RE: Request to Access Personal Information Dear Teksavvy User
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Teksavvy Solutions Inc. Consultation on the Technical and Policy
TekSavvy Solutions Inc. Reply Comments in Consultation on the Technical and Policy Framework for the 3650-4200 MHz Band and Changes to the Frequency Allocation of the 3500-3650 MHz Band Canada Gazette, Part I, August 2020, Notice No. SLPB-002-20 November 30, 2020 TekSavvy Solutions Inc. Reply Comments to Consultation SLPB-002-20 TABLE OF CONTENTS A. Introduction ____________________________________________________________ 1 B. Arguments for option 1 and against option 2 _________________________________ 1 a. Contiguity ______________________________________________________________ 1 b. Availability of ecosystem in the 3900: impacts on viability_________________________ 3 c. Moratorium ____________________________________________________________ 4 d. Arguments for Improvements to Option 1 _____________________________________ 4 C. 3800 MHz Auction _______________________________________________________ 5 a. Value _________________________________________________________________ 5 b. Procompetitive Measures _________________________________________________ 5 c. Tier 4 and 5 Licensing Area ________________________________________________ 6 TekSavvy Solutions Inc. Page 1 of 6 Reply Comments to Consultation SLPB-002-20 A. INTRODUCTION 1. TekSavvy Solutions Inc. (“TekSavvy”) is submitting its reply comments on ISED’s “Consultation on the Technical and Policy Framework for the 3650-4200 MHz Band and Changes to the Frequency Allocation of the 3500-3650 MHz Band”. 2. TekSavvy reasserts its position in favour of Option 1 in that Consultation document, and its strong opposition to Option 2, as expressed in its original submission. TekSavvy rejects Option 2 as disastrous both for WBS service providers’ ongoing viability and availability of broadband service to rural subscribers. 3. TekSavvy supports Option 1, wherein WBS Licensees would be allowed to continue to operate in the band of 3650 to 3700 MHz indefinitely as the only option that enables continued investment in rural broadband networks and continued improvement of broadband services to rural subscribers. -

January 11, 2019 the Broadcasting and Telecommunications Legislative Review Panel C/O Innovation, Science and Economic Devel
January 11, 2019 The Broadcasting and Telecommunications Legislative Review Panel c/o Innovation, Science and Economic Development Canada 235 Queen Street, 1st Floor Ottawa, Ontario K1A 0H5 VMedia Inc. (“VMedia”) is grateful for the opportunity to submit comments on the broadcasting and telecommunications legislative review (the “Review”) initiated by Innovation, Science and Economic Development (“ISED”) Canada. Executive Summary The Review ES1.The issues outlined in the terms of reference and the themes described by the panel appointed by ISED to review the relevant legislation (the “Panel”) are extensive. There are seven terms of reference relating to issues to consider in connection with the Telecommunications and Radiocommunication Acts, and eight in connection with the Broadcasting Act. In addition, there are four themes set out by the Panel intended to “help guide its work and structure meaningful dialogue during its consultation process”. ES2.Among those 19 elements of consideration, we note that the word competition is mentioned only twice, with little elaboration or context. ES3.As the second point under both the Telecommunications and Radiocommunication Acts, under the heading “Competition, Innovation, and Affordability”, the question is asked, “Are legislative changes warranted to better promote competition, innovation and affordability?” ES4.In addition, competition is mentioned at the very end of the first of the Panel’s themes, “Reducing Barriers to Access by All Canadian to Advanced Telecommunications Networks”. All of the rest of that theme focuses on the achievements of telephone and cable companies, and the heavy lifting ahead of them as they keep up with digital transformation. ES5.There is no mention at all of competition in the terms of reference relating to the Broadcasting Act. -
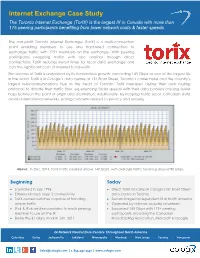
Cologix Torix Case Study
Internet Exchange Case Study The Toronto Internet Exchange (TorIX) is the largest IX in Canada with more than 175 peering participants benefiting from lower network costs & faster speeds The non-profit Toronto Internet Exchange (TorIX) is a multi-connection point enabling members to use one hardwired connection to exchange traffic with 175+ members on the exchange. With peering participants swapping traffic with one another through direct connections, TorIX reduces transit times for local data exchange and cuts the significant costs of Internet bandwidth. The success of TorIX is underlined by its tremendous growth, exceeding 145 Gbps as one of the largest IXs in the world. TorIX is in Cologix’s data centre at 151 Front Street, Toronto’s carrier hotel and the country’s largest telecommunications hub in the heart of Toronto. TorIX members define their own routing protocols to dictate their traffic flow, experiencing faster speeds with their data packets crossing fewer hops between the point of origin and destination. Additionally, by keeping traffic local, Canadian data avoids international networks, easing concerns related to privacy and security. Above: In Dec. 2014, TorIX traffic peaked above 140 Gbps, with average traffic hovering around 90 Gbps. Beginning Today Launched in July 1996 Direct TorIX on-ramp in Cologix’s151 Front Street Ethernet-based, layer 2 connectivity data centre in Toronto TorIX-owned switches capable of handling Second largest independent IX in North America ample traffic Operated by telecom industry volunteers IPv4 & IPv6 address provided to each peering Surpassed 145 Gbps with 175+ peering member to use on the IX participants, including the Canadian Broke the 61 Gbps mark in Jan. -

