Matrix Analysis
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Sobolev Spaces, Theory and Applications
Sobolev spaces, theory and applications Piotr Haj lasz1 Introduction These are the notes that I prepared for the participants of the Summer School in Mathematics in Jyv¨askyl¨a,August, 1998. I thank Pekka Koskela for his kind invitation. This is the second summer course that I delivere in Finland. Last August I delivered a similar course entitled Sobolev spaces and calculus of variations in Helsinki. The subject was similar, so it was not posible to avoid overlapping. However, the overlapping is little. I estimate it as 25%. While preparing the notes I used partially the notes that I prepared for the previous course. Moreover Lectures 9 and 10 are based on the text of my joint work with Pekka Koskela [33]. The notes probably will not cover all the material presented during the course and at the some time not all the material written here will be presented during the School. This is however, not so bad: if some of the results presented on lectures will go beyond the notes, then there will be some reasons to listen the course and at the same time if some of the results will be explained in more details in notes, then it might be worth to look at them. The notes were prepared in hurry and so there are many bugs and they are not complete. Some of the sections and theorems are unfinished. At the end of the notes I enclosed some references together with comments. This section was also prepared in hurry and so probably many of the authors who contributed to the subject were not mentioned. -

On Quasi Norm Attaining Operators Between Banach Spaces
ON QUASI NORM ATTAINING OPERATORS BETWEEN BANACH SPACES GEUNSU CHOI, YUN SUNG CHOI, MINGU JUNG, AND MIGUEL MART´IN Abstract. We provide a characterization of the Radon-Nikod´ymproperty in terms of the denseness of bounded linear operators which attain their norm in a weak sense, which complement the one given by Bourgain and Huff in the 1970's. To this end, we introduce the following notion: an operator T : X ÝÑ Y between the Banach spaces X and Y is quasi norm attaining if there is a sequence pxnq of norm one elements in X such that pT xnq converges to some u P Y with }u}“}T }. Norm attaining operators in the usual (or strong) sense (i.e. operators for which there is a point in the unit ball where the norm of its image equals the norm of the operator) and also compact operators satisfy this definition. We prove that strong Radon-Nikod´ymoperators can be approximated by quasi norm attaining operators, a result which does not hold for norm attaining operators in the strong sense. This shows that this new notion of quasi norm attainment allows to characterize the Radon-Nikod´ymproperty in terms of denseness of quasi norm attaining operators for both domain and range spaces, completing thus a characterization by Bourgain and Huff in terms of norm attaining operators which is only valid for domain spaces and it is actually false for range spaces (due to a celebrated example by Gowers of 1990). A number of other related results are also included in the paper: we give some positive results on the denseness of norm attaining Lipschitz maps, norm attaining multilinear maps and norm attaining polynomials, characterize both finite dimensionality and reflexivity in terms of quasi norm attaining operators, discuss conditions to obtain that quasi norm attaining operators are actually norm attaining, study the relationship with the norm attainment of the adjoint operator and, finally, present some stability results. -

On the Cone of a Finite Dimensional Compact Convex Set at a Point
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Elsevier - Publisher Connector On the Cone of a Finite Dimensional Compact Convex Set at a Point C. H. Sung Department of Mathematics University of Califmia at San Diego La Joll41, California 92093 and Department of Mathematics San Diego State University San Diego, California 92182 and B. S. Tam* Department of Mathematics Tamkang University Taipei, Taiwan 25137, Republic of China Submitted by Robert C. Thompson ABSTRACT Four equivalent conditions for a convex cone in a Euclidean space to be an F,-set are given. Our result answers in the negative a recent open problem posed by Tam [5], characterizes the barrier cone of a convex set, and also provides an alternative proof for the known characterizations of the inner aperture of a convex set as given by BrBnsted [2] and Larman [3]. 1. INTRODUCTION Let V be a Euclidean space and C be a nonempty convex set in V. For each y E C, the cone of C at y, denoted by cone(y, C), is the cone *The work of this author was supported in part by the National Science Council of the Republic of China. LINEAR ALGEBRA AND ITS APPLICATIONS 90:47-55 (1987) 47 0 Elsevier Science Publishing Co., Inc., 1987 52 Vanderbilt Ave., New York, NY 10017 00243795/87/$3.50 48 C. H. SUNG AND B. S. TAM { a(r - Y) : o > 0 and x E C} (informally called a point’s cone). On 23 August 1983, at the International Congress of Mathematicians in Warsaw, in a short communication session, the second author presented the paper [5] and posed the following open question: Is it true that, given any cone K in V, there always exists a compact convex set C whose point’s cone at some given point y is equal to K? In view of the relation cone(y, C) = cone(0, C - { y }), the given point y may be taken to be the origin of the space. -

