Belkasoft Evidence Center X User Reference Contents About
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Tracking an RGB-D Camera on Mobile Devices Using an Improved Frame-To-Frame Pose Estimation Method
Tracking an RGB-D Camera on Mobile Devices Using an Improved Frame-to-Frame Pose Estimation Method Jaepung An∗ Jaehyun Lee† Jiman Jeong† Insung Ihm∗ ∗Department of Computer Science and Engineering †TmaxOS Sogang University, Korea Korea fajp5050,[email protected] fjaehyun lee,jiman [email protected] Abstract tion between two time frames. For effective pose estima- tion, several different forms of error models to formulate a The simple frame-to-frame tracking used for dense vi- cost function were proposed independently in 2011. New- sual odometry is computationally efficient, but regarded as combe et al. [11] used only geometric information from rather numerically unstable, easily entailing a rapid accu- input depth images to build an effective iterative closest mulation of pose estimation errors. In this paper, we show point (ICP) model, while Steinbrucker¨ et al. [14] and Au- that a cost-efficient extension of the frame-to-frame tracking dras et al. [1] minimized a cost function based on photo- can significantly improve the accuracy of estimated camera metric error. Whereas, Tykkal¨ a¨ et al. [17] used both geo- poses. In particular, we propose to use a multi-level pose metric and photometric information from the RGB-D im- error correction scheme in which the camera poses are re- age to build a bi-objective cost function. Since then, sev- estimated only when necessary against a few adaptively se- eral variants of optimization models have been developed lected reference frames. Unlike the recent successful cam- to improve the accuracy of pose estimation. Except for the era tracking methods that mostly rely on the extra comput- KinectFusion method [11], the initial direct dense methods ing time and/or memory space for performing global pose were applied to the framework of frame-to-frame tracking optimization and/or keeping accumulated models, the ex- that estimates the camera poses by repeatedly registering tended frame-to-frame tracking requires to keep only a few the current frame against the last frame. -

Product ID Product Type Product Description Notes Price (USD) Weight (KG) SKU 10534 Mobile-Phone Apple Iphone 4S 8GB White 226.8
Rm A1,10/F, Shun Luen Factory Building, 86 Tokwawan Road, Hong Kong TEL: +852 2325 1867 FAX: +852 23251689 Website: http://www.ac-electronic.com/ For products not in our pricelist, please contact our sales. 29/8/2015 Product Price Weight Product Type Product Description Notes SKU ID (USD) (KG) 10534 mobile-phone Apple iPhone 4S 8GB White 226.8 0.5 40599 10491 mobile-phone Apple iPhone 5s 16GB Black Slate 486.4 0.5 40557 10497 mobile-phone Apple iPhone 5s 16GB Gold 495.6 0.5 40563 10494 mobile-phone Apple iPhone 5s 16GB White Silver 487.7 0.5 40560 10498 mobile-phone Apple iPhone 5s 32GB Gold 536.3 0.5 40564 11941 mobile-phone Apple iPhone 6 128GB Gold 784.1 0.5 41970 11939 mobile-phone Apple iPhone 6 16GB Gold 622.8 0.5 41968 11936 mobile-phone Apple iPhone 6 16GB Silver 633.3 0.5 41965 11942 mobile-phone Apple iPhone 6 16GB Space Grey 618.9 0.5 41971 11940 mobile-phone Apple iPhone 6 64GB Gold 705.4 0.5 41969 11937 mobile-phone Apple iPhone 6 64GB Silver 706.7 0.5 41966 11943 