Self-Exfiltration
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Browser Security Information
Browser Security Information Customer security is important to us. Our top priority is to protect the privacy of your personal account information and your financial transactions FirstLine Mortgages is leading the way in Internet banking services and uses several layers of robust security technology to help ensure the confidentiality of transactions across the Internet. The first security level begins with your Web browser. When you access FirstLine Mortgages Internet Site , your browser is checked to ensure that it meets our minimum requirements. Additionally, we only allow customers with browsers that use 128-bit encryption (one of the highest levels of browser security available today) to bank on our web site. But, even with this validation, there are other precautions you should follow to maximize your protection. You have a responsibility to ensure your own security. The browser validation will verify the browser type you are using, your browser encryption level, the version of Netscape or Microsoft browser, as well as Javascript and cookies being enabled. To access -FirstLine Mortgages Internet site , you need to use: • a Netscape browser version 4.06 or better with a minimum 128-bit encryption technology • a Microsoft browser version 4.01 SP2 or better with a minimum 128-bit encryption technology • Javascript (please see below for more information about how to check and enable Javascript support) • Cookies (see below) If your browser does not meet all of these requirements, you will need to upgrade your browser to access the FirstLine Internet Site . To upgrade your browser, select the Netscape or Microsoft button below and download the latest browser version. -

But Were Afraid to Ask!)
05_576593 ch01.qxd 10/12/04 9:55 PM Page 9 Chapter 1 All You Ever Wanted to Know about JavaScript (But Were Afraid to Ask!) In This Chapter ᮣ Understanding a working definition of JavaScript ᮣ Dispelling common JavaScript misconceptions ᮣ Getting started with JavaScript tools ᮣ Finding information online aybe you’ve surfed to a Web site that incorporates really cool features, Msuch as ߜ Images that change when you move your mouse over them ߜ Slideshow animations ߜ Input forms with pop-up messages that help you fill in fields correctly ߜ Customized messages that welcome repeat visitors By using JavaScript and the book you’re reading right now you can create all these effects and many more! The Web page in Figure 1-1 shows you an example COPYRIGHTEDof the kinds of things that you canMATERIAL look forward to creating for your own site. A lot has changed since the previous edition of JavaScript For Dummies came out. Perhaps the biggest change is the evolution of DHTML, or dynamic HTML. DHTML refers to JavaScript combined with HTML and cascading style sheets, and it’s a powerful combination you can use to create even more breathtak- ingly cool Web sites than ever before. 05_576593 ch01.qxd 10/12/04 9:55 PM Page 10 10 Part I: Building Killer Web Pages for Fun and Profit Figure 1-1: JavaScript lets you add interactive features to your Web site quickly and easily. Along with this increased power comes increased complexity, unfortunately — but that’s where this new, improved, better-tasting edition of JavaScript For Dummies comes in! Even if you’re not a crackerjack programmer, you can use the techniques and sample scripts in this book to create interactive Web pages bursting with animated effects. -

CA Network Flow Analysis Release Notes
CA Network Flow Analysis Release Notes Release 9.1.3 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the “Documentation”) is for your informational purposes only and is subject to change or withdrawal by CA at any time. This Documentation may not be copied, transferred, reproduced, disclosed, modified or duplicated, in whole or in part, without the prior written consent of CA. This Documentation is confidential and proprietary information of CA and may not be disclosed by you or used for any purpose other than as may be permitted in (i) a separate agreement between you and CA governing your use of the CA software to which the Documentation relates; or (ii) a separate confidentiality agreement between you and CA. Notwithstanding the foregoing, if you are a licensed user of the software product(s) addressed in the Documentation, you may print or otherwise make available a reasonable number of copies of the Documentation for internal use by you and your employees in connection with that software, provided that all CA copyright notices and legends are affixed to each reproduced copy. The right to print or otherwise make available copies of the Documentation is limited to the period during which the applicable license for such software remains in full force and effect. Should the license terminate for any reason, it is your responsibility to certify in writing to CA that all copies and partial copies of the Documentation have been returned to CA or destroyed. TO THE EXTENT PERMITTED BY APPLICABLE LAW, CA PROVIDES THIS DOCUMENTATION “AS IS” WITHOUT WARRANTY OF ANY KIND, INCLUDING WITHOUT LIMITATION, ANY IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, OR NONINFRINGEMENT. -

Security Analysis of Firefox Webextensions
6.857: Computer and Network Security Due: May 16, 2018 Security Analysis of Firefox WebExtensions Srilaya Bhavaraju, Tara Smith, Benny Zhang srilayab, tsmith12, felicity Abstract With the deprecation of Legacy addons, Mozilla recently introduced the WebExtensions API for the development of Firefox browser extensions. WebExtensions was designed for cross-browser compatibility and in response to several issues in the legacy addon model. We performed a security analysis of the new WebExtensions model. The goal of this paper is to analyze how well WebExtensions responds to threats in the previous legacy model as well as identify any potential vulnerabilities in the new model. 1 Introduction Firefox release 57, otherwise known as Firefox Quantum, brings a large overhaul to the open-source web browser. Major changes with this release include the deprecation of its initial XUL/XPCOM/XBL extensions API to shift to its own WebExtensions API. This WebExtensions API is currently in use by both Google Chrome and Opera, but Firefox distinguishes itself with further restrictions and additional functionalities. Mozilla’s goals with the new extension API is to support cross-browser extension development, as well as offer greater security than the XPCOM API. Our goal in this paper is to analyze how well the WebExtensions model responds to the vulnerabilities present in legacy addons and discuss any potential vulnerabilities in the new model. We present the old security model of Firefox extensions and examine the new model by looking at the structure, permissions model, and extension review process. We then identify various threats and attacks that may occur or have occurred before moving onto recommendations. -