Notes on Partial Differential Equations John K. Hunter
Notes on Partial Differential Equations John K. Hunter Department of Mathematics, University of California at Davis Contents Chapter 1. Preliminaries 1 1.1. Euclidean space 1 1.2. Spaces of continuous functions 1 1.3. H¨olderspaces 2 1.4. Lp spaces 3 1.5. Compactness 6 1.6. Averages 7 1.7. Convolutions 7 1.8. Derivatives and multi-index notation 8 1.9. Mollifiers 10 1.10. Boundaries of open sets 12 1.11. Change of variables 16 1.12. Divergence theorem 16 Chapter 2. Laplace's equation 19 2.1. Mean value theorem 20 2.2. Derivative estimates and analyticity 23 2.3. Maximum principle 26 2.4. Harnack's inequality 31 2.5. Green's identities 32 2.6. Fundamental solution 33 2.7. The Newtonian potential 34 2.8. Singular integral operators 43 Chapter 3. Sobolev spaces 47 3.1. Weak derivatives 47 3.2. Examples 47 3.3. Distributions 50 3.4. Properties of weak derivatives 53 3.5. Sobolev spaces 56 3.6. Approximation of Sobolev functions 57 3.7. Sobolev embedding: p < n 57 3.8. Sobolev embedding: p > n 66 3.9. Boundary values of Sobolev functions 69 3.10. Compactness results 71 3.11. Sobolev functions on Ω ⊂ Rn 73 3.A. Lipschitz functions 75 3.B. Absolutely continuous functions 76 3.C. Functions of bounded variation 78 3.D. Borel measures on R 80 v vi CONTENTS 3.E. Radon measures on R 82 3.F. Lebesgue-Stieltjes measures 83 3.G. Integration 84 3.H. Summary 86 Chapter 4. -

Boundedness in Linear Topological Spaces
BOUNDEDNESS IN LINEAR TOPOLOGICAL SPACES BY S. SIMONS Introduction. Throughout this paper we use the symbol X for a (real or complex) linear space, and the symbol F to represent the basic field in question. We write R+ for the set of positive (i.e., ^ 0) real numbers. We use the term linear topological space with its usual meaning (not necessarily Tx), but we exclude the case where the space has the indiscrete topology (see [1, 3.3, pp. 123-127]). A linear topological space is said to be a locally bounded space if there is a bounded neighbourhood of 0—which comes to the same thing as saying that there is a neighbourhood U of 0 such that the sets {(1/n) U} (n = 1,2,—) form a base at 0. In §1 we give a necessary and sufficient condition, in terms of invariant pseudo- metrics, for a linear topological space to be locally bounded. In §2 we discuss the relationship of our results with other results known on the subject. In §3 we introduce two ways of classifying the locally bounded spaces into types in such a way that each type contains exactly one of the F spaces (0 < p ^ 1), and show that these two methods of classification turn out to be identical. Also in §3 we prove a metrization theorem for locally bounded spaces, which is related to the normal metrization theorem for uniform spaces, but which uses a different induction procedure. In §4 we introduce a large class of linear topological spaces which includes the locally convex spaces and the locally bounded spaces, and for which one of the more important results on boundedness in locally convex spaces is valid. -

