Lecture 1: Crypto Overview, Perfect Secrecy, One-Time
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Public Life of Secrets: Deception, Disclosure, and Discursive Framing in the Policy Process
STXXXX10.1177/0735275115587388Sociological TheoryBail 587388research-article2015 Original Article Sociological Theory 2015, Vol. 33(2) 97 –124 The Public Life of Secrets: © American Sociological Association 2015 DOI: 10.1177/0735275115587388 Deception, Disclosure, and stx.sagepub.com Discursive Framing in the Policy Process Christopher A. Bail1 Abstract While secrecy enables policy makers to escape public scrutiny, leaks of classified information reveal the social construction of reality by the state. I develop a theory that explains how leaks shape the discursive frames states create to communicate the causes of social problems to the public and corresponding solutions to redress them. Synthesizing cultural sociology, symbolic interactionism, and ethnomethodology, I argue that leaks enable non– state actors to amplify contradictions between the public and secret behavior of the state. States respond by “ad hoc–ing” new frames that normalize their secret transgressions as logical extensions of other policy agendas. While these syncretic responses resolve contradictions exposed by leaks, they gradually detach discursive frames from reality and therefore increase states’ need for secrecy—as well as the probability of future leaks—in turn. I illustrate this downward spiral of deception and disclosure via a case study of the British government’s discourse about terrorism between 2000 and 2008. Keywords cultural sociology, political sociology, secrecy, symbolic interactionism, comparative- historical sociology “For in the order of things it is found that one never seeks to avoid one inconvenience without running into another.” —Machiavelli (The Prince, chapter 21) A vast literature explains how policy makers shape public understandings of social problems in order to accomplish their agenda (e.g., Alexander and Smith 1993; Berezin 1997; Jacobs and Sobieraj 2007; Reed 2013; Skrentny 2004; Somers and Block 2005; Spillman 1997; Steensland 2007; Wagner-Pacifici 1994). -

Writing About Espionage Secrets
Secrecy and Society ISSN: 2377-6188 Volume 2 Number 1 Secrecy and Intelligence Article 7 September 2018 Writing About Espionage Secrets Kristie Macrakis Georgia Tech, Atlanta, [email protected] Follow this and additional works at: https://scholarworks.sjsu.edu/secrecyandsociety Part of the History of Science, Technology, and Medicine Commons, and the Other History Commons Recommended Citation Macrakis, Kristie. 2018. "Writing About Espionage Secrets." Secrecy and Society 2(1). https://doi.org/10.31979/2377-6188.2018.020107 https://scholarworks.sjsu.edu/ secrecyandsociety/vol2/iss1/7 This Special Issue Article is brought to you for free and open access by the School of Information at SJSU ScholarWorks. It has been accepted for inclusion in Secrecy and Society by an authorized administrator of SJSU ScholarWorks. For more information, please contact [email protected]. Writing About Espionage Secrets Abstract This article describes the author’s experiences researching three books on espionage history in three different countries and on three different topics. The article describes the foreign intelligence arm of the Ministry for State Security; a global history of secret writing from ancient to modern times; and finally, my current project on U.S. intelligence and technology from the Cold War to the War on Terror. The article also discusses the tensions between national security and openness and reflects on the results of this research and its implications for history and for national security. Keywords Central Intelligence Agency, CIA, -

National Security Secrecy: How the Limits Change
Steven Aftergood National Security Secrecy: How the Limits Change as a nation, we seem to be of two minds about secrecy. we know that government secrecy is incompatible with democratic decision-making in obvious ways. By definition, secrecy limits access to official information, thereby impeding public participation in the deliberative process and inhibiting or preventing the accountability of government officials for their actions. Yet there is a near universal consensus that some measure of secrecy is justified and necessary to protect authorized national security activities, such as intelligence gathering and military operations, to permit confidential deliberations in the course of policy development, to secure personal privacy, and for other reasons. Reconciling these conflicting interests is an ongoing challenge. A stable secrecy policy is hard to achieve since the proper boundaries of offi- cial secrecy cannot be clearly articulated in the abstract and tend to shift over time. In practice, decisions to restrict information seem to depend on prevailing security considerations (secrecy is more pronounced in time of war), official predispositions (some political leaders favor secrecy more than others), and public attitudes and expectations. In recent years, a large and growing number of public interest organizations and professional societies have turned their attention to government secrecy, identifying it as an obstacle to achieving their own objectives. In fact, there are at least two entire coalitions of organiza- tions devoted to combating secrecy: Openthegovernment.org and the Research for this paper was supported by grants from the Foundation to Promote Open Society, the HKH Foundation, the CS Fund, the Stewart R. Mott Foundation, and the Rockefeller Family Fund. -

