Prime Numbers and Discrete Logarithms
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Enigmatic Number E: a History in Verse and Its Uses in the Mathematics Classroom
To appear in MAA Loci: Convergence The Enigmatic Number e: A History in Verse and Its Uses in the Mathematics Classroom Sarah Glaz Department of Mathematics University of Connecticut Storrs, CT 06269 [email protected] Introduction In this article we present a history of e in verse—an annotated poem: The Enigmatic Number e . The annotation consists of hyperlinks leading to biographies of the mathematicians appearing in the poem, and to explanations of the mathematical notions and ideas presented in the poem. The intention is to celebrate the history of this venerable number in verse, and to put the mathematical ideas connected with it in historical and artistic context. The poem may also be used by educators in any mathematics course in which the number e appears, and those are as varied as e's multifaceted history. The sections following the poem provide suggestions and resources for the use of the poem as a pedagogical tool in a variety of mathematics courses. They also place these suggestions in the context of other efforts made by educators in this direction by briefly outlining the uses of historical mathematical poems for teaching mathematics at high-school and college level. Historical Background The number e is a newcomer to the mathematical pantheon of numbers denoted by letters: it made several indirect appearances in the 17 th and 18 th centuries, and acquired its letter designation only in 1731. Our history of e starts with John Napier (1550-1617) who defined logarithms through a process called dynamical analogy [1]. Napier aimed to simplify multiplication (and in the same time also simplify division and exponentiation), by finding a model which transforms multiplication into addition. -

Exponent and Logarithm Practice Problems for Precalculus and Calculus
Exponent and Logarithm Practice Problems for Precalculus and Calculus 1. Expand (x + y)5. 2. Simplify the following expression: √ 2 b3 5b +2 . a − b 3. Evaluate the following powers: 130 =,(−8)2/3 =,5−2 =,81−1/4 = 10 −2/5 4. Simplify 243y . 32z15 6 2 5. Simplify 42(3a+1) . 7(3a+1)−1 1 x 6. Evaluate the following logarithms: log5 125 = ,log4 2 = , log 1000000 = , logb 1= ,ln(e )= 1 − 7. Simplify: 2 log(x) + log(y) 3 log(z). √ √ √ 8. Evaluate the following: log( 10 3 10 5 10) = , 1000log 5 =,0.01log 2 = 9. Write as sums/differences of simpler logarithms without quotients or powers e3x4 ln . e 10. Solve for x:3x+5 =27−2x+1. 11. Solve for x: log(1 − x) − log(1 + x)=2. − 12. Find the solution of: log4(x 5)=3. 13. What is the domain and what is the range of the exponential function y = abx where a and b are both positive constants and b =1? 14. What is the domain and what is the range of f(x) = log(x)? 15. Evaluate the following expressions. (a) ln(e4)= √ (b) log(10000) − log 100 = (c) eln(3) = (d) log(log(10)) = 16. Suppose x = log(A) and y = log(B), write the following expressions in terms of x and y. (a) log(AB)= (b) log(A) log(B)= (c) log A = B2 1 Solutions 1. We can either do this one by “brute force” or we can use the binomial theorem where the coefficients of the expansion come from Pascal’s triangle. -

Lecture 9: Arithmetics II 1 Greatest Common Divisor
DD2458, Problem Solving and Programming Under Pressure Lecture 9: Arithmetics II Date: 2008-11-10 Scribe(s): Marcus Forsell Stahre and David Schlyter Lecturer: Douglas Wikström This lecture is a continuation of the previous one, and covers modular arithmetic and topics from a branch of number theory known as elementary number theory. Also, some abstract algebra will be discussed. 1 Greatest Common Divisor Definition 1.1 If an integer d divides another integer n with no remainder, d is said to be a divisor of n. That is, there exists an integer a such that a · d = n. The notation for this is d | n. Definition 1.2 A common divisor of two non-zero integers m and n is a positive integer d, such that d | m and d | n. Definition 1.3 The Greatest Common Divisor (GCD) of two positive integers m and n is a common divisor d such that every other common divisor d0 | d. The notation for this is GCD(m, n) = d. That is, the GCD of two numbers is the greatest number that is a divisor of both of them. To get an intuition of what GCD is, let’s have a look at this example. Example Calculate GCD(9, 6). Say we have 9 black and 6 white blocks. We want to put the blocks in boxes, but every box has to be the same size, and can only hold blocks of the same color. Also, all the boxes must be full and as large as possible . Let’s for example say we choose a box of size 2: As we can see, the last box of black bricks is not full. -