Javascript Security
Color profile: Generic CMYK printer profile Composite Default screen Complete Reference / JavaScript: TCR / Powell & Schneider / 225357-6 / Chapter 22 Blind Folio 679 22 JavaScript Security ownloading and running programs written by unknown parties is a dangerous proposition. A program available on the Web could work as advertised, but then Dagain it could also install spyware, a backdoor into your system, or a virus, or exhibit even worse behavior such as stealing or deleting your data. The decision to take the risk of running executable programs is typically explicit; you have to download the program and assert your desire to run it by confirming a dialog box or double-clicking the program’s icon. But most people don’t think about the fact that nearly every time they load a Web page, they’re doing something very similar: inviting code—in this case, JavaScript—written by an unknown party to execute on their computer. Since it would be phenomenally annoying to have to confirm your wish to run JavaScript each time you loaded a new Web page, the browser implements a security policy designed to reduce the risk such code poses to you. A security policy is simply a set of rules governing what scripts can do, and under what circumstances. For example, it seems reasonable to expect browsers’ security policies to prohibit JavaScript included on Web pages downloaded from the Internet from having access to the files on your computer. If they didn’t, any Web page you visited could steal or destroy all of your files! In this chapter we examine the security policies browsers enforce on JavaScript embedded in Web pages. -

Inlined Information Flow Monitoring for Javascript
Inlined Information Flow Monitoring for JavaScript Andrey Chudnov David A. Naumann Stevens Institute of Technology Stevens Institute of Technology Hoboken, NJ 07030 USA Hoboken, NJ 07030 USA [email protected] [email protected] ABSTRACT JS engines are highly engineered for performance, which has Extant security mechanisms for web apps, notably the\same- led some researchers to argue for inlined monitoring for IFC. origin policy", are not sufficient to achieve confidentiality The main contribution of this paper is an inlined IFC mon- and integrity goals for the many apps that manipulate sen- itor that enforces non-interference for apps written in JS. sitive information. The trend in web apps is \mashups" We present the main design decisions and rationale, together which integrate JavaScript code from multiple providers in with technical highlights and a survey of state of the art al- ways that can undercut existing security mechanisms. Re- ternatives. The tool is evaluated using synthetic case studies searchers are exploring dynamic information flow controls and performance benchmarks. (IFC) for JavaScript, but there are many challenges to achiev- ing strong IFC without excessive performance cost or im- On IFC. Browsers and other platforms currently provide practical browser modifications. This paper presents an in- isolation mechanisms and access controls. Pure isolation lined IFC monitor for ECMAScript 5 with web support, goes against integration of app code from multiple providers. using the no-sensitive-upgrade (NSU) technique, together Access controls can be more nuanced, but it is well-known with experimental evaluation using synthetic mashups and that access control policies are safety properties whereas IF performance benchmarks. -
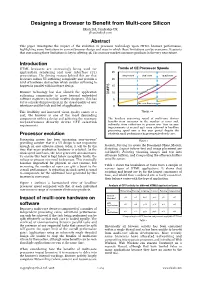
Designing a Browser to Benefit from Multi-Core Silicon
Designing a Browser to Benefit from Multi-core Silicon Ekioh Ltd, Cambridge UK. [email protected] Abstract This paper investigates the impact of the evolution in processor technology upon HTML browser performance, highlighting some limitations in current browser design and ways in which these limitations can be overcome. It asserts that overcoming these limitations is key to offering 4K UIs on mass-market consumer products in the very near future. Introduction HTML browsers are increasingly being used for Trends of CE Processor Speeds application rendering and user interface (UI) 25 presentation. The driving reasons behind this are that single core dual core quad core browsers reduce UI authoring complexity and provide a 20 level of hardware abstraction which enables authoring to happen in parallel with hardware design. 15 Browser technology has also allowed the application 10 authoring community to grow beyond embedded DMIPS Headline Performance software engineers to include creative designers. This has 5 led to a marked improvement in the visual quality of user Per core Performance interfaces and the look and feel of applications. 0 This flexibility and increased visual quality comes at a Time → cost; the browser is one of the most demanding components within a device and achieving the necessary The headline processing speed of multi-core devices responsiveness directly drives CPU selection benefits from increases in the number of cores and, requirements. indirectly, from reductions in process size. Year on year improvements of around 30% were achieved in headline processing speed over a five year period despite the Processor evolution relatively small performance improvements of each core. -

