Università Degli Studi Di Parma Service Oriented
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Fact Sheet: the Next Generation of Computing Has Arrived
News Fact Sheet The Next Generation of Computing Has Arrived: Performance to Power Amazing Experiences The new 5th Generation Intel® Core™ processor family is Intel’s latest wave of 14nm processors, delivering improved system and graphics performance, more natural and immersive user experiences, and enabling longer battery life compared to previous generations. The release of the 5th Generation Intel Core technology includes 14 new processors for consumers and businesses, including 10 new 15W processors with Intel® HD Graphics and four new 28W products with Intel® Iris™ Graphics. The 5th Generation Intel Core processor is purpose-built for the next generation of compute devices offering a thinner, lighter and more efficient experience across diverse form factors, including traditional notebooks, 2 in 1s, Ultrabooks™, Chromebooks, all-in-one desktop PCs and mini PCs. With the 5th Generation Intel Core processor availability, the “Broadwell” microarchitecture is expected to be the fastest mobile transition in company history to offer consumers a broad selection and availability of devices. Intel also started shipping its next generation 14nm processor for tablets, codenamed “Cherry Trail”, to device manufacturers. The new system on a chip (SoC) offers 64-bit computing, improved graphics with Intel® Generation 8-LP graphics, great performance and battery life for mainstream tablets. The platform offers world-class modem capabilities with LTE-Advanced on Intel® XMM™ 726x platform, which supports Cat-6 speeds and carrier aggregation. Customers will introduce new products based on this platform starting in the first half of this year. Key benefits of the 5th Generation Intel Core family and the next-generation 14nm processor for tablets include: Powerful Performance. -

Linux on the Road
Linux on the Road Linux with Laptops, Notebooks, PDAs, Mobile Phones and Other Portable Devices Werner Heuser <wehe[AT]tuxmobil.org> Linux Mobile Edition Edition Version 3.22 TuxMobil Berlin Copyright © 2000-2011 Werner Heuser 2011-12-12 Revision History Revision 3.22 2011-12-12 Revised by: wh The address of the opensuse-mobile mailing list has been added, a section power management for graphics cards has been added, a short description of Intel's LinuxPowerTop project has been added, all references to Suspend2 have been changed to TuxOnIce, links to OpenSync and Funambol syncronization packages have been added, some notes about SSDs have been added, many URLs have been checked and some minor improvements have been made. Revision 3.21 2005-11-14 Revised by: wh Some more typos have been fixed. Revision 3.20 2005-11-14 Revised by: wh Some typos have been fixed. Revision 3.19 2005-11-14 Revised by: wh A link to keytouch has been added, minor changes have been made. Revision 3.18 2005-10-10 Revised by: wh Some URLs have been updated, spelling has been corrected, minor changes have been made. Revision 3.17.1 2005-09-28 Revised by: sh A technical and a language review have been performed by Sebastian Henschel. Numerous bugs have been fixed and many URLs have been updated. Revision 3.17 2005-08-28 Revised by: wh Some more tools added to external monitor/projector section, link to Zaurus Development with Damn Small Linux added to cross-compile section, some additions about acoustic management for hard disks added, references to X.org added to X11 sections, link to laptop-mode-tools added, some URLs updated, spelling cleaned, minor changes. -
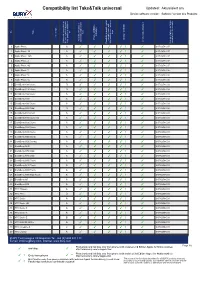
BURY Compatibility List Generator
Compatibility list Take&Talk universal Updated: Aktualisiert am: Device software version: Software Version des Produkts: on No key keys Type activation Set of tips Phone s REDIAL Charger available / private mode with Activation Bluetooth Article code (Charger) connection with device Bluetooth connection to used to test/ Comments after ignition is switched the last connected phone Bluetooth device / phones Possibility to switch car kit Version of phone software 1 Apple iPhone A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.07 2 Apple iPhone 3G A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.07 3 Apple iPhone 3GS A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.07 4 Apple iPhone 4 A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.07 5 Apple iPhone 4S A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.07 6 Apple iPhone 5 A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.08 7 Apple iPhone 5c A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.08 8 Apple iPhone 5s A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.08 9 BlackBerry 8300 Curve D ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.02 10 BlackBerry 8310 Curve D ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.02 11 BlackBerry 8520 Curve A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.01 12 BlackBerry 8800 A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.02 13 BlackBerry 8900 Curve A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.01 14 BlackBerry 9000 Bold D ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.02 15 BlackBerry 9105 Pearl A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.01 16 BlackBerry 9300 Curve 3G A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.01 17 BlackBerry 9320 Curve A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.01 18 BlackBerry 9360 Curve A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.01 19 BlackBerry 9380 Curve A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.01 20 BlackBerry 9500 Storm A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.01 21 BlackBerry 9520 Storm2 A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.01 22 BlackBerry 9630 A ✓ ✓ -

