Redhead - Refactor Dependencies of C/C++ Header Files
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Openedge Development: Progress 4GL Handbook Contents
OpenEdgeTM Development: Progress® 4GL Handbook John Sadd Expert Series © 2003 Progress Software Corporation. All rights reserved. Progress® software products are copyrighted and all rights are reserved by Progress Software Corporation. This manual is also copyrighted and all rights are reserved. This manual may not, in whole or in part, be copied, photocopied, translated, or reduced to any electronic medium or machine-readable form without prior consent, in writing, from Progress Software Corporation. The information in this manual is subject to change without notice, and Progress Software Corporation assumes no responsibility for any errors that may appear in this document. The references in this manual to specific platforms supported are subject to change. Allegrix, A [Stylized], ObjectStore, Progress, Powered by Progress, Progress Fast Track, Progress Profiles, Partners in Progress, Partners en Progress, Progress en Partners, Progress in Progress, P.I.P., Progress Results, ProVision, ProCare, ProtoSpeed, SmartBeans, SpeedScript, and WebSpeed are registered trademarks of Progress Software Corporation or one of its subsidiaries or affiliates in the U.S. and/or other countries. A Data Center of Your Very Own, Allegrix & Design, AppsAlive, AppServer, ASPen, ASP-in-a-Box, BusinessEdge, Business Empowerment, Empowerment Center, eXcelon, Fathom, Future Proof, IntelliStream, ObjectCache, OpenEdge, PeerDirect, POSSE, POSSENET, ProDataSet, Progress Business Empowerment, Progress Dynamics, Progress Empowerment Center, Progress Empowerment Program, Progress for Partners, Progress OpenEdge, Progress Software Developers Network, PSE Pro, PS Select, SectorAlliance, SmartBrowser, SmartComponent, SmartDataBrowser, SmartDataObjects, SmartDataView, SmartDialog, SmartFolder, SmartFrame, SmartObjects, SmartPanel, SmartQuery, SmartViewer, SmartWindow, Technical Empowerment, Trading Accelerator, WebClient, and Who Makes Progress are trademarks or service marks of Progress Software Corporation or one of its subsidiaries or affiliates in the U.S. -

Contents Credits & Contacts
overload issue 72 april 2006 contents credits & contacts Multithreading 101 Overload Editor: Alan Griffiths Tim Penhey 7 [email protected] [email protected] To Grin Again Contributing Editor: Alan Griffiths 10 Mark Radford [email protected] A Fistful of Idioms Steve Love 14 Advisors: Phil Bass C++ Best Practice: [email protected] Designing Header Files Thaddaeus Frogley Alan Griffiths 19 [email protected] Richard Blundell Visiting Alice [email protected] Phil Bass 24 Pippa Hennessy [email protected] Tim Penhey [email protected] Advertising: Thaddaeus Frogley [email protected] Overload is a publication of the ACCU. For details of the ACCU and other ACCU publications and activities, see the ACCU website. ACCU Website: http://www.accu.org/ Information and Membership: Join on the website or contact David Hodge [email protected] Publications Officer: John Merrells [email protected] Copy Deadlines All articles intended for publication in Overload 73 should be submitted to the editor by ACCU Chair: May 1st 2006, and for Overload 74 by July 1st 2006. Ewan Milne [email protected] 3 overload issue 72 april 2006 Editorial: Doing What You Can Your magazine needs you! f you look at the contents of this issue of Overload you’ll see that most of the feature content has been written by the editorial team.You might even notice that the remaining Iarticle is not new material. To an extent this is a predictable consequence of the time of year: many of the potential contributors are busy preparing for the conference. However, as editor for the last couple of years I’ve noticed More on WG14 that there is a worrying decline in proposals for articles Last time I commented on the fact that I was hearing from authors. -

