Is Docker Infrastructure Or Platform? & Cloud Foundry Intro
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

WEIYANG (STEPHEN) YUAN [email protected] | Chicago | 608-504-0649 | Stephenyuan.Urspace.Io Education University of Wisconsin-Madison B.S
WEIYANG (STEPHEN) YUAN [email protected] | Chicago | 608-504-0649 | stephenyuan.urspace.io Education University of Wisconsin-Madison B.S. in Computer Engineering May 2020 ● GPA: 3.83/4.0 ● Related Coursework: Operating Systems • A rtificial Intelligence • Computer Networks and Communication • Databases • Information Security • Big Data Systems • Android Mobile Development Skills ● Programming Languages: Java • Golang • C++ • Scala • MATLAB • SQL • Julia • C • Python ● Technologies: Git, Linux, Java Spring, Amazon Web Services (AWS), MongoDB, Postgres, React, Node.js, Docker, Jenkins, Play Framework, Hadoop, Spark, Wireshark, Visual Studio Experience Enfusion, Chicago Java Software Developer July 2020 - Current ● Develop the portfolio management software system used by over 500 clients that supports a variety of financial calculation and valuation over 20 financial derivatives as well as back office general ledger and cash flow with more than 10,000 daily positions on average ● Take responsibility in the whole development lifecycle from designing (10%), implementing (40%), running regression & unit testing (40%) to supporting internal and production issues (10%) ● Apply experience of Object-Oriented design patterns and best practices to creating a robust and reliable infrastructure for the system with knowledge of Java SE, Hibernate, JMS, JVM and MySQL and deliver constant results in weekly production release ● Automate development and testing frameworks by writing python and shell scripts to improve overall -

Open Virtualization Infrastructure for Large Telco: How Turkcell Adopted Ovirt for Its Test and Development Environments
Open Virtualization Infrastructure for large Telco: How Turkcell adopted oVirt for its test and development environments DEVRIM YILMAZ SAYGIN BAKTIR Senior Expert Cloud Engineer Cloud Systems Administrator 09/2020 This presentation is licensed under a Creative Commons Attribution 4.0 International License About Turkcell ● Turkcell is a digital operator headquartered in Turkey ● Turkcell Group companies operate in 5 countries – Turkey, Ukraine, Belarus, Northern Cyprus, Germany ● Turkcell is the only NYSE-listed company in Turkey. ● www.turkcell.com.tr 3 Business Objectives ● Alternative solutions compatible with Turkcell operational and security standards ● Dissemination of open source infrastructure technologies within the company ● Competitive infrastructure with cost advantage 3 The journey of oVirt 4 The Journey of oVirt 3. Step three 1. Research & 2. Go-Live 3. Go-Live 4. Private Cloud 5. Go-Live Development Phase-1 Phase-2 Automation RHV 5 Research & Development ● Motivation Factors ○ Cost 1. Research & ○ Participation Development ○ Regulation ○ Independence ○ Expertise ● Risk Factors ○ Security ○ Quality ○ Compliance ○ Support ○ Worst Practices 6 Research & Development ● Why oVirt? ○ Open Source licensing 1. Research & ○ Community contribution Development ○ The same roadmap with commercial product ○ Support via subscription if required ○ Adequate features for enterprise management ○ Rest API support 6 Research & Development ● Difficulties for new infra solution ○ Integration with current infrastructure 1. Research & - Centralized Management Development - Certified/Licensed Solutions - Integration Cost ○ Incident & Problem Management - 3rd Party Support - Support with SLA ○ Acquired Habits - Customer Expectations - Quality of IT Infrastructure Services 6 Research & Development ● What we achieved ○ Building of PoC environment 1. Research & ○ V2V Migration Development ○ Upgrade Tests starting with v.4.3.2 ○ Functional Tests ○ Backup Alternative Solutions 6 Go-Live Phase-1 ● Phase-1 contains : ○ Building of new oVirt platform with unused h/w 2. -

