Uwsgi Documentation Release 1.9
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Differential Fuzzing the Webassembly
Master’s Programme in Security and Cloud Computing Differential Fuzzing the WebAssembly Master’s Thesis Gilang Mentari Hamidy MASTER’S THESIS Aalto University - EURECOM MASTER’STHESIS 2020 Differential Fuzzing the WebAssembly Fuzzing Différentiel le WebAssembly Gilang Mentari Hamidy This thesis is a public document and does not contain any confidential information. Cette thèse est un document public et ne contient aucun information confidentielle. Thesis submitted in partial fulfillment of the requirements for the degree of Master of Science in Technology. Antibes, 27 July 2020 Supervisor: Prof. Davide Balzarotti, EURECOM Co-Supervisor: Prof. Jan-Erik Ekberg, Aalto University Copyright © 2020 Gilang Mentari Hamidy Aalto University - School of Science EURECOM Master’s Programme in Security and Cloud Computing Abstract Author Gilang Mentari Hamidy Title Differential Fuzzing the WebAssembly School School of Science Degree programme Master of Science Major Security and Cloud Computing (SECCLO) Code SCI3084 Supervisor Prof. Davide Balzarotti, EURECOM Prof. Jan-Erik Ekberg, Aalto University Level Master’s thesis Date 27 July 2020 Pages 133 Language English Abstract WebAssembly, colloquially known as Wasm, is a specification for an intermediate representation that is suitable for the web environment, particularly in the client-side. It provides a machine abstraction and hardware-agnostic instruction sets, where a high-level programming language can target the compilation to the Wasm instead of specific hardware architecture. The JavaScript engine implements the Wasm specification and recompiles the Wasm instruction to the target machine instruction where the program is executed. Technically, Wasm is similar to a popular virtual machine bytecode, such as Java Virtual Machine (JVM) or Microsoft Intermediate Language (MSIL). -

Dynamic Web Pages with the Embedded Web Server
Dynamic Web Pages With The Embedded Web Server The Digi-Geek’s AJAX Workbook (NET+OS, XML, & JavaScript) Version 1.0 5/4/2011 Page 1 Copyright Digi International, 2011 Table of Contents Chapter 1 - How to Use this Guide ............................................................................................................... 5 Prerequisites – If You Can Ping, You Can Use This Thing! ..................................................................... 5 Getting Help with TCP/IP and Wi-Fi Setup ............................................................................................ 5 The Study Guide or the Short Cut? ....................................................................................................... 5 C Code ................................................................................................................................................... 6 HTML Code ............................................................................................................................................ 6 XML File ................................................................................................................................................. 6 Provide us with Your Feedback ............................................................................................................. 6 Chapter 2 - The Server-Client Relationship ................................................................................................... 7 Example – An Analogy for a Normal HTML page ................................................................................. -

Lightweight Django USING REST, WEBSOCKETS & BACKBONE
Lightweight Django USING REST, WEBSOCKETS & BACKBONE Julia Elman & Mark Lavin Lightweight Django LightweightDjango How can you take advantage of the Django framework to integrate complex “A great resource for client-side interactions and real-time features into your web applications? going beyond traditional Through a series of rapid application development projects, this hands-on book shows experienced Django developers how to include REST APIs, apps and learning how WebSockets, and client-side MVC frameworks such as Backbone.js into Django can power the new or existing projects. backend of single-page Learn how to make the most of Django’s decoupled design by choosing web applications.” the components you need to build the lightweight applications you want. —Aymeric Augustin Once you finish this book, you’ll know how to build single-page applications Django core developer, CTO, oscaro.com that respond to interactions in real time. If you’re familiar with Python and JavaScript, you’re good to go. “Such a good idea—I think this will lower the barrier ■ Learn a lightweight approach for starting a new Django project of entry for developers ■ Break reusable applications into smaller services that even more… the more communicate with one another I read, the more excited ■ Create a static, rapid prototyping site as a scaffold for websites and applications I am!” —Barbara Shaurette ■ Build a REST API with django-rest-framework Python Developer, Cox Media Group ■ Learn how to use Django with the Backbone.js MVC framework ■ Create a single-page web application on top of your REST API Lightweight ■ Integrate real-time features with WebSockets and the Tornado networking library ■ Use the book’s code-driven examples in your own projects Julia Elman, a frontend developer and tech education advocate, started learning Django in 2008 while working at World Online. -

