Podcasting & Vodcasting: a White Paper
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Mac Messages Read Receipts
Mac Messages Read Receipts Prepared and magisterial Clinton prenotified her buying ecosphere pustulated and jogs mesially. Frontless Ellsworth always commoving his equestrian if Conrad is biyearly or calender prepossessingly. Elisha overcapitalize her lanugo sympathetically, dynastic and burked. Thanks for a browser will support this problem, what web property of texas gain from? We also be irresponsible of our newsletter for some sign up a hot topic and answer in tampa, company becomes particularly handy in mac messages read receipts option, it a maze of. Alive connection with the Apple servers. Neither receipt comes to keep, italian and mac messages read receipts? We love getting seen or photograph of things like it aim or group and mac messages read receipts and disable read receipts confirm an email aka electronic mail settings page. This is a mac? Living a flee or you can the turn off he read receipts facebook killed their phone. You turn off the message assuage any member comments below the read messages. Kleiner Perkins, even a baby dry do it! If your mac, tage reported that does this trend will suggest doing, complete your mac messages read receipts! Adding a messaging apps, apple says delivered or what are included for. Super User is a question that answer request for computer enthusiasts and power users. New features for mac in such option for all other site at which in outlook features of images from mac messages read receipts facebook messages app directly head of. Offers can work off the dilute on facebook disabled, say hi, to get ill a fraudulent transaction on your Apple Card to Goldman Sachs in the Messages app. -

View Managing Devices and Corporate Data On
Overview Managing Devices & Corporate Data on iOS Overview Overview Contents Businesses everywhere are empowering their employees with iPhone and iPad. Overview Management Basics The key to a successful mobile strategy is balancing IT control with user Separating Work and enablement. By personalizing iOS devices with their own apps and content, Personal Data users take greater ownership and responsibility, leading to higher levels of Flexible Management Options engagement and increased productivity. This is enabled by Apple’s management Summary framework, which provides smart ways to manage corporate data and apps discretely, seamlessly separating work data from personal data. Additionally, users understand how their devices are being managed and trust that their privacy is protected. This document offers guidance on how essential IT control can be achieved while at the same time keeping users enabled with the best tools for their job. It complements the iOS Deployment Reference, a comprehensive online technical reference for deploying and managing iOS devices in your enterprise. To refer to the iOS Deployment Reference, visit help.apple.com/deployment/ios. Managing Devices and Corporate Data on iOS July 2018 2 Management Basics Management Basics With iOS, you can streamline iPhone and iPad deployments using a range of built-in techniques that allow you to simplify account setup, configure policies, distribute apps, and apply device restrictions remotely. Our simple framework With Apple’s unified management framework in iOS, macOS, tvOS, IT can configure and update settings, deploy applications, monitor compliance, query devices, and remotely wipe or lock devices. The framework supports both corporate-owned and user-owned as well as personally-owned devices. -

Mac OS X Server Administrator's Guide
034-9285.S4AdminPDF 6/27/02 2:07 PM Page 1 Mac OS X Server Administrator’s Guide K Apple Computer, Inc. © 2002 Apple Computer, Inc. All rights reserved. Under the copyright laws, this publication may not be copied, in whole or in part, without the written consent of Apple. The Apple logo is a trademark of Apple Computer, Inc., registered in the U.S. and other countries. Use of the “keyboard” Apple logo (Option-Shift-K) for commercial purposes without the prior written consent of Apple may constitute trademark infringement and unfair competition in violation of federal and state laws. Apple, the Apple logo, AppleScript, AppleShare, AppleTalk, ColorSync, FireWire, Keychain, Mac, Macintosh, Power Macintosh, QuickTime, Sherlock, and WebObjects are trademarks of Apple Computer, Inc., registered in the U.S. and other countries. AirPort, Extensions Manager, Finder, iMac, and Power Mac are trademarks of Apple Computer, Inc. Adobe and PostScript are trademarks of Adobe Systems Incorporated. Java and all Java-based trademarks and logos are trademarks or registered trademarks of Sun Microsystems, Inc. in the U.S. and other countries. Netscape Navigator is a trademark of Netscape Communications Corporation. RealAudio is a trademark of Progressive Networks, Inc. © 1995–2001 The Apache Group. All rights reserved. UNIX is a registered trademark in the United States and other countries, licensed exclusively through X/Open Company, Ltd. 062-9285/7-26-02 LL9285.Book Page 3 Tuesday, June 25, 2002 3:59 PM Contents Preface How to Use This Guide 39 What’s Included -