Red Hat Enterprise Linux 7 Libreswan Cryptographic Module Version 7.0 and Version Rhel7.20190509 FIPS 140-2 Non-Proprietary Security Policy
Red Hat Enterprise Linux 7 Libreswan Cryptographic Module version 7.0 and version rhel7.20190509 FIPS 140-2 Non-Proprietary Security Policy Version 1.3 Last update: 2021-05-03 Prepared by: atsec information security corporation 9130 Jollyville Road, Suite 260 Austin, TX 78759 www.atsec.com ©2021 Red Hat®, Inc. / atsec information security corporation Page 1 of 23 This document can be reproduced and distributed only whole and intact, including this copyright notice. Red Hat Enterprise Linux 7 Libreswan Cryptographic Module FIPS 140-2 Non-Proprietary Security Policy Table of contents 1 Introduction ........................................................................................................................... 3 2 Cryptographic Module Specification ...................................................................................... 4 2.1 Module Overview ......................................................................................................... 4 2.2 FIPS 140-2 Validation ................................................................................................... 5 2.3 Modes of Operation ...................................................................................................... 6 3 Cryptographic Module Ports and Interfaces ........................................................................... 7 4 Roles, Services and Authentication ....................................................................................... 8 4.1 Roles ........................................................................................................................... -

Clouder Documentation Release 1.0
Clouder Documentation Release 1.0 Yannick Buron May 15, 2017 Contents 1 Getting Started 3 1.1 Odoo installation.............................................3 1.2 Clouder configuration..........................................4 1.3 Services deployed by the oneclick....................................6 2 Connect to a new node 9 3 Images 13 4 Applications 15 4.1 Application Types............................................ 15 4.2 Application................................................ 16 5 Services 21 6 Domains and Bases 25 6.1 Domains................................................. 25 6.2 Bases................................................... 27 7 Backups and Configuration 31 7.1 Backups................................................. 31 7.2 Configuration............................................... 33 i ii Clouder Documentation, Release 1.0 Contents: Contents 1 Clouder Documentation, Release 1.0 2 Contents CHAPTER 1 Getting Started In this chapter, we’ll see a step by step guide to install a ready-to-use infrastructure. For the example, the base we will create will be another Clouder. Odoo installation This guide will not cover the Odoo installation in itself, we suggest you read the installation documentation on the official website. You can also, and it’s probably the easier way, use an Odoo Docker image like https://hub.docker.com/ _/odoo/ or https://hub.docker.com/r/tecnativa/odoo-base/ Due to the extensive use of ssh, Clouder is only compatible with Linux. Once your Odoo installation is ready, install the paramiko, erppeek and apache-libcloud python libraries (pip install paramiko erppeek apache-libcloud), download the OCA/Connector module on Github and the Clouder modules on Github and add them in your addons directory, then install the clouder module and clouder_template_odoo (this module will install a lot of template dependencies, like postgres, postfix etc...). -