Embedded Linux Systems with the Yocto Project™
OPEN SOURCE SOFTWARE DEVELOPMENT SERIES Embedded Linux Systems with the Yocto Project" FREE SAMPLE CHAPTER SHARE WITH OTHERS �f, � � � � Embedded Linux Systems with the Yocto ProjectTM This page intentionally left blank Embedded Linux Systems with the Yocto ProjectTM Rudolf J. Streif Boston • Columbus • Indianapolis • New York • San Francisco • Amsterdam • Cape Town Dubai • London • Madrid • Milan • Munich • Paris • Montreal • Toronto • Delhi • Mexico City São Paulo • Sidney • Hong Kong • Seoul • Singapore • Taipei • Tokyo Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this book, and the publisher was aware of a trademark claim, the designations have been printed with initial capital letters or in all capitals. The author and publisher have taken care in the preparation of this book, but make no expressed or implied warranty of any kind and assume no responsibility for errors or omissions. No liability is assumed for incidental or consequential damages in connection with or arising out of the use of the information or programs contained herein. For information about buying this title in bulk quantities, or for special sales opportunities (which may include electronic versions; custom cover designs; and content particular to your business, training goals, marketing focus, or branding interests), please contact our corporate sales depart- ment at [email protected] or (800) 382-3419. For government sales inquiries, please contact [email protected]. For questions about sales outside the U.S., please contact [email protected]. Visit us on the Web: informit.com Cataloging-in-Publication Data is on file with the Library of Congress. -

1 Intel CEO Remarks Pat Gelsinger Q2'21 Earnings Webcast July 22
Intel CEO Remarks Pat Gelsinger Q2’21 Earnings Webcast July 22, 2021 Good afternoon, everyone. Thanks for joining our second-quarter earnings call. It’s a thrilling time for both the semiconductor industry and for Intel. We're seeing unprecedented demand as the digitization of everything is accelerated by the superpowers of AI, pervasive connectivity, cloud-to-edge infrastructure and increasingly ubiquitous compute. Our depth and breadth of software, silicon and platforms, and packaging and process, combined with our at-scale manufacturing, uniquely positions Intel to capitalize on this vast growth opportunity. Our Q2 results, which exceeded our top and bottom line expectations, reflect the strength of the industry, the demand for our products, as well as the superb execution of our factory network. As I’ve said before, we are only in the early innings of what is likely to be a decade of sustained growth across the industry. Our momentum is building as once again we beat expectations and raise our full-year revenue and EPS guidance. Since laying out our IDM 2.0 strategy in March, we feel increasingly confident that we're moving the company forward toward our goal of delivering leadership products in every category in which we compete. While we have work to do, we are making strides to renew our execution machine: 7nm is progressing very well. We’ve launched new innovative products, established Intel Foundry Services, and made operational and organizational changes to lay the foundation needed to win in the next phase of our company’s great history. Here at Intel, we’re proud of our past, pragmatic about the work ahead, but, most importantly, confident in our future. -

SIMD Extensions
SIMD Extensions PDF generated using the open source mwlib toolkit. See http://code.pediapress.com/ for more information. PDF generated at: Sat, 12 May 2012 17:14:46 UTC Contents Articles SIMD 1 MMX (instruction set) 6 3DNow! 8 Streaming SIMD Extensions 12 SSE2 16 SSE3 18 SSSE3 20 SSE4 22 SSE5 26 Advanced Vector Extensions 28 CVT16 instruction set 31 XOP instruction set 31 References Article Sources and Contributors 33 Image Sources, Licenses and Contributors 34 Article Licenses License 35 SIMD 1 SIMD Single instruction Multiple instruction Single data SISD MISD Multiple data SIMD MIMD Single instruction, multiple data (SIMD), is a class of parallel computers in Flynn's taxonomy. It describes computers with multiple processing elements that perform the same operation on multiple data simultaneously. Thus, such machines exploit data level parallelism. History The first use of SIMD instructions was in vector supercomputers of the early 1970s such as the CDC Star-100 and the Texas Instruments ASC, which could operate on a vector of data with a single instruction. Vector processing was especially popularized by Cray in the 1970s and 1980s. Vector-processing architectures are now considered separate from SIMD machines, based on the fact that vector machines processed the vectors one word at a time through pipelined processors (though still based on a single instruction), whereas modern SIMD machines process all elements of the vector simultaneously.[1] The first era of modern SIMD machines was characterized by massively parallel processing-style supercomputers such as the Thinking Machines CM-1 and CM-2. These machines had many limited-functionality processors that would work in parallel. -

