Connecting the Last Billion
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Head Coach, Tampa Bay Lightning
Table of Contents ADMINISTRATION Team History 270 - 271 All-Time Individual Record 272 - 274 Company Directory 4 - 5 All-Time Team Records 274 - 279 Executives 6 - 11 Scouting Staff 11 - 12 Coaching Staff 13 - 16 PLAYOFF HISTORY & RECORDS Hockey Operations 17 - 20 All-Time Playoff Scoring 282 Broadcast 21 - 22 Playoff Firsts 283 All-Time Playoff Results 284 - 285 2013-14 PLAYER ROSTER Team Playoff Records 286 - 287 Individual Playoff Records 288 - 289 2013-14 Player Roster 23 - 98 Minor League Affiliates 99 - 100 MISCELLANEOUS NHL OPPONENTS In the Community 292 NHL Executives 293 NHL Opponents 109 - 160 NHL Officials and Referees 294 Terms Glossary 295 2013-14 SEASON IN REVIEW Medical Glossary 296 - 298 Broadcast Schedule 299 Final Standings, Individual Leaders, Award Winners 170 - 172 Media Regulations and Policies 300 - 301 Team Statistics, Game-by-Game Results 174 - 175 Frequently Asked Questions 302 - 303 Home and Away Results 190 - 191 Season Summary, Special Teams, Overtime/Shootout 176 - 178 Highs and Lows, Injuries 179 Win / Loss Record 180 HISTORY & RECORDS Season Records 182 - 183 Special Teams 184 Season Leaders 185 All-Time Records 186 - 187 Last Trade With 188 Records vs. Opponents 189 Overtime/Shootout Register 190 - 191 Overtime History 192 Year by Year Streaks 193 All-Time Hat Tricks 194 All-Time Attendance 195 All-Time Shootouts & Penalty Shots 196-197 Best and Worst Record 198 Season Openers and Closers 199 - 201 Year by Year Individual Statistics and Game Results 202 - 243 All-Time Lightning Preseason Results 244 All-Time -

Buffalo Sabres Game Notes
Buffalo Sabres Game Notes Sat, Mar 29, 2014 NHL Game #1110 Buffalo Sabres 20 - 45 - 8 (48 pts) Tampa Bay Lightning 40 - 24 - 9 (89 pts) Team Game: 74 12 - 20 - 5 (Home) Team Game: 74 21 - 8 - 6 (Home) Home Game: 38 8 - 25 - 3 (Road) Road Game: 39 19 - 16 - 3 (Road) # Goalie GP W L OT GAA SV% # Goalie GP W L OT GAA SV% 1 Jhonas Enroth 28 4 17 5 2.82 .911 30 Ben Bishop 57 35 11 7 2.17 .926 31 Matt Hackett 3 1 2 0 3.02 .919 39 Anders Lindback 20 5 12 2 3.26 .878 34 Michal Neuvirth 15 4 8 2 2.78 .921 50 Nathan Lieuwen 4 0 2 0 3.00 .901 # P Player GP G A P +/- PIM # P Player GP G A P +/- PIM 4 D Jamie McBain 60 4 11 15 -11 10 2 D Eric Brewer (A) 68 1 13 14 6 57 5 D Chad Ruhwedel 16 0 0 0 -3 2 3 D Keith Aulie 14 0 1 1 -2 9 6 D Mike Weber 59 0 5 5 -29 67 6 D Sami Salo 64 3 13 16 10 16 10 D Christian Ehrhoff (A) 71 6 25 31 -19 34 7 D Radko Gudas 64 3 17 20 3 138 17 C Torrey Mitchell 63 1 8 9 -4 25 8 D Mark Barberio 47 5 5 10 12 28 19 C Cody Hodgson 63 16 20 36 -24 20 9 C Tyler Johnson 73 22 25 47 19 22 20 D Henrik Tallinder (A) 59 2 5 7 -23 32 11 C Tom Pyatt 23 3 4 7 0 4 21 R Drew Stafford (A) 65 15 16 31 -14 35 12 L Ryan Malone 53 5 9 14 -5 61 22 L Johan Larsson 22 0 2 2 -2 15 16 R Teddy Purcell 73 12 28 40 1 14 23 L Ville Leino 52 0 12 12 -14 8 17 C Alex Killorn 73 15 23 38 9 57 24 C Zenon Konopka 58 1 2 3 -10 83 18 L Ondrej Palat 73 19 32 51 27 18 27 R Matt D'Agostini 49 4 6 10 -12 22 19 R B.J. -