Primality Testing and Integer Factorisation
Primality Testing and Integer Factorisation Richard P. Brent, FAA Computer Sciences Laboratory Australian National University Canberra, ACT 2601 Abstract The problem of finding the prime factors of large composite numbers has always been of mathematical interest. With the advent of public key cryptosystems it is also of practical importance, because the security of some of these cryptosystems, such as the Rivest-Shamir-Adelman (RSA) system, depends on the difficulty of factoring the public keys. In recent years the best known integer factorisation algorithms have improved greatly, to the point where it is now easy to factor a 60-decimal digit number, and possible to factor numbers larger than 120 decimal digits, given the availability of enough computing power. We describe several recent algorithms for primality testing and factorisation, give examples of their use and outline some applications. 1. Introduction It has been known since Euclid’s time (though first clearly stated and proved by Gauss in 1801) that any natural number N has a unique prime power decomposition α1 α2 αk N = p1 p2 ··· pk (1.1) αj (p1 < p2 < ··· < pk rational primes, αj > 0). The prime powers pj are called αj components of N, and we write pj kN. To compute the prime power decomposition we need – 1. An algorithm to test if an integer N is prime. 2. An algorithm to find a nontrivial factor f of a composite integer N. Given these there is a simple recursive algorithm to compute (1.1): if N is prime then stop, otherwise 1. find a nontrivial factor f of N; 2. -

An Analysis of Primality Testing and Its Use in Cryptographic Applications
An Analysis of Primality Testing and Its Use in Cryptographic Applications Jake Massimo Thesis submitted to the University of London for the degree of Doctor of Philosophy Information Security Group Department of Information Security Royal Holloway, University of London 2020 Declaration These doctoral studies were conducted under the supervision of Prof. Kenneth G. Paterson. The work presented in this thesis is the result of original research carried out by myself, in collaboration with others, whilst enrolled in the Department of Mathe- matics as a candidate for the degree of Doctor of Philosophy. This work has not been submitted for any other degree or award in any other university or educational establishment. Jake Massimo April, 2020 2 Abstract Due to their fundamental utility within cryptography, prime numbers must be easy to both recognise and generate. For this, we depend upon primality testing. Both used as a tool to validate prime parameters, or as part of the algorithm used to generate random prime numbers, primality tests are found near universally within a cryptographer's tool-kit. In this thesis, we study in depth primality tests and their use in cryptographic applications. We first provide a systematic analysis of the implementation landscape of primality testing within cryptographic libraries and mathematical software. We then demon- strate how these tests perform under adversarial conditions, where the numbers being tested are not generated randomly, but instead by a possibly malicious party. We show that many of the libraries studied provide primality tests that are not pre- pared for testing on adversarial input, and therefore can declare composite numbers as being prime with a high probability. -

Primes and Primality Testing
Primes and Primality Testing A Technological/Historical Perspective Jennifer Ellis Department of Mathematics and Computer Science What is a prime number? A number p greater than one is prime if and only if the only divisors of p are 1 and p. Examples: 2, 3, 5, and 7 A few larger examples: 71887 524287 65537 2127 1 Primality Testing: Origins Eratosthenes: Developed “sieve” method 276-194 B.C. Nicknamed Beta – “second place” in many different academic disciplines Also made contributions to www-history.mcs.st- geometry, approximation of andrews.ac.uk/PictDisplay/Eratosthenes.html the Earth’s circumference Sieve of Eratosthenes 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 Sieve of Eratosthenes We only need to “sieve” the multiples of numbers less than 10. Why? (10)(10)=100 (p)(q)<=100 Consider pq where p>10. Then for pq <=100, q must be less than 10. By sieving all the multiples of numbers less than 10 (here, multiples of q), we have removed all composite numbers less than 100. -

Efficient Regular Modular Exponentiation Using
J Cryptogr Eng (2017) 7:245–253 DOI 10.1007/s13389-016-0134-5 SHORT COMMUNICATION Efficient regular modular exponentiation using multiplicative half-size splitting Christophe Negre1,2 · Thomas Plantard3,4 Received: 14 August 2015 / Accepted: 23 June 2016 / Published online: 13 July 2016 © Springer-Verlag Berlin Heidelberg 2016 Abstract In this paper, we consider efficient RSA modular x K mod N where N = pq with p and q prime. The private exponentiations x K mod N which are regular and con- data are the two prime factors of N and the private exponent stant time. We first review the multiplicative splitting of an K used to decrypt or sign a message. In order to insure a integer x modulo N into two half-size integers. We then sufficient security level, N and K are chosen large enough take advantage of this splitting to modify the square-and- to render the factorization of N infeasible: they are typically multiply exponentiation as a regular sequence of squarings 2048-bit integers. The basic approach to efficiently perform always followed by a multiplication by a half-size inte- the modular exponentiation is the square-and-multiply algo- ger. The proposed method requires around 16% less word rithm which scans the bits ki of the exponent K and perform operations compared to Montgomery-ladder, square-always a sequence of squarings followed by a multiplication when and square-and-multiply-always exponentiations. These the- ki is equal to one. oretical results are validated by our implementation results When the cryptographic computations are performed on which show an improvement by more than 12% compared an embedded device, an adversary can monitor power con- approaches which are both regular and constant time. -

