Digital Forensics Analysis of Ubuntu Touch on Pinephone
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Plasma on Mobile Devices
Plasma on Mobile devices Application Ecosystem MC Bhushan Shah KDE Developer Agenda ● Initial development of the Plasma Mobile ● Basic architecture details ● Advantages to KDE community ● Application ecosystem and development ● Future for Plasma Mobile ● Challenges Introduction ● KDE developer and sysadmin ● Plasma Mobile maintainer and lead developer ● Employed by Bluesystems GmbH ● From Vadodara, India KDE ● Previously known as the K Desktop Environment ● Now community, which creates free software for end users ● Several products including Plasma, KDE Frameworks, KDE applications. Plasma Mobile ● Announced in the July 2015 ● Vision of providing completely free and open-source mobile platform which respects user’s privacy and freedom. ● Initial prototype on the LG Nexus 5. Initial Development ● LGE Nexus 5 as reference device ● Ubuntu Touch 15.04 (vivid) as base system ● Makes use of the Android binary blobs / drivers ● Can also run on the desktop system for development Basic architecture details ● KWin wayland as compositor ● DRM/GBM or hwcomposer backends ● plasmashell and mobile shell package ● QtQuickControls2 and Kirigami for application development Advantages to KDE community ● Several performance improvements ● Better touch input support in applications and shell ● Improvements in Wayland support ● More modular and re-usable user interfaces Application ecosystem and development ● QtQuickControls2 and Kirigami as toolkit ● CMake/QMake as a buildsystem ● Various bundle formats as well as native distribution packaging for the distribution -
Backbox Penetration Testing Never Looked So Lovely
DISTROHOPPER DISTROHOPPER Our pick of the latest releases will whet your appetite for new Linux distributions. Picaros Diego Linux for children. here are a few distributions aimed at children: Doudou springs to mind, Tand there’s also Sugar on a Stick. Both of these are based on the idea that you need to protect children from the complexities of the computer (and protect the computer from the children). Picaros Diego is different. There’s nothing stripped- down or shielded from view. Instead, it’s a normal Linux distro with a brighter, more kid-friendly interface. The desktop wallpaper perhaps best We were too busy playing Secret Mario on Picaros Diego to write a witty or interesting caption. exemplifies this. On one hand, it’s a colourful cartoon image designed to interest young file manager. In the programming category, little young for a system like this, but the it children. Some of the images on the we were slightly disappointed to discover it may well work for children on the upper end landscape are icons for games, and this only had Gambas (a Visual Basic-like of that age range. should encourage children to investigate the language), and not more popular teaching Overall, we like the philosophy of wrapping system rather than just relying on menus. languages like Scratch or a Python IDE. Linux is a child-friendly package, but not On the other hand, it still displays technical However, it’s based on Debian, so you do dumbing it down. Picaros Diego won’t work details such as the CPU usage and the RAM have the full range of software available for every child, but if you have a budding and Swap availability. -
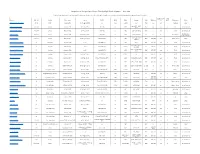
Comparison of 116 Open Spec, Hacker Friendly Single Board Computers -- June 2018
Comparison of 116 Open Spec, Hacker Friendly Single Board Computers -- June 2018 Click on the product names to get more product information. In most cases these links go to LinuxGizmos.com articles with detailed product descriptions plus market analysis. HDMI or DP- USB Product Price ($) Vendor Processor Cores 3D GPU MCU RAM Storage LAN Wireless out ports Expansion OSes 86Duino Zero / Zero Plus 39, 54 DMP Vortex86EX 1x x86 @ 300MHz no no2 128MB no3 Fast no4 no5 1 headers Linux Opt. 4GB eMMC; A20-OLinuXino-Lime2 53 or 65 Olimex Allwinner A20 2x A7 @ 1GHz Mali-400 no 1GB Fast no yes 3 other Linux, Android SATA A20-OLinuXino-Micro 65 or 77 Olimex Allwinner A20 2x A7 @ 1GHz Mali-400 no 1GB opt. 4GB NAND Fast no yes 3 other Linux, Android Debian Linux A33-OLinuXino 42 or 52 Olimex Allwinner A33 4x A7 @ 1.2GHz Mali-400 no 1GB opt. 4GB NAND no no no 1 dual 40-pin 3.4.39, Android 4.4 4GB (opt. 16GB A64-OLinuXino 47 to 88 Olimex Allwinner A64 4x A53 @ 1.2GHz Mali-400 MP2 no 1GB GbE WiFi, BT yes 1 40-pin custom Linux eMMC) Banana Pi BPI-M2 Berry 36 SinoVoip Allwinner V40 4x A7 Mali-400 MP2 no 1GB SATA GbE WiFi, BT yes 4 Pi 40 Linux, Android 8GB eMMC (opt. up Banana Pi BPI-M2 Magic 21 SinoVoip Allwinner A33 4x A7 Mali-400 MP2 no 512MB no Wifi, BT no 2 Pi 40 Linux, Android to 64GB) 8GB to 64GB eMMC; Banana Pi BPI-M2 Ultra 56 SinoVoip Allwinner R40 4x A7 Mali-400 MP2 no 2GB GbE WiFi, BT yes 4 Pi 40 Linux, Android SATA Banana Pi BPI-M2 Zero 21 SinoVoip Allwinner H2+ 4x A7 @ 1.2GHz Mali-400 MP2 no 512MB no no WiFi, BT yes 1 Pi 40 Linux, Android Banana -

