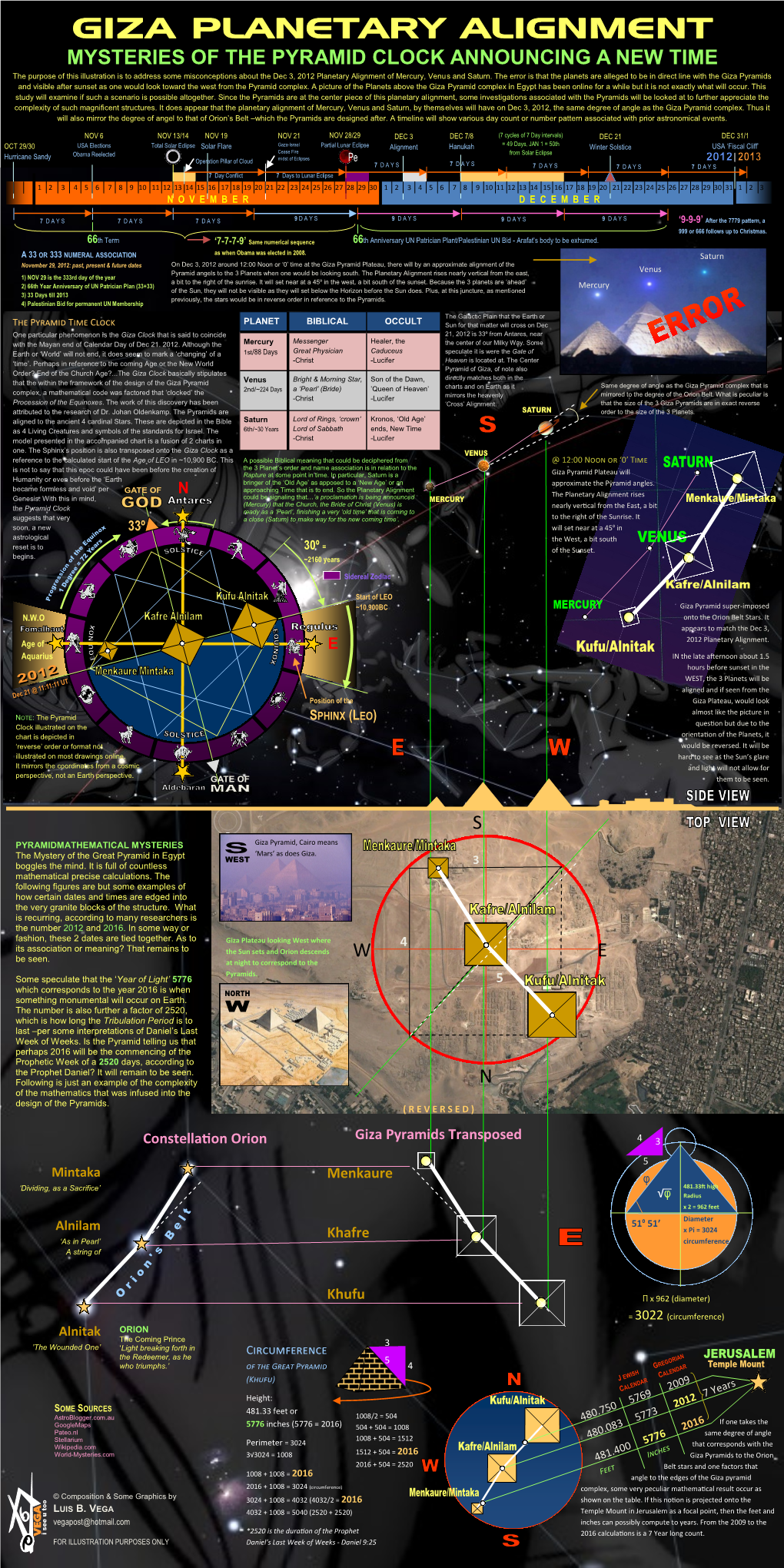
Giza Planetary Alignment
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Block Ciphers and the Data Encryption Standard
Lecture 3: Block Ciphers and the Data Encryption Standard Lecture Notes on “Computer and Network Security” by Avi Kak ([email protected]) January 26, 2021 3:43pm ©2021 Avinash Kak, Purdue University Goals: To introduce the notion of a block cipher in the modern context. To talk about the infeasibility of ideal block ciphers To introduce the notion of the Feistel Cipher Structure To go over DES, the Data Encryption Standard To illustrate important DES steps with Python and Perl code CONTENTS Section Title Page 3.1 Ideal Block Cipher 3 3.1.1 Size of the Encryption Key for the Ideal Block Cipher 6 3.2 The Feistel Structure for Block Ciphers 7 3.2.1 Mathematical Description of Each Round in the 10 Feistel Structure 3.2.2 Decryption in Ciphers Based on the Feistel Structure 12 3.3 DES: The Data Encryption Standard 16 3.3.1 One Round of Processing in DES 18 3.3.2 The S-Box for the Substitution Step in Each Round 22 3.3.3 The Substitution Tables 26 3.3.4 The P-Box Permutation in the Feistel Function 33 3.3.5 The DES Key Schedule: Generating the Round Keys 35 3.3.6 Initial Permutation of the Encryption Key 38 3.3.7 Contraction-Permutation that Generates the 48-Bit 42 Round Key from the 56-Bit Key 3.4 What Makes DES a Strong Cipher (to the 46 Extent It is a Strong Cipher) 3.5 Homework Problems 48 2 Computer and Network Security by Avi Kak Lecture 3 Back to TOC 3.1 IDEAL BLOCK CIPHER In a modern block cipher (but still using a classical encryption method), we replace a block of N bits from the plaintext with a block of N bits from the ciphertext. -