C H a P T E R § Methods Related to the Norm Al Equations
¡ ¢ £ ¤ ¥ ¦ § ¨ © © © © ¨ ©! "# $% &('*),+-)(./+-)0.21434576/),+98,:%;<)>=,'41/? @%3*)BAC:D8E+%=B891GF*),+H;I?H1KJ2.21K8L1GMNAPO45Q5R)S;S+T? =RU ?H1*)>./+EAVOKAPM ;<),5 ?H1G;P8W.XAVO4575R)S;S+Y? =Z8L1*)/[%\Z1*)]AB3*=,'Q;<)B=,'41/? @%3*)RAP8LU F*)BA(;S'*)Z)>@%3/? F*.4U ),1G;^U ?H1*)>./+ APOKAP;_),5a`Rbc`^dfeg`Rbih,jk=>.4U U )Blm;B'*)n1K84+o5R.EUp)B@%3*.K;q? 8L1KA>[r\0:D;_),1Ejp;B'/? A2.4s4s/+t8/.,=,' b ? A7.KFK84? l4)>lu?H1vs,+D.*=S;q? =>)m6/)>=>.43KA<)W;B'*)w=B8E)IxW=K? ),1G;W5R.K;S+Y? yn` `z? AW5Q3*=,'|{}84+-A_) =B8L1*l9? ;I? 891*)>lX;B'*.41Q`7[r~k8K{i)IF*),+NjL;B'*)71K8E+o5R.4U4)>@%3*.G;I? 891KA0.4s4s/+t8.*=,'w5R.BOw6/)Z.,l4)IM @%3*.K;_)7?H17A_8L5R)QAI? ;S3*.K;q? 8L1KA>[p1*l4)>)>lj9;B'*),+-)Q./+-)Q)SF*),1.Es4s4U ? =>.K;q? 8L1KA(?H1Q{R'/? =,'W? ;R? A s/+-)S:Y),+o+D)Blm;_8|;B'*)W3KAB3*.4Urc+HO4U 8,F|AS346KABs*.,=B)Q;_)>=,'41/? @%3*)BAB[&('/? A]=*'*.EsG;_),+}=B8*F*),+tA7? ;PM ),+-.K;q? F*)75R)S;S'K8ElAi{^'/? =,'Z./+-)R)K? ;B'*),+pl9?+D)B=S;BU OR84+k?H5Qs4U ? =K? ;BU O2+-),U .G;<)Bl7;_82;S'*)Q1K84+o5R.EU )>@%3*.G;I? 891KA>[ mWX(fQ - uK In order to solve the linear system 7 when is nonsymmetric, we can solve the equivalent system b b [¥K¦ ¡¢ £N¤ which is Symmetric Positive Definite. This system is known as the system of the normal equations associated with the least-squares problem, [ ¦ £N¤ minimize §* R¨©7ª§*«9¬ Note that (8.1) is typically used to solve the least-squares problem (8.2) for over- ®°¯± ±²³® determined systems, i.e., when is a rectangular matrix of size , . -