Avalanche 2.7.09
St Louis Volume 4, Issue 27 Game Time February 7, 2009 Four Dollars To Waive Your Doubts The Game Day Guide To St. Louis Blues Hockey Established in 2005 By Brad Lee playing pretty good, I thought my season was starting to come around,” Legace said, referring to his meltdown in Detroit Many Blues fans expected the end of the Manny Legacy era Monday night. “Then to have the carpet pulled out from here in St. Louis was coming quickly. We just didn’t think it underneath you, it’s not a good feeling.” would happen Friday. Here’s the thing that’s not expressed in those words from Twenty-four hours ago the Blues placed their former All-Star Legace. The NHL is a business. And when the team is counting on goaltender on waivers with the intention of demoting him to the a player to stop pucks and win games, patience will wear thin. The Peoria Rivermen. He passed through waivers without a team Blues are under a ton of pressure to show results in order to claiming him and he is now expected to report to Central keep the turnstiles clicking and the beer vendors Illinois on Monday. Looking at Legace’s numbers, pouring. Legace talked about some things during you can see why the Blues made this move. But the interview that hinted at the business of there has been plenty of talk of Legace’s hockey while also saying the right things in attitude around the team in the wake of the order to keep Blues fans sympathetic to him. -

Anaheim Ducks Game Notes
Anaheim Ducks Game Notes Fri, Jan 31, 2020 NHL Game #791 Anaheim Ducks 20 - 25 - 5 (45 pts) Tampa Bay Lightning 30 - 15 - 5 (65 pts) Team Game: 51 12 - 9 - 3 (Home) Team Game: 51 15 - 7 - 2 (Home) Home Game: 25 8 - 16 - 2 (Road) Road Game: 27 15 - 8 - 3 (Road) # Goalie GP W L OT GAA SV% # Goalie GP W L OT GAA SV% 30 Ryan Miller 13 5 5 2 3.01 .904 35 Curtis McElhinney 13 5 6 2 3.10 .902 36 John Gibson 38 15 20 3 2.96 .905 88 Andrei Vasilevskiy 37 25 9 3 2.53 .918 # P Player GP G A P +/- PIM # P Player GP G A P +/- PIM 4 D Cam Fowler 50 9 16 25 1 14 2 D Luke Schenn 15 1 0 1 -9 15 5 D Korbinian Holzer 38 1 3 4 -4 31 9 C Tyler Johnson 45 12 12 24 5 10 6 D Erik Gudbranson 46 4 5 9 2 93 13 C Cedric Paquette 42 4 9 13 -5 24 14 C Adam Henrique 50 17 10 27 -3 16 14 L Pat Maroon 45 6 10 16 1 60 15 C Ryan Getzlaf 48 11 22 33 -11 35 17 L Alex Killorn 48 20 20 40 15 12 20 L Nicolas Deslauriers 38 1 5 6 -6 68 18 L Ondrej Palat 49 12 19 31 20 18 24 C Carter Rowney 50 6 5 11 -2 12 21 C Brayden Point 47 18 26 44 16 9 25 R Ondrej Kase 44 6 14 20 -4 10 22 D Kevin Shattenkirk 50 7 20 27 21 24 29 C Devin Shore 32 2 4 6 -5 8 23 C Carter Verhaeghe 37 6 4 10 -6 6 32 D Jacob Larsson 40 1 3 4 -12 10 27 D Ryan McDonagh 44 1 11 12 2 13 33 R Jakob Silfverberg 45 15 14 29 -3 12 37 C Yanni Gourde 50 6 13 19 -5 32 34 C Sam Steel 45 4 12 16 -9 12 44 D Jan Rutta 30 1 5 6 5 14 37 L Nick Ritchie 29 4 7 11 -2 58 55 D Braydon Coburn 25 1 1 2 6 6 38 C Derek Grant 38 10 5 15 -1 24 67 C Mitchell Stephens 22 2 2 4 -4 4 42 D Josh Manson 31 1 4 5 -4 25 71 C Anthony Cirelli 49 12 -

Ebook Free Hockey's Young Superstars (Discoveries In
