Comparison and Evaluation of Routing Mechanisms for Wi-Fi Mesh Networks Centered Title Times Font Size 24 Bold
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A Comprehensive Study of Routing Protocols Performance with Topological Changes in the Networks Mohsin Masood Mohamed Abuhelala Prof
A comprehensive study of Routing Protocols Performance with Topological Changes in the Networks Mohsin Masood Mohamed Abuhelala Prof. Ivan Glesk Electronics & Electrical Electronics & Electrical Electronics & Electrical Engineering Department Engineering Department Engineering Department University of Strathclyde University of Strathclyde University of Strathclyde Glasgow, Scotland, UK Glasgow, Scotland, UK Glasgow, Scotland, UK mohsin.masood mohamed.abuhelala ivan.glesk @strath.ac.uk @strath.ac.uk @strath.ac.uk ABSTRACT different topologies and compare routing protocols, but no In the modern communication networks, where increasing work has been considered about the changing user demands and advance applications become a functionality of these routing protocols with the topology challenging task for handling user traffic. Routing with real-time network limitations. such as topological protocols have got a significant role not only to route user change, network congestions, and so on. Hence without data across the network but also to reduce congestion with considering the topology with different network scenarios less complexity. Dynamic routing protocols such as one cannot fully understand and make right comparison OSPF, RIP and EIGRP were introduced to handle among any routing protocols. different networks with various traffic environments. Each This paper will give a comprehensive literature review of of these protocols has its own routing process which each routing protocol. Such as how each protocol (OSPF, makes it different and versatile from the other. The paper RIP or EIGRP) does convergence activity with any change will focus on presenting the routing process of each in the network. Two experiments are conducted that are protocol and will compare its performance with the other. -

Inter-Flow Network Coding for Wireless Mesh Networks
Inter-Flow Network Coding for Wireless Mesh Networks Group 11gr1002 Martin Hundebøll Jeppe Ledet-Pedersen Master Thesis in Networks and Distributed Systems Aalborg University Spring 2011 The Faculty of Engineering and Science Department of Electronic Systems Frederik Bajers Vej 7 Phone: +45 96 35 86 00 http://es.aau.dk Title: Abstract: Inter-Flow Network Coding for This report documents the development and Wireless Mesh Networks implementation of the CATWOMAN (Coding Applied To Wireless On Mobile Ad-hoc Net- Project period: works) scheme for inter-flow network coding in February 1st - May 31st, 2011 wireless mesh networks. Networks that employ network coding differ Project group: from conventional store-and-forward networks, 11gr1002 by allowing intermediate nodes to combine packets from independent flows. Group members: CATWOMAN builds on the B.A.T.M.A.N Martin Hundebøll Adv. mesh routing protocol. The scheme Jeppe Ledet-Pedersen exploits the topology information from the routing layer to automatically identify cod- Supervisor: ing opportunities in the network. The net- Professor Frank H.P. Fitzek work coding scheme is implemented in the B.A.T.M.A.N Adv. Linux kernel module, and Number of copies: 4 can be used without modification to device Number of pages: 65 drivers or higher layer protocols. Appended documents: The protocol is tested in three different topolo- (2 appendices, 1 CD-ROM) gies, that are configured in a test network with Total number of pages: 71 five nodes. The coding scheme shows up to Finished: June 2011 62% increase in maximum achievable through- put for bidirectional UDP flows. The tests reveal an unequal allocation of transmission slots, when the nodes have different link quali- ties, with a preference for the node with the strongest link. -
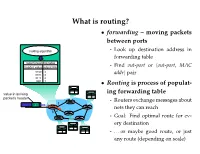
What Is Routing?
What is routing? • forwarding – moving packets between ports - Look up destination address in forwarding table - Find out-port or hout-port, MAC addri pair • Routing is process of populat- ing forwarding table - Routers exchange messages about nets they can reach - Goal: Find optimal route for ev- ery destination - . or maybe good route, or just any route (depending on scale) Routing algorithm properties • Static vs. dynamic - Static: routes change slowly over time - Dynamic: automatically adjust to quickly changing network conditions • Global vs. decentralized - Global: All routers have complete topology - Decentralized: Only know neighbors & what they tell you • Intra-domain vs. Inter-domain routing - Intra-: All routers under same administrative control - Intra-: Scale to ∼100 networks (e.g., campus like Stanford) - Inter-: Decentralized, scale to Internet Optimality A 6 1 3 2 F 1 E B 4 1 9 C D • View network as a graph • Assign cost to each edge - Can be based on latency, b/w, utilization, queue length, . • Problem: Find lowest cost path between two nodes - Must be computed in distributed way Distance Vector • Local routing algorithm • Each node maintains a set of triples - (Destination, Cost, NextHop) • Exchange updates w. directly connected neighbors - periodically (on the order of several seconds to minutes) - whenever table changes (called triggered update) • Each update is a list of pairs: - (Destination, Cost) • Update local table if receive a “better” route - smaller cost - from newly connected/available neighbor • Refresh existing -