Surjective Isometries on Grassmann Spaces 11
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Repository of the Academy's Library SURJECTIVE ISOMETRIES ON GRASSMANN SPACES FERNANDA BOTELHO, JAMES JAMISON, AND LAJOS MOLNAR´ Abstract. Let H be a complex Hilbert space, n a given positive integer and let Pn(H) be the set of all projections on H with rank n. Under the condition dim H ≥ 4n, we describe the surjective isometries of Pn(H) with respect to the gap metric (the metric induced by the operator norm). 1. Introduction The study of isometries of function spaces or operator algebras is an important research area in functional analysis with history dating back to the 1930's. The most classical results in the area are the Banach-Stone theorem describing the surjective linear isometries between Banach spaces of complex- valued continuous functions on compact Hausdorff spaces and its noncommutative extension for general C∗-algebras due to Kadison. This has the surprising and remarkable consequence that the surjective linear isometries between C∗-algebras are closely related to algebra isomorphisms. More precisely, every such surjective linear isometry is a Jordan *-isomorphism followed by multiplication by a fixed unitary element. We point out that in the aforementioned fundamental results the underlying structures are algebras and the isometries are assumed to be linear. However, descriptions of isometries of non-linear structures also play important roles in several areas. We only mention one example which is closely related with the subject matter of this paper. This is the famous Wigner's theorem that describes the structure of quantum mechanical symmetry transformations and plays a fundamental role in the probabilistic aspects of quantum theory. -
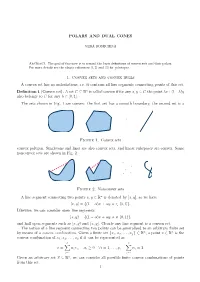
POLARS and DUAL CONES 1. Convex Sets
POLARS AND DUAL CONES VERA ROSHCHINA Abstract. The goal of this note is to remind the basic definitions of convex sets and their polars. For more details see the classic references [1, 2] and [3] for polytopes. 1. Convex sets and convex hulls A convex set has no indentations, i.e. it contains all line segments connecting points of this set. Definition 1 (Convex set). A set C ⊆ Rn is called convex if for any x; y 2 C the point λx+(1−λ)y also belongs to C for any λ 2 [0; 1]. The sets shown in Fig. 1 are convex: the first set has a smooth boundary, the second set is a Figure 1. Convex sets convex polygon. Singletons and lines are also convex sets, and linear subspaces are convex. Some nonconvex sets are shown in Fig. 2. Figure 2. Nonconvex sets A line segment connecting two points x; y 2 Rn is denoted by [x; y], so we have [x; y] = f(1 − α)x + αy; α 2 [0; 1]g: Likewise, we can consider open line segments (x; y) = f(1 − α)x + αy; α 2 (0; 1)g: and half open segments such as [x; y) and (x; y]. Clearly any line segment is a convex set. The notion of a line segment connecting two points can be generalised to an arbitrary finite set n n by means of a convex combination. Given a finite set fx1; x2; : : : ; xpg ⊂ R , a point x 2 R is the convex combination of x1; x2; : : : ; xp if it can be represented as p p X X x = αixi; αi ≥ 0 8i = 1; : : : ; p; αi = 1: i=1 i=1 Given an arbitrary set S ⊆ Rn, we can consider all possible finite convex combinations of points from this set. -

Locally Solid Riesz Spaces with Applications to Economics / Charalambos D
http://dx.doi.org/10.1090/surv/105 alambos D. Alipr Lie University \ Burkinshaw na University-Purdue EDITORIAL COMMITTEE Jerry L. Bona Michael P. Loss Peter S. Landweber, Chair Tudor Stefan Ratiu J. T. Stafford 2000 Mathematics Subject Classification. Primary 46A40, 46B40, 47B60, 47B65, 91B50; Secondary 28A33. Selected excerpts in this Second Edition are reprinted with the permissions of Cambridge University Press, the Canadian Mathematical Bulletin, Elsevier Science/Academic Press, and the Illinois Journal of Mathematics. For additional information and updates on this book, visit www.ams.org/bookpages/surv-105 Library of Congress Cataloging-in-Publication Data Aliprantis, Charalambos D. Locally solid Riesz spaces with applications to economics / Charalambos D. Aliprantis, Owen Burkinshaw.—2nd ed. p. cm. — (Mathematical surveys and monographs, ISSN 0076-5376 ; v. 105) Rev. ed. of: Locally solid Riesz spaces. 1978. Includes bibliographical references and index. ISBN 0-8218-3408-8 (alk. paper) 1. Riesz spaces. 2. Economics, Mathematical. I. Burkinshaw, Owen. II. Aliprantis, Char alambos D. III. Locally solid Riesz spaces. IV. Title. V. Mathematical surveys and mono graphs ; no. 105. QA322 .A39 2003 bib'.73—dc22 2003057948 Copying and reprinting. Individual readers of this publication, and nonprofit libraries acting for them, are permitted to make fair use of the material, such as to copy a chapter for use in teaching or research. Permission is granted to quote brief passages from this publication in reviews, provided the customary acknowledgment of the source is given. Republication, systematic copying, or multiple reproduction of any material in this publication is permitted only under license from the American Mathematical Society. -