Recent International Trade Commission Representations
Recent International Trade Commission Representations Certain Mobile Electronic Devices and Radio Frequency and Processing Components Thereof (II), Inv. No. 337-TA-1093 (ITC 2019). Quinn Emanuel was lead counsel for Qualcomm in a patent infringement action against Apple in the International Trade Commission. Qualcomm alleged that Apple engaged in the unlawful importation and sale of iPhones that infringe one or more claims of five Qualcomm patents covering key technologies that enable important features and function in the iPhones. After a seven day hearing, Administrative Law Judge McNamara issued an Initial Determination finding for Qualcomm on all issues related to claim 1 of U.S. Patent 8,063,674 related to an improved “Power on Control” circuit. ALJ McNamara recommended that the Commission issue a limited exclusion order with respect to the accused iPhone devices. Although the case settled shortly after AJ McNamara recommended the exclusion order, the order would have resulted in the exclusion of all iPhones and iPads without Qualcomm baseband processors from being imported into the United States. Certain Magnetic Tape Cartridges and Components Thereof Inv. No. 337-TA-1058 (ITC 2019): We represented Sony in a multifront battle against Fujifilm arising from Fujifilm’s anticompetitive conduct seeking to exclude Sony from the Linear Tape-Open magnetic tape market. LTO tape products are used to store large quantities of data by companies in a wide range of industries, including health care, education, finance and banking. Sony filed a complaint in the ITC seeking an exclusion order of Fujifilm’s products based on its infringement of three Sony patents covering various aspects of magnetic data storage technology. -

A3MAP: Architecture-Aware Analytic Mapping for Networks-On-Chip Wooyoung Jang and David Z
6C-2 A3MAP: Architecture-Aware Analytic Mapping for Networks-on-Chip Wooyoung Jang and David Z. Pan Department of Electrical and Computer Engineering University of Texas at Austin [email protected], [email protected] Abstract - In this paper, we propose a novel and global A3MAP formulation, we seek to embed a task graph into the metric (Architecture-Aware Analytic Mapping) algorithm applied to space of network. Then, the quality of task mapping is NoC (Networks-on-Chip) based MPSoC (Multi-Processor measured by the total distortion of metric embedding. System-on-Chip) not only with homogeneous cores on regular Through this formulation, our A3MAP can map a task mesh architecture as done by most previous mapping adaptively to any different sized tile both on a algorithms but also with heterogeneous cores on irregular mesh or custom architecture. As a main contribution, we develop a regular/irregular mesh and on a custom network. Fig. 1 simple yet efficient interconnection matrix that models any task shows the methodology of our A3MAP. Given a task graph graph and network. Then, task mapping problem is exactly and a network as inputs, an interconnection matrix that can formulated to an MIQP (Mixed Integer Quadratic model any task graph and network along interconnection is Programming). Since MIQP is NP-hard [15], we propose two generated. Then, task mapping problem is exactly effective heuristics, a successive relaxation algorithm and a formulated to an MIQP (Mixed Integer Quadratic genetic algorithm. Experimental results show that A3MAP by Programming) and is solved by two effective heuristics since the successive relaxation algorithm reduces an amount of the MIQP is NP-hard [15]. -

