E2E Verifiable Borda Count Voting System Without Tallying Authorities
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
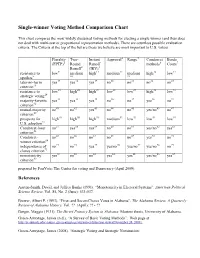
Single-Winner Voting Method Comparison Chart
Single-winner Voting Method Comparison Chart This chart compares the most widely discussed voting methods for electing a single winner (and thus does not deal with multi-seat or proportional representation methods). There are countless possible evaluation criteria. The Criteria at the top of the list are those we believe are most important to U.S. voters. Plurality Two- Instant Approval4 Range5 Condorcet Borda (FPTP)1 Round Runoff methods6 Count7 Runoff2 (IRV)3 resistance to low9 medium high11 medium12 medium high14 low15 spoilers8 10 13 later-no-harm yes17 yes18 yes19 no20 no21 no22 no23 criterion16 resistance to low25 high26 high27 low28 low29 high30 low31 strategic voting24 majority-favorite yes33 yes34 yes35 no36 no37 yes38 no39 criterion32 mutual-majority no41 no42 yes43 no44 no45 yes/no 46 no47 criterion40 prospects for high49 high50 high51 medium52 low53 low54 low55 U.S. adoption48 Condorcet-loser no57 yes58 yes59 no60 no61 yes/no 62 yes63 criterion56 Condorcet- no65 no66 no67 no68 no69 yes70 no71 winner criterion64 independence of no73 no74 yes75 yes/no 76 yes/no 77 yes/no 78 no79 clones criterion72 81 82 83 84 85 86 87 monotonicity yes no no yes yes yes/no yes criterion80 prepared by FairVote: The Center for voting and Democracy (April 2009). References Austen-Smith, David, and Jeffrey Banks (1991). “Monotonicity in Electoral Systems”. American Political Science Review, Vol. 85, No. 2 (June): 531-537. Brewer, Albert P. (1993). “First- and Secon-Choice Votes in Alabama”. The Alabama Review, A Quarterly Review of Alabama History, Vol. ?? (April): ?? - ?? Burgin, Maggie (1931). The Direct Primary System in Alabama. -

Ranked-Choice Voting from a Partisan Perspective
Ranked-Choice Voting From a Partisan Perspective Jack Santucci December 21, 2020 Revised December 22, 2020 Abstract Ranked-choice voting (RCV) has come to mean a range of electoral systems. Broadly, they can facilitate (a) majority winners in single-seat districts, (b) majority rule with minority representation in multi-seat districts, or (c) majority sweeps in multi-seat districts. Such systems can be combined with other rules that encourage/discourage slate voting. This paper describes five major versions used in U.S. public elections: Al- ternative Vote (AV), single transferable vote (STV), block-preferential voting (BPV), the bottoms-up system, and AV with numbered posts. It then considers each from the perspective of a `political operative.' Simple models of voting (one with two parties, another with three) draw attention to real-world strategic issues: effects on minority representation, importance of party cues, and reasons for the political operative to care about how voters rank choices. Unsurprisingly, different rules produce different outcomes with the same votes. Specific problems from the operative's perspective are: majority reversal, serving two masters, and undisciplined third-party voters (e.g., `pure' independents). Some of these stem from well-known phenomena, e.g., ballot exhaus- tion/ranking truncation and inter-coalition \vote leakage." The paper also alludes to vote-management tactics, i.e., rationing nominations and ensuring even distributions of first-choice votes. Illustrative examples come from American history and comparative politics. (209 words.) Keywords: Alternative Vote, ballot exhaustion, block-preferential voting, bottoms- up system, exhaustive-preferential system, instant runoff voting, ranked-choice voting, sequential ranked-choice voting, single transferable vote, strategic coordination (10 keywords). -

Office of the City Clerk: Elections and Voter Services Division Table of Contents
Office of the City Clerk: Elections and Voter Services Division Table of Contents EXECUTIVE SUMMARY ............................................................................................................................ 2 I. IMPACT OF THE 2012 PRESIDENTIAL GENERAL ELECTION ......................................................... 3 II. STATE LEGISLATIVE PLATFORM ISSUES (EARLY VOTING) ........................................................... 3 III. RECOMMENDED LOCAL IMPROVEMENTS .................................................................................. 4 IV. FINANCING ELECTIONS: MULTI-YEAR PERSPECTIVE .................................................................... 5 V. FINANCING THE 2013 MUNICIPAL ELECTION – SUPPLEMENTAL FUNDING REQUEST ........... 7 VI. PROCUREMENT OF NEW VOTING SYSTEMS & EQUIPMENT .......................................................... 8 VII. PRECINCTS & POLLING PLACES ......................................................................................................... 9 VIII. VOTER OUTREACH & EDUCATION ...................................................................................................11 IX. RANKED CHOICE VOTING – THE MINNEAPOLIS METHOD: RECOMMENDATIONS FOR PROCESS IMPROVEMENTS ...................................................................14 CONCLUSION: RECOMMENDATIONS & NEXT STEPS ...................................................................................18 EXECUTIVE SUMMARY This report provides an update on several initiatives aimed at improving administrative -

