Novell Access Manager 3.1 SP3 Installation Guide Contents
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Mac OS X Includes Built-In FTP Support, Easily Controlled Within a fifteen-Mile Drive of One-Third of the US Population
Cover 8.12 / December 2002 ATPM Volume 8, Number 12 About This Particular Macintosh: About the personal computing experience™ ATPM 8.12 / December 2002 1 Cover Cover Art Robert Madill Copyright © 2002 by Grant Osborne1 Belinda Wagner We need new cover art each month. Write to us!2 Edward Goss Tom Iov ino Editorial Staff Daniel Chvatik Publisher/Editor-in-Chief Michael Tsai Contributors Managing Editor Vacant Associate Editor/Reviews Paul Fatula Eric Blair Copy Editors Raena Armitage Ya n i v E i d e l s t e i n Johann Campbell Paul Fatula Ellyn Ritterskamp Mike Flanagan Brooke Smith Matt Johnson Vacant Matthew Glidden Web E ditor Lee Bennett Chris Lawson Publicity Manager Vacant Robert Paul Leitao Webmaster Michael Tsai Robert C. Lewis Beta Testers The Staff Kirk McElhearn Grant Osborne Contributing Editors Ellyn Ritterskamp Sylvester Roque How To Ken Gruberman Charles Ross Charles Ross Gregory Tetrault Vacant Michael Tsai Interviews Vacant David Zatz Legacy Corner Chris Lawson Macintosh users like you Music David Ozab Networking Matthew Glidden Subscriptions Opinion Ellyn Ritterskamp Sign up for free subscriptions using the Mike Shields Web form3 or by e-mail4. Vacant Reviews Eric Blair Where to Find ATPM Kirk McElhearn Online and downloadable issues are Brooke Smith available at http://www.atpm.com. Gregory Tetrault Christopher Turner Chinese translations are available Vacant at http://www.maczin.com. Shareware Robert C. Lewis Technic a l Evan Trent ATPM is a product of ATPM, Inc. Welcome Robert Paul Leitao © 1995–2002, All Rights Reserved Kim Peacock ISSN: 1093-2909 Artwork & Design Production Tools Graphics Director Grant Osborne Acrobat Graphic Design Consultant Jamal Ghandour AppleScript Layout and Design Michael Tsai BBEdit Cartoonist Matt Johnson CVL Blue Apple Icon Designs Mark Robinson CVS Other Art RD Novo DropDMG FileMaker Pro Emeritus FrameMaker+SGML RD Novo iCab 1. -

Bleach Documentation Release 3.0.1 20181009
Bleach Documentation Release 3.0.1 20181009 Will Kahn-Greene Oct 09, 2018 Contents 1 Reporting Bugs 3 2 Security 5 3 Installing Bleach 7 4 Upgrading Bleach 9 5 Basic use 11 6 Code of conduct 13 7 Contents 15 7.1 Sanitizing text fragments......................................... 15 7.2 Linkifying text fragments........................................ 23 7.3 Goals of Bleach............................................. 29 7.4 Bleach development........................................... 32 7.5 Bleach changes.............................................. 34 8 Indices and tables 43 i ii Bleach Documentation, Release 3.0.1 20181009 Bleach is an allowed-list-based HTML sanitizing library that escapes or strips markup and attributes. Bleach can also linkify text safely, applying filters that Django’s urlize filter cannot, and optionally setting rel attributes, even on links already in the text. Bleach is intended for sanitizing text from untrusted sources. If you find yourself jumping through hoops to allow your site administrators to do lots of things, you’re probably outside the use cases. Either trust those users, or don’t. Because it relies on html5lib, Bleach is as good as modern browsers at dealing with weird, quirky HTML fragments. And any of Bleach’s methods will fix unbalanced or mis-nested tags. The version on GitHub is the most up-to-date and contains the latest bug fixes. You can find full documentation on ReadTheDocs. Code https://github.com/mozilla/bleach Documentation https://bleach.readthedocs.io/ Issue tracker https://github.com/mozilla/bleach/issues IRC #bleach on irc.mozilla.org License Apache License v2; see LICENSE file Contents 1 Bleach Documentation, Release 3.0.1 20181009 2 Contents CHAPTER 1 Reporting Bugs For regular bugs, please report them in our issue tracker. -

