Installing PHP and Libraries
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Reflection, Zips, and Generalised Casts Abstract
Scrap More Boilerplate: Reflection, Zips, and Generalised Casts Ralf L a¨mmel Vrije Universiteit & CWI, Amsterdam Abstract Writing boilerplate code is a royal pain. Generic programming promises to alleviate this pain b y allowing the programmer to write a generic #recipe$ for boilerplate code, and use that recipe in many places. In earlier work we introduced the #Scrap y our boilerplate$ approach to generic p rogramming, which exploits Haskell%s exist- ing type-class mechanism to support generic transformations and queries. This paper completes the picture. We add a few extra #introspec- tive$ or #reflective$ facilities, that together support a r ich variety of serialisation and de-serialisation. We also show how to perform generic #zips$, which at first appear to be somewhat tricky in our framework. Lastly, we generalise the ability to over-ride a generic function with a type-specific one. All of this can be supported in Haskell with independently-useful extensions: higher-rank types and type-safe cast. The GHC imple- mentation of Haskell readily derives the required type classes for user-defined data types. Categories and Subject Descriptors D.2. 13 [Software Engineering]: Reusable Software; D.1.1 [Programming Techniques]: Functional Programming; D.3. 1 [Programming Languages]: Formal Definitions and Theory General Terms Design, Languages Keywords Generic p rogramming, reflection, zippers, type cast 1 Introduction It is common to find that large slabs of a program consist of #boil- erplate$ code, which conceals b y its b ulk a smaller amount of #in- teresting$ code. So-called generic p rogramming techniques allow Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for profit or c ommercial advantage and that copies b ear this notice and the full citation on the first page. -

Why ODF?” - the Importance of Opendocument Format for Governments
“Why ODF?” - The Importance of OpenDocument Format for Governments Documents are the life blood of modern governments and their citizens. Governments use documents to capture knowledge, store critical information, coordinate activities, measure results, and communicate across departments and with businesses and citizens. Increasingly documents are moving from paper to electronic form. To adapt to ever-changing technology and business processes, governments need assurance that they can access, retrieve and use critical records, now and in the future. OpenDocument Format (ODF) addresses these issues by standardizing file formats to give governments true control over their documents. Governments using applications that support ODF gain increased efficiencies, more flexibility and greater technology choice, leading to enhanced capability to communicate with and serve the public. ODF is the ISO Approved International Open Standard for File Formats ODF is the only open standard for office applications, and it is completely vendor neutral. Developed through a transparent, multi-vendor/multi-stakeholder process at OASIS (Organization for the Advancement of Structured Information Standards), it is an open, XML- based document file format for displaying, storing and editing office documents, such as spreadsheets, charts, and presentations. It is available for implementation and use free from any licensing, royalty payments, or other restrictions. In May 2006, it was approved unanimously as an International Organization for Standardization (ISO) and International Electrotechnical Commission (IEC) standard. Governments and Businesses are Embracing ODF The promotion and usage of ODF is growing rapidly, demonstrating the global need for control and choice in document applications. For example, many enlightened governments across the globe are making policy decisions to move to ODF. -

Template Meta-Programming for Haskell
Template Meta-programming for Haskell Tim Sheard Simon Peyton Jones OGI School of Science & Engineering Microsoft Research Ltd Oregon Health & Science University [email protected] [email protected] Abstract C++, albeit imperfectly... [It is] obvious to functional programmers what the committee did not realize until We propose a new extension to the purely functional programming later: [C++] templates are a functional language evalu- language Haskell that supports compile-time meta-programming. ated at compile time...” [12]. The purpose of the system is to support the algorithmic construction of programs at compile-time. Robinson’s provocative paper identifies C++ templates as a ma- The ability to generate code at compile time allows the program- jor, albeit accidental, success of the C++ language design. De- mer to implement such features as polytypic programs, macro-like spite the extremely baroque nature of template meta-programming, expansion, user directed optimization (such as inlining), and the templates are used in fascinating ways that extend beyond the generation of supporting data structures and functions from exist- wildest dreams of the language designers [1]. Perhaps surprisingly, ing data structures and functions. in view of the fact that templates are functional programs, func- tional programmers have been slow to capitalize on C++’s success; Our design is being implemented in the Glasgow Haskell Compiler, while there has been a recent flurry of work on run-time meta- ghc. programming, much less has been done on compile-time meta- This version is very slightly modified from the Haskell Workshop programming. The Scheme community is a notable exception, as 2002 publication; a couple of typographical errors are fixed in Fig- we discuss in Section 10. -