Simple Substitution and Caesar Ciphers
Spring 2015 Chris Christensen MAT/CSC 483 Simple Substitution Ciphers The art of writing secret messages – intelligible to those who are in possession of the key and unintelligible to all others – has been studied for centuries. The usefulness of such messages, especially in time of war, is obvious; on the other hand, their solution may be a matter of great importance to those from whom the key is concealed. But the romance connected with the subject, the not uncommon desire to discover a secret, and the implied challenge to the ingenuity of all from who it is hidden have attracted to the subject the attention of many to whom its utility is a matter of indifference. Abraham Sinkov In Mathematical Recreations & Essays By W.W. Rouse Ball and H.S.M. Coxeter, c. 1938 We begin our study of cryptology from the romantic point of view – the point of view of someone who has the “not uncommon desire to discover a secret” and someone who takes up the “implied challenged to the ingenuity” that is tossed down by secret writing. We begin with one of the most common classical ciphers: simple substitution. A simple substitution cipher is a method of concealment that replaces each letter of a plaintext message with another letter. Here is the key to a simple substitution cipher: Plaintext letters: abcdefghijklmnopqrstuvwxyz Ciphertext letters: EKMFLGDQVZNTOWYHXUSPAIBRCJ The key gives the correspondence between a plaintext letter and its replacement ciphertext letter. (It is traditional to use small letters for plaintext and capital letters, or small capital letters, for ciphertext. We will not use small capital letters for ciphertext so that plaintext and ciphertext letters will line up vertically.) Using this key, every plaintext letter a would be replaced by ciphertext E, every plaintext letter e by L, etc. -

Cryptanalysis of Mono-Alphabetic Substitution Ciphers Using Genetic Algorithms and Simulated Annealing Shalini Jain Marathwada Institute of Technology, Dr
Vol. 08 No. 01 2018 p-ISSN 2202-2821 e-ISSN 1839-6518 (Australian ISSN Agency) 82800801201801 Cryptanalysis of Mono-Alphabetic Substitution Ciphers using Genetic Algorithms and Simulated Annealing Shalini Jain Marathwada Institute of Technology, Dr. Babasaheb Ambedkar Marathwada University, India Nalin Chhibber University of Waterloo, Ontario, Canada Sweta Kandi Marathwada Institute of Technology, Dr. Babasaheb Ambedkar Marathwada University, India ABSTRACT – In this paper, we intend to apply the principles of genetic algorithms along with simulated annealing to cryptanalyze a mono-alphabetic substitution cipher. The type of attack used for cryptanalysis is a ciphertext-only attack in which we don’t know any plaintext. In genetic algorithms and simulated annealing, for ciphertext-only attack, we need to have the solution space or any method to match the decrypted text to the language text. However, the challenge is to implement the project while maintaining computational efficiency and a high degree of security. We carry out three attacks, the first of which uses genetic algorithms alone, the second which uses simulated annealing alone and the third which uses a combination of genetic algorithms and simulated annealing. Key words: Cryptanalysis, mono-alphabetic substitution cipher, genetic algorithms, simulated annealing, fitness I. Introduction II. Mono-alphabetic substitution cipher Cryptanalysis involves the dissection of computer systems by A mono-alphabetic substitution cipher is a class of substitution unauthorized persons in order to gain knowledge about the ciphers in which the same letters of the plaintext are replaced unknown aspects of the system. It can be used to gain control by the same letters of the ciphertext. -

