Training: An Introduction to Burp Suite – Part Two By Mike Sheward
Burp Suite provides a solid platform for launching a web application security assessment. This is the second part of our guide introducing the features of Burp and how you can use them to discover web application vulnerabilities.
Burp Repeater
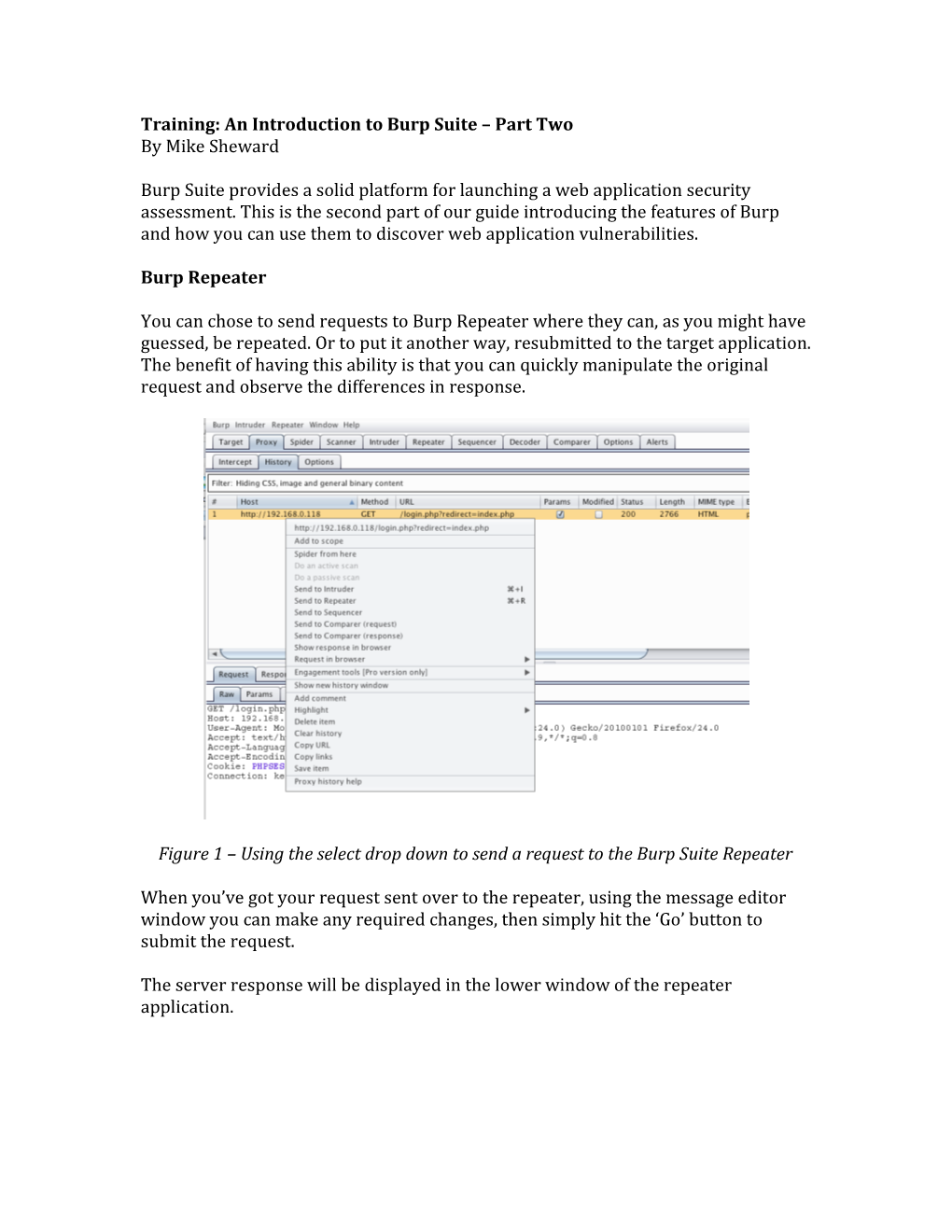
You can chose to send requests to Burp Repeater where they can, as you might have guessed, be repeated. Or to put it another way, resubmitted to the target application. The benefit of having this ability is that you can quickly manipulate the original request and observe the differences in response.