BCE Inc. 2015 Annual Report
Leading the way in communications BCE INC. 2015 ANNUAL REPORT for 135 years BELL LEADERSHIP AND INNOVATION PAST, PRESENT AND FUTURE OUR GOAL For Bell to be recognized by customers as Canada’s leading communications company OUR STRATEGIC IMPERATIVES Invest in broadband networks and services 11 Accelerate wireless 12 Leverage wireline momentum 14 Expand media leadership 16 Improve customer service 18 Achieve a competitive cost structure 20 Bell is leading Canada’s broadband communications revolution, investing more than any other communications company in the fibre networks that carry advanced services, in the products and content that make the most of the power of those networks, and in the customer service that makes all of it accessible. Through the rigorous execution of our 6 Strategic Imperatives, we gained further ground in the marketplace and delivered financial results that enable us to continue to invest in growth services that now account for 81% of revenue. Financial and operational highlights 4 Letters to shareholders 6 Strategic imperatives 11 Community investment 22 Bell archives 24 Management’s discussion and analysis (MD&A) 28 Reports on internal control 112 Consolidated financial statements 116 Notes to consolidated financial statements 120 2 We have re-energized one of Canada’s most respected brands, transforming Bell into a competitive force in every communications segment. Achieving all our financial targets for 2015, we strengthened our financial position and continued to create value for shareholders. DELIVERING INCREASED -

Media and Internet Concentration in Canada, 1984-2018
MEDIA AND INTERNET CONCENTRATION IN CANADA, 1984-2018 REPORT DECEMBER 2019 Canadian Media Concentration Research Project Research Canadian Media Concentration www.cmcrp.org Candian Media Concentration Research Project x The Canadian Media Concentration Research project is directed by Professor Dwayne Winseck, School of Journalism and Communication, Carleton University. The project was funded by the Social Sciences and Humanities Research Council between 2012 and 2018, after which the Faculty of Public Affairs at Carleton University generously stepped in to provide bridge funding for the next two years of the project. The overall objective of the CMCR Project is to develop a comprehensive, systematic and long-term analysis of the telecoms, internet and media industries in Canada to better inform public and policy-related discussions about these issues. Professor Winseck can be reached at either [email protected] or 613 769- 7587 (mobile). Open Access to CMCR Project Data CMCR Project data can be freely downloaded and used under Creative Commons licensing arrangements for non-commercial purposes with proper attribution and in accordance with the ShareAlike principles set out in the International License 4.0. Explicit, written permission is required for any other use that does not follow these principles. Our data sets are available for download here and also available in our long term data archive hosted on the CMCRP Dataverse. Dataverse is a publicly-accessible repository of scholarly works created and maintained by a consortium of Canadian universities. All works and datasets deposited in our CMCRP Dataverse are given a permanent DOI, so as to not be lost when a website becomes no longer available—a form of “dead media”. -