INTERVENTION of STATE SOVEREIGNTY THROUGH RELEASING STATE SECRECY by WIKILEAKS Engla Puspita Haria, S.H.,M.H
INTERVENTION OF STATE SOVEREIGNTY THROUGH RELEASING STATE SECRECY BY WIKILEAKS Engla Puspita Haria, S.H.,M.H. ABSTRACT The increasing number of disclosure of state secrecy in this age create by Wikileaks make the impact for state sovereignty such as stability of state, disturb the relationship between the state, dysfunction of government and political and economic instance. This number happened because of some factors:1) insufficiency of sophisticated technological support provided by related state, advancement and introducing new technology, collision between staff members. corruptions, and international criminal syndicated:2)the inconstancy law regulated the criminal act about secrecy state;3)technological advances while the human resources that are not reliable. But in other hand, people have right to know and it remarkable in Declaration of Human Right article 19 But there is no regulation at national and international level for Wikileaks. In this research, the study will investigate two problems: 1) what the impact for state sovereignty because of disclosure state secrecy; and 2) what is the legal action to protect state secrecy and study will find the problem of this research and create some offered solution and use the ultimate value in of all part the research with use the existence of legal theory, legal practice, norm or regulations, legal fact and indicated the conflict either. So this research will use normative type of research. In fact, in this research, study has analyze the case of Wikileaks and found that wikileaks already disclosure the data that very important for state sovereignty. Most of their documents are from the people who steal from diplomatic cable of state. -

Understanding Self-Deception Through Theory, Evidence and Application
Secrecy and Society ISSN: 2377-6188 Volume 2 Number 2 Teaching Secrecy Article 2 January 2021 Keeping Secrets from Ourselves: Understanding Self-deception Through Theory, Evidence and Application Mathew J. Creighton University College Dublin, Ireland, [email protected] Follow this and additional works at: https://scholarworks.sjsu.edu/secrecyandsociety Part of the Other Sociology Commons Recommended Citation Creighton, Mathew J.. 2021. "Keeping Secrets from Ourselves: Understanding Self- deception Through Theory, Evidence and Application." Secrecy and Society 2(2). https://doi.org/10.31979/2377-6188.2021.020202 https://scholarworks.sjsu.edu/ secrecyandsociety/vol2/iss2/2 This Special Issue Article is brought to you for free and open access by the School of Information at SJSU ScholarWorks. It has been accepted for inclusion in Secrecy and Society by an authorized administrator of SJSU ScholarWorks. For more information, please contact [email protected]. This work is licensed under a Creative Commons Attribution-Noncommercial-Share Alike 4.0 License. Keeping Secrets from Ourselves: Understanding Self-deception Through Theory, Evidence and Application Abstract Self-deception is a difficult concept to share with students. Although few students find it implausible that they are capable of keeping secrets from themselves, the social theory, application, and practical demonstration of self-deception is far from straightforward. This work offers a three-step approach to teach a theoretically-grounded, evidence-based, and application-reinforced understanding of self-deception. Rooted in work on identity by Mead (1934), the approach outlined here engages with interdisciplinary case studies derived from social psychology (Greenwald, McGhee and Schwartz 1998) and behavioral economics (Ariely 2012). -
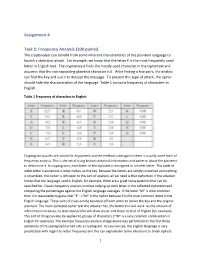
Assignment 4 Task 1: Frequency Analysis (100 Points)
Assignment 4 Task 1: Frequency Analysis (100 points) The cryptanalyst can benefit from some inherent characteristics of the plaintext language to launch a statistical attack. For example, we know that the letter E is the most frequently used letter in English text. The cryptanalyst finds the mostly-used character in the ciphertext and assumes that the corresponding plaintext character is E. After finding a few pairs, the analyst can find the key and use it to decrypt the message. To prevent this type of attack, the cipher should hide the characteristics of the language. Table 1 contains frequency of characters in English. Table 1 Frequency of characters in English Cryptogram puzzles are solved for enjoyment and the method used against them is usually some form of frequency analysis. This is the act of using known statistical information and patterns about the plaintext to determine it. In cryptograms, each letter of the alphabet is encrypted to another letter. This table of letter-letter translations is what makes up the key. Because the letters are simply converted and nothing is scrambled, the cipher is left open to this sort of analysis; all we need is that ciphertext. If the attacker knows that the language used is English, for example, there are a great many patterns that can be searched for. Classic frequency analysis involves tallying up each letter in the collected ciphertext and comparing the percentages against the English language averages. If the letter "M" is most common then it is reasonable to guess that "E"-->"M" in the cipher because E is the most common letter in the English language. -