Diplomarbeit Kalenderstandards Im Internet
Diplomarbeit Kalenderstandards im Internet Eingereicht von Reinhard Fischer Studienkennzahl J151 Matrikelnummer: 9852961 Diplomarbeit am Institut für Informationswirtschaft WIRTSCHAFTSUNIVERSITÄT WIEN Studienrichtung: Betriebswirtschaft Begutachter: Prof. DDr. Arno Scharl Betreuender Assistent: Dipl.-Ing. Mag. Dr. Albert Weichselbraun Wien, 20. August 2007 ii Inhaltsverzeichnis Abbildungsverzeichnis vi Abkürzungsverzeichnis vii 1 Einleitung 1 1.1 Problemstellung . 1 1.2 Inhalt und Vorgehensweise . 3 2 Standards für Kalender im Internet 5 2.1 iCalendar und darauf basierende Standards . 6 2.1.1 iCalendar und vCalendar . 6 2.1.2 Transport-Independent Interoperability Protocol (iTIP) . 8 2.1.3 iCalendar Message-Based Interoperability Protocol (iMIP) . 8 2.1.4 iCalendar über WebDAV (WebCAL) . 10 2.1.5 Storage of Groupware Objects in WebDAV (GroupDAV) . 11 2.1.6 Calendaring and Scheduling Extensions to WebDAV (CalDAV) . 12 2.1.7 IETF Calendar Access Protocol (CAP) . 13 2.2 XML-basierte Formate . 15 2.2.1 XML iCalendar (xCal) . 15 2.2.2 RDF Calendar (RDFiCal) . 16 2.2.3 RDFa (RDF/A) . 16 2.2.4 OWL-Time . 17 2.3 Mikroformate (hCalendar) . 18 2.4 SyncML . 20 2.5 Weitere Formate . 21 2.6 Zusammenfassung . 22 iii 3 Offene Kalenderanwendungen im Internet 24 3.1 Server . 24 3.1.1 Citadel/UX . 24 3.1.2 Open-Xchange . 26 3.1.3 OpenGroupware.org . 26 3.1.4 Kolab2 . 27 3.1.5 Weitere Server . 28 3.2 Clients . 29 3.2.1 Mozilla Calendar Project . 29 3.2.2 KDE Kontact . 30 3.2.3 Novell Evolution . 30 3.2.4 OSAF Chandler . 31 3.2.5 Weitere Open-Source- und Closed-Source-Clients . -

Relevé Des Frais Annuels De L'entente De Licence Destinée À L
Relevé des frais annuels de l’entente de licence destinée à l’enseignement postsecondaire AOÛT 2016 Les Informations de Programme scolaire Relient Les Instructions de Sélection de produit : As part of the compliance and annual order process, this worksheet must be sent to [email protected] (for Europe, Middle East, Africa) or [email protected] (rest of world). Sélectionnez un seul modèle : ___ Modèle ETP; ___ Modèle par poste de travail; ___ Modèle par poste de travail de service EMBALLER CALCUL INSTRUCTIONS : A. Place une marque dans le Modèle de colonne A Choisi la boîte des produits que vous souhaitez acheter OU choisir un Paquet de Valeur. Si un Paquet de Valeur n'est pas choisi, au moins quatre (4) les produits doivent être choisis. B. Calcule le Total A Emballé le Prix (TBP) en ajoutant les prix appropriés des produits choisis et le modèle d'évaluation approprié. C. Le Total A Emballé le Prix sera utilisé pour calculer les Frais annuels. Vous ne pouvez pas utiliser le modèle de FTE dans calculer vos Frais annuels à moins que votre population de FTE dépasse votre compte de poste de travail. POUR EMPECHER DES RETARDS DANS TRAITER VOTRE ORDRE DE RENOUVELLEMENT, S'IL VOUS PLAIT SOUMETTRE VOTRE FACTURE D'ACHAT ET VOTRE FEUILLE DE TRAVAIL COMPLETEE ENSEMBLE MOBILE DEVICE LICENSE: Upon purchase of a license for Novell ZENworks Mobile Management, the following terms become part of Your ALA. To acquire a Mobile Device License, You must purchase a license for each Mobile Device. To acquire a FTE license, you must purchase a license for all FTE. -