Morning News Call Canada
MORNING NEWS CALL Powered by Re uters Canada Edition Monday, April 26, 2021 TOP NEWS • Frustrated Canada presses White House to keep Great Lakes oil pipeline open Canada is pushing on several diplomatic fronts against the U.S. state of Michigan's efforts to close a cross-border oil pipeline, the second such dispute since Joe Biden became U.S. president in January, complicating the governments' efforts to work together to lower carbon emissions. • Shippers push for CP Railway to win bidding war for Kansas City Southern North America's freight rail customers, from grain shippers to logistics companies, are pushing for Canadian Pacific Railway to win a bidding war for Kansas City Southern over rival Canadian National Railway, eyeing stronger competition and swifter service. • Moderna vaccine to be reviewed for WHO emergency listing on April 30 - WHO spokesman Moderna's COVID-19 vaccine will be reviewed on April 30 by technical experts for possible WHO emergency-use listing, a World Health Organization spokesman told Reuters. • Health Canada finds Astrazeneca COVID-19 vaccines from Baltimore plant safe, of high quality Canada's health department said on Sunday the 1.5 million doses of the Astrazeneca COVID-19 vaccine imported from Emergent BioSolutions' Baltimore facility were safe and met quality specifications. • Canadian government to intervene to end potential Montreal port strike The Canadian government will intervene to end a potential strike at the country's second-largest port, the labour minister said on Sunday, as the clock ticked down to a walkout by Montreal dockworkers. BEFORE THE BELL Canada's main stock index futures fell, weighed by a drop in oil prices, as investors awaited a first-quarter earnings update from Canadian National Railway later in the day. -

Reply Comments of Shaw Communications Inc. Consultation
Reply Comments of Shaw Communications Inc. Consultation on a New Set of Service Areas for Spectrum Licensing Canada Gazette, Part I, November 27, 2018, Notice No. DGSO-002-18, as amended March 21, 2019 I. INTRODUCTION 1. The following constitute the reply comments of Shaw Communications Inc. (“Shaw”) to Innovation, Science and Economic Development Canada (“ISED” or the “Department”) in connection with the proceeding (the “Consultation”) initiated by Consultation on a New Set of Service Areas for Spectrum Licensing, Notice No. DGSO-002-18 (the “Consultation Document”), as amended by Notice No. DGSO-003-18. 2. As explained in our initial comments, Shaw is generally supportive of the goals and policy objectives that motivate and guide the Department in the present Consultation.1 However, we question the need to establish a new set of nationwide service tiers to achieve them. In fact, the development and use of an overly prescriptive licensing tool at this time could actually diminish efficient spectrum usage and hinder Canada’s ability to meet future wireless needs, especially if the Department’s proposals are not carefully examined and adjusted. 3. Other parties share these reservations.2 Québecor has opposed the Department’s proposal to create Tier 5 licence areas, echoing Shaw’s concerns.3 It has further noted that the Department recently established stricter deployment requirements in order to promote rural deployment by licensees, and that such measures should be given time to take effect.4 Bell has stated that the “creation of Tier -

Part 1 Application to Review and Vary Telecom Regulatory Policy CRTC 2019-269, the Internet Code
December 6, 2019 VIA Intervention Comment Form Mr. Claude Doucet Secretary General Canadian Radio-television and Telecommunications Commission Ottawa, Ontario K1A 0N2 Dear Mr. Doucet, Subject: Part 1 Application to Review and Vary Telecom Regulatory Policy CRTC 2019-269, The Internet Code 1. The Canadian Communication Systems Alliance (“CCSA”) and the Independent Telecommunications Providers Association (“ITPA”) hereby submit their joint response to the Part 1 Application by Bell, Cogeco, Eastlink, Quebecor Media, SaskTel, Shaw and TELUS (collectively, “the Applicants” or “the large, facilities-based ISPs”) for a Commission review and variance of TRP CRTC 2019-269, “The Internet Code”. 2. In making this joint response, CCSA and ITPA speak for their combined memberships. While some CCSA/ITPA members offer non-facilities-based service outside their home networks, all such members who offer Internet service to the public are small, facilities- based ISPs. Executive Summary 3. The decisions in Telecommunications Regulatory Policy CRTC 2019-269 were based on the Commission’s consideration of an extensive body of evidence gathered in the course of a full public process. 4. That evidence included representations from “over 2,300 individuals, including more than 65 current or past employees of the Service Providers or of third parties offering the Service Providers’ services for sale; the CCTS; consumer and public advocacy groups; researchers; unions representing employees; government agencies and departments; and the 12 Service Providers [the -