mobile-phone Apple iPhone 6 64GB Space Grey 708 0.5 41972 11963 mobile-phone Apple iPhone 6 Plus 128GB Silver 917.9 1 41991 11955 mobile-phone Apple iPhone 6 Plus 16GB Gold 755.3 1 41983 11961 mobile-phone Apple iPhone 6 Plus 16GB Silver 731.6 1 41989 11958 mobile-phone Apple iPhone 6 Plus 16GB Space Grey 735.6 1 41986 11956 mobile-phone Apple iPhone 6 Plus 64GB Gold 843.1 1 41984 11962 mobile-phone Apple iPhone 6 Plus 64GB Silver 841.8 1 41990 11959 mobile-phone Apple iPhone 6 Plus 64GB Space Grey 840.5 1 41987 12733 mobile-phone ASUS ZenFone 2 ZE550ML Dual SIM -

Plug and Play LOGISTICS DATA
PRODUCT DATA Plug and play PRODUCT DATA Type: USB-C to socket adapter for headphones Contact (other enda): Mini-phone stereo 3.5mm female Connection: USB-C male, 3.5mm 4-pin stereo female Cable length: 10 cm Colour: white LOGISTICS DATA Article number: USBC-1145 Brand: DELTACO EAN Code: 7333048043306 Country of origin: China Custom tariff number: 85444290 Master carton packing unit: 40 pcs Master carton gross weight: 2 kg Master carton dimensions: 290x270x280 mm Package type: Box Package weight: 0.03 kg Package dimensions: 120x22x120 mm Article weight: 0.004 kg Article dimensions: 116.45 x 11.3 x 6 mm USBC-1145 compatibility list AUDIO (if device supports HEADSET BUTTON CONTROL (if device Brand Model CALL audio) supports) APPLE Ipad 2018 Pro Works Works Not avaiable Blackberry Blackberry KEYone Works Works Works Google Google Pixel2 Works Works Works Google Google Pixel 1 Works Works Works HTC HTC U11+ Works Works Works HTC HTC ULTRA Works Works Doesn’t work HUAWEI HUAWEI P20 Works Works Works HUAWEI HUAWEI MATE RS Works Works Works HUAWEI HUAWEI MATE 10 PRO Works Works Works HUAWEI HUAWEI Honor Play Works Works Works HUAWEI HUAWEI Mate 9 Pro High Spec Ver Works Works Doesn’t work HUAWEI HUAWEI Honor V9 Works Works Doesn’t work BRAND MODEL AUDIO HEADSET BUTTON CONTROL CALL HUAWEI HUAWEI P10 Plus Works Works Doesn’t work HUAWEIHUAWEI HUAWEIHuawei Honor Mate 9 10 / Mate 10 Pro Works Works WorksWorks Doesn’t workWorks HUAWEI HUAWEIHuawei Nova 2 Mate 20 Pro WorksWorks WorksWorks Doesn’t workWorks HUAWEI HUAWEI NovaP20 2 Plus / P20 Pro WorksWorks -

Nokia 2 Udhëzues Përdorues Pdfdisplaydoctitle=True Pdflang=Sq
Nokia 2 Udhëzues Përdorues Botimi 2020-03-17 sq Nokia 2 Udhëzues Përdorues 1 Mbi këtë udhëzues përdorimi E rëndësishme: Për informacione të rëndësishme për përdorimin e sigurt të pajisjes dhe baterisë tuaj, lexoni informacionet “Për sigurinë tuaj” dhe “Siguria e produktit” në udhëzuesin e printuar të përdorimit ose në www.nokia.com/support para se ta përdorni pajisjen. Për të mësuar se si të filloni me pajisjen tuaj të re, lexoni udhëzuesin e printuar të përdorimit. © 2019 HMD Global Oy. Të gjitha të drejtat të rezervuara. 2 Nokia 2 Udhëzues Përdorues Indeksi 1 Mbi këtë udhëzues përdorimi 2 2 Indeksi 3 3 Get started 6 Keys and parts .......................................... 6 Insert or remove SIM and memory card ............................ 7 Charge your phone ....................................... 8 Switch on and set up your phone ................................ 8 Dual SIM settings ........................................ 9 Lock or unlock your phone ................................... 10 Use the touch screen ...................................... 10 4 Basics 14 Personalize your phone ..................................... 14 Open and close an app ..................................... 14 Notifications ........................................... 15 Control volume .......................................... 15 Screenshots ........................................... 16 Battery life ............................................ 16 Save on data roaming costs .................................. 17 Write text ............................................ -