League of Women Voters Positions on Ranked Voting Methods (IRV and Choice Voting)
League of Women Voters positions on Ranked Voting Methods (IRV and Choice Voting) ARIZOA The League of Women Voters of Arizona believes in the election system principle of greater vote representation. The LWVAZ maintains the hope that election system reform that provides a stronger voice for the greatest number of voters should have a positive effect on voter participation. Therefore, the LWVAZ: • Supports changing the present election systems so that they more accurately represent the wishes of voters: • Adopting the Instant Runoff Voting (IRV)system for single seat races; • Adopting proportional representation for multi-seat races, specifically Ranked Choice Voting. • Believes that education of the voting public is important to election systems. • Supports giving Arizona voters the option of more choice among election systems. Consensus 2005, Amended 2008 CALIFORIA Election Systems Position Support election systems for executive offices, both at the state and local levels, that require the winner to receive a majority of the votes, as long as the majority is achieved using a voting method such as Instant Runoff Voting, rather than a second, separate runoff election. Adopted 2001; Modified 2003; Readopted at last convention. FLORIDA Following statewide local League consensus meetings, the League of Women Voters of Florida announced a new Election Law, Voting Process position making the method of instant runoff voting a recommended alternative to plurality voting. MASSACHUSETTS VOTING SYSTEMS GOAL: Voting systems should be easy to use, administer and understand, encourage high voter turnout, encourage real discussion on issues, promote minority representation, and encourage candidates to run. When electing someone to a single executive office at the state level, such as governor or attorney general, including primary and general elections, the voting system should require the winner to obtain a majority of the votes. -

Ranked Choice Voting: a Different Way of Casting and Counting Votes David C. Kimball and Joseph Anthony
Ranked Choice Voting: A Different Way of Casting and Counting Votes David C. Kimball and Joseph Anthony 1 Can changing the way votes are cast and counted change how campaigns are conducted and who is elected? This chapter examines ranked choice voting, a different set of voting rules than the plurality system we are accustomed to in the United States. Ranked choice voting asks voters to rank candidates by order of preference, allowing for a more complete expression of a voter’s candidate preferences. Several American cities have recently adopted ranked choice voting for local elections. Based on our limited experience with these new voting rules, ranked choice voting appears to improve on plurality voting rules in several ways: (1) attracting more candidates for local office, particularly women and people of color; (2) reducing incentives for negative campaigns; (3) and lessening the burden on voters and local governments by consolidating two elections into one. However, there are concerns that ranked choice voting rules are more complicated for voters and some voters may not take full advantage of these rules. Issues with Plurality, Winner-Take-All Voting Casual observers of American politics may not appreciate how crucial the voting rules are in shaping political competition and determining whose interests are represented in government. Since the nation’s founding, the United States has relied almost exclusively on plurality, or “winner-take-all,” rules for electing government officials. Plurality voting rules are very simple. Candidates compete for an office and voters mark their ballots to indicate the single candidate they prefer the most. -

Improving Elections with Instant Runoff Voting
FAIRVOTE: THE CENTER FOR VOTING & DEMOCRACY | WWW.FAIRVOTE.ORG | (301) 270-4616 Improving Elections with Instant Runoff Voting Instant Runoff Voting (IRV) - Used for both government and private elections around the United States and the world, instant runoff voting is a simple election process used to avoid the expense, difficulties and shortcomings of runoff elections. Compared to the traditional “delayed” runoff, IRV saves taxpayers money, cuts the costs of running campaigns, elects public officials with higher voter turnout and encourages candidates to run less negative campaigns. How instant runoff voting works: • First round of counting: The voters rank their preferred candidate first and may also rank additional choices (second, third, etc.). In the first round of counting, the voters’ #1 choices are tallied. A candidate who receives enough first choices to win outright (typically a majority) is declared the winner. However, other candidates may have enough support to require a runoff – just as in traditional runoff systems. • Second round: If no one achieves a clear victory, the runoff occurs instantly. The candidate with the fewest votes is removed and the votes made for that candidate are redistributed using voters’ second choices. Other voters’ top choices remain the same. The redistributed votes are added to the counts of the candidates still in competition. The process is repeated until one candidate has majority support. The benefits: Instant runoff voting (IRV) would do everything the current runoff system does to ensure that the winner has popular support – but it does it in one election rather than two. • Saves localities, taxpayers and candidates money by holding only one election. -