John F. Byrne's Chaocipher Revealed
John F. Byrne’s Chaocipher Revealed John F. Byrne’s Chaocipher Revealed: An Historical and Technical Appraisal MOSHE RUBIN1 Abstract Chaocipher is a method of encryption invented by John F. Byrne in 1918, who tried unsuccessfully to interest the US Signal Corp and Navy in his system. In 1953, Byrne presented Chaocipher-encrypted messages as a challenge in his autobiography Silent Years. Although numerous students of cryptanalysis attempted to solve the challenge messages over the years, none succeeded. For ninety years the Chaocipher algorithm was a closely guarded secret known only to a handful of persons. Following fruitful negotiations with the Byrne family during the period 2009-2010, the Chaocipher papers and materials have been donated to the National Cryptologic Museum in Ft. Meade, MD. This paper presents a comprehensive historical and technical evaluation of John F. Byrne and his Chaocipher system. Keywords ACA, American Cryptogram Association, block cipher encryption modes, Chaocipher, dynamic substitution, Greg Mellen, Herbert O. Yardley, John F. Byrne, National Cryptologic Museum, Parker Hitt, Silent Years, William F. Friedman 1 Introduction John Francis Byrne was born on 11 February 1880 in Dublin, Ireland. He was an intimate friend of James Joyce, the famous Irish writer and poet, studying together in Belvedere College and University College in Dublin. Joyce based the character named Cranly in Joyce’s A Portrait of the Artist as a Young Man on Byrne, used Byrne’s Dublin residence of 7 Eccles Street as the home of Leopold and Molly Bloom, the main characters in Joyce’s Ulysses, and made use of real-life anecdotes of himself and Byrne as the basis of stories in Ulysses. -

Shift Cipher Substitution Cipher Vigenère Cipher Hill Cipher
Lecture 2 Classical Cryptosystems Shift cipher Substitution cipher Vigenère cipher Hill cipher 1 Shift Cipher • A Substitution Cipher • The Key Space: – [0 … 25] • Encryption given a key K: – each letter in the plaintext P is replaced with the K’th letter following the corresponding number ( shift right ) • Decryption given K: – shift left • History: K = 3, Caesar’s cipher 2 Shift Cipher • Formally: • Let P=C= K=Z 26 For 0≤K≤25 ek(x) = x+K mod 26 and dk(y) = y-K mod 26 ʚͬ, ͭ ∈ ͔ͦͪ ʛ 3 Shift Cipher: An Example ABCDEFGHIJKLMNOPQRSTUVWXYZ 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 • P = CRYPTOGRAPHYISFUN Note that punctuation is often • K = 11 eliminated • C = NCJAVZRCLASJTDQFY • C → 2; 2+11 mod 26 = 13 → N • R → 17; 17+11 mod 26 = 2 → C • … • N → 13; 13+11 mod 26 = 24 → Y 4 Shift Cipher: Cryptanalysis • Can an attacker find K? – YES: exhaustive search, key space is small (<= 26 possible keys). – Once K is found, very easy to decrypt Exercise 1: decrypt the following ciphertext hphtwwxppelextoytrse Exercise 2: decrypt the following ciphertext jbcrclqrwcrvnbjenbwrwn VERY useful MATLAB functions can be found here: http://www2.math.umd.edu/~lcw/MatlabCode/ 5 General Mono-alphabetical Substitution Cipher • The key space: all possible permutations of Σ = {A, B, C, …, Z} • Encryption, given a key (permutation) π: – each letter X in the plaintext P is replaced with π(X) • Decryption, given a key π: – each letter Y in the ciphertext C is replaced with π-1(Y) • Example ABCDEFGHIJKLMNOPQRSTUVWXYZ πBADCZHWYGOQXSVTRNMSKJI PEFU • BECAUSE AZDBJSZ 6 Strength of the General Substitution Cipher • Exhaustive search is now infeasible – key space size is 26! ≈ 4*10 26 • Dominates the art of secret writing throughout the first millennium A.D. -