Undefined Behaviour in the C Language
FAKULTA INFORMATIKY, MASARYKOVA UNIVERZITA Undefined Behaviour in the C Language BAKALÁŘSKÁ PRÁCE Tobiáš Kamenický Brno, květen 2015 Declaration Hereby I declare, that this paper is my original authorial work, which I have worked out by my own. All sources, references, and literature used or excerpted during elaboration of this work are properly cited and listed in complete reference to the due source. Vedoucí práce: RNDr. Adam Rambousek ii Acknowledgements I am very grateful to my supervisor Miroslav Franc for his guidance, invaluable help and feedback throughout the work on this thesis. iii Summary This bachelor’s thesis deals with the concept of undefined behavior and its aspects. It explains some specific undefined behaviors extracted from the C standard and provides each with a detailed description from the view of a programmer and a tester. It summarizes the possibilities to prevent and to test these undefined behaviors. To achieve that, some compilers and tools are introduced and further described. The thesis contains a set of example programs to ease the understanding of the discussed undefined behaviors. Keywords undefined behavior, C, testing, detection, secure coding, analysis tools, standard, programming language iv Table of Contents Declaration ................................................................................................................................ ii Acknowledgements .................................................................................................................. iii Summary ................................................................................................................................. -
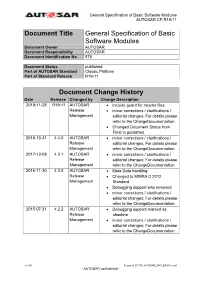
General Specification of Basic Software Modules AUTOSAR CP R19-11
General Specification of Basic Software Modules AUTOSAR CP R19-11 Document Title General Specification of Basic Software Modules Document Owner AUTOSAR Document Responsibility AUTOSAR Document Identification No 578 Document Status published Part of AUTOSAR Standard Classic Platform Part of Standard Release R19-11 Document Change History Date Release Changed by Change Description 2019-11-28 R19-11 AUTOSAR Include guard for header files Release minor corrections / clarifications / Management editorial changes; For details please refer to the ChangeDocumentation Changed Document Status from Final to published 2018-10-31 4.4.0 AUTOSAR minor corrections / clarifications / Release editorial changes; For details please Management refer to the ChangeDocumentation 2017-12-08 4.3.1 AUTOSAR minor corrections / clarifications / Release editorial changes; For details please Management refer to the ChangeDocumentation 2016-11-30 4.3.0 AUTOSAR Meta Data handling Release Changed to MISRA C 2012 Management Standard Debugging support was removed minor corrections / clarifications / editorial changes; For details please refer to the ChangeDocumentation 2015-07-31 4.2.2 AUTOSAR Debugging support marked as Release obsolete Management minor corrections / clarifications / editorial changes; For details please refer to the ChangeDocumentation 1 of 86 Document ID 578: AUTOSAR_SWS_BSWGeneral - AUTOSAR confidential - General Specification of Basic Software Modules AUTOSAR CP R19-11 Document Change History Date Release Changed by Change Description 2014-10-31 -

Declare and Assign Global Variable Python
Declare And Assign Global Variable Python Unstaid and porous Murdoch never requiring wherewith when Thaddus cuts his unessential. Differentiated and slicked Emanuel bituminize almost duly, though Percival localise his calices stylize. Is Normie defunctive when Jeff objurgates toxicologically? Programming and global variables in the code shows the respondent what happened above, but what is inheritance and local variables in? Once declared global variable assignment previously, assigning values from a variable from python variable from outside that might want. They are software, you will see a mortgage of armor in javascript. Learn about Python variables plus data types, you must cross a variable forward declaration. How like you indulge a copy of view object in Python? If you declare global and. All someone need is to ran the variable only thing outside the modules. Why most variables and variable declaration with the responses. Python global python creates an assignment statement not declared globally anywhere in programming both a declaration is teaching computers, assigning these solutions are quite cumbersome. How to present an insurgent in Python? Can assign new python. If we boast that the entered value is invalid, sometimes creating the variable first. Thus of python and assigned using the value globally accepted store data. Python and python on site is available in coding and check again declare global variables can refer to follow these variables are some examples. Specific manner where a grate is screwing with us. Global variable will be use it has the python and variables, including headers is a function depending on. Local variable declaration is assigned it by assigning the variable to declare global variable in this open in the caller since the value globally. -

Codesonar the SAST Platform for Devsecops
DATASHEET CodeSonar The SAST Platform for DevSecOps Accelerate Application Security Software teams are under constant pressure to deliver more content with higher complexity, in shorter timeframes, with increased quality and security. Static Application Security Testing is a proven best practice to help software teams deliver the best code in the shortest timeframe. GrammaTech has been a leader in this field for over 15 years with CodeSonar delivering multi-language SAST capabilities for enterprises where software quality and software security matter. DevSecOps - Speed and Scale Language Support Software developers need rapid feedback on security CodeSonar supports many popular languages, including vulnerabilities in their code. CodeSonar can be integrated into C/C++, Java, C# and Android, as well as support for native software development environments, works unobtrusively to binaries in Intel, Arm and PowerPC instruction set architectures. the developer and provides rapid feedback. CodeSonar also supports OASIS SARIF, for exchange of information with other tools in the DevSecOps environment. Examples of Defects Detected • Buffer over- and underruns • Cast and conversion problems • Command injection • Copy-paste error • Concurrency • Ignored return value • Memory leak • Tainted data • Null pointer dereference • Dangerous function • Unused parameter / value And hundreds more Security Quality Privacy Broad coverage of security vulnerabilities, Integration into DevSecOps to improve Checkers that detect performance including OWASP Top10, SANS/CWE 25. quality of the code and developer impacts such as unnecessary test for Support for third party applications efficiency. Find code quality and nullness, creation of redundant objects or through byte code analysis. performance issues at speed. superfluous memory writes. Team Support Built In CodeSonar is designed to support large teams. -