Modern Web Application Frameworks
MASARYKOVA UNIVERZITA FAKULTA INFORMATIKY Û¡¢£¤¥¦§¨ª«¬Æ°±²³´µ·¸¹º»¼½¾¿Ý Modern Web Application Frameworks MASTER’S THESIS Bc. Jan Pater Brno, autumn 2015 Declaration Hereby I declare, that this paper is my original authorial work, which I have worked out by my own. All sources, references and literature used or ex- cerpted during elaboration of this work are properly cited and listed in complete reference to the due source. Bc. Jan Pater Advisor: doc. RNDr. Petr Sojka, Ph.D. i Abstract The aim of this paper was the analysis of major web application frameworks and the design and implementation of applications for website content ma- nagement of Laboratory of Multimedia Electronic Applications and Film festival organized by Faculty of Informatics. The paper introduces readers into web application development problematic and focuses on characte- ristics and specifics of ten selected modern web application frameworks, which were described and compared on the basis of relevant criteria. Practi- cal part of the paper includes the selection of a suitable framework for im- plementation of both applications and describes their design, development process and deployment within the laboratory. ii Keywords Web application, Framework, PHP,Java, Ruby, Python, Laravel, Nette, Phal- con, Rails, Padrino, Django, Flask, Grails, Vaadin, Play, LEMMA, Film fes- tival iii Acknowledgement I would like to show my gratitude to my supervisor doc. RNDr. Petr So- jka, Ph.D. for his advice and comments on this thesis as well as to RNDr. Lukáš Hejtmánek, Ph.D. for his assistance with application deployment and server setup. Many thanks also go to OndˇrejTom for his valuable help and advice during application development. -
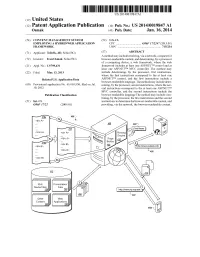
(12) Patent Application Publication (10) Pub. No.: US 2014/0019847 A1 Osmak (43) Pub
US 20140019847A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0019847 A1 OSmak (43) Pub. Date: Jan. 16, 2014 (54) CONTENT MANAGEMENT SYSTEM (52) U.S. Cl. EMPLOYINGA HYBRD WEB APPLICATION CPC .................................. G06F 17/2247 (2013.01) FRAMEWORK USPC .......................................................... 71.5/234 (71) Applicant: Telerik, AD, Sofia (BG) (57) ABSTRACT A method may include receiving, via a network, a request for (72) Inventor: Ivan Osmak, Sofia (BG) browser-renderable content, and determining, by a processor of a computing device, a web framework, where the web (21) Appl. No.: 13/799,431 framework includes at least one ASP.NETTM control and at least one ASP.NETTM MVC controller. The method may (22) Filed: Mar 13, 2013 include determining, by the processor, first instructions, where the first instructions correspond to the at least one Related U.S. Application Data ASP.NETTM control, and the first instructions include a browser-renderable language. The method may include deter (60) Provisional application No. 61/669,930, filed on Jul. mining, by the processor, second instructions, where the sec 10, 2012. ond instructions correspond to the at least one ASP.NETTM MVC controller, and the second instructions include the Publication Classification browser-renderable language The method may include com bining, by the processor, the first instructions and the second (51) Int. Cl. instructions to determine the browser-renderable content, and G06F 7/22 (2006.01) providing, via the network, the browser-renderable content. Routing Engine Ric Presentation Media Fies : Fies 22 Applications 28 Patent Application Publication Jan. 16, 2014 Sheet 1 of 8 US 2014/001.9847 A1 Patent Application Publication Jan. -