Ebook Free Hockey's Young Superstars (Discoveries In Palaeontology) Every young hockey fan will want a copy of this book, which gives the lowdown on the best up-and-coming players in the sport today. The stars come from a variety of different teams and backgrounds, including Canada, the United States, Eastern Europe, and Scandinavia. Each in-depth profile contains details on the player’s strengths and weaknesses on the ice, achievements and statistics, and how he made it to the NHL. In addition to interviews with the players themselves, the chapters are rounded out with input from coaches, teammates, and broadcasters. Profiled players include Tomas Kaberle of the Toronto Maple Leafs, Eric Brewer of the Edmonton Oilers, Marco Sturm of the San Jose Sharks, Joe Thornton of the Boston Bruins, Derek Morris of the Colorado Avalanche, Brad Richards of the Tampa Bay Lightning, Marian Gaborik of the Minnesota Wild, Dany Heatley of the Atlanta Thrashers, Marian Hossa of the Ottawa Senators, and Simon Gagne of the Philadelphia Flyers. Series: Discoveries in Palaeontology Paperback: 120 pages Publisher: Raincoast Books (November 2003) Language: English ISBN-10: 1551926377 ISBN-13: 978-1551926377 Product Dimensions: 10 x 8 x 0.5 inches Shipping Weight: 1.1 pounds Average Customer Review: Be the first to review this item Best Sellers Rank: #6,072,073 in Books (See Top 100 in Books) #43 in Books > Teens > Sports & Outdoors > Hockey #359 in Books > Teens > Biographies > Sports #565 in Books > Biographies & Memoirs > Sports & Outdoors > Hockey Hockey's Young Superstars (Discoveries in Palaeontology) Hockey Workout: Complete Off-Season Hockey Workout: Hockey agility & speed drills, hockey plyometric workouts, hockey core exercises, hockey weight training and anaerobic training for hockey players. -

Prince George Cougars
Prince George Cougars: Proud to be Locally Owned & Operated Over ¼ century in Prince George New Ownership purchased team in May 2014: Greg Pocock, Eric Brewer, Dan Hamhuis, John Pateman, Ernest Ouellet, Ray Fortier WHL is the Highest Level of Sports Entertainment in Northern BC Dan Hamhuis Derek Boogaard Eric Brewer Devin Setoguchi Zdeno Chara Martin Marincin Dustin Jansen Harkins Byfugelien ….and many Brett Connolly others! Chris Mason Prince George Cougars & the WHL Add Value to Quality of Life, Recruiting & Retaining Employees in Prince George Economic Impact of WHL in Prince George: 14 Full Time Staff and dozens of part time staff Including many who moved to PG Food & Beverage staff TicketsNorth Box office staff Security, First Aid, PT City Staff, etc.! Hotels, restaurants gear their staffing schedules according to PG Cougars games CHL Economic Impact Study Genuine Partnership with CN Centre & City: Significant Capital Investment Since 2014 Office space renovations Dressing room renovations Laundry Room Media Box renovations LOGE seating area Wi-Fi & fiber optics upgrades Sound System Scoreclock replacement Video cameras Genuine Partnership with CN Centre & City: “What can we do to help?” Recent rink closures & COVID restrictions Partnering in attracting and facilitating events: o 2019 Women’s World Curling o 2018 Brett Connolly Stanley Cup Celebration o 2017 Telus Cup National Championship o 2015 Canada Winter Games o 2015 Vancouver Canucks Training Camp Offer our dressing room, laundry services & -