CHAPTER 15 Accessing Online Calendars and Event Aggregators
CHAPTER 15 Accessing Online Calendars and Event Aggregators Online calendars will move from being merely trendy to virtually indispensable as our lives move increasingly to the network. Calendaring (scheduling appointments and coordinating calendars) is something most of us can relate to since we all have appointments that we make and keep. As we use electronic calendars, there is a good chance that we will have more than one calendar to synchronize—people use different calendars or work with people with other calendars, no matter how much Microsoft, Apple, Google, or Yahoo! might want everyone to use its calendar alone. A lot of this calendaring activity has moved to not only digital form but specifically to a networked digital form. In addition to the old calendars, new generations of online calendars are coming into existence—that’s the focus of this chapter. Online calendars exist in the context of other digital calendars: desktop calendars such as Microsoft Outlook and Apple iCal and calendars on handheld devices such as the Palm calendar. Much work has been done on synchronizing these calendars. Of course, calendar synchronization has been operant for a while, but these approaches (specialized conduits/SyncML1) have been more opaque than the APIs now available.2 Today’s online calendars with APIs generally make synchronization easier. In addition to the proliferation of online calendars, event aggregation sites such as Upcoming.yahoo.com and Eventful.com are starting to create a marketplace of event data. They are focused on public events, whereas online calendars have as their focal point individuals and private events. -
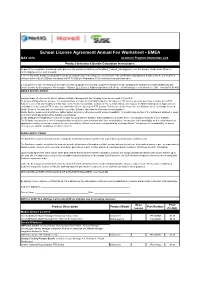
School License Agreement Annual Fee Worksheet - EMEA MAY 2016 Academic Program Information Link Product Selection & Bundle Calculation Instructions
School License Agreement Annual Fee Worksheet - EMEA MAY 2016 Academic Program Information Link Product Selection & Bundle Calculation Instructions: As part of the compliance and annual order process, this worksheet must be sent to [email protected] (for Europe, Middle East, Africa) or [email protected] (rest of world). 1. Select any of the bundles or products below by checking the box in the Model Selected column. Any combination of products or bundles may be selected for a minimum price of $2.36 USD per enrollment or $35.70 USD per Workstation. $1000 minimum total purchase price. 2. Compute the Total Price based on the total cost of the products selected and compute the Annual Fee by multiplying the total Enrollment/Workstation/Mobile Device number by the total price. For example: 1 Bundle @ 2.25 plus 2 Additional products ($0.60 ea) = $3.45 total price x enrollment of 1,000 = Annual Fee $3,450. MOBILE DEVICE LICENSE: Upon purchase of a license for Novell ZENworks Mobile Management, the following terms become part of Your SLA. To acquire a Mobile Device License, You must purchase a license for each Mobile Device. To acquire a FTE license, you must purchase a license for all FTE. Subject to the terms and conditions of this Agreement, the license purchase authorizes You to install and use one copy of the Mobile Management Application on each Mobile Device (for an FTE license, for each Mobile Device used by an FTE person). This license allows You to use the Software solely to manage licensed Mobile Devices. You may not use or allow the use of the Software other than for Your own internal purposes. -