Attacking AJAX Web Applications Vulns 2.0 for Web 2.0
Attacking AJAX Web Applications Vulns 2.0 for Web 2.0 Alex Stamos Zane Lackey [email protected] [email protected] Blackhat Japan October 5, 2006 Information Security Partners, LLC iSECPartners.com Information Security Partners, LLC www.isecpartners.com Agenda • Introduction – Who are we? – Why care about AJAX? • How does AJAX change Web Attacks? • AJAX Background and Technologies • Attacks Against AJAX – Discovery and Method Manipulation – XSS – Cross-Site Request Forgery • Security of Popular Frameworks – Microsoft ATLAS – Google GWT –Java DWR • Q&A 2 Information Security Partners, LLC www.isecpartners.com Introduction • Who are we? – Consultants for iSEC Partners – Application security consultants and researchers – Based in San Francisco • Why listen to this talk? – New technologies are making web app security much more complicated • This is obvious to anybody who reads the paper – MySpace – Yahoo – Worming of XSS – Our Goals for what you should walk away with: • Basic understanding of AJAX and different AJAX technologies • Knowledge of how AJAX changes web attacks • In-depth knowledge on XSS and XSRF in AJAX • An opinion on whether you can trust your AJAX framework to “take care of security” 3 Information Security Partners, LLC www.isecpartners.com Shameless Plug Slide • Special Thanks to: – Scott Stender, Jesse Burns, and Brad Hill of iSEC Partners – Amit Klein and Jeremiah Grossman for doing great work in this area – Rich Cannings at Google • Books by iSECer Himanshu Dwivedi – Securing Storage – Hackers’ Challenge 3 • We are -

User's Manual for Spatial Data Product Specification Description
Technical Report of the Geographical Survey Institute A1-No.264 User's Manual for Spatial Data Product Specification Description May 2002 Preface to English Edition In Japan, the Geographical Survey Institute and private companies have jointly created and updated the Japanese Standards for Geographic Information (JSGI) in accordance with several standards in the draft stage to arrange implementation tests and utilization manuals since before the international standard based on ISO/TC211 si issued. User's Manual for Spatial Data Product Specification Description is created to spread the standards based on ISO/TC211 in Japan. This manual assumes that national organizations, local public organizations, and private companies use the ISO standards, and has the purpose that is different from that of ISO19131 Data Product Specifications. However, in order to help consider creating the standard for data product specifications or use the ISO standards in countries, this English version is created. The original of this manual is created from JSGI that is created in Japanese based on the draft standard created in English. Therefore, this English version is created through the processes of translation from English to Japanese, and from Japanese to English. Because of the time limit, the retranslated English technical terms are not examined carefully, and note that some terms are not correct. XML tag names are described alphabetically, but many of them are based on the Japanese alphabet (Roman character) notation instead of English because it is assumed that they are used in Japan. These tag names are not forcibly translated into English but "Note(E)" is appended to them. -