Egypt and the Egyptians
Cambridge University Press 978-0-521-61689-8 - Egypt and the Egtptians, Second Edition Douglas J. Brewer and Emily Teeter Frontmatter More information Egypt and the Egyptians Surveying more than three thousand years of Egyptian civilization, Egypt and the Egyptians offers a comprehensive introduction to this most rich and complex of early societies. From high politics to the concerns of everyday Egyptians, the book explores every aspect of Egyptian culture and society, including religion, language, art, architecture, cities, and mummification. Archaeological and doc- umentary sources are combined to give the reader a unique and expansive view of a remarkable ancient culture. Fully revised and updated, this new edition looks more closely at the role of women in Egypt, delves deeper into the Egyptian Neolithic and Egypt’s transi- tion to an agricultural society, and includes many new illustrations. Written for students and the general reader, and including an extensive bibliography, a glossary, a dynastic chronology and suggestions for further reading, this richly illustrated book is an essential resource for anybody wishing to explore the society and civilization of ancient Egypt. douglas j. brewer is Professor of Anthropology at the University of Illi- nois, Urbana, and Director of the Spurlock Museum. He is the author of numer- ous books and articles on Egypt covering topics from domestication to cultural change and the environment. He has over twenty-five years’ experience of field- work in Egypt and is currently co-director of the excavations at Mendes. emily teeter is an Egyptologist and Research Associate at the Oriental Insti- tute, University of Chicago. -