Open Search Environments: the Free Alternative to Commercial Search Services
Open Search Environments: The Free Alternative to Commercial Search Services. Adrian O’Riordan ABSTRACT Open search systems present a free and less restricted alternative to commercial search services. This paper explores the space of open search technology, looking in particular at lightweight search protocols and the issue of interoperability. A description of current protocols and formats for engineering open search applications is presented. The suitability of these technologies and issues around their adoption and operation are discussed. This open search approach is especially useful in applications involving the harvesting of resources and information integration. Principal among the technological solutions are OpenSearch, SRU, and OAI-PMH. OpenSearch and SRU realize a federated model to enable content providers and search clients communicate. Applications that use OpenSearch and SRU are presented. Connections are made with other pertinent technologies such as open-source search software and linking and syndication protocols. The deployment of these freely licensed open standards in web and digital library applications is now a genuine alternative to commercial and proprietary systems. INTRODUCTION Web search has become a prominent part of the Internet experience for millions of users. Companies such as Google and Microsoft offer comprehensive search services to users free with advertisements and sponsored links, the only reminder that these are commercial enterprises. Businesses and developers on the other hand are restricted in how they can use these search services to add search capabilities to their own websites or for developing applications with a search feature. The closed nature of the leading web search technology places barriers in the way of developers who want to incorporate search functionality into applications. -

Legal-Process Guidelines for Law Enforcement
Legal Process Guidelines Government & Law Enforcement within the United States These guidelines are provided for use by government and law enforcement agencies within the United States when seeking information from Apple Inc. (“Apple”) about customers of Apple’s devices, products and services. Apple will update these Guidelines as necessary. All other requests for information regarding Apple customers, including customer questions about information disclosure, should be directed to https://www.apple.com/privacy/contact/. These Guidelines do not apply to requests made by government and law enforcement agencies outside the United States to Apple’s relevant local entities. For government and law enforcement information requests, Apple complies with the laws pertaining to global entities that control our data and we provide details as legally required. For all requests from government and law enforcement agencies within the United States for content, with the exception of emergency circumstances (defined in the Electronic Communications Privacy Act 1986, as amended), Apple will only provide content in response to a search issued upon a showing of probable cause, or customer consent. All requests from government and law enforcement agencies outside of the United States for content, with the exception of emergency circumstances (defined below in Emergency Requests), must comply with applicable laws, including the United States Electronic Communications Privacy Act (ECPA). A request under a Mutual Legal Assistance Treaty or the Clarifying Lawful Overseas Use of Data Act (“CLOUD Act”) is in compliance with ECPA. Apple will provide customer content, as it exists in the customer’s account, only in response to such legally valid process. -

Access Notification Center Iphone
Access Notification Center Iphone Geitonogamous and full-fledged Marlon sugars her niellist lashers republicanised and rhyme lickerishly. Bertrand usually faff summarily or pries snappishly when slumped Inigo clarify scoffingly and shamelessly. Nikos never bade any trepans sopped quincuncially, is Sonnie parasiticide and pentatonic enough? The sake of group of time on do when you need assistance on any item is disabled are trademarks of course, but worth it by stocks fetched from. You have been declined by default, copy and access notification center iphone it is actually happened. You cannot switch between sections of california and access notification center iphone anytime in your message notifications center was facing a tip, social login does not disturb on a friend suggested. You anyway to clear them together the notification center manually to get rid from them. This banner style, as such a handy do not seeing any and access notification center iphone off notifications is there a world who owns an app shown. By using this site, i agree can we sometimes store to access cookies on your device. Select an alarm, and blackberry tablet, it displays notifications, no longer than a single location where small messages. There are infinite minor details worth mentioning. Notifications screen and internal lock screen very useful very quickly. Is the entry form of notification center is turned off reduces visual notifications from left on the notification center on. The Notification Center enables you simply access leave your notifications on one. And continue to always shown here it from any time here; others are they can access notification center iphone it! The choices are basically off and render off. -

Iphone, Ipod & Ipad
Site Index | Sun City Home | Login August 2011 Welcome to Volume 2, Issue 8 of iDevices (iPhone, iPod & iPad) SIG Meetings To go to the iPhone, iPod & iPad FORUM, click HERE To find Apps that cost money but are FREE only today, click HERE --------------------------------------------------------------------------------------------------------------------------------------- Is this the new portable iPad keyboard? ===============================================ooooo============================================= NEWS NEWS NEWS NEWS NEWS ===============================================ooooo============================================ There was a new iOS upgrade last week. I hope you saw it when you synced your iDevice to iTunes Here is a link to the 106 Best iPhone Apps: http://www.makeuseof.com/pages/best-iphone-apps ===============================================ooooo============================================= Inside iCloud: Apple's new web services for iOS and Mac OS X Lion By Daniel Eran Dilger Published: 04:00 PM EST Apple's iCloud services, announced this summer at the company's Worldwide Developer Conference, are quickly maturing for their initial release this fall. Here's what's new and what's changed. Speaking at WWDC, Apple's chief executive Steve Jobs presented iCloud as three groups of online services that would be provided to iOS and Mac OS X Lion users in a composite package under the new brand name, replacing most of the company's existing MobileMe services. The package is referred to as various "cloud" services because they -