Instant Runoff Voting in Charter Counties and Charter Cities
Instant Runoff Voting in Charter Counties and Charter Cities “Instant Runoff Voting,” also known as “Ranked Voting,” is an election method in which a single election determines the candidate supported by the voters, eliminating the need for separate run-off elections. As defined in these guidelines, it is a method in which voters rank candidates for office in order of preference and ballots are counted in rounds that simulate a series of runoffs until either a single candidate among several attains a majority of votes or only two candidates remain and the one with the greatest number of votes is declared winner. These guidelines are offered as a model that local jurisdictions may adopt, in whole or in part. They are not regulations and do not have the force of law. At present only charter cites and counties, by virtue of a charter provision approved by the voters, may adopt this method of voting. These guidelines address only single-seat or single-winner contests. Ranked Voting may also be employed in elections to fill multiple positions. However, these guidelines are not intended to address multiple-seat elections. Article 1. General Provisions 1. Definitions. For purposes of these guidelines, the following terms have the following meanings: (a) “Choice” means an indication on a ballot of a voter’s ranking of candidates for any single office. (b) “Continuing ballot” means a ballot that counts towards a continuing candidate. (c) “Continuing candidate” means a qualified candidate that has not been eliminated. (d) “Exhausted ballot” means a ballot on which all of a particular voter’s choices for an office have been eliminated or there are no more valid choices for that office indicated on that voter’s ballot. -

Instant-Runoff Voting
INFORMATION BRIEF Minnesota House of Representatives Research Department 600 State Office Building St. Paul, MN 55155 Matt Gehring, Legislative Analyst 651-296-5052 February 2007 Instant-Runoff Voting Instant-runoff voting is a system of voting that allows voters to rank their preference for an office among multiple candidates. In November 2006, Minneapolis voters approved this method of voting for candidates for city offices beginning in 2009. This information brief answers basic questions about how instant-runoff voting works. Contents What is Instant-Runoff Voting?....................................................................... 2 What does an IRV ballot look like?................................................................. 2 How are IRV votes counted? ........................................................................... 3 Contingencies: What if...?................................................................................ 4 Effects: How does IRV affect...? ..................................................................... 5 Who uses IRV? ................................................................................................ 6 Do local governments need authorization to use IRV? ................................... 6 Is IRV vulnerable to legal challenges? ............................................................ 7 Copies of this publication may be obtained by calling 651-296-6753. This document can be made available in alternative formats for people with disabilities by calling 651-296-6753 or the -

Review of Paradoxes Afflicting Various Voting Procedures Where One out of M Candidates (M ≥ 2) Must Be Elected*
Review of Paradoxes Afflicting Various Voting Procedures Where One Out of m Candidates (m ≥ 2) Must Be Elected* Dan S. Felsenthal University of Haifa and Centre for Philosophy of Natural and Social Science London School of Economics and Political Science Revised 26 May 2010 This paper will be presented at the Leverhulme Trust sponsored 2010 Voting Power in Practice workshop held at Chateau du Baffy, Normandy, France, 30 July – 2 August, 2010 Please send by email all communications regarding this paper to the author at: [email protected] or at [email protected] * I wish to thank Vincent Chua, Rudolf Fara, and Moshé Machover for helpful comments, as well as Hannu Nurmi for sending me several examples contained in this paper. No member of the Voting Power & Procedures (VPP) project at LSE, except myself, bears any responsibility whatsoever for the opinions and recommendations expressed here. Abstract The paper surveys 17 deterministic electoral procedures for selecting one out of two or more candidates, as well as the susceptibility of each of these procedures to various paradoxes. A detailed appendix exemplifies the paradoxes to which each electoral procedure is susceptible. It is concluded that from the perspective of vulnerability to serious paradoxes, as well as in light of additional technical-administrative criteria, Copeland’s or Kemeny’s proposed procedures are the most desirable. 1. Introduction Three factors motivated me to write this paper: • The recent passage (25 February 2010) by the British House of Commons of the Constitutional Reform and Governance Bill, clause #29 of which states that a referendum will be held by 31 October 2011 on changing the current single member plurality (aka first-past- the-post, briefly FPTP) electoral procedure for electing the British House of Commons to the (highly paradoxical) alternative vote (AV) procedure (aka Instant Runoff). -