Miller-Rabin Primality Test (Java)
Miller-Rabin primality test (Java) Other implementations: C | C, GMP | Clojure | Groovy | Java | Python | Ruby | Scala The Miller-Rabin primality test is a simple probabilistic algorithm for determining whether a number is prime or composite that is easy to implement. It proves compositeness of a number using the following formulas: Suppose 0 < a < n is coprime to n (this is easy to test using the GCD). Write the number n−1 as , where d is odd. Then, provided that all of the following formulas hold, n is composite: for all If a is chosen uniformly at random and n is prime, these formulas hold with probability 1/4. Thus, repeating the test for k random choices of a gives a probability of 1 − 1 / 4k that the number is prime. Moreover, Gerhard Jaeschke showed that any 32-bit number can be deterministically tested for primality by trying only a=2, 7, and 61. [edit] 32-bit integers We begin with a simple implementation for 32-bit integers, which is easier to implement for reasons that will become apparent. First, we'll need a way to perform efficient modular exponentiation on an arbitrary 32-bit integer. We accomplish this using exponentiation by squaring: Source URL: http://www.en.literateprograms.org/Miller-Rabin_primality_test_%28Java%29 Saylor URL: http://www.saylor.org/courses/cs409 ©Spoon! (http://www.en.literateprograms.org/Miller-Rabin_primality_test_%28Java%29) Saylor.org Used by Permission Page 1 of 5 <<32-bit modular exponentiation function>>= private static int modular_exponent_32(int base, int power, int modulus) { long result = 1; for (int i = 31; i >= 0; i--) { result = (result*result) % modulus; if ((power & (1 << i)) != 0) { result = (result*base) % modulus; } } return (int)result; // Will not truncate since modulus is an int } int is a 32-bit integer type and long is a 64-bit integer type. -

Leonhard Euler: His Life, the Man, and His Works∗
SIAM REVIEW c 2008 Walter Gautschi Vol. 50, No. 1, pp. 3–33 Leonhard Euler: His Life, the Man, and His Works∗ Walter Gautschi† Abstract. On the occasion of the 300th anniversary (on April 15, 2007) of Euler’s birth, an attempt is made to bring Euler’s genius to the attention of a broad segment of the educated public. The three stations of his life—Basel, St. Petersburg, andBerlin—are sketchedandthe principal works identified in more or less chronological order. To convey a flavor of his work andits impact on modernscience, a few of Euler’s memorable contributions are selected anddiscussedinmore detail. Remarks on Euler’s personality, intellect, andcraftsmanship roundout the presentation. Key words. LeonhardEuler, sketch of Euler’s life, works, andpersonality AMS subject classification. 01A50 DOI. 10.1137/070702710 Seh ich die Werke der Meister an, So sehe ich, was sie getan; Betracht ich meine Siebensachen, Seh ich, was ich h¨att sollen machen. –Goethe, Weimar 1814/1815 1. Introduction. It is a virtually impossible task to do justice, in a short span of time and space, to the great genius of Leonhard Euler. All we can do, in this lecture, is to bring across some glimpses of Euler’s incredibly voluminous and diverse work, which today fills 74 massive volumes of the Opera omnia (with two more to come). Nine additional volumes of correspondence are planned and have already appeared in part, and about seven volumes of notebooks and diaries still await editing! We begin in section 2 with a brief outline of Euler’s life, going through the three stations of his life: Basel, St. -