Poza Promocją) Wersja Z Dnia 27/04/2021 R
Ceny urządzeń telekomunikacyjnych i innych towarów na warunkach ogólnych (poza promocją) Wersja z dnia 27/04/2021 r. obowiązująca do odwołania lub do wyczerpania stanów magazynowych Polkomtel sp. z o.o. Nazwa urządzenia Cena w zł netto Cena w zł brutto Apple iPhone 7 128GB (odnowiony) 1406,50 1730,00 Apple iPhone 8 64GB (odnowiony) 1650,41 2030,00 Apple iPhone 11 128GB 3439,02 4230,00 Apple iPhone 11 Pro 256GB 5186,99 6380,00 DOOGEE S40 487,80 600,00 Fiat F500-F85 1463,41 1800,00 HTC U12+ 1650,41 2030,00 HUAWEI Mate 20 Dual SIM 1650,41 2030,00 HUAWEI Mate 20 Lite Dual SIM 1000,00 1230,00 HUAWEI Mate 30 PRO 256GB 2463,41 3030,00 HUAWEI Mate 40 Pro 5G 4414,63 5430,00 HUAWEI Mate Xs 512GB 5G 7341,46 9030,00 HUAWEI Mini Speaker 80,49 99,00 HUAWEI Mini Speaker 2 pack 161,79 199,00 Huawei Nova 5T 1243,90 1530,00 HUAWEI P smart 2021 128GB 593,50 730,00 HUAWEI P Smart 2021 NFC 128GB 593,50 730,00 HUAWEI P Smart PRO 918,70 1130,00 Huawei P Smart Z 674,80 830,00 Huawei P30 Lite 1040,65 1280,00 Huawei P30 1813,01 2230,00 Huawei P30 PRO 2747,97 3380,00 HUAWEI P30 Pro 128GB 2382,11 2930,00 HUAWEI P40 128GB 5G 2463,41 3030,00 HUAWEI P40 PRO 256GB 5G 3276,42 4030,00 HUAWEI P40 Lite 128GB 837,40 1030,00 HUAWEI P40 Lite 128GB 5G 1325,20 1630,00 HUAWEI Y5 2019 390,24 480,00 HUAWEI Y5p 32GB 349,59 430,00 HUAWEI Y6s 552,85 680,00 HUAWEI Y6p 64GB 512,20 630,00 Instax mini 9 308,94 380,00 JBL Głośnik Mobilny Link Portable 577,24 710,00 LG G8s ThinQ 2138,21 2630,00 LG G8X ThinQ 2626,02 3230,00 LG K22 430,89 530,00 LG K40 430,89 530,00 LG K40s 430,89 530,00 LG K41S 593,50 730,00 LG K42 699,19 860,00 LG K50 756,10 930,00 LG K50S 593,50 730,00 LG K51S 796,75 980,00 LG K52 837,40 1030,00 LG K61 878,05 1080,00 POLKOMTEL sp. -

Lowe's Bets on Augmented Reality by April Berthene
7 » LOWE'S BETS ON AUGMENTED REALITY In testing two augmented reality mobile apps, the home improvement retail chain aims to position Lowe's as a technology leader. Home improvement retailer Lowe's launched an augmented reality app that allows shoppers to visualize products in their home. Lowe's bets on augmented reality By April Berthene owe's Cos. Inc. wants to In-Store Navigation app, helps measure spaces, has yet to be be ready when augmented shoppers navigate the retailer's widely adopted; the Lenovo Phab 2 reality hits the mainstream. large stores, which average 112,000 Pro is the only consumer device that That's why the home square feet. hasTango. improvement retail chain The retailer's new technology In testing two different aug• Lrecently began testing two and development team, Lowe's mented reality apps, Lowe's seeks consumer-facing augmented Innovation Labs, developed the to position its brand as a leader as reality mobile apps. Lowe's Vision apps that rely on Google's Tango the still-new technology becomes allows shoppers to see how Lowe's technology. The nascent Tango more common. About 