Multi-Winner Elections: Working Toward Proportional Representation
Multi-Winner Elections: Working Toward Proportional Representation Celeste Landry Electoral Reform Symposium 1 Denver, Dec 7, 2019 Multi-Winner Elections Deserve More Attention Look for opportunities to hold multi-winner elections • Eliminate gerrymandering • Increase competitiveness I Voted • Use a voting method that promotes proportional representationElectoral Reform Symposium 2 Denver, Dec 7, 2019 Definitions Single-Winner Election: governor, ward member, member of Congress Versus Multi-Winner Election: 2 or more seats filled in one contest Electoral Reform Symposium 3 Denver, Dec 7, 2019 Example: 2019 Denver Single Winner Two Winners Clerk and Recorder Councilmembers At-Large Vote for one (1) Vote for not more than two (2) • Peg Perl • Jesse Lashawn Parris • Paul D. Lopez • Johnny Hayes • Deborah "Debbie" Ortega • Sarah O. McCarthy • Tony Pigford • Lynne Langdon • Robin Kniech Electoral Reform Symposium 4 Denver, Dec 7, 2019 Appropriate Use Single-Winner Contests Appropriate for unitary executive offices, such as governor, treasurer, and mayor Multi-Winner Contests Appropriate for multi-member legislative or executive bodies, such as the US House of Representatives, city council, and school boards Electoral Reform Symposium 5 Denver, Dec 7, 2019 Multi-Winner Elections Deserve More Attention Look for opportunities to hold multi-winner elections • Eliminate gerrymandering • Increase competitiveness • Use a voting method that promotes PR Electoral Reform Symposium 6 Denver, Dec 7, 2019 Conditions for Gerrymandering •Elected multi-member body •Elections by geographic district where different district boundaries are possible. Electoral Reform Symposium 7 Denver, Dec 7, 2019 Solve Gerrymandering! Gerrymandering is manipulating the boundaries of an electoral district. To eliminate gerrymandering, get rid of districts! Electoral Reform Symposium 8 Denver, Dec 7, 2019 Solve Gerrymandering! Gerrymandering is manipulating the boundaries of an electoral district. -

Submission to ERRE Martin Laplante, Phd, for 123 Canada
Submission to ERRE Martin Laplante, PhD, for 123 Canada Summary 123 Canada is the national organization that promotes Preferential systems. We are proposing 3 alternatives: A) Optional Preferential Voting, B) Two-Round System, or C) Reforms in case the electoral system is unchanged. A) and B) are types of Preferential systems. The problem to be solved is vote splitting. We show that voters believe this is the most significant distortion in the current system. Preferential Voting is the second most used system in Canada, the only other one with official status. It is common in the French speaking world and growing rapidly in the US and Canada. Preferential systems are the ones that best fit the committee's 5 principles. The major distortion in the current system, as shown by voter behaviour, is vote splitting. There is a diversity of intentions that voters may have, for a person or party or against, and our proposals best support the full range of different intentions. We discuss the two alternative models of democratic consensus: the one underlying proportional systems where parties, each representing a relatively narrow range of opinions, mediate the relationship between voters and their government through negotiations between politicians, versus what we propose, where each candidate must address the diversity within their community, and the proposed consensus gets a direct democratic mandate from voters. While claims that electoral systems change the engagement of individuals and groups are known to be incorrect, we show how preferential voting directly empowers the voters who have minority views, not the party of their first choice candidate, and ensures they cannot be ignored no matter who wins. -
![Colorado Secretary of State Election Rules [8 CCR 1505-1] Rule 26 – As](https://docslib.b-cdn.net/cover/4551/colorado-secretary-of-state-election-rules-8-ccr-1505-1-rule-26-as-3584551.webp)
Colorado Secretary of State Election Rules [8 CCR 1505-1] Rule 26 – As
Colorado Secretary of State Election Rules [8 CCR 1505-1] Rule 26. Ranked Voting Method 26.1 Definitions. As used in this Rule, unless stated otherwise: 26.1.1 “Active Ballot” means a ballot properly marked and counted for either a winning candidate or a continuing candidate. 26.1.2 “Continuing candidate” means a candidate who has not been eliminated but is not a winning candidate. 26.1.3 “Duplicate ranking” means a voter marked more than one ranking for a candidate. 26.1.4 “Instant Run-off Election” means a type of ranked voting election where only one candidate will be elected to office. 26.1.5 “Overvote” means a voter marked more than one candidate with the same ranking. 26.1.6 “Ranking” means the voter’s assigned number or the numeric position for a candidate to express the voter’s preference for that candidate. Ranking number one is the highest rank, ranking number two is the next-highest rank, and so on. 26.1.7 “Single Transferable Vote Election” means a type of ranked voting election where more than one candidate will be elected to the same office. 26.1.8 “Skipped ranking” means a voter did not rank candidates in numerical order (e.g., voter ranks top candidate with a “1” and second candidate with a “3”, or leaves a ranking blank). 26.1.9 “Surplus votes” means the votes cast for a winning candidate in excess of the winning threshold that may be transferred to a continuing candidate. 26.1.10 “Surplus fraction” means a fraction calculated by dividing the surplus votes by the total votes cast for the winning candidate, calculated to four decimal places, ignoring any remainder.