Mtois F/A L/G 6’2” 215 01/08/99 Longueuil, Que./Qc Anaheim (NHL) 73 Brandon Pirri F/A L/G 6’1” 180 04/10/91 Toronto, Ont
2021 IIHF WORLD CHAMPIONSHIP CHAMPIONNAT MONDIAL 2021 DE L’IIHF GAME NOTES / NOTES SUR LE MATCH CANADA VS. GERMANY CANADA C. ALLEMAGNE MONDAY, MAY 24, 2021 / LUNDI 24 MAI 2021 CANADA’S NATIONAL MEN’S TEAM ÉQUIPE NATIONALE MASCULINE DU CANADA # Name P S/C Ht. Wt. Born Hometown Club Team No Nom P T/A Gr. Pds DDN Ville d’origine Club 33 Adin Hill G L/G 6’6” 202 05/11/96 Calgary, Alta./Alb. Arizona (NHL) 35 Darcy Kuemper G L/G 6’5” 215 05/05/90 Saskatoon, Sask. Arizona (NHL) 65 Michael DiPietro G L/G 6’0” 200 06/09/99 Amherstburg, Ont. Vancouver (NHL) 2 Braden Schneider D R/D 6’2” 207 09/20/01 Prince Albert, Sask. Brandon (WHL) 5 Jacob Bernard-Docker D R/D 6’0” 190 06/30/00 Canmore, Alta./Alb. Ottawa (NHL) 6 Colin Miller D R/D 6’1” 199 10/29/92 Sault Ste. Marie, Ont. Buffalo (NHL) 25 Owen Power D L/G 6’5” 214 11/22/02 Mississauga, Ont. University of Michigan (Big Ten) 26 Sean Walker D R/D 5’11” 196 11/13/94 Keswick, Ont. Los Angeles (NHL) 38 Mario Ferraro D L/G 5’11” 185 09/17/98 King City, Ont. San Jose (NHL) 70 Troy Stecher D R/D 5’10” 186 04/07/94 Richmond, B.C./C.-B. Detroit (NHL) 74 Nicolas Beaudin D L/G 5’11” 168 11/07/99 Châteauguay, Que./Qc Chicago (NHL) 8 Liam Foudy F/A L/G 6’2” 193 02/04/00 Scarborough, Ont. -
Special Section
FRIDAY, OCTOBER 7, 2011 ଁ SECTION E Is this the year they grab it? E2 | CAPITALS 2011-12 ଁ FRIDAY, OCTOBER 7, 2011 COVER STORY ACUP FORTHE CAPS? ANDREW HARNIK/THE WASHINGTON TIMES Right wing Mike Knuble (from left), left wing Alex Ovechkin and center Nicklas Backstrom constitute the bulk of the firepower on the Capitals’ top two lines and serve as the foundation for leadership. They again will be counted on to provide ample offense as Washington takes aim at its first Stanley Cup. BY STEPHEN WHYNO to win a title. THE WASHINGTON TIMES It’s not unrealistic to think When it didn’t work out, McPhee took a similar tone in free agency: Not blowing the Caps up but getting Ward, Halpern, t’s the dream of owner Ted Leonsis, Vokoun and Hamrlik after dealing away a who said he’d “cry like a baby” if it this is the season Washington first-round pick for Brouwer. happened. It’s the dream of public “I think [McPhee]did a great job. They address announcer Wes Johnson, brings home a championship didn’t just go willy-nilly and pick free who said he wouldn’t be able to agents,” Boudreau said. “They picked guys hear himself if it happened. It’s the Some fans decried the magazine’s pre- points in the NHL. Even last season, they that they thought were not only really dream of every kid who wants to diction as a jinx, just like a picture last sea- made a run to finish atop the Eastern Con- good but would be good fits for our hockey play in the NHL. -