30.7 million products look in their home, while technology, which uses several consumers used augmented reality the other app, The Lowe's Vision: depth sensing cameras to accurately at least once per month in 2016 and 1ULY2017 | WWW.INTERNETRETAILER.COM LOWE'S BETS ON AUGMENTED REALITY that number is expected to grow 30.3% this year to 40.0 million, according to estimates by research firm eMarketer Inc. The Lowe's Vision app, which launched last November, allows consumers to use their smartphones to see how Lowe's products look in their home, says Kyle Nel, executive director at Lowe's Innovation Labs. -

Cennik Urządzeń W Ofercie Nowa Formuła MIX Przy Sprzedaży Na Odległość
MIX Cennik urządzeń w Ofercie Nowa Formuła MIX przy sprzedaży na odległość Obowiązuje od dnia 25.01.2021 do wyczerpania stanów magazynowych objętych niniejszym Cennikiem lub jego odwołania. Nowa Formuła MIX Nowa Elastyczna Formuła MIX Model Nowa Formuła Nowa Formuła Nowa Formuła Nowa Formuła Nowa Elastyczna Formuła Nowa Elastyczna Formuła Nowa Elastyczna Formuła MIX XS MIX S MIX M MIX L MIX S MIX M MIX L Alcatel 1S 2020 199 119 39 1 1 1 1 Alcatel 30.25 1 1 1 1 1 1 1 Hammer 5 Smart 79 1 1 1 1 1 1 Hammer Energy 2 339 259 179 99 139 19 1 Honor 9X 349 269 189 109 149 29 1 HTC Desire 20 Pro 739 659 579 499 539 419 299 Huawei AM115 1 1 1 1 1 1 1 Huawei Band 4 Pro 39 1 1 1 1 1 1 Huawei Band 4e 1 1 1 1 1 1 1 Huawei MediaPad T3 10 LTE 389 319 239 159 199 79 1 Huawei Mini Speaker CM510 1 1 1 1 1 1 1 Huawei P smart 2021 429 349 269 199 239 119 1 Huawei P30 Lite 699 629 549 469 499 389 269 Huawei P40 lite 699 619 539 459 499 379 259 Huawei P40 lite E 159 79 1 1 1 1 1 Huawei Y5p 79 1 1 1 1 1 1 Huawei Y6p 299 219 139 59 99 1 1 iPhone SE (2020) 128GB 2229 2149 2069 1989 2029 1909 1789 iPhone SE (2020) 64GB 1799 1719 1639 1559 1599 1479 1359 P4 Sp. -

Totalmem),Form Factor,System on Chip,Screen Sizes,Screen Densities,Abis,Android SDK Versions,Opengl ES Versions
Manufacturer,Model Name,Model Code,RAM (TotalMem),Form Factor,System on Chip,Screen Sizes,Screen Densities,ABIs,Android SDK Versions,OpenGL ES Versions 10.or,E,E,2846MB,Phone,Qualcomm MSM8937,1080x1920,480,arm64-v8a 10.or,G,G,3603MB,Phone,Qualcomm MSM8953,1080x1920,480,arm64-v8a 10.or,D,10or_D,2874MB,Phone,Qualcomm MSM8917,720x1280,320,arm64-v8a 4good,A103,4GOOD_Light_A103,907MB,Phone,Mediatek MT6737M,540x960,240,armeabi- v7a 4good,4GOOD Light B100,4GOOD_Light_B100,907MB,Phone,Mediatek MT6737M,540x960,240,armeabi-v7a 7Eleven,IN265,IN265,466MB,Phone,Mediatek MT6572,540x960,240,armeabi-v7a 7mobile,DRENA,DRENA,925MB,Phone,Spreadtrum SC7731C,480x800,240,armeabi-v7a 7mobile,KAMBA,KAMBA,1957MB,Phone,Mediatek MT6580,720x1280,320,armeabi-v7a 7mobile,SWEGUE,SWEGUE,1836MB,Phone,Mediatek MT6737T,1080x1920,480,arm64-v8a A.O.I. ELECTRONICS FACTORY,A.O.I.,TR10CS1_11,965MB,Tablet,Intel Z2520,1280x800,160,x86 Aamra WE,E2,E2,964MB,Phone,Mediatek MT6580,480x854,240,armeabi-v7a Accent,Pearl_A4,Pearl_A4,955MB,Phone,Mediatek MT6580,720x1440,320,armeabi-v7a Accent,FAST7 3G,FAST7_3G,954MB,Tablet,Mediatek MT8321,720x1280,160,armeabi-v7a Accent,Pearl A4 PLUS,PEARL_A4_PLUS,1929MB,Phone,Mediatek MT6737,720x1440,320,armeabi-v7a Accent,SPEED S8,SPEED_S8,894MB,Phone,Mediatek MT6580,720x1280,320,armeabi-v7a Acegame S.A. -
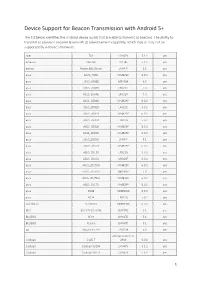
Device Support for Beacon Transmission with Android 5+