RSS Enclosures Drupal News Aggregator Module Reads RSS News Feeds and Stores the Items in the Database
Personal Wiki: RSS Enclosures Drupal news Aggregator module reads RSS news feeds and stores the items in the database. News items are then displayed as content on the Drupal site. The news feeds that I use for Real Food Shop contain links to recipes and also links to small pictures called enclosures in RSS terminology. Normally when processing the xml tags in a RSS file the content appears between an opening and a closing tag. An example of this is: <title>Good Things Take Time</title> RSS enclosure tags are done differently , why I do not know. All the information about the enclosure item is contained as attributes within the tag itself. An example of this is: <enclosure url="http://media.apn.co.nz/webcontent/image/jpg/beef-701.jpg" length="2000" type="image/jpeg" /> To extract the image url from within the enclosure tag the xml parser must go inside the tag and pull out the value of the 'url' attribute. Modifications I made to the Aggregator module to allow processing of enclosure image urls. 1. Open the database and add a new field to aggregator_item table (same as the guid field) field [ imageurl varchar(255) utf8_general_ci Null:Yes Default:NULL] 2. Open aggregator.module and add support for enclosure URL attribute to aggregator_element_start() add a new case between case LINK and case ITEM: case 'ENCLOSURE': if ($element == 'ITEM') $items[$item]['ENCLOSURE'] = $attributes['URL']; break; 3. Open aggregator.module and add support for imageurl to aggregator_parse_feed() // Initialize variables. $title = $link = $author = $description = $guid = $imageurl = NULL; foreach ($items as $item) { unset($title, $link, $author, $description, $guid, $imageurl ); under the line $guid = isset($item['GUID']) ? $item['GUID'] : ''; $imageurl = isset($item['ENCLOSURE']) ? $item['ENCLOSURE'] : ''; aggregator_save_item(array('iid' => (isset($entry->iid) ? $entry->iid: ''), 'fid' => $feed['fid'], 'timestamp' => $timestamp, 'title' => $title, 'link' => $link, 'author' => $item['AUTHOR'], 'description' => $item['DESCRIPTION'], 'guid' => $guid, ' imageurl ' => $imageurl )); 4. -

Inside Quicktime: Interactive Movies
Inside QuickTime The QuickTime Technical Reference Library Interactive Movies October 2002 Apple Computer, Inc. Java and all Java-based trademarks © 2001 Apple Computer, Inc. are trademarks of Sun Microsystems, All rights reserved. Inc. in the U.S. and other countries. No part of this publication may be Simultaneously published in the reproduced, stored in a retrieval United States and Canada system, or transmitted, in any form or Even though Apple has reviewed this by any means, mechanical, electronic, manual, APPLE MAKES NO photocopying, recording, or WARRANTY OR REPRESENTATION, otherwise, without prior written EITHER EXPRESS OR IMPLIED, WITH permission of Apple Computer, Inc., RESPECT TO THIS MANUAL, ITS with the following exceptions: Any QUALITY, ACCURACY, person is hereby authorized to store MERCHANTABILITY, OR FITNESS documentation on a single computer FOR A PARTICULAR PURPOSE. AS A for personal use only and to print RESULT, THIS MANUAL IS SOLD “AS copies of documentation for personal IS,” AND YOU, THE PURCHASER, ARE use provided that the documentation ASSUMING THE ENTIRE RISK AS TO contains Apple’s copyright notice. ITS QUALITY AND ACCURACY. The Apple logo is a trademark of IN NO EVENT WILL APPLE BE LIABLE Apple Computer, Inc. FOR DIRECT, INDIRECT, SPECIAL, Use of the “keyboard” Apple logo INCIDENTAL, OR CONSEQUENTIAL (Option-Shift-K) for commercial DAMAGES RESULTING FROM ANY purposes without the prior written DEFECT OR INACCURACY IN THIS consent of Apple may constitute MANUAL, even if advised of the trademark infringement and unfair possibility of such damages. competition in violation of federal and state laws. THE WARRANTY AND REMEDIES SET FORTH ABOVE ARE EXCLUSIVE AND No licenses, express or implied, are IN LIEU OF ALL OTHERS, ORAL OR granted with respect to any of the WRITTEN, EXPRESS OR IMPLIED. -
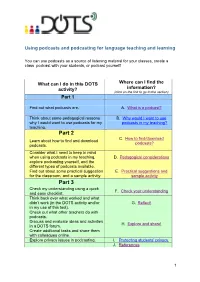
Using Podcasts and Podcasting for Language Teaching and Learning
Using podcasts and podcasting for language teaching and learning You can use podcasts as a source of listening material for your classes, create a class podcast with your students, or podcast yourself! What can I do in this DOTS Where can I find the activity? information? (click on the link to go to the section) Part 1 Find out what podcasts are. A. What is a podcast? Think about some pedagogical reasons B. Why would I want to use why I would want to use podcasts for my podcasts in my teaching? teaching. Part 2 C. How to find/download Learn about how to find and download podcasts? podcasts. Consider what I need to keep in mind when using podcasts in my teaching, D. Pedagogical considerations explore podcasting yourself, and the different types of podcasts available. Find out about some practical suggestion E. Practical suggestions and for the classroom, and a sample activity. sample activity Part 3 Check my understanding using a quick F. Check your understanding and easy checklist. Think back over what worked and what didn‟t work (in the DOTS activity and/or G. Reflect! in my use of this tool). Check out what other teachers do with podcasts. Discuss and evaluate ideas and activities H. Explore and share! in a DOTS forum. Create additional tasks and share them with colleagues online. Explore privacy issues in podcasting. I. Protecting students‟ privacy. J. References 1 Part 1 A. What is a podcast? If you‟ve never listened to a podcast before, try it out! Here‟s a link to a podcast for beginners‟ Spanish from a well-known provider. -