Building a Distribution: Openharmony and Openmandriva
Two different approaches to building a distribution: OpenHarmony and OpenMandriva Bernhard "bero" Rosenkränzer <[email protected]> FOSDEM 2021 -- February 6, 2021 1 MY CONTACT: [email protected], [email protected] Way more important than that, he also feeds LINKEDIN: dogs. https://www.linkedin.com/in/berolinux/ Bernhard "bero" Rosenkränzer I don't usually do "About Me", but since it may be relevant to the topic: Principal Technologist at Open Source Technology Center since November 2020 President of the OpenMandriva Association, Contributor since 2012 - also a contributor to Mandrake back in 1998/1999 2 What is OpenHarmony? ● More than an operating system: Can use multiple different kernels (Linux, Zephyr, ...) ● Key goal: autonomous, cooperative devices -- multiple devices form a distributed virtual bus and can share resources ● Initial target devices: Avenger 96 (32-bit ARMv7 Cortex-A7+-M4), Nitrogen 96 (Cortex-M4) ● Built with OpenEmbedded/Yocto - one command builds the entire OS ● Fully open, developed as an Open Source project instead of an inhouse product from the start. ● For more information, visit Stefan Schmidt's talk in the Embedded devroom, 17.30 and/or talk to us at the Huawei OSTC stand. 3 What is OpenMandriva? ● A more traditional Linux distribution - controlled by the community, continuing where Mandriva left off after the company behind it went out of business in 2012. Its roots go back to the first Mandrake Linux release in 1998. ● Originally targeting only x86 PCs - Support for additional architectures (aarch64, armv7hnl, RISC-V) added later ● Repositiories contain 17618 packages, built and updated individually, assembled into an installable product with omdv-build-iso or os-image-builder. -

Filesystem Hierarchy Standard
Filesystem Hierarchy Standard LSB Workgroup, The Linux Foundation Filesystem Hierarchy Standard LSB Workgroup, The Linux Foundation Version 3.0 Publication date March 19, 2015 Copyright © 2015 The Linux Foundation Copyright © 1994-2004 Daniel Quinlan Copyright © 2001-2004 Paul 'Rusty' Russell Copyright © 2003-2004 Christopher Yeoh Abstract This standard consists of a set of requirements and guidelines for file and directory placement under UNIX-like operating systems. The guidelines are intended to support interoperability of applications, system administration tools, development tools, and scripts as well as greater uniformity of documentation for these systems. All trademarks and copyrights are owned by their owners, unless specifically noted otherwise. Use of a term in this document should not be regarded as affecting the validity of any trademark or service mark. Permission is granted to make and distribute verbatim copies of this standard provided the copyright and this permission notice are preserved on all copies. Permission is granted to copy and distribute modified versions of this standard under the conditions for verbatim copying, provided also that the title page is labeled as modified including a reference to the original standard, provided that information on retrieving the original standard is included, and provided that the entire resulting derived work is distributed under the terms of a permission notice identical to this one. Permission is granted to copy and distribute translations of this standard into another language, under the above conditions for modified versions, except that this permission notice may be stated in a translation approved by the copyright holder. Dedication This release is dedicated to the memory of Christopher Yeoh, a long-time friend and colleague, and one of the original editors of the FHS. -

