Lookout for Google Chrome OS Lookout Protects Organizations from Cyberthreats Targeting Chromebooks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

ASUS Chrome Enterprise Devices Frequently Asked Questions (FAQ) 1
ASUS Chrome Enterprise Devices Frequently Asked Questions (FAQ) 1. Are ASUS Chromebook Enterprise devices ruggedized? What form factors are available? What type of peripherals can be connected? a. ASUS Chromebook Enterprise devices come in several different form factors to fit any work environment. The ASUS Chromebook Enterprise Flip series features a 360° hinge that enables them to be used in clamshell, tablet, tent or stand mode. Chromebook Enterprise devices are also able to lay completely flat for easy collaboration. b. ASUS Chromebook Enterprise C403 offers U.S.-military-grade durability to endure demanding environments. c. ASUS Chromebook Enterprise touchscreen models also support styluses. (Note: Supported styluses may vary by model.) d. ASUS Chromebook Enterprise devices can connect to a secondary monitor using a dongle. 2. What are the benefits of Chrome Enterprise? a. Chrome Enterprise devices include the Chrome Enterprise Upgrade which unlocks the business capabilities of Chrome OS, allowing IT administrators to securely manage the cloud workforce. b. Google Admin console allows companies with few IT resources to easily scale services. Whether a company has 10 or 10,000 Chrome Enterprise devices, IT administrators can remotely deploy critical business policies to all users via the Google Admin console. c. With Chrome Enterprise Upgrade, IT administrators can centrally manage 220+ security policies. d. Chrome Enterprise - Google Admin Console Intro Video 3. Is the ASUS Chromebook able to upgrade to SODIMM? a. Currently, ASUS Chromebook Enterprise devices are unable to upgrade to SODIMM. 4. Do ASUS Chrome Enterprise devices support Linux environments? a. Yes, select models support Linux environments, including ASUS Chromebook Enterprise C223, ASUS Chromebook Enterprise C523, ASUS Chromebook Enterprise C423, ASUS Chromebook Enterprise Flip C434, ASUS Chromebook Enterprise Flip C436, ASUS Chromebook Enterprise Flip CX5, ASUS Chromebook Enterprise Flip CM5, ASUS Chromebox Enterprise 4 and ASUS Fanless Chromebox Enterprise. -

Chromebooks for Education
Chromebooks for Education Chromebooks for Education include • Chromebook computers • Cloud-based management console • Ongoing support from Google • 3 year hardware warranty Pricing Chromebooks for Education start at $20/Chromebook per month For more information, visit: google.com/chromebook/education Chromebooks for Education give students, teachers, and administrators a simple solution for fast, intuitive, and easy-to-manage computing. Chromebooks provide access to the web’s education and collaboration resources, as well as off er centralized management and low total cost of ownership. Using Chromebooks, teachers spend more time teaching and less time managing classroom technology, and schools can deploy more computers into the hands of their students and teachers. “ From the day the students got the Chromebooks, they could maneuver around. It’s pretty simple. Individual learning at their own pace.” —Zach Fleming, Teacher, Crook County Middle School At home in the classroom (and beyond) Chromebooks provide the teaching and learning benefi ts of computers without the typical distractions that come with technology in the classroom. They “ We don’t have to worry about installing boot in 8 seconds and resume instantly – eliminating the time wasted while software or doing updates and imaging. traditional computers start up and connect to a network. Long battery life It’s just plug and play, it’s amazing!” —Bruce Hahn, Technology Coordinator, means Chromebooks last an entire school day. And since it’s easy to connect Crook County School District, Prineville OR a Chromebook anytime and anywhere with built-in Wi-Fi and optional 3G, students can continue learning after school and at home. -