Bell V. Cogeco: Unfair Competition – the “Best Internet Experience” Results in an Unfavorable Judicial Experience
Bell v. Cogeco: Unfair competition – the “best Internet experience” results in an unfavorable judicial experience October 28, 2016 Author Alain Y. Dussault Partner, Lawyer Partner, and Trademark Agent In the field of telecommunications, it is not uncommon to see competing Internet service providers engage in advertising war campaigns in order to attract new customers, particularly in this highly competitive market due to the small number of competitors. Competitors are prepared to do anything to attract consumers, perhaps even making their offered products and services appear more attractive than they are. It is in this context that the Superior Court of Ontario issued, in Bell Canada v. Cogeco Cable Canada, 2016 ONSC 6044 1, September 20, 2016, an interlocutory injunction against Cogeco Cable Canada, in order to cease any use of the advertising phrase “the best Internet experience in your neighborhood ” in its advertisements, on the grounds of false and misleading representations. Facts and background of the case Bell Canada (hereinafter “Bell”) and Cogeco Cable Canada (hereinafter “Cogeco”) are two competing Internet providers in Ontario. However, Bell and Cogeco do not use the same technology to provide their services to consumers. Specifically, Cogeco uses “Hybrid fiber coaxial cable” technology (Cable / HFC), while Bell uses “Digital subscriber lines” (DSL) technology. In addition to DSL, Bell also uses “Fiber to the home” (FTTH) through the entire province of Ontario while Cogeco offers this technology only in new residential neighborhoods. In August 2016, Cogeco announced its new brand identity as part of its advertising campaign for the Copyright (c) Lavery, de Billy, S.E.N.C.R.L. -

Court File No. CV-16-11257-00CL ONTARIO SUPERIOR COURT of JUSTICE COMMERCIAL LIST
Court File No. CV-16-11257-00CL ONTARIO SUPERIOR COURT OF JUSTICE COMMERCIAL LIST IN THE MATTER OF THE COMPANIES’ CREDITORS ARRANGEMENT ACT, R.S.C. 1985, c. C-36, AS AMENDED AND IN THE MATTER OF A PLAN OF COMPROMISE OR ARRANGEMENT OF PT HOLDCO, INC., PRIMUS TELECOMMUNICATIONS CANADA, INC., PTUS, INC., PRIMUS TELECOMMUNICATIONS, INC., AND LINGO, INC. (Applicants) APPROVAL AND VESTING ORDER SERVICE LIST GENERAL STIKEMAN ELLIOTT LLP Samantha Horn 5300 Commerce Court West Tel: (416) 869- 5636 199 Bay Street Email: [email protected] Toronto, ON M5L 1B9 Maria Konyukhova Tel: (416) 869-5230 Email: [email protected] Kathryn Esaw Tel: (416) 869-6820 Email: [email protected] Vlad Calina Tel: (416) 869-5202 Lawyers for the Applicants Email: [email protected] FTI CONSULTING CANADA INC. Nigel D. Meakin TD Waterhouse Tower Tel: (416) 649-8100 79 Wellington Street, Suite 2010 Fax: (416) 649-8101 Toronto, ON M5K 1G8 Email: [email protected] Steven Bissell Tel: (416) 649-8100 Fax: (416) 649-8101 Email: [email protected] Kamran Hamidi Tel: (416) 649-8100 Fax: (416) 649-8101 Monitor Email: [email protected] 2 BLAKE, CASSELS & GRAYDON LLP Linc Rogers 199 Bay Street Tel: (416) 863-4168 Suite 4000, Commerce Court West Fax: (416) 863-2653 Toronto, ON M5L 1A9 Email: [email protected] Aryo Shalviri Tel: (416) 863- 2962 Fax: (416) 863-2653 Lawyers for the Monitor Email: [email protected] DAVIES WARD PHILLIPS VINEBERG LLP Natasha MacParland 155 Wellington Street West Tel: (416) 863 5567 Toronto, ON M5V 3J7 Fax: (416) 863 0871 Email: [email protected] Lawyers for the Bank of Montreal, as Administrative Agent for the Syndicate FOGLER, RUBINOFF LLP Gregg Azeff 77 King Street West Tel: (416) 365-3716 Suite 3000, P.O. -