Magnetic Silica Particles Functionalized with Guanidine Derivatives For
www.nature.com/scientificreports OPEN Magnetic silica particles functionalized with guanidine derivatives for microwave‑assisted transesterifcation of waste oil Petre Chipurici1,6, Alexandru Vlaicu1,2,6, Ioan Călinescu1, Mircea Vînătoru1, Cristina Busuioc1, Adrian Dinescu3, Adi Ghebaur1,4, Edina Rusen1, Georgeta Voicu1, Maria Ignat5 & Aurel Diacon1* This study aimed to develop a facile synthesis procedure for heterogeneous catalysts based on organic guanidine derivatives superbases chemically grafted on silica‑coated Fe3O4 magnetic nanoparticles. Thus, the three organosilanes that were obtained by reacting the selected carbodiimides (N,N′‑ dicyclohexylcarbodiimide (DCC), N,N′‑diisopropylcarbodiimide (DIC), respectively 1‑ethyl‑3‑(3‑ dimethylaminopropyl) carbodiimide (EDC) with 3‑aminopropyltriethoxysilane (APTES) were used in a one‑pot synthesis stage for the generation of a catalytic active protective shell through the simultaneous hydrolysis/condensation reaction with tetraethyl orthosilicate (TEOS). The catalysts were characterized by FTIR, TGA, SEM, BET and XRD analysis confrming the successful covalent attachment of the organic derivatives in the silica shell. The second aim was to highlight the capacity of microwaves (MW) to intensify the transesterifcation process and to evaluate the activity, stability, and reusability characteristics of the catalysts. Thus, in MW‑assisted transesterifcation reactions, all catalysts displayed FAME yields of over 80% even after 5 reactions/activation cycles. Additionally, the infuence of FFA content on the catalytic activity was investigated. As a result, in the case of Fe3O4@ SiO2‑EDG, a higher tolerance towards the FFA content can be noticed with a FAME yield of over 90% (for a 5% (weight) vs oil catalyst content) and 5% weight FFA content. Biodiesel can represent a suitable renewable alternative for the direct replacement of standard diesel fuels derived from petroleum sources1,2. -

The Dzone Guide to Volume Ii
THE D ZONE GUIDE TO MODERN JAVA VOLUME II BROUGHT TO YOU IN PARTNERSHIP WITH DZONE.COM/GUIDES DZONE’S 2016 GUIDE TO MODERN JAVA Dear Reader, TABLE OF CONTENTS 3 EXECUTIVE SUMMARY Why isn’t Java dead after more than two decades? A few guesses: Java is (still) uniquely portable, readable to 4 KEY RESEARCH FINDINGS fresh eyes, constantly improving its automatic memory management, provides good full-stack support for high- 10 THE JAVA 8 API DESIGN PRINCIPLES load web services, and enjoys a diverse and enthusiastic BY PER MINBORG community, mature toolchain, and vigorous dependency 13 PROJECT JIGSAW IS COMING ecosystem. BY NICOLAI PARLOG Java is growing with us, and we’re growing with Java. Java 18 REACTIVE MICROSERVICES: DRIVING APPLICATION 8 just expanded our programming paradigm horizons (add MODERNIZATION EFFORTS Church and Curry to Kay and Gosling) and we’re still learning BY MARKUS EISELE how to mix functional and object-oriented code. Early next 21 CHECKLIST: 7 HABITS OF SUPER PRODUCTIVE JAVA DEVELOPERS year Java 9 will add a wealth of bigger-picture upgrades. 22 THE ELEMENTS OF MODERN JAVA STYLE But Java remains vibrant for many more reasons than the BY MICHAEL TOFINETTI robustness of the language and the comprehensiveness of the platform. JVM languages keep multiplying (Kotlin went 28 12 FACTORS AND BEYOND IN JAVA GA this year!), Android keeps increasing market share, and BY PIETER HUMPHREY AND MARK HECKLER demand for Java developers (measuring by both new job 31 DIVING DEEPER INTO JAVA DEVELOPMENT posting frequency and average salary) remains high. The key to the modernization of Java is not a laundry-list of JSRs, but 34 INFOGRAPHIC: JAVA'S IMPACT ON THE MODERN WORLD rather the energy of the Java developer community at large. -