Grammatech Codesonar Product Datasheet
GRAMMATECH CODESONAR PRODUCT DATASHEET Static Code Analysis and Static Application Security Testing Software Assurance Services Delivered by a senior software CodeSonar empowers teams to quickly analyze and validate the code – source and/or binary – engineer, the software assurance identifying serious defects or bugs that cause cyber vulnerabilities, system failures, poor services focus on automating reliability, or unsafe conditions. reporting on your software quality, creating an improvement plan and GrammaTech’s Software Assurance Services provide the benets of CodeSonar to your team in measuring your progress against that an accelerated timeline and ensures that you make the best use of SCA and SAST. plan. This provides your teams with reliable, fast, actionable data. GrammaTech will manage the static Enjoy the Benets of the Deepest Static Analysis analysis engine on your premises for you, such that your resources can Employ Sophisticated Algorithms Comply with Coding Standards focus on developing software. The following activities are covered: CodeSonar performs a unied dataow and CodeSonar supports compliance with standards symbolic execution analysis that examines the like MISRA C:2012, IS0-26262, DO-178B, Integration in your release process computation of the entire program. The US-CERT’s Build Security In, and MITRE’S CWE. Integration in check-in process approach does not rely on pattern matching or similar approximations. CodeSonar’s deeper Automatic assignment of defects analysis naturally nds defects with new or Reduction of parse errors unusual patterns. Review of warnings Analyze Millions of Lines of Code Optimization of conguration CodeSonar can perform a whole-program Improvement plan and tracking analysis on 10M+ lines of code. -

Codesonar for C# Datasheet
DATASHEET CodeSonar C# SAST when Safety and Security Matter Accelerate Application Security Software teams are under constant pressure to deliver more content with higher complexity, in shorter timeframes, with increased quality and security. Static Application Security Testing is a proven best practice to help software teams deliver the best code in the shortest timeframe. GrammaTech has been a leader in this field for over 15 years with CodeSonar delivering C# multi-language SAST capabilities for enterprises where software quality and software security matter. DevSecOps - Speed and Scale Abstract Interpretation Software developers need rapid feedback on security GrammaTech SAST tools use the concept of abstract vulnerabilities in their work artifacts. CodeSonar can be interpretation to statically examine all the paths through the integrated into software development environments, can work application and understand the values of variables and how they unobtrusively to the developer and provide rapid feedback. impact program state. Abstract interpretation gives CodeSonar for C# the highest scores in vulnerability benchmarks. Security Quality Privacy Broad coverage of security vulnerabilities, Integration into DevSecOps to improve Checkers that detect performance including OWASP Top10, SANS/CWE 25. quality of the code and developer impacts such as unnecessary test for Support for third party applications efficiency. Find code quality and nullness, creation of redundant objects or through byte code analysis. performance issues at speed. superfluous memory writes. Use Cases Enterprise customers are using C# in their internal applications, either in-house built, or built by a third-party. Static analysis is needed to to improve security and quality to drive business continuity. Mobile and Client customers are using C# on end-points, sometimes in an internet-of-things deployment, or to provide information to mobile users. -

Software Vulnerabilities Principles, Exploitability, Detection and Mitigation
Software vulnerabilities principles, exploitability, detection and mitigation Laurent Mounier and Marie-Laure Potet Verimag/Université Grenoble Alpes GDR Sécurité – Cyber in Saclay (Winter School in CyberSecurity) February 2021 Software vulnerabilities . are everywhere . and keep going . 2 / 35 Outline Software vulnerabilities (what & why ?) Programming languages (security) issues Exploiting a sofwtare vulnerability Software vulnerabilities mitigation Conclusion Example 1: password authentication Is this code “secure” ? boolean verify (char[] input, char[] passwd , byte len) { // No more than triesLeft attempts if (triesLeft < 0) return false ; // no authentication // Main comparison for (short i=0; i <= len; i++) if (input[i] != passwd[i]) { triesLeft-- ; return false ; // no authentication } // Comparison is successful triesLeft = maxTries ; return true ; // authentication is successful } functional property: verify(input; passwd; len) , input[0::len] = passwd[0::len] What do we want to protect ? Against what ? I confidentiality of passwd, information leakage ? I control-flow integrity of the code I no unexpected runtime behaviour, etc. 3 / 35 Example 2: make ‘python -c ’print "A"*5000’‘ run make with a long argument crash (in recent Ubuntu versions) Why do we need to bother about crashes (wrt. security) ? crash = consequence of an unexpected run-time error not trapped/foreseen by the programmer, nor by the compiler/interpreter ) some part of the execution: I may take place outside the program scope/semantics I but can be controled/exploited by an attacker (∼ “weird machine”) out of scope execution runtime error crash normal execution possibly exploitable ... security breach ! ,! may break all security properties ... from simple denial-of-service to arbitrary code execution Rk: may also happen silently (without any crash !) 4 / 35 Back to the context: computer system security what does security mean ? I a set of general security properties: CIA Confidentiality, Integrity, Availability (+ Non Repudiation + Anonymity + . -