In the Supreme Court of Canada
Court File No. 34231 IN THE SUPREME COURT OF CANADA (ON APPEAL FROM THE FEDERAL COURT OF APPEAL) IN THE MATTER OF AN APPLICATION BY WAY OF A REFERENCE TO THE FEDERAL COURT OF APPEAL PURSUANT TO SECTIONS 18.3(1) AND 28(2) OF THE FEDERAL COURTS ACT, R.S.C. 1985, C.F-7 B E T W E E N: COGECO CABLE INC. Appellant - and - BELL MEDIA INC. (FORMERLY CTV GLOBEMEDIA INC.), CANWEST TELEVISION LIMITED PARTNERSHIP, NEWFOUNDLAND BROADCASTING CO. LTD., V INTERACTIONS INC. AND ATTORNEY GENERAL OF CANADA Respondents A N D B E T W E E N: ROGERS COMMUNICATIONS INC. and TELUS COMMUNICATIONS Appellants - and - BELL MEDIA INC. (FORMERLY CTV GLOBEMEDIA INC.), CANWEST TELEVISION LIMITED PARTNERSHIP, NEWFOUNDLAND BROADCASTING CO. LTD., V INTERACTIONS INC. AND ATTORNEY GENERAL OF CANADA Respondents A N D B E T W E E N: SHAW COMMUNICATIONS INC. Appellant - and - BELL MEDIA INC. (FORMERLY CTV GLOBEMEDIA INC.), CANWEST TELEVISION LIMITED PARTNERSHIP, NEWFOUNDLAND BROADCASTING CO. LTD., V INTERACTIONS INC. AND ATTORNEY GENERAL OF CANADA Respondents - and - THE CANADIAN RADIO-TELEVISION AND TELECOMMUNICATIONS COMMISSION (CRTC) Intervener FACTUM OF THE APPELLANT COGECO CABLE INC. (Pursuant to Rules 35 and 42 of the Rules of the Supreme Court of Canada) McCarthy Tétrault LLP Cavanagh Williams Conway Baxter LLP Suite 5300, Toronto-Dominion Bank Tower Suite 401 Toronto, ON M5K 1E6 1111 Prince of Wales Drive Ottawa, ON K2C 3T2 Neil Finkelstein Steven G. Mason Colin S. Baxter Daniel G.C. Glover Tel: (613) 780-2011 Tel: (416) 601-8200 Fax: (613) 569-8668 Fax: (416) 868-0673 Ottawa Agent for the Appellant Solicitors for the Appellant Cogeco Cable Inc. -

Implementation of Universal Network-Level Blocking of Calls with Blatantly Illegitimate Caller Identification
Compliance and Enforcement and Telecom Regulatory Policy CRTC 2018-484 PDF version References: 2017-405 and 2017-405-1 Ottawa, 19 December 2018 Public record: 1011-NOC2017-0405 Implementation of universal network-level blocking of calls with blatantly illegitimate caller identification The Commission mandates that universal network-level call blocking where the caller identification purports to originate from telephone numbers that do not conform to established numbering plans is to be implemented by Canadian carriers and other telecommunications service providers (TSPs) that provide voice telecommunications services within 12 months of the date of this decision. This mandate will not apply to those Canadian carriers and other TSPs providing voice telecommunications services that implement call filtering solutions within the time frame prescribed for the implementation of universal network-level call blocking. The Commission also sets out its findings for mitigation, notification, disclosure, redress, and monitoring approaches related to the implementation of universal network-level call blocking. Introduction Compliance and Enforcement and Telecom Regulatory Policy 2016-442 1. In Compliance and Enforcement and Telecom Regulatory Policy 2016-442, the Commission set out its findings on technical solutions that Canadians could use to protect themselves from unwanted unsolicited and illegitimate telecommunications. In particular, the Commission concluded that • universal network-level call blocking is the most effective and efficient solution to manage nuisance calls in cases where it is possible to accurately identify blatantly illegitimate caller identification (caller ID) spoofing;1 and 1 A spoofed number can appear as a string of digits, such as 000-000-0000, a random number, or the number of a company, person, or government entity.