Calendar Subscription Upgrades
Table of Contents ▲ Workgroup: Network Working Group Internet-Draft: draft-ietf-calext-subscription-upgrade-02 : Updates: 5988 (if approved) Published: 29 July 2020 Intended Status: Standards Track Expires: 30 January 2021 Author: M. Douglass Calendar subscription upgrades Abstract This specification updates [RFC5545] to add the value DELETED to the STATUS property. This specification also updates [RFC7240] to add the subscribe- enhanced-get and limit preferences. Status of This Memo This Internet-Draft is submitted in full conformance with the provisions of BCP 78 and BCP 79. Internet-Drafts are working documents of the Internet Engineering Task Force (IETF). Note that other groups may also distribute working documents as Internet-Drafts. The list of current Internet-Drafts is at https://datatracker.ietf.org/drafts/current/. Internet-Drafts are draft documents valid for a maximum of six months and may be updated, replaced, or obsoleted by other documents at any time. It is inappropriate to use Internet- Drafts as reference material or to cite them other than as "work in progress." This Internet-Draft will expire on 30 January 2021. Copyright Notice Copyright (c) 2020 IETF Trust and the persons identified as the document authors. All rights reserved. This document is subject to BCP 78 and the IETF Trust's Legal Provisions Relating to IETF Documents (https://trustee.ietf.org/license-info) in effect on the date of publication of this document. Please review these documents carefully, as they describe your rights and restrictions with respect to this document. Code Components extracted from this document must include Simplified BSD License text as described in Section 4.e of the Trust Legal Provisions and are provided without warranty as described in the Simplified BSD License. -

Server Baseline Document: Jan 1, 2016
Server Baseline Document: Jan 1, 2016 Major Patches Published Through Jan 1, 2016 Our Baseline Document is a compilation of patches that are considered stable and production ready for the current business quarter. This list outlines the major products which fit into our core expertise, primarily in the Data Center. We generally perform a quarterly Baseline process for all of our customers, and ensure that all the updates listed here are applied and functional. This accomplishes the following: • Implements bug fixes and other defects • Resolves known security vulnerabilities • May include feature enhancements • Keeps systems up to date and easier to support • Ensure support from vendor if issues arise The following tables outline the baselines for the major products within our core area of expertise. Red = Recent Patches; Gray = Obsolete Product / End of Life Marvin Huffaker Consulting, Inc. Published Jan 1, 2016 http://www.redjuju.com Phone: 480-988-7215 Server Operating Systems Patch Build/Kernel Release Date SUSE Linux Enterprise Server 12 (SLES 12) SLES 12 SP1 3.12.51-52.31 July 16, 2015 SLES Kernel Updates: 3.12.51-60.20.2 Dec 17, 2015 SUSE Linux Enterprise Server 11 (SLES 11) SLES 11 SP4 3.0.101-63.1 July 2015 SLES Kernel Updates: 3.0.101-68.1 Dec 22, 2015 Novell Open Enterprise Server 2015 SLES 11 SP3 + OES 2015 3.0.76-0.11 July 8, 2013 + Sept 14, 2015 SLES Kernel Updates: 3.0.101-0.47.71 Nov 26, 2015 OES Updates: Update 10858 Nov 30, 2015 Novell Open Enterprise Server 11 (OES 11) SLES 11 SP3 + OES 11 SP2 3.0.76-0.11 July 8, 2013 -

SEP Sesam Vs. Commvault Simpana Product Comparison SEP Sesam Vs
SEP sesam vs. CommVault Simpana Product Comparison SEP sesam vs. CommVault Simpana Product Comparison SEP sesam Overview The modern enterprise has data requirements covering a broad range of use cases. From physical servers in the data center to virtual servers hosted in a private or public cloud, data needs are growing at an unprecedented rate. Enterprises that, a decade ago, had overall data needs in the terabyte range are now looking at storage requirements that may be hundreds or even thousands of times as large. The laws of supply and demand apply directly to data growth in the enterprise. Storage is in ever-increasing supply, with larger and cheaper devices appearing on the market every day. Correspondingly, the enterprise demand for that storage is growing exponentially as well. With e-mail, corporate databases, shared documents, and regulatory compliance requirements, organizations now generate and track more data than ever before. One of the biggest challenges in the modern information technology landscape is now providing accessibility and disaster recovery for enterprise data banks. SEP sesam is an easy-to-use, high-performance business solution that provides flexible backup, restore, and disaster recovery options for businesses of any size. With broad platform support and a high performance data transfer technology, SEP sesam provides the best data recovery and migration solution in its class. Installation Requirements SEP sesam makes a strong first impression with its minimal system requirements and straight-forward and quick installation process. It requires a much smaller footprint for installation, both in terms of additional required software and the size of the installation, than any of its competitors. -