Consolidate Home Directories to Improve Workforce Productivity
Solution brief Consolidate home directories to improve workforce productivity HPE 3PAR File Persona Software Empower and enable users while increasing security Efficient: Improve your primary storage efficiency and control • One-third the data center footprint and significant power savings • One converged capacity eliminates Challenge Truly converged storage for wasted block or file space reservation home directory consolidation Localized user data with inadequate and Effortless: Simplify your storage inefficient protection and control HPE 3PAR StoreServ is highly efficient, deployment and administration Every IT organization has a need to store • Autonomic provisioning of all capacity flash-optimized storage engineered for and manage user-generated data such as the true convergence of block, file, and • Single, simple, and streamlined business documents, images, audio, and administration of block, file, and object access. HPE 3PAR Operating System object access video files. Traditionally, this has been done and converged controllers incorporate in local home directories on individual users’ multi-protocol support into the heart Bulletproof: Deploy your file shares laptops and desktops resulting in higher of the system architecture. This unique with confidence than necessary client device costs, ineffective • Resilient Mesh-Active architecture solution delivers tightly integrated, truly and intrusive backup processes, complex converged storage for provisioning both • Mission-critical proven HPE file system and time-consuming restore processes, and block volumes for server workloads and file poor data governance. IT needs a solution and object shares for client workloads such that maximizes workforce productivity while as home directory consolidation—efficiently, ensuring that data is effectively protected, effortlessly, and without compromise. secured, and controlled—all with minimal cost and effort. -

Firefox OS Overview Ewa Janczukowicz
Firefox OS Overview Ewa Janczukowicz To cite this version: Ewa Janczukowicz. Firefox OS Overview. [Research Report] Télécom Bretagne. 2013, pp.28. hal- 00961321 HAL Id: hal-00961321 https://hal.archives-ouvertes.fr/hal-00961321 Submitted on 24 Apr 2014 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Collection des rapports de recherche de Télécom Bretagne RR-2013-04-RSM Firefox OS Overview Ewa JANCZUKOWICZ (Télécom Bretagne) This work is part of the project " Étude des APIs Mozilla Firefox OS" supported by Orange Labs / TC PASS (CRE API MOZILLA FIREFOX OS - CTNG13025) ACKNOWLEGMENTS Above all, I would like to thank Ahmed Bouabdallah and Arnaud Braud for their assistance, support and guidance throughout the contract. I am very grateful to Gaël Fromentoux and Stéphane Tuffin for giving me the possibility of working on the Firefox OS project. I would like to show my gratitude to Jean-Marie Bonnin, to all members of Orange NCA/ARC team and RSM department for their help and guidance. RR-2013-04-RSM 1 RR-2013-04-RSM 2 SUMMARY Firefox OS is an operating system for mobile devices such as smartphones and tablets. -

Download Android Os for Phone Open Source Mobile OS Alternatives to Android
download android os for phone Open Source Mobile OS Alternatives To Android. It’s no exaggeration to say that open source operating systems rule the world of mobile devices. Android is still an open-source project, after all. But, due to the bundle of proprietary software that comes along with Android on consumer devices, many people don’t consider it an open source operating system. So, what are the alternatives to Android? iOS? Maybe, but I am primarily interested in open-source alternatives to Android. I am going to list not one, not two, but several alternatives, Linux-based mobile OSes . Top Open Source alternatives to Android (and iOS) Let’s see what open source mobile operating systems are available. Just to mention, the list is not in any hierarchical or chronological order . 1. Plasma Mobile. A few years back, KDE announced its open source mobile OS, Plasma Mobile. Plasma Mobile is the mobile version of the desktop Plasma user interface, and aims to provide convergence for KDE users. It is being actively developed, and you can even find PinePhone running on Manjaro ARM while using KDE Plasma Mobile UI if you want to get your hands on a smartphone. 2. postmarketOS. PostmarketOS (pmOS for short) is a touch-optimized, pre-configured Alpine Linux with its own packages, which can be installed on smartphones. The idea is to enable a 10-year life cycle for smartphones. You probably already know that, after a few years, Android and iOS stop providing updates for older smartphones. At the same time, you can run Linux on older computers easily. -

Pinephone User Manual - Quick Start Guide (En)
PINEPHONE USER MANUAL - QUICK START GUIDE (EN) 1 Package contents ● User Manual - Quick Start Guide (x1) ● PinePhone (x1) ● USB-C power cable (x1) 2 Safety precautions and recycling 2.1 Cautions Before using the device please read this manual carefully. Notes for safe operation: ● The PinePhone should be charged using a 15W (5V 3A) USB-PD power adapter. Charging at a higher voltage may result in damage to the device. ● The PinePhone will only operate when its internal temperature is between 5°C and 65°C. It should never be operated with an external temperature lower than -20°C or higher than 40°C. ● Do not puncture, disassemble, strike or squeeze the battery. Old batteries need to be disposed of in accordance with local regulations (see section 2.2). ● Do not expose the device to direct sunlight, water or high levels of humidity. ● In the event of overheating, power off the PinePhone and let it cool for 15 minutes. ● Comply with local regulation pertaining to using mobile devices. This extends to and includes use of the device in public spaces, when operating motor vehicles and heavy machinery. 2.2 Recycling of components and batteries Recycling any PinePhone components should be done according to local regulation. This may require you to dispose of the phone or its parts at a local recycling centre or at a designated container. Please consult local legislation for details. Batteries should never, under any circumstances, be disposed of with general household waste. The end user is legally obliged to return used batteries. Batteries can be returned to us to be disposed of. -