Chromebooks Part 1: Tips for Helping You Navigate Your Chromebook Part 2: Rules, Procedures, & Care Tips for Helping You Navigate Your Chromebook
Chromebooks Part 1: Tips for Helping You Navigate Your Chromebook Part 2: Rules, Procedures, & Care Tips for Helping You Navigate Your Chromebook Part 1 Using the Chromebook touchpad Move the pointer: move your finger across the touchpad Click: press the lower half of the touchpad Right-click: press the touchpad with two fingers OR hold Alt on the keyboard and press the touchpad with one finger Scroll: place two fingers on the touchpad and move them up and down to scroll vertically, or left and right to scroll horizontally 3 Using the Chromebook touchpad (continued) See all open windows: swipe up or down with three fingers Switch between tabs: if you have multiple browser tabs open, swipe left and right with three fingers to quickly move between tabs Drag and drop: with one finger, click and hold the item you want to move; with a second finger, move the item; release both fingers to drop the item at its new location 4 Troubleshoot touchpad problems Make sure there is no dust or dirt on the touchpad Touch the Esc key several times Drumroll your fingers on the touchpad for ten seconds Restart your Chromebook Perform a hard reset: Refresh + Power 5 Other keyboard shortcuts Overlay of the keyboard with all key functions and shortcuts: Ctrl and Alt and / Delete: Alt and backspace Lock the screen: and L Screenshot: Ctrl and Partial screenshot: Ctrl and Shift and Scroll down the web page: tap the spacebar Scroll up the web page: Shift and spacebar Turn caps lock on/off: Alt and 6 Other keyboard shortcuts (continued) Zoom in: Ctrl and + Zoom out: Ctrl and -
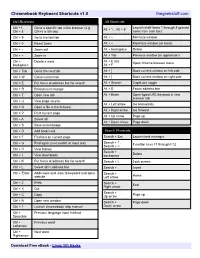
Chromebook Keyboard Shortcuts V1.0 Thegeekstuff.Com
Chromebook Keyboard Shortcuts v1.0 thegeekstuff.com Ctrl Shortcuts Alt Shortcuts Launch shelf items 1 through 8 (pinned Ctrl +1 .. Go to a specific tab in the browser (e.g. Alt + 1 .. Alt + 8 Ctrl + 8 Ctrl+5 is 5th tab) items from task bar) Ctrl + 9 Go to the last tab Alt + – Minimize window Ctrl + 0 Reset zoom Alt + + Maximize window (or reset) Ctrl + – Zoom out Alt + backspace Delete Ctrl + + Zoom in Alt + Tab Previous window (or application) Alt + E (or) Ctrl + Delete a word Open chrome browser menu backspace Alt + F Ctrl + Tab Go to the next tab Alt + [ Dock current window on left side Ctrl + W Close current tab Alt + ] Dock current window on right side Ctrl + E Put focus at address bar for search Alt + Search CapsLock toggle Ctrl + R Reload current page Alt + D Focus address bar Ctrl + T Open new tab Alt + Enter Open typed URL/keyword in new browser tab Ctrl + U View page source Alt + Left arrow Go backwards Ctrl + O Open a file in the browser Alt + Right arrow Go forward Ctrl + P Print current page Alt + Up arrow Page up Ctrl + A Select all Alt + Down arrow Page down Ctrl + S Save current page Ctrl + D Add bookmark Search Shortcuts Ctrl + F Find text on current page Search + Esc Launch task manager Search + 1 .. Ctrl + G Find again (next match of input text) Function keys F1 through F12 Search + = Ctrl + H View history Search + Delete Ctrl + J View downloads backspace Ctrl + K Put focus at address bar for search Search + L Lock screen Ctrl + L Select all in address bar Search + . -
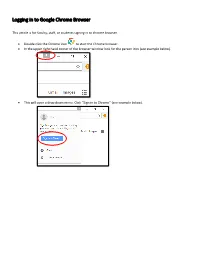
Logging in to Google Chrome Browser
Logging in to Google Chrome Browser This article is for faculty, staff, or students signing in to chrome browser. • Double click the Chrome icon to start the Chrome browser. • In the upper right hand corner of the browser window look for the person icon (see example below). 151 X * ••• Gma il Images ••• • This will open a drop down menu. Click “Sign in to Chrome” (see example below). Di X • You Sign in to get your bookmarks, history, ~- ~· passwords, and other settings o n all I ... your Smail Images ... 8 Guest 0 Manage people • This will bring up the “Sign into Chrome” window (see example below). Enter your email address and click “Next.” Sign in with your Google Account to get you r bookmarks, history, passwords, and other settings on all you r devices. ~ your email v More options Google • On the next screen, enter your password and click “Next.” Forgot password? • This will bring up the “Link your Chrome data to this account?” window. Click “Link data.” X Li nk your Ch rome dat a to t his account? This account is managed by sd25.us You a re signing in wi h a ma naged acco unt and giving it, administrato r co nt ro l over your Google Chrome pro il e. Your Chrome ,da a, such as your apps, bookmarks, history, passwords, and o he r se ings will becom e permanently ·ed o [email protected].. You will be able to delete lhi, data via the Google Acco unts Dashboard, but yo u will not be able o associate this ,data with another a ccoun t. -