Related-Key Cryptanalysis of 3-WAY, Biham-DES,CAST, DES-X, Newdes, RC2, and TEA
Related-Key Cryptanalysis of 3-WAY, Biham-DES,CAST, DES-X, NewDES, RC2, and TEA John Kelsey Bruce Schneier David Wagner Counterpane Systems U.C. Berkeley kelsey,schneier @counterpane.com [email protected] f g Abstract. We present new related-key attacks on the block ciphers 3- WAY, Biham-DES, CAST, DES-X, NewDES, RC2, and TEA. Differen- tial related-key attacks allow both keys and plaintexts to be chosen with specific differences [KSW96]. Our attacks build on the original work, showing how to adapt the general attack to deal with the difficulties of the individual algorithms. We also give specific design principles to protect against these attacks. 1 Introduction Related-key cryptanalysis assumes that the attacker learns the encryption of certain plaintexts not only under the original (unknown) key K, but also under some derived keys K0 = f(K). In a chosen-related-key attack, the attacker specifies how the key is to be changed; known-related-key attacks are those where the key difference is known, but cannot be chosen by the attacker. We emphasize that the attacker knows or chooses the relationship between keys, not the actual key values. These techniques have been developed in [Knu93b, Bih94, KSW96]. Related-key cryptanalysis is a practical attack on key-exchange protocols that do not guarantee key-integrity|an attacker may be able to flip bits in the key without knowing the key|and key-update protocols that update keys using a known function: e.g., K, K + 1, K + 2, etc. Related-key attacks were also used against rotor machines: operators sometimes set rotors incorrectly. -

Classifying Classic Ciphers Using Machine Learning
San Jose State University SJSU ScholarWorks Master's Projects Master's Theses and Graduate Research Spring 5-20-2019 Classifying Classic Ciphers using Machine Learning Nivedhitha Ramarathnam Krishna San Jose State University Follow this and additional works at: https://scholarworks.sjsu.edu/etd_projects Part of the Artificial Intelligence and Robotics Commons, and the Information Security Commons Recommended Citation Krishna, Nivedhitha Ramarathnam, "Classifying Classic Ciphers using Machine Learning" (2019). Master's Projects. 699. DOI: https://doi.org/10.31979/etd.xkgs-5gy6 https://scholarworks.sjsu.edu/etd_projects/699 This Master's Project is brought to you for free and open access by the Master's Theses and Graduate Research at SJSU ScholarWorks. It has been accepted for inclusion in Master's Projects by an authorized administrator of SJSU ScholarWorks. For more information, please contact [email protected]. Classifying Classic Ciphers using Machine Learning A Project Presented to The Faculty of the Department of Computer Science San José State University In Partial Fulfillment of the Requirements for the Degree Master of Science by Nivedhitha Ramarathnam Krishna May 2019 © 2019 Nivedhitha Ramarathnam Krishna ALL RIGHTS RESERVED The Designated Project Committee Approves the Project Titled Classifying Classic Ciphers using Machine Learning by Nivedhitha Ramarathnam Krishna APPROVED FOR THE DEPARTMENT OF COMPUTER SCIENCE SAN JOSÉ STATE UNIVERSITY May 2019 Dr. Mark Stamp Department of Computer Science Dr. Thomas Austin Department of Computer Science Professor Fabio Di Troia Department of Computer Science ABSTRACT Classifying Classic Ciphers using Machine Learning by Nivedhitha Ramarathnam Krishna We consider the problem of identifying the classic cipher that was used to generate a given ciphertext message. -

Chapter 3 – Block Ciphers and the Data Encryption Standard
Symmetric Cryptography Chapter 6 Block vs Stream Ciphers • Block ciphers process messages into blocks, each of which is then en/decrypted – Like a substitution on very big characters • 64-bits or more • Stream ciphers process messages a bit or byte at a time when en/decrypting – Many current ciphers are block ciphers • Better analyzed. • Broader range of applications. Block vs Stream Ciphers Block Cipher Principles • Block ciphers look like an extremely large substitution • Would need table of 264 entries for a 64-bit block • Arbitrary reversible substitution cipher for a large block size is not practical – 64-bit general substitution block cipher, key size 264! • Most symmetric block ciphers are based on a Feistel Cipher Structure • Needed since must be able to decrypt ciphertext to recover messages efficiently Ideal Block Cipher Substitution-Permutation Ciphers • in 1949 Shannon introduced idea of substitution- permutation (S-P) networks – modern substitution-transposition product cipher • These form the basis of modern block ciphers • S-P networks are based on the two primitive cryptographic operations we have seen before: – substitution (S-box) – permutation (P-box) (transposition) • Provide confusion and diffusion of message Diffusion and Confusion • Introduced by Claude Shannon to thwart cryptanalysis based on statistical analysis – Assume the attacker has some knowledge of the statistical characteristics of the plaintext • Cipher needs to completely obscure statistical properties of original message • A one-time pad does this Diffusion -