Figure 1 – Using the select drop down to send a request to the Burp Suite Repeater
When you’ve got your request sent over to the repeater, using the message editor window you can make any required changes, then simply hit the ‘Go’ button to submit the request.
The server response will be displayed in the lower window of the repeater application. Figure 2 – A Request and Response Captured by Burp Repeater
You can open multiple repeater sessions within Burp, with each session being contained within its own tab. Using the backwards and forwards arrow buttons you can browse through the history of the requests that have been completed within that repeater session.
Burp Sequencer
Something that appears to be random may actually not be that random at all. The Burp Sequencer tool is designed to detect randomness, which when you are dealing with application components such as security tokens is highly important. If you have a token that appears to be random, but isn’t, this could become a vulnerability.
We’ll demonstrate testing a token for randomness using the sequencer application. In this example we’ll test the randomness of the PHP Session ID set by an example application. The application sets the session ID in a cookie, so the first step is to capture a response from the application that includes the Set-Cookie header.
Figure 3 – A Response that Includes a Set-Cookie header Then, from the proxy history screen in Burp, we use the context menu to send the response to the Sequencer tool. Here, we select the location of the token within the response. In this case, the token is the PHPSESSID cookie.
Figure 4 – Selecting the Token Location in Sequencer
Once we’ve given Burp Sequencer all the required information to find the token, it’s time to start collecting tokens. Hitting the ‘Start Live Capture’ button will begin this process. Burp will start making requests to the application in order to capture multiple tokens, which will be analyzed as part of the randomness calculation. The more tokens you capture, the more accurate the results will be. Figure 5 – Capturing tokens using Burp Sequencer
Once you have collected a reasonable number of tokens (say, 1000), you can pause the live capture and run the analysis using the ‘Analyse Now’ button.
Figure 6 – Reviewing the Results of a Sequencer Test
The results of a sequencer test are displayed in the same window that the live capture statistics were shown, the opening sentence on the summary page will provide you with a plain English description of the test outcome. In this case, ‘the overall quality of randomness within the sample is estimated to be: excellent’. Well, that is excellent news!
It is also possible to review extremely in depth results and information on how the tests were run, and randomness results at the character-level and at the bit-level.
Burp Decoder
The decoder tool is a simple utility that allows you to encode or decode raw data. It sounds basic, and it is, but having a tool that allows you to quickly transform data during a web application assessment is incredibly useful. Simply paste or type the data you wish to encode into the window and select ‘decode as’ or ‘encode as’.
Figure 7 – Burp Decoder
You can also use the tool to generate a hash of the entered data using one of the hashing algorithms listed in the tool.
Burp Comparer
Another simple yet useful tool, Burp Comparer allows you to take two sets of data from anywhere else in the application, and visually compare them side-by-side.
There are many possible uses for this tool. One great example is a username enumeration exercise. If you have a valid username, compare the failed login response to a response for an invalid username. Subtle differences may provide you with all the information you need to build an automated enumeration tool for the target application.
To send data to the comparer, use the ‘send to Comparer’ option on the context menu to send a couple of pieces of data to the tool. Then use the comparer tab to chose which two pieces of data you wish to compare. Figure 8 – Selecting two inputs for the Comparer tool.
You can chose to ‘Compare…’ by words or bytes by selecting the relevant button.
Figure 9 – The results of a comparison.
Conclusion
Over the course of our two-part introduction, we’ve covered the basic tools that make up the core of the Burp Suite platform. These tools give you a great starting point, and are more than enough to start producing some very interesting results. As you become more familiar with Burp, you’ll discover that it’s abilities extend far beyond those offered by the basic functions of the built in tools.
The keyword here is ‘platform’. There are plenty of extensions for Burp that allow you to further enhance its usability.
As with all testing tools, the best way to unlock their value is to practice in a safe testing environment. There are multiple purpose built vulnerable web applications on the internet that you can download for this purpose (have a look at the OWASP Broken Web Applications).
Go forth, and test!