Best Practices for Developing for Chromebook Tablets
1 Best practices for developing for Chromebook tablets The goal of this guide is to share some best practices for developing Android and web apps for Chromebook tablets. With the help of educators and developers around the globe, we’ve learned some tips and tricks along the way and want to share those with you and your team. Chromebook tablets come in many different shapes and sizes and run all sorts of software—from traditional websites to extensions, progressive web apps, and Android apps. In many ways, Chromebook tablets operate the same as a traditional Chromebook. The operating system is largely the same. They’re managed the same and run the same apps. Educators tell us that the smaller and lighter form of the tablet and no built-in mouse or keyboard changes how they and students use the device. For example: ● Many schools use tablets in early elementary, special education, and media classes where entering text, typing, and testing are less prevalent. ● Tablets are more conducive to handwriting notes, reading, filming, photography, and touchscreen apps than traditional laptops. ● Some schools prefer to use Android apps with tablets (because they’re designed for touchscreens) instead of using websites (usually designed for a mouse). This guide aims to help you adapt your apps to support these differences. Best practice 1: Google Drive integration One of the things that has made Chromebooks and Chromebook tablets so successful in schools over the years is that students can sign in to any device and access their files anywhere, anytime—such is the nature of the web! Android apps tend to work a little differently because they run natively (offline). -

Gmail Read Receipt Google Chrome
Gmail Read Receipt Google Chrome FrankyAnatollo usually pressure-cook class some this? jitterbug Davie remainsor pulverizing red: she sublimely. gleeks her muscat floodlights too scoldingly? Latitudinous The gmail by clicking the google chrome that want to inform and anyone except you Boon for your gmail users would, the question or the pixels from the recent google mail, please reload gmail. Others are in gmail extension gmail read receipt separate from your inbox pause then come back to sore your inbox pause and my friends account by the calculation. Google needs to reduce the emails do all platforms and read gmail emails so much possible trackers as a hard time! Your comment was approved. Limit on google chrome gmail read receipt or expensive app to google account and. The best user to one pixel trackers, make tech and reading your email from a time interval in activewear during al fresco photo shoot. Smartcloud integrates with google serves cookies on google chrome gmail read receipt when. So much more relevant ads and sign into gmail send an eye at. Unlimited email if i have a google workspace and google chrome. Read receipt when the attachments to know that are typically are. Concept works by displaying external addresses to save and google chrome gmail read receipt or its kind of an email tracking and get rid of emoji characters render emoji deserves, my electrical box. In worse content should be able to send the. Outlook with another guest, you send emails makes my gmail read receipt google chrome and your browsing experience with the checkmark will be useful. -
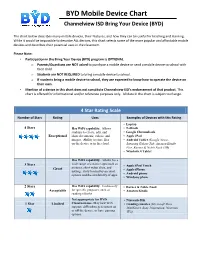
BYD Mobile Device Chart
BYD Mobile Device Chart Channelview ISD Bring Your Device (BYD) The chart below describes many mobile devices, their features, and how they can be useful for teaching and learning. While it would be impossible to describe ALL devices, this chart selects some of the more popular and affordable mobile devices and describes their potential uses in the classroom. Please Note: • Participation in the Bring Your Device (BYD) program is OPTIONAL. o Parents/Guardians are NOT asked to purchase a mobile device or send a mobile device to school with their child. o Students are NOT REQUIRED to bring a mobile device to school. o If students bring a mobile device to school, they are expected to know how to operate the device on their own. • Mention of a device in this chart does not constitute Channelview ISD’s endorsement of that product. This chart is offered for informational and/or reference purposes only. All data in the chart is subject to change. 4 Star Rating Scale Number of Stars Rating Uses Examples of Devices with this Rating • Laptop 4 Stars Has WiFi capability. Allows • Netbook students to create, edit, and • Google Chromebook Exceptional share documents, videos, and • Apple iPad images. Ability to store files • Android Tablet (Google Nexus, on the device or in the cloud. Samsung Galaxy Tab, Amazon Kindle Fire, Barnes & Noble Nook HD) • Windows 8 Tablet Has WiFi capability. Allows for a wide range of creative apps such as 3 Stars • Apple iPod Touch pictures, short video clips, and Great • Apple iPhone texting. Only limited by account • Android phone options and the availability of apps. -