2019-Egypt-Skydive.Pdf
Giza Pyramids Skydive Adventure February 15-19, 2019 “Yesterday we fell over the pyramids of Giza. Today we climbed into the King’s Chamber of the Great Pyramid. I could not think of any other way on (or above) the earth to experience all of the awe inspiring mysteries that this world has to offer.” JUMP Like a Pharaoh in 2019 Start making plans now for our first Tandem Jump Adventure over the Pyramids of Giza! Tandem Skydive over the Great Giza Pyramid, one of the Seven Ancient Wonders of the World. Leap from an Egyptian military Hercules C-130 and land between the pyramids. No prior skydiving experience is necessary….just bring your sense of adventure! Skydive Egypt – Sample Itinerary February 15th-19th, 2019 Day 1, February 15 – Arrival Arrive in Cairo, Egypt at own expense Met by Incredible Adventures Representative Transfer to Mercure La Sphinx Hotel * Days 2, 3 - February 16 – 17 – Designated Jump Days** Arrive at Drop Zone Review and sign any necessary waivers Group briefing and equipment fitting Review of aircraft safety procedures and features Individual training with assigned tandem master Complete incredible Great Giza Tandem Skydive Day 4 (5) – February 18 (19) Free Day for Sightseeing & Jump Back-Up Day - Depart Egypt Note: Hotel room will be kept until check-out time on the 19th. American clients should plan to depart on an “overnight flight” leaving after midnight on the 18th. * Designated hotel may change, based on availability. Upgrade to the Marriott Mena for an additional fee. ** You’ll be scheduled in advance to tandem jump on Day 2 or 3, with Day 4 serving as a weather back-up day. -

Provable Security Evaluation of Structures Against Impossible Differential and Zero Correlation Linear Cryptanalysis ⋆
Provable Security Evaluation of Structures against Impossible Differential and Zero Correlation Linear Cryptanalysis ⋆ Bing Sun1,2,4, Meicheng Liu2,3, Jian Guo2, Vincent Rijmen5, Ruilin Li6 1 College of Science, National University of Defense Technology, Changsha, Hunan, P.R.China, 410073 2 Nanyang Technological University, Singapore 3 State Key Laboratory of Information Security, Institute of Information Engineering, Chinese Academy of Sciences, Beijing, P.R. China, 100093 4 State Key Laboratory of Cryptology, P.O. Box 5159, Beijing, P.R. China, 100878 5 Dept. Electrical Engineering (ESAT), KU Leuven and iMinds, Belgium 6 College of Electronic Science and Engineering, National University of Defense Technology, Changsha, Hunan, P.R.China, 410073 happy [email protected] [email protected] [email protected] [email protected] [email protected] Abstract. Impossible differential and zero correlation linear cryptanal- ysis are two of the most important cryptanalytic vectors. To character- ize the impossible differentials and zero correlation linear hulls which are independent of the choices of the non-linear components, Sun et al. proposed the structure deduced by a block cipher at CRYPTO 2015. Based on that, we concentrate in this paper on the security of the SPN structure and Feistel structure with SP-type round functions. Firstly, we prove that for an SPN structure, if α1 → β1 and α2 → β2 are possi- ble differentials, α1|α2 → β1|β2 is also a possible differential, i.e., the OR “|” operation preserves differentials. Secondly, we show that for an SPN structure, there exists an r-round impossible differential if and on- ly if there exists an r-round impossible differential α → β where the Hamming weights of both α and β are 1. -