ELASTIC SEARCH – MAGENTO 2 COPYRIGHT 2018 MAGEDELIGHT.COM Page 2 of 6
Elasticsearch - Magento 2 INSTALLATION GUIDE MAGEDELIGHT.COM Installation: Before installing the extension, please make below notes complete: Backup your web directory and store database. Elasticsearch – M2 Installation: Install elasticsearch on your webserver, here is the reference link http://blog.magedelight.com/how-to- install-elasticsearch-on-centos-7-ubuntu-14-10-linux-mint-17-1/ Unzip the extension package file into the root folder of your Magento 2 installation. Install elastic search library o Back up your current composer.json cp composer.json composer.json.bk o Edit composer.json file and add below code to required clause. “elasticsearch/elasticsearch” : “~5.0” o Update dependencies composer update Connect to SSH console of your server: o Navigate to root folder of your Magento 2 setup o Run command php -f bin/magento module:enable Magedelight_Elasticsearch o Run command php -f bin/magento setup:upgrade o Run command php -f bin/magento setup:static-content:deploy Flush store cache; log out from the backend and log in again ELASTIC SEARCH – MAGENTO 2 COPYRIGHT 2018 MAGEDELIGHT.COM Page 2 of 6 License Activation: Note: This section is not applicable for extension purchased from Magento Marketplace How to activate the extension? Step 1: Go to Admin Control Panel >Stores > Configuration > Magedelight > Elasticsearch > License Configuration, you will see Serial Key and Activation key fields in License Configuration. Please enter the keys you received on purchase of the product and save configuration. Step 2: Expand “General Configuration” tab, you will find list of domains for which license is purchased and configured, now select the domain you are going to use, you can select multiple domain by clicking “Ctrl + Select”. -
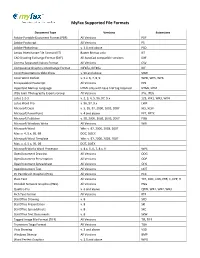
Supported File Types
MyFax Supported File Formats Document Type Versions Extensions Adobe Portable Document Format (PDF) All Versions PDF Adobe Postscript All Versions PS Adobe Photoshop v. 3.0 and above PSD Amiga Interchange File Format (IFF) Raster Bitmap only IFF CAD Drawing Exchange Format (DXF) All AutoCad compatible versions DXF Comma Separated Values Format All Versions CSV Compuserve Graphics Interchange Format GIF87a, GIF89a GIF Corel Presentations Slide Show v. 96 and above SHW Corel Word Perfect v. 5.x. 6, 7, 8, 9 WPD, WP5, WP6 Encapsulated Postscript All Versions EPS Hypertext Markup Language HTML only with base href tag required HTML, HTM JPEG Joint Photography Experts Group All Versions JPG, JPEG Lotus 1-2-3 v. 2, 3, 4, 5, 96, 97, 9.x 123, WK1, WK3, WK4 Lotus Word Pro v. 96, 97, 9.x LWP Microsoft Excel v. 5, 95, 97, 2000, 2003, 2007 XLS, XLSX Microsoft PowerPoint v. 4 and above PPT, PPTX Microsoft Publisher v. 98, 2000, 2002, 2003, 2007 PUB Microsoft Windows Write All Versions WRI Microsoft Word Win: v. 97, 2000, 2003, 2007 Mac: v. 4, 5.x, 95, 98 DOC, DOCX Microsoft Word Template Win: v. 97, 2000, 2003, 2007 Mac: v. 4, 5.x, 95, 98 DOT, DOTX Microsoft Works Word Processor v. 4.x, 5, 6, 7, 8.x, 9 WPS OpenDocument Drawing All Versions ODG OpenDocument Presentation All Versions ODP OpenDocument Spreadsheet All Versions ODS OpenDocument Text All Versions ODT PC Paintbrush Graphics (PCX) All Versions PCX Plain Text All Versions TXT, DOC, LOG, ERR, C, CPP, H Portable Network Graphics (PNG) All Versions PNG Quattro Pro v. -