On the Ekeland Variational Principle with Applications and Detours
Lectures on The Ekeland Variational Principle with Applications and Detours By D. G. De Figueiredo Tata Institute of Fundamental Research, Bombay 1989 Author D. G. De Figueiredo Departmento de Mathematica Universidade de Brasilia 70.910 – Brasilia-DF BRAZIL c Tata Institute of Fundamental Research, 1989 ISBN 3-540- 51179-2-Springer-Verlag, Berlin, Heidelberg. New York. Tokyo ISBN 0-387- 51179-2-Springer-Verlag, New York. Heidelberg. Berlin. Tokyo No part of this book may be reproduced in any form by print, microfilm or any other means with- out written permission from the Tata Institute of Fundamental Research, Colaba, Bombay 400 005 Printed by INSDOC Regional Centre, Indian Institute of Science Campus, Bangalore 560012 and published by H. Goetze, Springer-Verlag, Heidelberg, West Germany PRINTED IN INDIA Preface Since its appearance in 1972 the variational principle of Ekeland has found many applications in different fields in Analysis. The best refer- ences for those are by Ekeland himself: his survey article [23] and his book with J.-P. Aubin [2]. Not all material presented here appears in those places. Some are scattered around and there lies my motivation in writing these notes. Since they are intended to students I included a lot of related material. Those are the detours. A chapter on Nemyt- skii mappings may sound strange. However I believe it is useful, since their properties so often used are seldom proved. We always say to the students: go and look in Krasnoselskii or Vainberg! I think some of the proofs presented here are more straightforward. There are two chapters on applications to PDE. -

Approximation Boundedness Surjectivity
APPROXIMATION BOUNDEDNESS SURJECTIVITY Olav Kristian Nygaard Dr. scient. thesis, University of Bergen, 2001 Approximation, Boundedness, Surjectivity Olav Kr. Nygaard, 2001 ISBN 82-92-160-08-6 Contents 1Theframework 9 1.1 Separability, bases and the approximation property ....... 13 1.2Thecompletenessassumption................... 16 1.3Theoryofclosed,convexsets................... 19 2 Factorization of weakly compact operators and the approximation property 25 2.1Introduction............................. 25 2.2 Criteria of the approximation property in terms of the Davis- Figiel-Johnson-Pe'lczy´nskifactorization.............. 27 2.3Uniformisometricfactorization.................. 33 2.4 The approximation property and ideals of finite rank operators 36 2.5 The compact approximation property and ideals of compact operators.............................. 39 2.6 From approximation properties to metric approximation prop- erties................................. 41 3 Boundedness and surjectivity 49 3.1Introduction............................. 49 3.2Somemorepreliminaries...................... 52 3.3 The boundedness property in normed spaces . ....... 57 3.4ThesurjectivitypropertyinBanachspaces........... 59 3.5 The Seever property and the Nikod´ymproperty......... 63 3.6 Some results on thickness in L(X, Y )∗ .............. 63 3.7Somequestionsandremarks.................... 65 4 Slices in the unit ball of a uniform algebra 69 4.1Introduction............................. 69 4.2Thesliceshavediameter2..................... 70 4.3Someremarks........................... -

The Column and Row Hilbert Operator Spaces
The Column and Row Hilbert Operator Spaces Roy M. Araiza Department of Mathematics Purdue University Abstract Given a Hilbert space H we present the construction and some properties of the column and row Hilbert operator spaces Hc and Hr, respectively. The main proof of the survey is showing that CB(Hc; Kc) is completely isometric to B(H ; K ); in other words, the completely bounded maps be- tween the corresponding column Hilbert operator spaces is completely isometric to the bounded operators between the Hilbert spaces. A similar theorem for the row Hilbert operator spaces follows via duality of the operator spaces. In particular there exists a natural duality between the column and row Hilbert operator spaces which we also show. The presentation and proofs are due to Effros and Ruan [1]. 1 The Column Hilbert Operator Space Given a Hilbert space H , we define the column isometry C : H −! B(C; H ) given by ξ 7! C(ξ)α := αξ; α 2 C: Then given any n 2 N; we define the nth-matrix norm on Mn(H ); by (n) kξkc;n = C (ξ) ; ξ 2 Mn(H ): These are indeed operator space matrix norms by Ruan's Representation theorem and thus we define the column Hilbert operator space as n o Hc = H ; k·kc;n : n2N It follows that given ξ 2 Mn(H ) we have that the adjoint operator of C(ξ) is given by ∗ C(ξ) : H −! C; ζ 7! (ζj ξ) : Suppose C(ξ)∗(ζ) = d; c 2 C: Then we see that cd = (cj C(ξ)∗(ζ)) = (cξj ζ) = c(ζj ξ) = (cj (ζj ξ)) : We are also able to compute the matrix norms on rectangular matrices.