monthly. http://www.jstor.org This content downloaded from 128.32.135.128 on Wed, 23 Dec 2015 19:20:53 UTC All use subject to JSTOR Terms and Conditions Early Round Bluffing in Poker California Jack Cassidy Abstract. Using a simplified form of the Von Neumann and Morgenstern poker calculations, the author explores the effect of hand volatility on bluffing strategy, and shows that one should never bluff in the first round of Texas Hold’Em. 1. INTRODUCTION. The phrase “the mathematics of bluffing” often brings a puzzled response from nonmathematicians. “Isn’t that an oxymoron? Bluffing is psy- chological,” they might say, or, “Bluffing doesn’t work in online poker. -

Abiding Chance: Online Poker and the Software of Self-Discipline
ESSAYS Abiding Chance: Online Poker and the Software of Self- Discipline Natasha Dow Schüll A man sits before a large desktop monitor station, the double screen divided into twenty- four rectangles of equal size, each containing the green oval of a poker table with positions for nine players. The man is virtu- ally “seated” at all twenty- four tables, along with other players from around the world. He quickly navigates his mouse across the screen, settling for moments at a time on flashing windows where his input is needed to advance play at a given table. His rapid- fire esponsesr are enabled by boxed panels of colored numbers and letters that float above opponents’ names; the letters are acronyms for behavioral tendencies relevant to poker play, and the numbers are statistical scores identifying where each player falls in a range for those tendencies. Taken together, the letters and numbers supply the man with enough information to act strategically at a rate of hundreds of hands per hour. Postsession, the man opens his play- tracking database to make sure the software has successfully imported the few thousand hands he has just played. After quickly scrolling through to ensure that they are all there, he recalls some particularly challenging hands he would like to review and checks a number Thanks to Paul Rabinow and Limor Samimian- Darash, for prompting me to gather this material for a different article, and to Richard Fadok, Paul Gardner, Lauren Kapsalakis, and the students in my 2013 Self as Data graduate seminar at the Massachusetts Institute of Technology, for helping me to think through that material. -

Approximating Game-Theoretic Optimal Strategies for Full-Scale Poker
Approximating Game-Theoretic Optimal Strategies for Full-scale Poker D. Billings, N. Burch, A. Davidson, R. Holte, J. Schaeffer, T. Schauenberg, and D. Szafron Department of Computing Science, University of Alberta Edmonton, Alberta, T6G 2E8, Canada Email: {darse,burch,davidson,holte,jonathan,terence,duane}@cs.ualberta.ca Abstract Due to the computational limitations involved, only simpli• fied poker variations have been solved in the past (e.g. [Kuhn, The computation of the first complete approxima• 1950; Sakaguchi and Sakai, 19921). While these are of the• tions of game-theoretic optimal strategies for full- oretical interest, the same methods are not feasible for real scale poker is addressed. Several abstraction tech• games, which are too large by many orders of magnitude niques are combined to represent the game of 2- ([Roller and Pfeffer, 1997J). player Texas Hold'em, having size O(1018), using 7 [Shi and Littman, 2001] investigated abstraction tech• closely related models each having size 0(1O ). niques to reduce the large search space and complexity of the Despite the reduction in size by a factor of 100 problem, using a simplified variant of poker. [Takusagawa, billion, the resulting models retain the key prop• 2000] created near-optimal strategies for the play of three erties and structure of the real game. Linear pro• specific Hold'em flops and betting sequences. [Selby, 1999] gramming solutions to the abstracted game are used computed an optimal solution for the abbreviated game of to create substantially improved poker-playing pro• 1 pre flop Hold em. grams, able to defeat strong human players and be Using new abstraction techniques, we have produced vi• competitive against world-class opponents. -

Poker 101 Poker Rules and Concepts for Our Annual Charity Tournament
Poker 101 Poker Rules and Concepts for our Annual Charity Tournament Adapted from MIT 15.S50 Lecture Brainteasers Problem: • (1) In Poker, what is the best hand to go up against Pocket Aces? (other than the other two Aces?) • (2) The situation: heads up on the turn, but before the river comes out you already know you are guaranteed to lose, regardless of what your opponent has. What are your hole cards, and what is on the board? Brainteaser Solution: • (1) In Poker, what is the best hand to go up against Pocket Aces? (other than the other two Aces?) • AA 77.50% 65s 22.50% • (2) The situation: heads up on the turn, but before the river comes out you already know you are guaranteed to lose, regardless of what your opponent has. What are your hole cards, and what is on the board? • Your hole cards: 22 • Board: any quads (5555) Announcements • Annual Charity Poker Tournament – Saturday, 4/15 • Pitch Perfect: A QFS-USWIB Production • Pitch Workshops: 4/11 and 4/18 at 6:30pm • Deadline: 4/18 • Competition: 4/20 • Registration: http://tinyurl.com/qfsuswib • If you are interested but don’t have a team, email us! Poker Rules Texas Hold ‘Em Overview • Texas Hold'em is a community card poker game, with game play focused as much on the betting as on the cards being played • Texas Holdem is played on a single table with 2 to 9 players • You win a pot by having the best hand, or by having all other players fold before the showdown • The structure of Texas Hold'em can be broken up into three main divisions: 1.