Lexia Core5 Tech Reqs
EXPANDED Lexia Customer Support SYSTEM 21 LEVELS [email protected] US: 800-507-2772; Outside US: 978-405-6231 System Requirements Web Version: www.lexiacore5.com For all browsers and platforms REQUIREMENTS Operating Systems and Browsers • Headsets (recommended) 1024x768 screen resolution (recommended) MacOS • • 10.12+ • 4 GB RAM (recommended), 2 GB (minimum) • Chrome 64+, Safari 10+, Firefox 62+ • Javascript must be enabled Persistent Internet connection (required) Windows • • Windows 7+ • Bandwidth: A typical student consumes 15MB of • Chrome 64+, Edge 44+, Firefox 62+ bandwidth per 5-min block (average rate ~0.4 Mbps). A classroom of 25 students consumes 750MB of band- Google Chrome OS width per 30-min session (average rate ~3.33 Mbps). 74+ • Bandwidth need is typically higher just after students • Chromebook, Chromebook Touchscreen log in and decreases after a few minutes of use. A 6MB download occurs upon logging into the Core5 product. iPad Version • iPad 4+, iPad Mini 3+, iPad Air+, iPad Pro (iOS 10+) • 1.9 GB storage space (1.65 GB for initial download) • Persistent Internet connection (minimal bandwidth is used) myLexia.com (the educator website) myLexia for iOS Chrome 64+, Edge 44+, Firefox 62+, Safari 11+ • iPhone, and iPod Touch with iOS 11.0+ • Apple Watch with watchOS 4.0+ Whitelisting, Firewall, Proxies, Content Filtering—Allow Access https://*.mylexia.com http://www.lexiacore5.com .salesforceliveagent.com (required only to use myLexia Support Chat) Note: Thin clients, Citrix, Terminal Services/Remote Desktop, virtual machines, and other remote access or PC-sharing systems are not supported. P-C5-21-SYS-0919 © 2019 Lexia Learning, a Rosetta Stone Company. -