Device Support for Beacon Transmission with Android 5+ The list below identifies the Android device builds that are able to transmit as beacons. The ability to transmit as a beacon requires Bluetooth LE advertisement capability, which may or may not be supported by a device’s firmware. Acer T01 LMY47V 5.1.1 yes Amazon KFFOWI LVY48F 5.1.1 yes archos Archos 80d Xenon LMY47I 5.1 yes asus ASUS_T00N MMB29P 6.0.1 yes asus ASUS_X008D MRA58K 6.0 yes asus ASUS_Z008D LRX21V 5.0 yes asus ASUS_Z00AD LRX21V 5.0 yes asus ASUS_Z00AD MMB29P 6.0.1 yes asus ASUS_Z00ED LRX22G 5.0.2 yes asus ASUS_Z00ED MMB29P 6.0.1 yes asus ASUS_Z00LD LRX22G 5.0.2 yes asus ASUS_Z00LD MMB29P 6.0.1 yes asus ASUS_Z00UD MMB29P 6.0.1 yes asus ASUS_Z00VD LMY47I 5.1 yes asus ASUS_Z010D MMB29P 6.0.1 yes asus ASUS_Z011D LRX22G 5.0.2 yes asus ASUS_Z016D MXB48T 6.0.1 yes asus ASUS_Z017DA MMB29P 6.0.1 yes asus ASUS_Z017DA NRD90M 7.0 yes asus ASUS_Z017DB MMB29P 6.0.1 yes asus ASUS_Z017D MMB29P 6.0.1 yes asus P008 MMB29M 6.0.1 yes asus P024 LRX22G 5.0.2 yes blackberry STV100-3 MMB29M 6.0.1 yes BLU BLU STUDIO ONE LMY47D 5.1 yes BLUBOO XFire LMY47D 5.1 yes BLUBOO Xtouch LMY47D 5.1 yes bq Aquaris E5 HD LRX21M 5.0 yes ZBXCNCU5801712 Coolpad C106-7 291S 6.0.1 yes Coolpad Coolpad 3320A LMY47V 5.1.1 yes Coolpad Coolpad 3622A LMY47V 5.1.1 yes 1 CQ CQ-BOX 2.1.0-d158f31 5.1.1 yes CQ CQ-BOX 2.1.0-f9c6a47 5.1.1 yes DANY TECHNOLOGIES HK LTD Genius Talk T460 LMY47I 5.1 yes DOOGEE F5 LMY47D 5.1 yes DOOGEE X5 LMY47I 5.1 yes DOOGEE X5max MRA58K 6.0 yes elephone Elephone P7000 LRX21M 5.0 yes Elephone P8000 -

Microsoft 2012 Citizenship Report
Citizenship at Microsoft Our Company Serving Communities Working Responsibly About this Report Microsoft 2012 Citizenship Report Microsoft 2012 Citizenship Report 01 Contents Citizenship at Microsoft Serving Communities Working Responsibly About this Report 3 Serving communities 14 Creating opportunities for youth 46 Our people 85 Reporting year 4 Working responsibly 15 Empowering youth through 47 Compensation and benefits 85 Scope 4 Citizenship governance education and technology 48 Diversity and inclusion 85 Additional reporting 5 Setting priorities and 16 Inspiring young imaginations 50 Training and development 85 Feedback stakeholder engagement 18 Realizing potential with new skills 51 Health and safety 86 United Nations Global Compact 5 External frameworks 20 Supporting youth-focused 53 Environment 6 FY12 highlights and achievements nonprofits 54 Impact of our operations 23 Empowering nonprofits 58 Technology for the environment 24 Donating software to nonprofits Our Company worldwide 61 Human rights 26 Providing hardware to more people 62 Affirming our commitment 28 Sharing knowledge to build capacity 64 Privacy and data security 8 Our business 28 Solutions in action 65 Online safety 8 Where we are 67 Freedom of expression 8 Engaging our customers 31 Employee giving and partners 32 Helping employees make 69 Responsible sourcing 10 Our products a difference 71 Hardware production 11 Investing in innovation 73 Conflict minerals 36 Humanitarian response 74 Expanding our efforts 37 Providing assistance in times of need 76 Governance 40 Accessibility 77 Corporate governance 41 Empowering people with disabilities 79 Maintaining strong practices and performance 42 Engaging students with special needs 80 Public policy engagement 44 Improving seniors’ well-being 83 Compliance Cover: Participants at the 2012 Imagine Cup, Sydney, Australia. -