Server Baseline Document Q3 2012 (July 2012 – September 2012)
Server Baseline Document Q3 2012 (July 2012 – September 2012) Our Baseline Document is a compilation of patches that are considered stable and production ready for the current business quarter. This list outlines the major products which fit into our core expertise, primarily in the Data Center. We generally perform a quarterly Baseline process for all of our customers, and ensure that all the updates listed here are applied and functional. This accomplishes the following: • Implements bug fixes and other defects • Resolves known security vulnerabilities • May include feature enhancements • Keeps systems up to date and easier to support • Ensure support from vendor if issues arise The following tables outline the baselines for the major products within our core area of expertise. Red = Changed since last quarterly baseline; Gray Italics = Obsolete Product Server Operating Systems Patch Version (Release Date) SUSE Linux Enterprise Server 11 (SLES11) SLES 11 SP2 (Feb 27, 2012)** SUSE Linux Enterprise Server 10 (SLES10) SLES 10 SP4 (April 12, 2011) Novell Open Enterprise Server 11 (OES 11) SLES 11 SP1 (June 2, 2010) OES 11 (Dec 12, 2011) Novell Open Enterprise Server 2 (OES 2) SLES 10 SP4 (April 12, 2011) OES 2 SP3 (Dec 22, 2010) ** Microsoft Windows Server 2008 R2 Win2008 R2 SP1 (March 15, 2011) Microsoft Windows Server 2008 Win2008 SP2 (June 25, 2009) Novell NetWare 6.5 (Obsolete) NW6.5 SP8 + (May 6, 2009) Microsoft Windows Server 2003 (Obsolete) Windows 2003 SP2 (May 12, 2007) Email Systems and Collaboration Patch Version (Release Date) -

Links in an Event Description
1. Home . 3 1.1 Frequently Asked Questions (FAQ) . 3 1.1.1 Remove Calendar Ads . 8 1.1.2 Why is my calendar cut off on the bottom . 9 1.2 Overview of the localendar menu . 9 1.3 Entering and Editing Events . 11 1.3.1 Adding New Events . 12 1.3.1.1 Add Links in an Event Description . 15 1.3.2 Editing Existing Events . 16 1.3.3 Preview an Event . 16 1.3.4 Adding Clipart to an Event . 17 1.3.5 Uploading your own Images . 20 1.3.6 Repeating Events . 23 1.3.7 Entering a Multi-Day Event . 27 1.3.8 Entering a Multi-Day Event that Repeats . 29 1.3.9 Setting up Reminders . 32 1.3.10 Custom HTML in Events . 32 1.3.11 Tips and Tricks for Events . 33 1.3.12 Creating Events that Accept RSVPs, Payments, and More . 34 1.3.13 Attaching files to Events . 36 1.4 Deleting Events . 38 1.5 Publishing a Calendar . 38 1.5.1 Common Publishing Questions . 39 1.5.2 Gallery of Calendar Styles . 40 1.5.2.1 Timeline View . 44 1.5.3 Your Calendar's URL and Parameters . 46 1.5.4 The Publish Wizard . 47 1.6 Customizing your localendar . 48 1.6.1 General Options . 49 1.6.1.1 Additional General Options . 51 1.6.1.2 Using an Email Group for Reminders . 52 1.6.1.3 Visitor-Submitted Events . 52 1.6.2 Event Options . 52 1.6.3 Colors and Backgrounds . -

Groupware Reference
IceWarp Unified Communications GroupWare Reference Version 10.4 Printed on 20 December, 2012 Contents GroupWare 1 About.............................................................................................................................................................................. 2 Pre-requisities ................................................................................................................................................................ 3 Database ............................................................................................................................................... 3 Supported clients .................................................................................................................................. 3 Licenses ................................................................................................................................................. 4 General Setup ........................................................................................................................................ 4 Terminology, Abbreviations ........................................................................................................................................... 5 Sharing Concepts ............................................................................................................................................................ 7 User Groups ......................................................................................................................................................