The Complete Freebsd
The Complete FreeBSD® If you find errors in this book, please report them to Greg Lehey <grog@Free- BSD.org> for inclusion in the errata list. The Complete FreeBSD® Fourth Edition Tenth anniversary version, 24 February 2006 Greg Lehey The Complete FreeBSD® by Greg Lehey <[email protected]> Copyright © 1996, 1997, 1999, 2002, 2003, 2006 by Greg Lehey. This book is licensed under the Creative Commons “Attribution-NonCommercial-ShareAlike 2.5” license. The full text is located at http://creativecommons.org/licenses/by-nc-sa/2.5/legalcode. You are free: • to copy, distribute, display, and perform the work • to make derivative works under the following conditions: • Attribution. You must attribute the work in the manner specified by the author or licensor. • Noncommercial. You may not use this work for commercial purposes. This clause is modified from the original by the provision: You may use this book for commercial purposes if you pay me the sum of USD 20 per copy printed (whether sold or not). You must also agree to allow inspection of printing records and other material necessary to confirm the royalty sums. The purpose of this clause is to make it attractive to negotiate sensible royalties before printing. • Share Alike. If you alter, transform, or build upon this work, you may distribute the resulting work only under a license identical to this one. • For any reuse or distribution, you must make clear to others the license terms of this work. • Any of these conditions can be waived if you get permission from the copyright holder. Your fair use and other rights are in no way affected by the above. -

Ubuntu Server CLI Pro Tips
Ubuntu Server CLI pro tips Networking Packages Files Get the IP address of all interfaces Search for packages List files Create directories recursively networkctl status apt search <string> ls mkdir -p <directory1>/<directory2> BASIC snap find <string> Display all IP addresses of the host List files with permissions and dates Delete a directory recursively List available updates hostna m e -I ls -al rm -r <directory> apt list --upgradable Enable/disable interface Apply all available updates Common file operations Quick file search create empty: touch <filename> locate <q> ip link set <interface> up sudo apt update && sudo apt upgrade ip link set <interface> down create with content: echo "<content>" > <filename> Install from the Ubuntu archive: append content: echo "<content>" >> <filename> Search string in file Manage firewall rules sudo apt install <package> display a text file: cat <file> grep <string> <filename> enable firewall: sudo ufw enable copy: cp <file> <target filename> Install from the snap store: move/rename: mv <file> <target directory/filename> Search string recursively in list rules: sudo ufw status sudo snap install <package> delete: rm <file> directory allow port: sudo ufw allow <port> grep -Iris <string> <directory> deny port: sudo ufw deny <port> Which package provides this file? Create a directory sudo apt install apt-file mkdir <directory> Connect remotely through SSH sudo apt-file update ssh <user>@<host IP> apt-file <filename or command> Security Ubuntu release cadence Show which users are logged in Automatically -

Filesystem Hierarchy Standard
Filesystem Hierarchy Standard Filesystem Hierarchy Standard Group Edited by Rusty Russell Daniel Quinlan Filesystem Hierarchy Standard by Filesystem Hierarchy Standard Group Edited by Rusty Russell and Daniel Quinlan Published November 4 2003 Copyright © 1994-2003 Daniel Quinlan Copyright © 2001-2003 Paul ’Rusty’ Russell Copyright © 2003 Christopher Yeoh This standard consists of a set of requirements and guidelines for file and directory placement under UNIX-like operating systems. The guidelines are intended to support interoperability of applications, system administration tools, development tools, and scripts as well as greater uniformity of documentation for these systems. All trademarks and copyrights are owned by their owners, unless specifically noted otherwise. Use of a term in this document should not be regarded as affecting the validity of any trademark or service mark. Permission is granted to make and distribute verbatim copies of this standard provided the copyright and this permission notice are preserved on all copies. Permission is granted to copy and distribute modified versions of this standard under the conditions for verbatim copying, provided also that the title page is labeled as modified including a reference to the original standard, provided that information on retrieving the original standard is included, and provided that the entire resulting derived work is distributed under the terms of a permission notice identical to this one. Permission is granted to copy and distribute translations of this standard into another language, under the above conditions for modified versions, except that this permission notice may be stated in a translation approved by the copyright holder. Table of Contents 1. Introduction........................................................................................................................................................1 1.1.