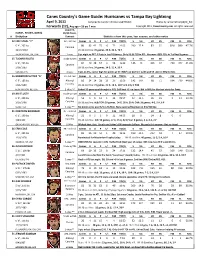
4 9 Vs Lightning.Xlsx
Canes Country's Game Guide: Hurricanes vs Tampa Bay Lightning April 9, 2011 compiled by Carolyn Christians (@HMof2) Photos by Jamie Kellner (@jbk_ltd) Forwards (12), Avg age = 26 yrs 7 mos Copyright 2011, CanesCountry.com . All rights reserved. acquired, NAME , HT/WT, DOB & 09/10 Team, # Birthplace Contract Statistics from this year, last season, and other notes 12 ERIC STAAL "C" 03 - 1st rnd Games G A P +/- PIM TOI/G S S% HT BS FW FL FO% 6' 4", 205 lbs 80 33 42 75 -6 72 21:55 290 11.4 81 31 820 899 47.7% Carolina 10/29/1984 09-10 stat line: 70 games, 29 G, 41 A, 70 P THUNDER BAY, ON, CAN 1-way 3 pt night vs DET. 12 pts in last 10 Games. Only 15:36 TOI in ATL. Has won >50% FO's in 7 of last 8 games 15 TUOMO RUUTU Trade w/CHI Games G A P +/- PIM TOI/G S S% HT BS FW FL FO% 6' 0", 205 lbs 81 19 38 57 4 54 16:49 146 13 306 37 259 372 41.0% Carolina 2/16/1983 09-10 stat line: 54 games, 14 G, 21 A, 35 P VANTAA, FIN 1-way 3 pts in ATL, career high for points at 57. RW/C on 2nd line w/36 and 53. 2nd in NHL for hits. 16 BRANDON SUTTER "A" 07- 1st rnd Games G A P +/- PIM TOI/G S S% HT BS FW FL FO% 6' 3", 183 lbs Albany/ 81 14 14 28 13 25 16:50 142 9.9 68 71 594 739 44.6% 2/14/1989 Carolina 09-10 stat line: 72 games, 21 G, 19 A, 40 P and only 2 PIM HUNTINGTON, NY, USA 2-Way ^^ Ended 10-game goal drought in ATL. -

There Is Nothing Like the Sweet Taste of Gold
Publisher: International Ice Hockey Federation, Editor-in-Chief: Jan-Ake Edvinsson Supervising Editor: Kimmo Leinonen Editor: Szymon Szemberg, Assistant Editor: Jenny Wiedeke June 2004 - Vol 8 - No 3 There is nothing like the sweet taste of gold Back in the April issue of this publication, I wrote that the 2004 IIHF World Championship in the Czech Republic had the potential to be the best tournament ever. It proved to be a correct assumption. 552,097 spectators in Prague and Ostrava made this a festival which we will never forget. RENÉ FASEL EDITORIAL ■■ For some years now we have been contemplating whether the record of 526,172 fans from Finland 1997 would ever be broken. And, finally, seven years later, the IIHF World Championship has a new attendance record. More than 25,000 spectators surpassed the previous mark. Our new record figure of 552,097 means that an ave- rage of almost 10,000 spectators (9,859 to be exact) attended the 56 games of the 68th IIHF World Championship. This is a remarkable number and a testimony to the passion for our game in the Czech Republic. This was the ninth time that an IIHF World Championship was hosted in Prague, which now defi- nitely deserves to be called the unofficial capital of the tournament. ■■ All this wouldn’t have been possible if not for the Sazka Arena, which must rank among the top three or four ice hockey venues in the world today. The 17,300 seat state-of-the-art arena was everything we were hoping for in terms of spectator comfort as well as facilitating the needs of teams and officials. -

Jan 05 Maryland's Omar Gonzalez Is a Hot Prospect As a Few Clubs