The Routing Table V1.12 – Aaron Balchunas 1
The Routing Table v1.12 – Aaron Balchunas 1 - The Routing Table - Routing Table Basics Routing is the process of sending a packet of information from one network to another network. Thus, routes are usually based on the destination network, and not the destination host (host routes can exist, but are used only in rare circumstances). To route, routers build Routing Tables that contain the following: • The destination network and subnet mask • The “next hop” router to get to the destination network • Routing metrics and Administrative Distance The routing table is concerned with two types of protocols: • A routed protocol is a layer 3 protocol that applies logical addresses to devices and routes data between networks. Examples would be IP and IPX. • A routing protocol dynamically builds the network, topology, and next hop information in routing tables. Examples would be RIP, IGRP, OSPF, etc. To determine the best route to a destination, a router considers three elements (in this order): • Prefix-Length • Metric (within a routing protocol) • Administrative Distance (between separate routing protocols) Prefix-length is the number of bits used to identify the network, and is used to determine the most specific route. A longer prefix-length indicates a more specific route. For example, assume we are trying to reach a host address of 10.1.5.2/24. If we had routes to the following networks in the routing table: 10.1.5.0/24 10.0.0.0/8 The router will do a bit-by-bit comparison to find the most specific route (i.e., longest matching prefix). -

Overview of Wireless Mesh Networks
Journal of Communications Vol. 8, No. 9, September 2013 Overview of Wireless Mesh Networks Salah A. Alabady and M. F. M. Salleh School of Electrical and Electronic Engineering, Universiti Sains Malaysia, Seri Ampangan, 14300, Nibong Tebal, Pulau Pinang, Malaysia Email: [email protected]; [email protected] Abstract—Wireless Mesh Networks (WMNs) introduce a new and have a continuous power supply. They normally stay paradigm of wireless broadband Internet access by providing in static and supply connections and services to mesh high data rate service, scalability, and self-healing abilities at clients. reduced cost. Obtaining high throughput for multi-cast applications (e.g. video streaming broadcast) in WMNs is challenging due to the interference and the change of channel quality. To overcome this issue, cross-layer has been proposed to improve the performance of WMNs. Network coding is a powerful coding technique that has been proven to be the very effective in achieving the maximum multi-cast throughput. In addition to achieving the multi-cast throughput, network coding offers other benefits such as load balancing and saves bandwidth consumption. This paper presents a review the fundamental concept types of medium access control (MAC) layer, routing protocols, cross-layer and network coding for wireless mesh networks. Finally, a list of directions for further research is considered. Index Terms—Wireless mesh networks, multi-cast multi- radio multi- channel, medium access control, routing protocols, Wireless Wireless client channel assignment, cross layer, network coding. client Access I. INTRODUCTION point Nowadays, wireless mesh networks (WMNs) are Cellular Networks actively investigating with related applications and Wi-Fi services. -

Mesh Sensor Networks Bridge Iot's Last Mile
Internet of Things Internet of Things ADVERTISEMENT Fully Converged, Scalable Solution for an Intelligent Edge The solution is optimized for 1U and 2U rack environment, including a new 1U solution for 12x 3.5” hot-swap drive and 2U solutions for 24x 2.5” hot-swap drives. Features include redundant high efficiency power supplies, specially designed optimized cooling, and dual PCIe 3.0, Mini PCIe/mSATA and M.2 expansion slots for superior network and additional storage Mesh Sensor options. Supermicro Embedded Building Block Solutions: Lowest TCO for hyper-scale cloud workloads, storage, communications and security devices. Networks With the enormous growth of data and connected devices in mobile networks, carriers require a fully converged and scalable high-performance solution at the intelligent edge. Supermicro Figure 2: Supermicro® SC216 2U with 24x 2.5" and Supermicro® SC801 1U with 12x 12 3.5"Hot-Swap Drives Bridge is helping carrier providers address these edge convergence needs by introducing a converged yet scalable building block Powered by the Latest Intel® Xeon® Processor D Product solution with the new X10SDV-7TP8F embedded/server Family with up to 16 Cores motherboard design. The high-density hyper-scale Supermicro X10SDV-7TP8F IoT’s Last Mile provides scalable performance when paired the Intel® Xeon® Designed expressly for consolidating infrastructure at the processor D product family. Based on Intel’s 14nm process intelligent edge, this optimized solution offers exciting technology, these processors couple lower power consumption possibilities when paired with the latest Intel® Xeon® processor with the performance of up to 16 cores. The processor family D product family. -