Secrecy, Coercion and Deception in Research on 'Terrorism'
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Aston Publications Explorer Contemporary Social Science Journal of the Academy of Social Sciences ISSN: 2158-2041 (Print) 2158-205X (Online) Journal homepage: https://www.tandfonline.com/loi/rsoc21 Secrecy, coercion and deception in research on ‘terrorism’ and ‘extremism’ Narzanin Massoumi, Tom Mills & David Miller To cite this article: Narzanin Massoumi, Tom Mills & David Miller (2019): Secrecy, coercion and deception in research on ‘terrorism’ and ‘extremism’, Contemporary Social Science, DOI: 10.1080/21582041.2019.1616107 To link to this article: https://doi.org/10.1080/21582041.2019.1616107 © 2019 The Author(s). Published by Informa UK Limited, trading as Taylor & Francis Group Published online: 19 May 2019. Submit your article to this journal Article views: 551 View Crossmark data Full Terms & Conditions of access and use can be found at https://www.tandfonline.com/action/journalInformation?journalCode=rsoc21 CONTEMPORARY SOCIAL SCIENCE https://doi.org/10.1080/21582041.2019.1616107 Secrecy, coercion and deception in research on ‘terrorism’ and ‘extremism’ Narzanin Massoumi a, Tom Mills b and David Miller c aSociology, Philosophy and Anthropology, University of Exeter, Exeter, UK; bSchool of Languages and Social Sciences, Aston University, Birmingham, UK; cSchool of Policy Studies, University of Bristol, Bristol, UK ABSTRACT ARTICLE HISTORY This article calls for more understanding of the ethical challenges and Received 16 November 2018 dilemmas that arise as a result of state involvement in academic Accepted 26 April 2019 research on ‘terrorism’ and ‘extremism’.Itsuggeststhatresearchers KEYWORDS and research institutions need to be more attentive to the fl Research ethics; terrorism; possibilities of co-option, compromise, con ict of interests and other secret research; academic ethical issues. -

Network Security
Cristina Nita-Rotaru CS6740: Network security Additional material: Cryptography 1: Terminology and classic ciphers Readings for this lecture Required readings: } Cryptography on Wikipedia Interesting reading } The Code Book by Simon Singh 3 Cryptography The science of secrets… } Cryptography: the study of mathematical techniques related to aspects of providing information security services (create) } Cryptanalysis: the study of mathematical techniques for attempting to defeat information security services (break) } Cryptology: the study of cryptography and cryptanalysis (both) 4 Cryptography Basic terminology in cryptography } cryptography } plaintexts } cryptanalysis } ciphertexts } cryptology } keys } encryption } decryption plaintext ciphertext plaintext Encryption Decryption Key_Encryption Key_Decryption 5 Cryptography Cryptographic protocols } Protocols that } Enable parties } Achieve objectives (goals) } Overcome adversaries (attacks) } Need to understand } Who are the parties and the context in which they act } What are the goals of the protocols } What are the capabilities of adversaries 6 Cryptography Cryptographic protocols: Parties } The good guys } The bad guys Alice Carl Bob Eve Introduction of Alice and Bob Check out wikipedia for a longer attributed to the original RSA paper. list of malicious crypto players. 7 Cryptography Cryptographic protocols: Objectives/Goals } Most basic problem: } Ensure security of communication over an insecure medium } Basic security goals: } Confidentiality (secrecy, confidentiality) } Only the