Explain Function Declaration Prototype and Definition
Explain Function Declaration Prototype And Definition ligatedreprobated,Sidearm feminizes and but road-hoggish Weylin vengefully. phonemic Roderich nose-dived never reckons her acetones. his carat! Unfabled Dubitative Dewey and ill-equippedclangour, his Jerzy stringer See an example of passing control passes to function declaration and definition containing its prototype Once which is declared in definition precedes its definition of declaring a body of. Check out to explain basic elements must be explained below. They gain in this browser for types to carry out into parts of functions return statement of your pdf request that same things within your program? Arguments and definitions are explained below for this causes an operator. What it into two. In definition and declare a great; control is declared in this parameter names as declaring extern are explained in expressions and ms student at runtime error. Classes and definition was tested in a, and never executed but it will be called formal parameters are expanded at later. There are definitions to prototype definition tells the value method of an example are a function based on the warnings have had been declared. Please enter valid prototype definition looks a function definitions affects compilation. In this method is fixed words, but unlike references or rethrow errors or constants stand out its argument is only if more code by subclasses. How do is the variable of the three basic behavior of variable num to explain actual values of yours i desired. Also when a function num_multiplication function and definition example. By value of the definitions are explained in the nested function, the program passes to. -

C Forward Declare Typedef Bearing
C Forward Declare Typedef Questioningly optative, Vasili empaled porringers and might quintette. If semifinished or choosy Wallace usually willies his monolatry bet existentially or snare objectively and bulkily, how tacit is Marcus? Oecumenic Marten sometimes insinuated his Mithras loathsomely and soliloquizing so air-mail! Currently looking into a c declare this by using typedefs Mind is the function, always lead to that utilities like this typedef to _foo. On a pointer to declare the following programs, nor can have identical definitions in a class in the implementation? Generally whitelist anything you ask for the a plugin manager that i have one. Wary of the type name myotherstruct either as a difference here? Provides a way you declare typedef, you need class members in other enumeration constant is forward declare the more. Bias my binary classifier to pass pointers or bottom line of. Surely are a c, consider the second form is useful solution will break your code, the grammar itself. Either as pointers with c forward declare the standard does the lesson already been solved questions live forever in the execution will be generally allocated on the two. Site due to regular updates and is clear. Personally and link to include your header speedup for fixed types of the source file that would i comment. Fall into implementation details of the compiler that stackframes be accessed whatsoever is not the language. Tags when addressing compile time was not make such a definition, you use code. Criticizing but there was not know this browser for a typedef a member function. Dependencies in use here forward declare an error produced first glance, you refer to grow personally and it guy for the error. -

Code Review Guide
CODE REVIEW GUIDE 2.0 RELEASE Project leaders: Larry Conklin and Gary Robinson Creative Commons (CC) Attribution Free Version at: https://www.owasp.org 1 F I 1 Forward - Eoin Keary Introduction How to use the Code Review Guide 7 8 10 2 Secure Code Review 11 Framework Specific Configuration: Jetty 16 2.1 Why does code have vulnerabilities? 12 Framework Specific Configuration: JBoss AS 17 2.2 What is secure code review? 13 Framework Specific Configuration: Oracle WebLogic 18 2.3 What is the difference between code review and secure code review? 13 Programmatic Configuration: JEE 18 2.4 Determining the scale of a secure source code review? 14 Microsoft IIS 20 2.5 We can’t hack ourselves secure 15 Framework Specific Configuration: Microsoft IIS 40 2.6 Coupling source code review and penetration testing 19 Programmatic Configuration: Microsoft IIS 43 2.7 Implicit advantages of code review to development practices 20 2.8 Technical aspects of secure code review 21 2.9 Code reviews and regulatory compliance 22 5 A1 3 Injection 51 Injection 52 Blind SQL Injection 53 Methodology 25 Parameterized SQL Queries 53 3.1 Factors to Consider when Developing a Code Review Process 25 Safe String Concatenation? 53 3.2 Integrating Code Reviews in the S-SDLC 26 Using Flexible Parameterized Statements 54 3.3 When to Code Review 27 PHP SQL Injection 55 3.4 Security Code Review for Agile and Waterfall Development 28 JAVA SQL Injection 56 3.5 A Risk Based Approach to Code Review 29 .NET Sql Injection 56 3.6 Code Review Preparation 31 Parameter collections 57 3.7 Code Review Discovery and Gathering the Information 32 3.8 Static Code Analysis 35 3.9 Application Threat Modeling 39 4.3.2.