P2P Resource Sharing in Wired/Wireless Mixed Networks 1
INT J COMPUT COMMUN, ISSN 1841-9836 Vol.7 (2012), No. 4 (November), pp. 696-708 P2P Resource Sharing in Wired/Wireless Mixed Networks J. Liao Jianwei Liao College of Computer and Information Science Southwest University of China 400715, Beibei, Chongqing, China E-mail: [email protected] Abstract: This paper presents a new routing protocol called Manager-based Routing Protocol (MBRP) for sharing resources in wired/wireless mixed networks. MBRP specifies a manager node for a designated sub-network (called as a group), in which all nodes have the similar connection properties; then all manager nodes are employed to construct the backbone overlay network with ring topology. The manager nodes act as the proxies between the internal nodes in the group and the external world, that is not only for centralized management of all nodes to a certain extent, but also for avoiding the messages flooding in the whole network. The experimental results show that compared with Gnutella2, which uses super-peers to perform similar management work, the proposed MBRP has less lookup overhead including lookup latency and lookup hop count in the most of cases. Besides, the experiments also indicate that MBRP has well configurability and good scaling properties. In a word, MBRP has less transmission cost of the shared file data, and the latency for locating the sharing resources can be reduced to a great extent in the wired/wireless mixed networks. Keywords: wired/wireless mixed network, resource sharing, manager-based routing protocol, backbone overlay network, peer-to-peer. 1 Introduction Peer-to-Peer technology (P2P) is a widely used network technology, the typical P2P network relies on the computing power and bandwidth of all participant nodes, rather than a few gathered and dedicated servers for central coordination [1, 2]. -

Routing As a Service
Routing as a Service Karthik Lakshminarayanan Ion Stoica Scott Shenker Jennifer Rexford University of California, Berkeley Princeton University Abstract configuration, making it difficult to offer meaningful service- level agreements (SLAs) to customers or to identify the AS In Internet routing, there is a fundamental tussle between the responsible for end-to-end performance problems. end users who want control over the end-to-end paths and the An ISP's customers, such as end users, enterprise net- Autonomous Systems (ASes) who want control over the flow works, and smaller ISPs, have even less control over the se- of traffic through their infrastructure. To resolve this tussle lection of end-to-end paths. By connecting to more than one and offer flexible routing control across multiple routing do- ISPs, an enterprise can select from multiple paths [2]; how- mains, we argue that customized route computation should ever, the customer controls only the first hop for outbound be offered as a service by third-party providers. Outsourcing traffic and has (at best) crude influence on incoming traffic. specialized route computation allows different path-selection Yet, some customers need more control over the end-to-end mechanisms to coexist, and evolve over time. path, or at least its properties, to satisfy performance and pol- icy goals. For example, a customer might not want his Web 1 Introduction traffic forwarded through an AS that filters packets based on Interdomain routing has long been based on three pillars: their contents. Alternatively, a customer might need to discard traffic from certain sources to block denial-of-service attacks • Local control: ASes have complete control over routing or protect access to a server storing sensitive data. -