Jan 05 Maryland's Omar Gonzalez is a hot prospect as a few clubs This may be the 1st of a couple ridicule drafts that guide up to then week?¡¥s MLS SuperDraft,create football jersey. Of lesson I want only be working with the first round as this jeer draft as the second amongst forth circular order hasn?¡¥t been officially announced yet. A lot could procurable alter also as some players mentioned are on the fences nearly going to the blueprint this annual or waiting until afterward year,new nike nfl jerseys. Also there are expected to be a slew of trades between immediately and then week. While no an is expected as of right immediately to transfer up and tug a Kansas City to commerce into the top spot this daily I do discern abundance of crews looking to package deals to migrate up to the second overall pick,nike custom football jerseys. Reports right swiftly suggest that New England,new nike football uniforms, Dallas, LA, and DC always have interest among trading up to that second overall elect From what I am hearing we could discern a handle done as soon as the end of this week. Also, with the aggregate of picks that some clubs have expect them to send them off as some others ambition be looking accessory picks. Lastly, we longing know a lot more behind the MLS Combine too which begins at the kill of this week. Usually the Combine is a great trading ground as clubs You can expect to discern a few deals worked out at this year Combine as sure. -

2019 World Under-17 Hockey Challenge Défi Mondial De Hockey Des Moins De 17 Ans 2019
2019 WORLD UNDER-17 HOCKEY CHALLENGE DÉFI MONDIAL DE HOCKEY DES MOINS DE 17 ANS 2019 ALL-TIME DRAFTED PLAYERS JOUEURS REPÊCHÉS DE TOUS LES TEMPS TOTAL: 1,865 * THROUGH THE 2019 NHL DRAFT * * REPÊCHAGE 2019 DE LA LNH INCLUS * 1st Round / 1re ronde 436 Alexander Alexeyev (2018 – Washington) 2015 – Russia/Russie Bryan Allen (1998 – Vancouver) 1997 – Ontario Karl Alzner (2007 – Washington) 2005 – Pacific/Pacifique Lias Andersson (2017 – New York Rangers) 2014 – Sweden/Suède Joel Armia (2011 – Buffalo) 2010 – Finland/Finlande Carter Ashton (2009 – Tampa Bay) 2008 – West/Ouest Anton Babchuk (2002 – Chicago) 2001 – Russia/Russie Christian Backman (1998 – St. Louis) 1997 – Sweden/Suède Joshua Bailey (2008 – New York Islanders) 2006 – Ontario Jake Bean (2016 – Carolina) 2014 – Canada Black/Noirs Nathan Beaulieu (2011 – Montreal) 2009 – Atlantic/Atlantique Anthony Beauvillier (2015 – New York Islanders) 2014 - Québec John Beecher (2019 – Boston) 2017 – United States/États-Unis Shawn Belle (2003 – St. Louis) 2002 – Pacific/Pacifique Sam Bennett (2014 – Calgary) 2013 – Ontario Bryan Berard (1995 – Ottawa) 1994 – United States/États-Unis Jonathan Bernier (2006 – Los Angeles) 2005 – Québec Steve Bernier (2003 – San Jose) 2001 & 2002 – Québec Tyler Biggs (2011 – Toronto) 2010 – United States/États-Unis Tobias Björnfot (2019 – Los Angeles) 2017 – Sweden/Suède Dan Blackburn (2001 – New York Rangers) 2000 – Pacific/Pacifique Conner Bleackley (2014 – Colorado) 2013 – Pacific/Pacifique Matthew Boldy (2019 – Minnesota) 2017 – United States/États-Unis Radek