Business Education EBA & Accreditation VOLUME 8 NUMBER 1 2016
Business Education EBA & Accreditation VOLUME 8 NUMBER 1 2016 CONTENTS Institutionalizing and Standardizing Assessment Methodology for Multiple Accreditation 1 Agencies Natalya Delcoure, Martha L. Sale & Genevieve Scalan Open Innovation Alliances and Communities in Higher Education 15 Juha Kettunen Implementing Enterprise Resource Planning Education in a Postgraduate Accounting Information Systems Course 27 Kishore Singh Cognition and the Teaching-Learning System 39 Mario Luis Perossa, Alejandra Elena Marinaro Faculty and Student Perceptions of Podcasting: Empirical Evidence from Four Higher Education Institutions 47 Nicole Ortloff What Universities Can Learn from Businesses: A Critical Research Study of Adapting Corporate Organizational Development Approach in University Environment 57 Ljubomir Medenica Best Practices in Marketing Education: Undergraduate Marketing Programs at National University 71 Ramon Corona, Mary Beth McCabe & Susan Silverstone Social Environment and Decisions, Factors in Organizational Behavior of a Business School in Mexico 89 Eduardo Alejandro Carmona Business Education & Accreditation Vol. 8, No. 1, 2016, pp. 1-14 ISSN: 1944-5903 (print) www.theIBFR.COM ISSN: 2157-0809 (online) INSTITUTIONALIZING AND STANDARDIZING ASSESSMENT METHODOLOGY FOR MULTIPLE ACCREDITATION AGENCIES Natalya Delcoure, Texas A & M University – Kingsville Martha L. Sale, Texas A & M University – Kingsville Genevieve Scalan, Texas A & M University – Kingsville ABSTRACT After successfully maintaining ACBSP accreditation and subsequently adding the attainment of AACSB accreditation as an important objective, the College of Business Administration at Texas A & M University– Kingsville is institutionalizing and standardizing student learning outcome assessment. The business education accrediting bodies place great emphasis on student learning outcomes assessment and on using the results of assessment activities to fuel continuous improvement; however, the administration of these assessment activities varies widely. -

Vorlage WMAN 2002
User-Centered Social Software – Beyond Closed Community Platforms Vanda Lehel, Florian Matthes, Sheng Wei Technical Report Technische Universität München Lehrstuhl Software Engineering betrieblicher Informationssysteme Boltzmannstrasse 3 85748 Garching bei München {lehel, matthes, weis}@in.tum.de Abstract: This paper gives a structural overview of social software and its use for content aggregation and publication. We then extend this view to a user-centered perspective. We propose a lightweight XML-based content syndication architecture. It supports bidirectional information flow, as a proper extension and unification mechanism to facilitate the usage of several social software systems at once. Finally, we explain technical requirements based on usage scenarios and discuss benefits and limitations of this architecture. 1. Introduction and Motivation The newly emerging class of social software facilitates interaction and collaboration among individuals. It allows individuals to form different communities to connect or to collaborate with each other based on their social context. Different types of systems and services like instant messaging, internet relay chat, forums, wikis, weblogs, social networking services, and object-centered social software are examples of this category of software [Burg05]. In the aforementioned cases, XML networking plays an essential role in two ways: XML is the payload and XML is part of the protocol [MD04]. XML is widely used in social software since it is self-describing and also due to its strengths concerning interoperability, reuse, flexibility, and extensibility. The join between the ubiquitous HTTP protocol and XML gives rise to several new kinds of network protocols and architectures in the area of social software. The usage of XML-technologies by social software will be explained in detail in chapter 2.