File Operation Induced Unserialization Via the “Phar://” Stream Wrapper
File Operation Induced Unserialization via the “phar://” Stream Wrapper Sam Thomas - @_s_n_t Contents Introduction ............................................................................................................................................ 2 Stream Wrappers .................................................................................................................................... 3 Phar Archives and the "phar://" Stream Wrapper ................................................................................. 4 Basic Attack Methodology ...................................................................................................................... 5 Identifying File Path Handling Vulnerabilities ......................................................................................... 6 The Phar File Format ............................................................................................................................... 7 Exploiting Induced Unserialization.......................................................................................................... 9 PHPGGC / PHARGGC ............................................................................................................................. 10 Case Studies .......................................................................................................................................... 11 Typo 3 ............................................................................................................................................... -

PHP: Composer Orchestrating PHP Applications
PHP: Composer Orchestrating PHP Applications Dayle Rees This book is for sale at http://leanpub.com/composer-php This version was published on 2016-05-16 This is a Leanpub book. Leanpub empowers authors and publishers with the Lean Publishing process. Lean Publishing is the act of publishing an in-progress ebook using lightweight tools and many iterations to get reader feedback, pivot until you have the right book and build traction once you do. © 2016 Dayle Rees Tweet This Book! Please help Dayle Rees by spreading the word about this book on Twitter! The suggested tweet for this book is: I’m reading Composer: Orchestrating PHP Applications by @daylerees - https://leanpub.com/composer-php #composer The suggested hashtag for this book is #composer. Find out what other people are saying about the book by clicking on this link to search for this hashtag on Twitter: https://twitter.com/search?q=#composer Contents Acknowledgements ..................................... i Errata ............................................. ii Feedback ............................................ iii Translations ......................................... iv 1. Introduction ....................................... 1 2. Concept .......................................... 2 Dependency Management ............................... 2 Class Autoloading .................................... 3 Team Collaboration ................................... 3 3. Packages ......................................... 5 Application Packages .................................. 5 Dependency -

Metaprogramming Concepts of Programming Languages
Metaprogramming Concepts of Programming Languages Alexander Schramm Institut für Softwaretechnik und Programmiersprachen 2. November 2015 A. Schramm 2. November 2015 1/39 Table of Contents Introduction Runtime Reflection in Java Runtime Metaprogramming in Ruby C++ Templates Haskell Templates Lisp Macros Conclusion A. Schramm 2. November 2015 2/39 Outline Introduction Runtime Reflection in Java Runtime Metaprogramming in Ruby C++ Templates Haskell Templates Lisp Macros Conclusion A. Schramm 2. November 2015 3/39 Motivation Which issues do we want to tackle? I Avoid writing boilerplate code I Write code that shows our intention I Expand the syntax of languages I Write type independent code in strongly typed languages A. Schramm 2. November 2015 4/39 What is Metaprogramming Definition: Metaprogramming Metaprograming describes different ways to generate and manipulate code Differentations: I Compile time vs. runtime metaprogramming I Domain language vs. host language A. Schramm 2. November 2015 5/39 Differentations of Metaprograms Compile time Metaprogramming Ways to manipulate or generate code during compilation, e.g: Macros, Templates Runtime Metaprogramming Ways to manipulate or generate code, while it is executed, e.g: dynamic methods, Reflections A. Schramm 2. November 2015 6/39 Differentations of Metaprograms Domain Language The Programming Language, in which the metaprogram is written Host Language The Programming Language of the generated code I Can be different (YACC, Compilers) I Domain language can be a subset of the host language (C++ Templates) I Domain language can be an integral part of the host language (Ruby) A. Schramm 2. November 2015 7/39 Outline Introduction Runtime Reflection in Java Runtime Metaprogramming in Ruby C++ Templates Haskell Templates Lisp Macros Conclusion A. -

Developer Survey
Developer Survey Questions requiring a response are in r ed . Questions in which a response is NOT required are in blue. This survey is a critical element of the developers workshop. We are using it to capture nuts and bolts information about codes within the community so that we can assess the landscape before the workshop and use this information to drive the discussions. Please collaborate to provide only one submission per code and submit your response using the online survey: h ttps://ucdavis.co1.qualtrics.com/jfe/form/SV_57wtv4gpuaowTsh Basic Information Code identification 1. What is the name of the code? [small text box] 2. Who are the primary authors/maintainers? [medium text box] 3. URL of webpage for the code (if different than the version control repository) [small text box] 4. URL of version control repository (if public) [small text box] Software 1. Which license(s) do you use? Select all that apply. a. Apache license b. BSD license c. GNU General Public License d. GNU Lesser General Public License e. MIT license f. Mozilla Public License g. Common Development and Distribution License h. Eclipse Public License i. Other. Please specify [small text box] j. No license 2. What programming language(s) is your code currently written in? Select all that apply a. Fortran 77 b. Fortran 90 or later c. C d. C++ e. Go f. Python g. Julia h. Matlab i. Other. Please specify. [small text box] 3. List the primary (high-level) code dependencies (e.g., PETSc, deal.ii, FEniCS) [medium text box] 4. List any additional (low-level) code dependencies (e.g., MPI, NetCDF, HDF5) [medium text box] 5. -