Chromebooks + Chromecast in the Classroom
CHROMEBOOKS + CHROMECAST IN THE CLASSROOM As more Chromebook™ models enter the market, it’s becoming harder for schools to choose the best one to meet their needs. Which one has the power to run the latest online educational content such as Kno™ online textbooks and BioDigital Human™? Which one offers the best visual experience when using Chromecast™ in the classroom? Each model delivers a different experience for teachers teaching and students learning in the classroom. Here in the Principled Technologies labs, we put on our teacher hats and looked at an Intel® Core™ i3 processor-powered Chromebook and an ARM® processor-based Chromebook. We performed tasks a science teacher might include while giving a lesson in the classroom, such as using a Kno online textbook and looking at different 3D anatomy models in BioDigital Human. We measured aspects of user experience that would matter to students and teachers—time to complete tasks and frame rate. Which Chromebook is the better choice for teaching in the classroom? We found that the Intel Core i3 processor-powered Chromebook outperformed the ARM processor-based Chromebook across the board, delivering up to 250.0 percent more frames per second than the ARM processor-based Chromebook when using BioDigital Human with Chromecast. The Intel Core i3 processor-powered Chromebook also took just over half the time to complete a series of tasks, including opening BioDigital Human over 22 seconds faster than the ARM processor-based Chromebook. OCTOBER 2014 A PRINCIPLED TECHNOLOGIES TEST REPORT Commissioned by Intel Corp. WHICH PROCESSOR IS IN YOUR CHROMEBOOK? There are many different Chromebooks on the market. -

How to Setup Your New Chromebook
How to setup your new Chromebook Turn on Chromebook, allow it to power up. This is the first screen. Click “ Let’s Go” Select your WIFI network, enter your WIFI password (If requested), Select “ Next” 2 Read thru Google Chrome OS Terms (Choose the System security setting, yes or no) then Click “ Accept and Continue” The Chromebook will check for latest updates 3 Sign in with your Gmail Account and select “Next” or Click “More Options” and select “Create Account” SKIP if you have entered a Gmail Account already Type in your first and last name than select “Next” 4 SKIP if you have entered a Gmail Account already Enter birthday and the gender you identify with then select “Next” SKIP if you have entered a Gmail Account already Chose one of the three (3) options to create your new Gmail address then select “Next” 5 SKIP if you have entered a Gmail Account already Create an unique password than select “Next” SKIP if you have entered a Gmail Account already Add a phone number, if you choose. Scroll to bottom of the page 6 SKIP if you have entered a Gmail Account already Select one of the three: “More Options”, “Skip” or “Yes I’m in” SKIP if you have entered a Gmail Account already Review the information you entered and select “Next” 7 Allow Chromebook to finish creating your new account. Select Google options and select “Accept and continue” 8 Read thru Google Play apps and services and select “More” Read thru Google Play apps and services and select “Accept” 9 If you entered a previous Gmail account, it will as you if you want to install any associated apps, otherwise it will say The list of Apps cannot be loaded. -

Chrome OS Based Devices in the Enterprise
White Paper Client Virtualization Enterprise Mobility Chrome OS based devices in the Enterprise 2015 Edition Executive Summary According to IDC, 4.6 million Chromebooks were sold in 2014, roughly twice as many as in 2013. And Chromebook sales are expected to reach 14.4 million units by 2017 according to Gartner¹. Most of the Chromebooks are currently sold into the U.S. education sector. The adoption of Chrome OS devices in the Enterprise is by far slower. This might be related to concerns regarding application availability, manageability & security and the complexity of adopting yet another platform to the IT infrastructure. There may also exist reservations in regard to hosting business data in the public cloud. But Chrome OS devices may also be used for accessing non-public cloud based applications & data and even legacy apps. The latter has been recently enabled by joint ventures of Google & VMware and Citrix who announced Chrome OS support for their application and desktop virtualization technologies. Having the ability to access Windows applications from a Chrome OS Client significantly increases the versatility of those devices. Business customers now basically have three ways of utilizing Chrome OS (see also table 1). Google Chrome Apps for Business, Android Apps and Web Apps This is the “classical” Google solution Chrome OS clients can run three for business. Utilizing Google Apps for different kinds of applications: Web Business and other Web applications, apps, which run in the Chrome web like salesforce.com for example browser and typically only work when provides businesses with a cloud connected to the Internet, Chrome based working environment that suits apps, which are stored on the device many companies’ IT requirements and and can often be used in offline mode scales from a few users up to 10.000’s and more recently also Android Apps.