RSA Power Analysis Obfuscation: a Dynamic FPGA Architecture John W
Air Force Institute of Technology AFIT Scholar Theses and Dissertations Student Graduate Works 3-22-2012 RSA Power Analysis Obfuscation: A Dynamic FPGA Architecture John W. Barron Follow this and additional works at: https://scholar.afit.edu/etd Part of the Electrical and Computer Engineering Commons Recommended Citation Barron, John W., "RSA Power Analysis Obfuscation: A Dynamic FPGA Architecture" (2012). Theses and Dissertations. 1078. https://scholar.afit.edu/etd/1078 This Thesis is brought to you for free and open access by the Student Graduate Works at AFIT Scholar. It has been accepted for inclusion in Theses and Dissertations by an authorized administrator of AFIT Scholar. For more information, please contact [email protected]. RSA POWER ANALYSIS OBFUSCATION: A DYNAMIC FPGA ARCHITECTURE THESIS John W. Barron, Captain, USAF AFIT/GE/ENG/12-02 DEPARTMENT OF THE AIR FORCE AIR UNIVERSITY AIR FORCE INSTITUTE OF TECHNOLOGY Wright-Patterson Air Force Base, Ohio APPROVED FOR PUBLIC RELEASE; DISTRIBUTION UNLIMITED. The views expressed in this thesis are those of the author and do not reflect the official policy or position of the United States Air Force, Department of Defense, or the United States Government. This material is declared a work of the U.S. Government and is not subject to copyright protection in the United States. AFIT/GE/ENG/12-02 RSA POWER ANALYSIS OBFUSCATION: A DYNAMIC FPGA ARCHITECTURE THESIS Presented to the Faculty Department of Electrical and Computer Engineering Graduate School of Engineering and Management Air Force Institute of Technology Air University Air Education and Training Command In Partial Fulfillment of the Requirements for the Degree of Master of Science in Electrical Engineering John W. -
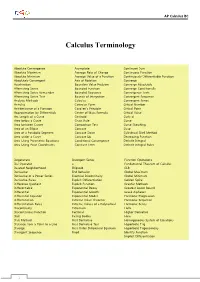
Calculus Terminology
AP Calculus BC Calculus Terminology Absolute Convergence Asymptote Continued Sum Absolute Maximum Average Rate of Change Continuous Function Absolute Minimum Average Value of a Function Continuously Differentiable Function Absolutely Convergent Axis of Rotation Converge Acceleration Boundary Value Problem Converge Absolutely Alternating Series Bounded Function Converge Conditionally Alternating Series Remainder Bounded Sequence Convergence Tests Alternating Series Test Bounds of Integration Convergent Sequence Analytic Methods Calculus Convergent Series Annulus Cartesian Form Critical Number Antiderivative of a Function Cavalieri’s Principle Critical Point Approximation by Differentials Center of Mass Formula Critical Value Arc Length of a Curve Centroid Curly d Area below a Curve Chain Rule Curve Area between Curves Comparison Test Curve Sketching Area of an Ellipse Concave Cusp Area of a Parabolic Segment Concave Down Cylindrical Shell Method Area under a Curve Concave Up Decreasing Function Area Using Parametric Equations Conditional Convergence Definite Integral Area Using Polar Coordinates Constant Term Definite Integral Rules Degenerate Divergent Series Function Operations Del Operator e Fundamental Theorem of Calculus Deleted Neighborhood Ellipsoid GLB Derivative End Behavior Global Maximum Derivative of a Power Series Essential Discontinuity Global Minimum Derivative Rules Explicit Differentiation Golden Spiral Difference Quotient Explicit Function Graphic Methods Differentiable Exponential Decay Greatest Lower Bound Differential -

THE MILLER–RABIN PRIMALITY TEST 1. Fast Modular
THE MILLER{RABIN PRIMALITY TEST 1. Fast Modular Exponentiation Given positive integers a, e, and n, the following algorithm quickly computes the reduced power ae % n. • (Initialize) Set (x; y; f) = (1; a; e). • (Loop) While f > 1, do as follows: { If f%2 = 0 then replace (x; y; f) by (x; y2 % n; f=2), { otherwise replace (x; y; f) by (xy % n; y; f − 1). • (Terminate) Return x. The algorithm is strikingly efficient both in speed and in space. To see that it works, represent the exponent e in binary, say e = 2f + 2g + 2h; 0 ≤ f < g < h: The algorithm successively computes (1; a; 2f + 2g + 2h) f (1; a2 ; 1 + 2g−f + 2h−f ) f f (a2 ; a2 ; 2g−f + 2h−f ) f g (a2 ; a2 ; 1 + 2h−g) f g g (a2 +2 ; a2 ; 2h−g) f g h (a2 +2 ; a2 ; 1) f g h h (a2 +2 +2 ; a2 ; 0); and then it returns the first entry, which is indeed ae. 2. The Fermat Test and Fermat Pseudoprimes Fermat's Little Theorem states that for any positive integer n, if n is prime then bn mod n = b for b = 1; : : : ; n − 1. In the other direction, all we can say is that if bn mod n = b for b = 1; : : : ; n − 1 then n might be prime. If bn mod n = b where b 2 f1; : : : ; n − 1g then n is called a Fermat pseudoprime base b. There are 669 primes under 5000, but only five values of n (561, 1105, 1729, 2465, and 2821) that are Fermat pseudoprimes base b for b = 2; 3; 5 without being prime.