Updating Systems and Adding Software in Oracle® Solaris 11.4
Updating Systems and Adding Software ® in Oracle Solaris 11.4 Part No: E60979 November 2020 Updating Systems and Adding Software in Oracle Solaris 11.4 Part No: E60979 Copyright © 2007, 2020, Oracle and/or its affiliates. License Restrictions Warranty/Consequential Damages Disclaimer This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. Warranty Disclaimer The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. Restricted Rights Notice If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, then the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs (including any operating system, integrated software, any programs embedded, installed or activated on delivered hardware, and modifications of such programs) and Oracle computer documentation or other Oracle data delivered to or accessed by U.S. Government end users are "commercial -

Today's Howtos Today's Howtos
Published on Tux Machines (http://www.tuxmachines.org) Home > content > today's howtos today's howtos By Roy Schestowitz Created 23/11/2020 - 3:13pm Submitted by Roy Schestowitz on Monday 23rd of November 2020 03:13:32 PM Filed under HowTos [1] An introduction to Prometheus metrics and performance monitoring | Enable Sysadmin[2] Use Prometheus to gather metrics into usable, actionable entries, giving you the data you need to manage alerts and performance information in your environment. Why does Wireshark say no interfaces found ? Linux Hint [3] Wireshark is a very famous, open-source network capturing and analyzing tool. While using Wireshark, we may face many common issues. One of the common issues is ?No Interfaces are listed in Wireshark?. Let?s understand the issue and find a solution in Linux OS.If you do not know Wireshark basic, then check Wireshark Basic first, then come back here. How to Solve ?Sub-process /usr/bin/dpkg returned an error code (1)? In Ubuntu[4] It?s not uncommon to run into an issue of broken packages in Ubuntu and other Debian-based distributions. Sometimes, when you upgrade the system or install a software package, you may encounter the ?Sub-process /usr/bin/dpkg returned an error code? error. For example, a while back, I tried to upgrade Ubuntu 18.04 and I bumped into the dpkg error as shown below. [...] This type of dpkg error points to an issue with the package installer usually caused by the interruption of an installation process or a corrupt dpkg database. Any of the above-mentioned solutions should fix this error. -

Foundation API Client Library PHP – Usage Examples By: Juergen Rolf Revision Version: 1.2
Foundation API Client Library PHP – Usage Examples By: Juergen Rolf Revision Version: 1.2 Revision Date: 2019-09-17 Company Unrestricted Foundation API Client Library PHP – Installation Guide Document Information Document Details File Name MDG Foundation API Client Library PHP - Usage Examples_v1_2 external.docx Contents Usage Examples and Tutorial introduction for the Foundation API Client Library - PHP Author Juergen Rolf Version 1.2 Date 2019-09-17 Intended Audience This document provides a few examples helping the reader to understand the necessary mechanisms to request data from the Market Data Gateway (MDG). The intended audience are application developers who want to get a feeling for the way they can request and receive data from the MDG. Revision History Revision Date Version Notes Author Status 2017-12-04 1.0 Initial Release J. Rolf Released 2018-03-27 1.1 Adjustments for external J. Rolf Released release 2019-09-17 1.2 Minor bugfixes J. Ockel Released References No. Document Version Date 1. Quick Start Guide - Market Data Gateway (MDG) 1.1 2018-03-27 APIs external 2. MDG Foundation API Client Library PHP – Installation 1.2 2019-09-17 Guide external Company Unrestricted Copyright © 2018 FactSet Digital Solutions GmbH. All rights reserved. Revision Version 1.2, Revision Date 2019-09-17, Author: Juergen Rolf www.factset.com | 2 Foundation API Client Library PHP – Installation Guide Table of Contents Document Information ............................................................................................................................