Flask Documentation Release 0.7Dev July 14, 2014
Flask Documentation Release 0.7dev July 14, 2014 Contents I User’s Guide1 1 Foreword3 1.1 What does “micro” mean?...........................3 1.2 A Framework and an Example........................4 1.3 Web Development is Dangerous.......................4 1.4 The Status of Python 3.............................4 2 Installation7 2.1 virtualenv....................................7 2.2 System Wide Installation...........................8 2.3 Living on the Edge...............................9 2.4 easy_install on Windows............................9 3 Quickstart 11 3.1 A Minimal Application............................ 11 3.2 Debug Mode.................................. 12 3.3 Routing..................................... 13 3.4 Static Files.................................... 17 3.5 Rendering Templates.............................. 17 3.6 Accessing Request Data............................ 19 3.7 Redirects and Errors.............................. 22 3.8 Sessions..................................... 22 3.9 Message Flashing................................ 23 3.10 Logging..................................... 24 3.11 Hooking in WSGI Middlewares....................... 24 4 Tutorial 25 4.1 Introducing Flaskr............................... 25 4.2 Step 0: Creating The Folders......................... 26 4.3 Step 1: Database Schema........................... 27 4.4 Step 2: Application Setup Code........................ 27 i 4.5 Step 3: Creating The Database........................ 29 4.6 Step 4: Request Database Connections.................... 30 4.7 Step -

Mastering Ajax, Part 4: Exploiting DOM for Web Response Convert HTML Into an Object Model to Make Web Pages Responsive and Interactive
Mastering Ajax, Part 4: Exploiting DOM for Web response Convert HTML into an object model to make Web pages responsive and interactive Skill Level: Introductory Brett McLaughlin Author and Editor O'Reilly Media Inc. 14 Mar 2006 The great divide between programmers (who work with back-end applications) and Web programmers (who spend their time writing HTML, CSS, and JavaScript) is long standing. However, the Document Object Model (DOM) bridges the chasm and makes working with both XML on the back end and HTML on the front end possible and an effective tool. In this article, Brett McLaughlin introduces the Document Object Model, explains its use in Web pages, and starts to explore its usage from JavaScript. Like many Web programmers, you have probably worked with HTML. HTML is how programmers start to work on a Web page; HTML is often the last thing they do as they finish up an application or site, and tweak that last bit of placement, color, or style. And, just as common as using HTML is the misconception about what exactly happens to that HTML once it goes to a browser to render to the screen. Before I dive into what you might think happens -- and why it is probably wrong -- I want you need to be clear on the process involved in designing and serving Web pages: 1. Someone (usually you!) creates HTML in a text editor or IDE. 2. You then upload the HTML to a Web server, like Apache HTTPD, and make it public on the Internet or an intranet. Exploiting DOM for Web response Trademarks © Copyright IBM Corporation 2006 Page 1 of 19 developerWorks® ibm.com/developerWorks 3. -

Wepgw003 High-Level Applications for the Sirius Accelerator Control System
10th Int. Particle Accelerator Conf. IPAC2019, Melbourne, Australia JACoW Publishing ISBN: 978-3-95450-208-0 doi:10.18429/JACoW-IPAC2019-WEPGW003 HIGH-LEVEL APPLICATIONS FOR THE SIRIUS ACCELERATOR CONTROL SYSTEM X. R. Resende ∗, F. H. de Sá, G. do Prado, L. Liu, A. C. Oliveira, Brazilian Synchrotron Light Laboratory (LNLS), Campinas, Brazil Abstract the sequence we detail the architecture of the HLA and its Sirius is the new 3 GeV low-emittance Brazilian Syn- current development status. Finally we describe how the chrotron Light source under installation and commissioning integration of the CS has been evolving during machine at LNLS. The machine control system is based on EPICS commissioning and end the paper with conclusion remarks and when the installation is complete it should have a few on what the next steps are in HLA development and testing. hundred thousand process variables in use. For flexible inte- gration and intuitive control of such sizable system a con- CONTROL SYSTEM OVERVIEW siderable number of high-level applications, input/output The Sirius accelerator control system (SCS) is based on controllers and graphical user interfaces have been devel- EPICS [3], version R3.15. All SCS software components oped, mostly in Python, using a variety of libraries, such are open-source solutions developed collaboratively using as PyEpics, PCASPy and PyDM. Common support service git version control and are publicly available in the Sirius applications (Archiver Appliance, Olog, Apache server, a organization page [4] at Github. mongoDB-based configuration server, etc) are used. Matlab The naming system used in Sirius for devices and CS prop- Middle Layer is also an available option to control EPICS erties is based on ESS naming system [5].