Аксессуары В Подарок При Покупке Huawei Nova 2I» Список Товара 2, Участвующего В Акции
Приложение 2 к Правилам Акции «Аксессуары в подарок при покупке Huawei Nova 2i» Список Товара 2, участвующего в Акции Артикул Наименование 0315-2319 Брелок Brillstone Кошка в сердце (21) золото 0313-2121 Чехол-кейс Clever ультратонкий Lumia 520 прозрачный 0313-2663 Чехол-книжка Gresso МТС Smart Sprint 4,5” Канцлер красный 0313-1728 Чехол-кейс Nokia Lumia 820 CC-3058 (Original) черный 0313-2996 Чехол-книжка Muvit Slim S Folio Sony Xperia M4 Aqua черный 0313-2631 Клип-кейс RedLine iBox Fresh Samsung G313 Galaxy Ace 4 DS белый 0313-1443 Сумка RedPoint кроко прайм XL 0400-0913 Чехол Sumdex ST3-820 BK Samsung Galaxy Tab 3 8" черный 0317-0679 Пленка защитная RedLine Sony Xperia Z3 матовая 0305-1162 USB Flash EMTEC 32Gb USB3.0/Lightning 8-pin iCobra2 (ECMMD32GT503V2B) черная 0305-0222 Карта памяти MS Micro M2 SanDisk 4Gb 0313-3178 Чехол-книжка Arvy универсальный размер M принт 190 0313-3363 Клип-кейс Deppa iPhone 6 Plus Black Коршун 0313-3367 Клип-кейс Deppa iPhone 6 Plus Military Бабочки 2 0313-4214 Клип-кейс RedLine Crystal Lenovo A2010 прозрачный 0400-1079 Чехол-книжка Clever SuperSlim Samsung Galaxy Tab S2 8 красный 0400-0902 Чехол-книжка iBox Premium Samsung Galaxy Tab S 10.5 черный 0313-3059 Клип-кейс Deppa Air Case Samsung I9300 Galaxy S3 мятный 0313-3061 Клип-кейс Deppa Air Case Samsung I9300 Galaxy S3 черный 0400-1080 Чехол-книжка Clever SuperSlim Samsung Galaxy Tab S2 8 черный 0202-0347 MP3-плеер teXet T-979HD 4Гб/TFT 4,3" черный 0307-0185 Дата-кабель Gal 2604 USB - microUSB 2.0 1м оранжевый 0313-3516 Чехол-книжка Puro Samsung Galaxy -

Pesona Edan Flagship Gres Review Pete Lau
Edisi Agustus 2018 www.sinyalmagz.com REVIEW ONEPLUS 6 PESONA EDAN FLAGSHIP GRES PETE LAU, BOS ONEPLUS BICARA TEKNOLOGI PAKET TELKO HAJI INDOSAT OOREDOO Hal 1 DI009DAFTAR ISI: EDITORIAL Rayakan Pesta Olahraga Asia .............................10 Bulan Agustus selain perayaan HUT Kemerdekaan RI ke 73, kita akan disuguhi oleh pergelaran olahraga se-Asia, Asian Games ke 18. Ini untuk kedua kalinya Indonesia mendapat kehormatan setelah 56 tahun silam digelar di Jakarta, tepatnya pada 1962 ketika Soekarno masih menjabat sebagai presiden. DI011 DI011 KOLOM HENDROWIJONO Bijaksana Bermedsos Jelang Pemilu ..................12 TENSI politik naik setiap menjelang pemilu, baik pemi- lihan anggota legislatif, kepala daerah, dan terutama pemilihan presiden merupakan hal yang mirip dari masa ke masa. Hal 2 DI017 DI015 KABAR OPERATOR INDOSAT OOREDOO TAWARKAN PAKET KOMUNIKASI HAJI ..............................................16 Menjelang pelaksanaan ibadah haji yang akan diikuti oleh lebih dari 200 ribu jamaah dari Indonesia, Indos- at Ooredoo telah menyiapkan paket untuk telekomu- nikasi. Paket tersebut bervariasi mulai layanan tele- foni, SMS dan paket data. DI018 INDOSAT OOREDOO BUSINESS TAWARKAN IoT CONNECT ............................................................19 DI022 AXIS GELAR KOMPETISI E-SPORT DI INDONESIA ....................................................23 DI025 TELKOMSEL LUNCURKAN TELKOMSEL INNOVATION CENTER .........................................26 DI029 XL AXIATA PERKETAT INFORMASI DATA PELANGGAN .......................................................30