Theory and Practice of Cryptography: Lecture 1
Theory and Practice of Cryptography From Classical to Modern About this Course All course materials: http://saweis.net/crypto.shtml Four Lectures: 1. History and foundations of modern cryptography. 2. Using cryptography in practice and at Google. 3. Theory of cryptography: proofs and definitions. 4. A special topic in cryptography. Classic Definition of Cryptography Kryptósgráfo , or the art of "hidden writing", classically meant hiding the contents or existence of messages from an adversary. Informally, encryption renders the contents of a message unintelligible to anyone not possessing some secret information. Steganography, or "covered writing", is concerned with hiding the existence of a message -- often in plain sight. Scytale Transposition Cipher Caesar Substitution Cipher Zodiac Cipher Vigenère Polyalphabetic Substitution Key: GOOGLE Plaintext: BUYYOUTUBE Ciphertext: HIMEZYZIPK Rotor-based Polyalphabetic Ciphers Steganography He rodotus tattoo and wax tablets Inv is ible ink Mic rodots "Th e Finger" Priso n gang codes Low-order bits Codes Codes replace a specific piece of plaintext with a predefined code word. Codes are essentially a substitution cipher, but can replace strings of symbols rather than just individual symbols. Examples: "One if by land, two if by sea." Beale code Numbers stations ECB Mode Kerckhoffs' Principle A cryptosystem should be secure even if everything about it is public knowledge except the secret key. Do not rely on "security through obscurity". One-Time Pads Generate a random key of equal length to your message, then exclusive-or (XOR) the key with your message. This is information theoretically secure...but: "To transmit a large secret message, first transmit a large secret message" One time means one time. -

Optimization of Core Components of Block Ciphers Baptiste Lambin
Optimization of core components of block ciphers Baptiste Lambin To cite this version: Baptiste Lambin. Optimization of core components of block ciphers. Cryptography and Security [cs.CR]. Université Rennes 1, 2019. English. NNT : 2019REN1S036. tel-02380098 HAL Id: tel-02380098 https://tel.archives-ouvertes.fr/tel-02380098 Submitted on 26 Nov 2019 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. THÈSE DE DOCTORAT DE L’UNIVERSITE DE RENNES 1 COMUE UNIVERSITE BRETAGNE LOIRE Ecole Doctorale N°601 Mathématique et Sciences et Technologies de l’Information et de la Communication Spécialité : Informatique Par Baptiste LAMBIN Optimization of Core Components of Block Ciphers Thèse présentée et soutenue à RENNES, le 22/10/2019 Unité de recherche : IRISA Rapporteurs avant soutenance : Marine Minier, Professeur, LORIA, Université de Lorraine Jacques Patarin, Professeur, PRiSM, Université de Versailles Composition du jury : Examinateurs : Marine Minier, Professeur, LORIA, Université de Lorraine Jacques Patarin, Professeur, PRiSM, Université de Versailles Jean-Louis Lanet, INRIA Rennes Virginie Lallemand, Chargée de Recherche, LORIA, CNRS Jérémy Jean, ANSSI Dir. de thèse : Pierre-Alain Fouque, IRISA, Université de Rennes 1 Co-dir. de thèse : Patrick Derbez, IRISA, Université de Rennes 1 Remerciements Je tiens à remercier en premier lieu mes directeurs de thèse, Pierre-Alain et Patrick. -