Hybrid Wireless Mesh Network, Worldwide Satellite Communication, and PKI Technology for Small Satellite Network System
Hybrid Wireless Mesh Network, Worldwide Satellite Communication, and PKI Technology for Small Satellite Network System A project present to The Faculty of the Department of Aerospace Engineering San Jose State University in partial fulfillment of the requirements for the degree Master of Science in Aerospace Engineering By Stephen S. Im May 2015 approved by Dr. Periklis Papadopoulos Faculty Advisor 1 ©2015 Stephen S. Im ALL RIGHTS RESERVED 2 An Abstract of Hybrid Wireless Mesh Network, Worldwide Satellite Communication, and PKI Technology for Small Satellite Network System by Stephen S. Im1 San Jose State University May 2015 Small satellites are getting the spotlight in the aerospace industry because this earth- orbiting technology is well-suited for use in military service, space mission research, weather prediction, wireless communication, scientific observation, and education demonstration. Small satellites have advantages of low cost of manufacturing, ease of mass production, low cost of launch system, ability to be launched in groups, and minimal financial failure. Until now, a number of the small satellites have been built and launched for various purposes. As network simplification, operation efficiency, communication accessibility, and high-end data security are the fundamental communication factors for small satellite operations, a standardized space network communication with strong data protection has become a significant technology. This is also highly beneficial for mass manufacture, compatible for cross-platform, and common error detection. And the ground-based network technologies which fulfill Internet-of-Things (IOT) concept, which consist of Wireless Mesh Network (WMN) and data security, are presented in this paper. 1 Graduate Student, San Jose State University, One Washington Square, San Jose, CA. -
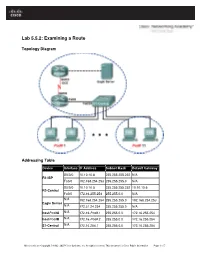
Lab 5.5.2: Examining a Route
Lab 5.5.2: Examining a Route Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway S0/0/0 10.10.10.6 255.255.255.252 N/A R1-ISP Fa0/0 192.168.254.253 255.255.255.0 N/A S0/0/0 10.10.10.5 255.255.255.252 10.10.10.6 R2-Central Fa0/0 172.16.255.254 255.255.0.0 N/A N/A 192.168.254.254 255.255.255.0 192.168.254.253 Eagle Server N/A 172.31.24.254 255.255.255.0 N/A host Pod# A N/A 172.16. Pod#.1 255.255.0.0 172.16.255.254 host Pod# B N/A 172.16. Pod#. 2 255.255.0.0 172.16.255.254 S1-Central N/A 172.16.254.1 255.255.0.0 172.16.255.254 All contents are Copyright © 1992–2007 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 1 of 7 CCNA Exploration Network Fundamentals: OSI Network Layer Lab 5.5.1: Examining a Route Learning Objectives Upon completion of this lab, you will be able to: • Use the route command to modify a Windows computer routing table. • Use a Windows Telnet client command telnet to connect to a Cisco router. • Examine router routes using basic Cisco IOS commands. Background For packets to travel across a network, a device must know the route to the destination network. This lab will compare how routes are used in Windows computers and the Cisco router. -

Routing Basics
CHAPTER 5 Chapter Goals • Learn the basics of routing protocols. • Learn the differences between link-state and distance vector routing protocols. • Learn about the metrics used by routing protocols to determine path selection. • Learn the basics of how data travels from end stations through intermediate stations and on to the destination end station. • Understand the difference between routed protocols and routing protocols. Routing Basics This chapter introduces the underlying concepts widely used in routing protocols. Topics summarized here include routing protocol components and algorithms. In addition, the role of routing protocols is briefly contrasted with the role of routed or network protocols. Subsequent chapters in Part VII, “Routing Protocols,” address specific routing protocols in more detail, while the network protocols that use routing protocols are discussed in Part VI, “Network Protocols.” What Is Routing? Routing is the act of moving information across an internetwork from a source to a destination. Along the way, at least one intermediate node typically is encountered. Routing is often contrasted with bridging, which might seem to accomplish precisely the same thing to the casual observer. The primary difference between the two is that bridging occurs at Layer 2 (the link layer) of the OSI reference model, whereas routing occurs at Layer 3 (the network layer). This distinction provides routing and bridging with different information to use in the process of moving information from source to destination, so the two functions accomplish their tasks in different ways. The topic of routing has been covered in computer science literature for more than two decades, but routing achieved commercial popularity as late as the mid-1980s. -

Routing Tables
Routing Tables A routing table is a grouping of information stored on a networked computer or network router that includes a list of routes to various network destinations. The data is normally stored in a database table and in more advanced configurations includes performance metrics associated with the routes stored in the table. Additional information stored in the table will include the network topology closest to the router. Although a routing table is routinely updated by network routing protocols, static entries can be made through manual action on the part of a network administrator. How Does a Routing Table Work? Routing tables work similar to how the post office delivers mail. When a network node on the Internet or a local network needs to send information to another node, it first requires a general idea of where to send the information. If the destination node or address is not connected directly to the network node, then the information has to be sent via other network nodes. In order to save resources, most local area network nodes will not maintain a complex routing table. Instead, they will send IP packets of information to a local network gateway. The gateway maintains the primary routing table for the network and will send the data packet to the desired location. In order to maintain a record of how to route information, the gateway will use a routing table that keeps track of the appropriate destination for outgoing data packets. All routing tables maintain routing table lists for the reachable destinations from the router’s location.