Deploying Netapp HCI for Red Hat Openshift on RHV HCI Netapp September 23, 2021
Deploying NetApp HCI for Red Hat OpenShift on RHV HCI NetApp September 23, 2021 This PDF was generated from https://docs.netapp.com/us-en/hci- solutions/redhat_openshift_deployment_summary.html on September 23, 2021. Always check docs.netapp.com for the latest. Table of Contents Deploying NetApp HCI for Red Hat OpenShift on RHV . 1 Deployment Summary: NetApp HCI for Red Hat OpenShift on RHV . 1 1. Create Storage Network VLAN: NetApp HCI for Red Hat OpenShift on RHV. 1 2. Download OpenShift Installation Files: NetApp HCI for Red Hat OpenShift on RHV . 2 3. Download CA Certificate from RHV: NetApp HCI for Red Hat OpenShift on RHV . 4 4. Register API/Apps in DNS: NetApp HCI for Red Hat OpenShift on RHV . 5 5. Generate and Add SSH Private Key: NetApp HCI for Red Hat OpenShift on RHV. 7 6. Install OpenShift Container Platform: NetApp HCI for Red Hat OpenShift on RHV . 8 7. Access Console/Web Console: NetApp HCI for Red Hat OpenShift on RHV . 10 8. Configure Worker Nodes to Run Storage Services: NetApp HCI for Red Hat OpenShift on RHV. 11 9. Download and Install NetApp Trident: NetApp HCI for Red Hat OpenShift on RHV . 13 Deploying NetApp HCI for Red Hat OpenShift on RHV Deployment Summary: NetApp HCI for Red Hat OpenShift on RHV The detailed steps provided in this section provide a validation for the minimum hardware and software configuration required to deploy and validate the NetApp HCI for Red Hat OpenShift on RHV solution. Deploying Red Hat OpenShift Container Platform through IPI on Red Hat Virtualization consists of the following steps: 1. -
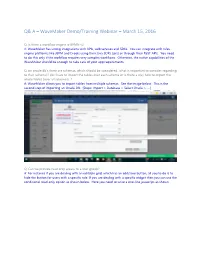
Q& a – Wavemaker Demo/Training Webinar – March 15, 2016
Q& A – WaveMaker Demo/Training Webinar – March 15, 2016 Q: Is there a workflow engine ie BPMN v2 A: WaveMaker has strong integrations with APIs, web services and SDKs. You can integrate with rules engine platforms like JBPM and Drools using their Java SDKs (jars) or through their ReST APIs. You need to do this only if the workflow requires very complex workflows. Otherwise, the native capabilities of the WaveMaker should be enough to take care of your app requirements. Q: on oracle db's there are schemas, which should be considered...what is important to consider regarding to that (schema)? do I have to import the tables over each schema or is there a way how to import the whole tables (over all schemas)...? A: WaveMaker allows you to import tables from multiple schemas. See the image below. This is the second step of importing an Oracle DB. [Steps: Import > Database > Select Oracle > ….] Q: Can we provide read only access to a user group? A: For instance if you are dealing with an editable grid, which has an add/save button, all you to do is to hide the button for users with a specific role. If you are dealing with a specific widget then you can use the conditional read-only option as shown below. Here you need to write a one-line javascript as shown below, where the users with the role “rolename” will be presented a read-only birthdate. Q: Can we integrate the application for SSO ? A: You can configure SSO easily through the following approach. -

8. IBM Z and Hybrid Cloud
The Centers for Medicare and Medicaid Services The role of the IBM Z® in Hybrid Cloud Architecture Paul Giangarra – IBM Distinguished Engineer December 2020 © IBM Corporation 2020 The Centers for Medicare and Medicaid Services The Role of IBM Z in Hybrid Cloud Architecture White Paper, December 2020 1. Foreword ............................................................................................................................................... 3 2. Executive Summary .............................................................................................................................. 4 3. Introduction ........................................................................................................................................... 7 4. IBM Z and NIST’s Five Essential Elements of Cloud Computing ..................................................... 10 5. IBM Z as a Cloud Computing Platform: Core Elements .................................................................... 12 5.1. The IBM Z for Cloud starts with Hardware .............................................................................. 13 5.2. Cross IBM Z Foundation Enables Enterprise Cloud Computing .............................................. 14 5.3. Capacity Provisioning and Capacity on Demand for Usage Metering and Chargeback (Infrastructure-as-a-Service) ................................................................................................................... 17 5.4. Multi-Tenancy and Security (Infrastructure-as-a-Service) ....................................................... -