Generic Pipelined Processor Modeling and High Performance
Generic Pipelined Processor Modeling and High Performance Cycle-Accurate Simulator Generation Mehrdad Reshadi, Nikil Dutt Center for Embedded Computer Systems (CECS), Donald Bren School of Information and Computer Science, University of California Irvine, CA 92697, USA. {reshadi, dutt}@cecs.uci.edu simulators were more limited or slower than their manually generated Abstract counterparts. Detailed modeling of processors and high performance cycle- Colored Petri Net (CPN) [1] is a very powerful and flexible accurate simulators are essential for today’s hardware and software modeling technique and has been successfully used for describing design. These problems are challenging enough by themselves and parallelism, resource sharing and synchronization. It can naturally have seen many previous research efforts. Addressing both capture most of the behavioral elements of instruction flow in a simultaneously is even more challenging, with many existing processor. However, CPN models of realistic processors are very approaches focusing on one over another. In this paper, we propose complex mostly due to incompatibility of a token-based mechanism for the Reduced Colored Petri Net (RCPN) model that has two capturing data hazards. Such complexity reduces the productivity and advantages: first, it offers a very simple and intuitive way of modeling results in very slow simulators. In this paper, we present Reduced pipelined processors; second, it can generate high performance cycle- Colored Petri Net (RCPN), a generic modeling approach for accurate simulators. RCPN benefits from all the useful features of generating fast cycle-accurate simulators for pipelined processors. Colored Petri Nets without suffering from their exponential growth in RCPN is based on CPN and reduces the modeling complexity by complexity. -
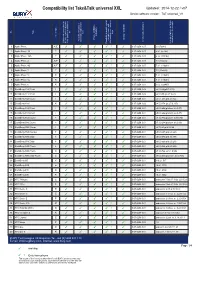
BURY Compatibility List Generator
Compatibility list Take&Talk universal XXL Updated: 2014-12-22 / v07 Device software version: T&T universal_V8 on No key keys Type activation Set of tips Phone s REDIAL Charger available / private mode with Activation Bluetooth Article code (Charger) connection with device Bluetooth connection to used to test/ Comments after ignition is switched the last connected phone Bluetooth device / phones Possibility to switch car kit Version of phone software 1 Apple iPhone A'/E ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.07 3.0 (7a341) 2 Apple iPhone 3G E ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.07 4.2.1 (8c148) 3 Apple iPhone 3GS E ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.07 6.1.2 (10b146) 4 Apple iPhone 4 A'/E ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.07 7.0 (11a465) 5 Apple iPhone 4S A'/E ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.07 7.1.1 (11d201) 6 Apple iPhone 5 E ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.08 7.0 (11a465) 7 Apple iPhone 5c A' ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.08 7.1.1 (11d201) 8 Apple iPhone 5s A' ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.08 7.1.1 (11d201) 9 Apple iPhone 6 A' ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.08 8.0.2 (12a405) 10 BlackBerry 8100 Pearl F ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.02 v4.5.0.69(pl2.7.0.72) 11 BlackBerry 8110 Pearl F ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.02 v4.5.0.55 (pl 2.7.0.68) 12 BlackBerry 8520 Curve F ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.01 v4.6.1.286 pl 4.2.0.122 13 BlackBerry 8800 A' ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.02 v4.5.0.174 (pl 2.7.0.105) 14 BlackBerry 9100 Pearl E ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.01 v5.0.0.696(platform 6.2.0.57) 15 BlackBerry 9105 Pearl E ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.01 v5.0.0.696(platform 6.2.0.57) 16 BlackBerry 9320 Curve E ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.01 v7.1.0.714(platform -

SUSTAINABLE INVESTMENT & ANALYSIS by J. TYLER RENZI A
Sustainable Investment and Analysis Item Type text; Electronic Thesis Authors Renzi, J. Tyler Publisher The University of Arizona. Rights Copyright © is held by the author. Digital access to this material is made possible by the University Libraries, University of Arizona. Further transmission, reproduction or presentation (such as public display or performance) of protected items is prohibited except with permission of the author. Download date 24/09/2021 04:29:36 Link to Item http://hdl.handle.net/10150/146637 Renzi, 1 SUSTAINABLE INVESTMENT & ANALYSIS By J. TYLER RENZI ________________________ A Thesis Submitted to The Honors College In Partial Fulfillment of the Bachelors degree With Honors in Finance The University of Arizona May 2010 Approved by: ______________________________ Dr. Sharon Garrison Department of Finance Renzi, 2 The University of Arizona Electric Theses and Dissertations Reproduction and Distribution Form Name: Renzi, John Tyler Degree Title: Bachelor’s in Business Administration Honors Area: Finance Date thesis submitted to Honors College: 05/05/2010 Title of Honors thesis: Sustainable Investment and Analysis The University of Arizona Library Release I hereby grant to the University of Arizona Library the nonexclusive worldwide right to reproduce and distribute my dissertation or thesis and abstract (herein, the “licensed materials”), in whole or in part, in any and all media of distribution and in any format in existence now or developed in the future. I represent and warrant to the University of Arizona that the licensed materials are my original work, that I am the sole owner of all rights in and to the licensed materials, and that none of the licensed materials infringe or violate the rights of others. -

Testimony to the Subcommittee on Research of the House Committee
Testimony to the Subcommittee on Research Of the House Committee on Science, Space, Technology Shelly Esque Intel Vice-President of Legal and Corporate Affairs, Global Director of Corporate Affairs Group President of the Intel Foundation March 13, 2013 Intel Corporation respectfully submits this testimony for the record in conjunction with the Committee’s hearing on STEM education. The testimony will focus on three topics The importance of a highly skilled workforce to Intel’s manufacturing and research investments in the United States The role of STEM education in fostering innovation to solve global challenges Intel’s education programs and partnerships to create that workforce and foster innovation Intel Corporation Intel Corporation is the world's largest semiconductor chip maker, based on revenue. We develop advanced integrated digital technology, primarily integrated circuits, for industries such as computing and communications. Our goal is to be the preeminent computing solutions company that powers the worldwide digital economy. We are transforming from a company with a primary focus on the design and manufacture of semiconductor chips for PCs and servers to a computing company that delivers complete solutions in the form of hardware and software platforms and supporting services. Intel was founded 45 years ago at the dawn of the digital age in Silicon Valley and our corporate headquarters is in Santa Clara, California. Our history is the history of the 20th century technology revolution and is still being written today. As of the end of 2012 Intel employed over 105,000 people worldwide and more than half of them, over 53,000, are here in the US.