Chapter 2 the Data Encryption Standard (DES)
Chapter 2 The Data Encryption Standard (DES) As mentioned earlier there are two main types of cryptography in use today - symmet- ric or secret key cryptography and asymmetric or public key cryptography. Symmet- ric key cryptography is the oldest type whereas asymmetric cryptography is only being used publicly since the late 1970’s1. Asymmetric cryptography was a major milestone in the search for a perfect encryption scheme. Secret key cryptography goes back to at least Egyptian times and is of concern here. It involves the use of only one key which is used for both encryption and decryption (hence the use of the term symmetric). Figure 2.1 depicts this idea. It is necessary for security purposes that the secret key never be revealed. Secret Key (K) Secret Key (K) ? ? - - - - Plaintext (P ) E{P,K} Ciphertext (C) D{C,K} Plaintext (P ) Figure 2.1: Secret key encryption. To accomplish encryption, most secret key algorithms use two main techniques known as substitution and permutation. Substitution is simply a mapping of one value to another whereas permutation is a reordering of the bit positions for each of the inputs. These techniques are used a number of times in iterations called rounds. Generally, the more rounds there are, the more secure the algorithm. A non-linearity is also introduced into the encryption so that decryption will be computationally infeasible2 without the secret key. This is achieved with the use of S-boxes which are basically non-linear substitution tables where either the output is smaller than the input or vice versa. 1It is claimed by some that government agencies knew about asymmetric cryptography before this. -

Thesis Submitted for the Degree of Doctor of Philosophy
Optimizations in Algebraic and Differential Cryptanalysis Theodosis Mourouzis Department of Computer Science University College London A thesis submitted for the degree of Doctor of Philosophy January 2015 Title of the Thesis: Optimizations in Algebraic and Differential Cryptanalysis Ph.D. student: Theodosis Mourouzis Department of Computer Science University College London Address: Gower Street, London, WC1E 6BT E-mail: [email protected] Supervisors: Nicolas T. Courtois Department of Computer Science University College London Address: Gower Street, London, WC1E 6BT E-mail: [email protected] Committee Members: 1. Reviewer 1: Professor Kenny Paterson 2. Reviewer 2: Dr Christophe Petit Day of the Defense: Signature from head of PhD committee: ii Declaration I herewith declare that I have produced this paper without the prohibited assistance of third parties and without making use of aids other than those specified; notions taken over directly or indirectly from other sources have been identified as such. This paper has not previously been presented in identical or similar form to any other English or foreign examination board. The following thesis work was written by Theodosis Mourouzis under the supervision of Dr Nicolas T. Courtois at University College London. Signature from the author: Abstract In this thesis, we study how to enhance current cryptanalytic techniques, especially in Differential Cryptanalysis (DC) and to some degree in Al- gebraic Cryptanalysis (AC), by considering and solving some underlying optimization problems based on the general structure of the algorithm. In the first part, we study techniques for optimizing arbitrary algebraic computations in the general non-commutative setting with respect to sev- eral metrics [42, 44]. -

Giza Plateau Mapping Project. Mark Lehner
GIZA PLATEAU MAPPING PROJECT GIZA PLATEAU MAPPING PROJECT Mark Lehner Ancient Egypt Research Associates (AERA) Season 2017: The Old and the New This year AERA team members busied themselves with the old and very new in research. I had the opportunity to return to some of my earliest work at the Sphinx, thanks to a grant from the American Research Center in Egypt (ARCE) Antiquities Endowment Fund (AEF) for the Sphinx Digital Database. This project will digitize, conserve, and make available as open source the archive from the 1979–1983 ARCE Sphinx Project, for which Dr. James Allen was project director and I was field director. My work at the Sphinx started three years earlier, in 1977, with Dr. Zahi Hawass, so that makes it exactly forty years ago.1 Search for Khufu We launched a new initiative, directed by Mohsen Kamel and Ali Witsell, to explore the older layers of the Heit el-Ghurab (“Wall of the Crow,” HeG) site. In some areas we have seen an older, different layout below what we have so far mapped, which dates to Khafre and Men- kaure. We believe that the older phase settlement and infrastructure, which was razed and rebuilt, served Khufu’s building of the Great Pyramid. The discovery in 2013, and publication this year, of the Journal of Merer2 piques our interest all the more in the early phase of Heit el-Ghurab. Pierre Tallet and a team from the Sorbonne and the French Institute in Cairo discovered the inscribed papyri at Wadi el-Jarf on the west- ern Red Sea Coast, in a port facility used only in the time of Khufu.