Salesforce Heroku Enterprise: a Cloud Security Overview June 2016
Salesforce Heroku Enterprise: A Cloud Security Overview June 2016 1 Contents INTRODUCTION 3 CASESTUDY:GLIBC 19 Heroku behind the Curtain: Patching SALESFORCETRUSTMODEL 4 the glibc Security Hole What Do We Do When a Security CLOUD COMPUTING AND Vulnerability Lands? THESHAREDSECURITYMODEL 5 Provider Responsibilities How Do We Do This with Minimum Downtime? Tenant Responsibilities What about Data? INFRASTRUCTURE AND What about Heroku Itself? APPLICATIONSECURITY 8 Keep Calm, Carry On Server Hardening Customer Applications BUSINESSCONTINUITY 23 Heroku Platform: High Availability Container Hardening and Disaster Recovery Application Security Customer Applications Heroku Flow Postgres Databases Identity and Access Management Customer Configuration and Identity Federation via Single Sign-On Meta-Information Organizations, Roles, and Permissions Service Resiliency and Availability Business Continuity and Emergency NETWORKSECURITY 14 Preparedness Secure Network Architecture Secure Access Points INCIDENTRESPONSE 27 Data in Motion ELEMENTSMARKETPLACE 28 Private Spaces App Permissions Building Secure Applications with Add-Ons DATASECURITY 16 Heroku Postgres PHYSICALSECURITY 29 Encryption Data Center Access Customer Data Retention and Destruction Environmental Controls Management SECURITYMONITORING 17 Storage Device Decommissioning Logging and Network Monitoring DDoS COMPLIANCEANDAUDIT 31 Man in the Middle and IP Spoofing SUMMARY 33 Patch Management HEROKU ENTERPRISE SECURITY WHITE PAPER 2 Introduction eroku Enterprise, a key component of the Salesforce Platform, is a cloud application platform used by organizations of all sizes to deploy and operate applications throughout Hthe world. The Heroku platform is one of the first cloud application platforms delivered entirely as a service, allowing organizations to focus on application development and business strategy while Salesforce and the Heroku division of Salesforce focus on infrastructure management, scaling, and security. -

Cloud Computing: a Taxonomy of Platform and Infrastructure-Level Offerings David Hilley College of Computing Georgia Institute of Technology
Cloud Computing: A Taxonomy of Platform and Infrastructure-level Offerings David Hilley College of Computing Georgia Institute of Technology April 2009 Cloud Computing: A Taxonomy of Platform and Infrastructure-level Offerings David Hilley 1 Introduction Cloud computing is a buzzword and umbrella term applied to several nascent trends in the turbulent landscape of information technology. Computing in the “cloud” alludes to ubiquitous and inexhaustible on-demand IT resources accessible through the Internet. Practically every new Internet-based service from Gmail [1] to Amazon Web Services [2] to Microsoft Online Services [3] to even Facebook [4] have been labeled “cloud” offerings, either officially or externally. Although cloud computing has garnered significant interest, factors such as unclear terminology, non-existent product “paper launches”, and opportunistic marketing have led to a significant lack of clarity surrounding discussions of cloud computing technology and products. The need for clarity is well-recognized within the industry [5] and by industry observers [6]. Perhaps more importantly, due to the relative infancy of the industry, currently-available product offerings are not standardized. Neither providers nor potential consumers really know what a “good” cloud computing product offering should look like and what classes of products are appropriate. Consequently, products are not easily comparable. The scope of various product offerings differ and overlap in complicated ways – for example, Ama- zon’s EC2 service [7] and Google’s App Engine [8] partially overlap in scope and applicability. EC2 is more flexible but also lower-level, while App Engine subsumes some functionality in Amazon Web Services suite of offerings [2] external to EC2. -

Paas Solutions Evaluation
PaaS solutions evaluation August 2014 Author: Sofia Danko Supervisors: Giacomo Tenaglia Artur Wiecek CERN openlab Summer Student Report 2014 CERN openlab Summer Student Report 2014 Project Specification OpenShift Origin is an open source software developed mainly by Red Hat to provide a multi- language PaaS. It is meant to allow developers to build and deploy their applications in a uniform way, reducing the configuration and management effort required on the administration side. The aim of the project is to investigate how to deploy OpenShift Origin at CERN, and to which extent it could be integrated with CERN "Middleware on Demand" service. The student will be exposed to modern cloud computing concepts such as PaaS, and will work closely with the IT middleware experts in order to evaluate how to address service needs with a focus on deployment in production. Some of the tools that are going to be heavily used are Puppet and Openstack to integrate with the IT infrastructure. CERN openlab Summer Student Report 2014 Abstract The report is a brief summary of Platform as a Service (PaaS) solutions evaluation including investigation the current situation at CERN and Services on Demand provision, homemade solutions, external market analysis and some information about PaaS deployment process. This first part of the report is devoted to the current status of the process of deployment OpenShift Origin at existing infrastructure at CERN, as well as specification of the common issues and restrictions that were found during this process using different machines for test. Furthermore, the following open source software solutions have been proposed for the investigation of possible PaaS provision at CERN: OpenShift Online; Cloud Foundry; Deis; Paasmaster; Cloudify; Stackato; WSO2 Stratos. -

Red Hat Openshift Container Platform 3.6
RED HAT OPENSHIFT CONTAINER PLATFORM 3.6 DATASHEET KEY BENEFITS OVERVIEW • Deliver your latest innova- Red Hat® OpenShift Container Platform helps organizations develop, deploy, and manage exist- tion to market faster and stay ing and container-based applications seamlessly across physical, virtual, and public cloud infra- ahead of your competition. structures. Built on proven open source technologies, Red Hat OpenShift Container Platform helps application development and IT operations teams modernize applications, deliver new services, and • Accelerate application accelerate development processes. development by giving your developers and system admin- RED HAT OPENSHIFT CONTAINER PLATFORM istrators the tools they need FOR APPLICATION DEVELOPMENT TEAMS to get the job done. OpenShift Container Platform provides developers with an optimal platform for provisioning, build- • Use a secure, enterprise- ing, and deploying applications and their components in a self-service fashion. With automated grade, container-based workflows like our source-to-image (S2I) process, it is easy to get source code from version control platform with no vendor systems into ready-to-run, docker-formatted container images. OpenShift Container Platform inte- lock-in. grates with continuous integration (CI) and continuous delivery (CD) tools, making it an ideal solution • Support DevOps and depart- for any organization. ment-wide collaboration. FOR I.T. OPERATIONS OpenShift Container Platform gives IT operations a secure, enterprise-grade Kubernetes that pro- Red Hat OpenShift Online vides policy-based control and automation for applications. Cluster services, scheduling, and orches- is a public cloud application tration provide load-balancing and auto-scaling capabilities. Security features prevent tenants from platform that lets you quickly compromising other applications or the underlying host. -

Cloud Computing Parallel Session Cloud Computing
Cloud Computing Parallel Session Jean-Pierre Laisné Open Source Strategy Bull OW2 Open Source Cloudware Initiative Cloud computing -Which context? -Which road map? -Is it so cloudy? -Openness vs. freedom? -Opportunity for Europe? Cloud in formation Source: http://fr.wikipedia.org/wiki/Fichier:Clouds_edited.jpg ©Bull, 2 ITEA2 - Artemis: Cloud Computing 2010 1 Context 1: Software commoditization Common Specifications Not process specific •Marginal product •Economies of scope differentiation Offshore •Input in many different •Recognized quality end-products or usage standards •Added value is created •Substituable goods downstream Open source •Minimize addition to end-user cost Mature products Volume trading •Marginal innovation Cloud •Economies of scale •Well known production computing •Industry-wide price process levelling •Multiple alternative •Additional margins providers through additional volume Commoditized IT & Internet-based IT usage ©Bull, 3 ITEA2 - Artemis: Cloud Computing 2010 Context 2: The Internet is evolving ©Bull, 4 ITEA2 - Artemis: Cloud Computing 2010 2 New trends, new usages, new business -Apps vs. web pages - Specialized apps vs. HTML5 - Segmentation vs. Uniformity -User “friendly” - Pay for convenience -New devices - Phones, TV, appliances, etc. - Global economic benefits of the Internet - 2010: $1.5 Trillion - 2020: $3.8 Trillion Information Technology and Innovation Foundation (ITIF) Long live the Internet ©Bull, 5 ITEA2 - Artemis: Cloud Computing 2010 Context 3: Cloud on peak of inflated expectations According to