On the Disparity of Display Security in Mobile and Traditional Web Browsers
On the Disparity of Display Security in Mobile and Traditional Web Browsers Chaitrali Amrutkar, Kapil Singh, Arunabh Verma and Patrick Traynor Converging Infrastructure Security (CISEC) Laboratory Georgia Institute of Technology Abstract elements. The difficulty in efficiently accessing large pages Mobile web browsers now provide nearly equivalent fea- on mobile devices makes an adversary capable of abusing tures when compared to their desktop counterparts. How- the rendering of display elements particularly acute from a ever, smaller screen size and optimized features for con- security perspective. strained hardware make the web experience on mobile In this paper, we characterize a number of differences in browsers significantly different. In this paper, we present the ways mobile and desktop browsers render webpages that the first comprehensive study of the display-related security potentially allow an adversary to deceive mobile users into issues in mobile browsers. We identify two new classes of performing unwanted and potentially dangerous operations. display-related security problems in mobile browsers and de- Specifically, we examine the handling of user interaction vise a range of real world attacks against them. Addition- with overlapped display elements, the ability of malicious ally, we identify an existing security policy for display on cross-origin elements to affect the placement of honest el- desktop browsers that is inappropriate on mobile browsers. ements and the ability of malicious cross-origin elements Our analysis is comprised of eight mobile and five desktop to alter the navigation of honest parent and descendant el- browsers. We compare security policies for display in the ements. We then perform the same tests against a number candidate browsers to infer that desktop browsers are signif- of desktop browsers and find that the majority of desktop icantly more compliant with the policies as compared to mo- browsers are not vulnerable to the same rendering issues. -

Guideline for Securing Your Web Browser P a G E | 2
CMSGu2011-02 CERT-MU SECURITY GUIDELINE 2011 - 02 Mauritian Computer Emergency Response Team Enhancing Cyber Security in Mauritius Guideline For Securing Your Web Browser National Computer Board Mauritius JuJunene 2011 2011 Version 1.7 IssueIssue No. No. 4 2 National Computer Board © Table of Contents 1.0 Introduction .......................................................................................................................... 7 1.1 Purpose and Scope ........................................................................................................... 7 1.2 Audience........................................................................................................................... 7 1.3 Document Structure.......................................................................................................... 7 2.0 Background .......................................................................................................................... 8 3.0 Types of Web Browsers ....................................................................................................... 9 3.1 Microsoft Internet Explorer .............................................................................................. 9 3.2 Mozilla Firefox ................................................................................................................. 9 3.3 Safari ................................................................................................................................ 9 3.4 Chrome .......................................................................................................................... -

Browser Security
Transcript of Episode #38 Browser Security Description: Steve and Leo discuss the broad topic of web browser security. They examine the implications of running "client-side" code in the form of interpreted scripting languages such as Java, JavaScript, and VBScript, and also the native object code contained within browser "plug- ins" including Microsoft’s ActiveX. Steve outlines the "zone-based" security model used by IE and explains how he surfs with high security under IE, only "lowering his shields" to a website after he’s had the chance to look around and decide that the site is trustworthy. High quality (64 kbps) mp3 audio file URL: http://media.GRC.com/sn/SN-038.mp3 Quarter size (16 kbps) mp3 audio file URL: http://media.GRC.com/sn/sn-038-lq.mp3 Leo Laporte: Bandwidth for Security Now! is provided by AOL Radio at AOL.com/podcasting. This is Security Now! with Steve Gibson, Episode 38 for May 4, 2006: Browser Security. Security Now! is brought to you by Astaro, makers of the Astaro Security Gateway, on the web at www.astaro.com. So finally the sun is shining in beautiful California. We have summer, or at least spring finally arrived. And, look, Steve Gibson’s wearing a tank top and shorts. No, he’s not. Steve Gibson: Well, it’s dry in Toronto, Leo. You were all chapped; I was all, like, chapped just after one day. Leo: I am. And, you know, they complain in Toronto that it’s too humid because they have the lake effect. But I guess it gets humid some other time because I – chapped is the word, exactly. -

New Standards and Upcoming Technologies in Browser Security
OWASP The OWASP Foundation AppSec Europe 2011 http://www.owasp.org New Standards and upcoming Technologies in Browser Security Tobias Gondrom Board member of OWASP London Chair of IETF Web Security WG [email protected] Copyright © The OWASP Foundation Permission is granted to copy, distribute and/or modify this document under the terms of the OWASP License. Tobias Gondrom • 12 years information security experience • 10 years application development experience • Information Security & Risk Management, Research and Advisory, Director • Author of Standards on Digital Signatures and Secure Archiving • Chair of IETF Web Security Working Group http://datatracker.ietf.org/wg/websec/charter/ Member of the IETF Security Directorate • London OWASP chapter board member (former OWASP Germany chapter lead) www.owasp.org Browser Security • History • What’s the problem • Who & Why • What’s been done • When 3 Browser Security • History • What’s the problem • Who & Why • What’s been done • When 4 History • Internet/Arpanet Protocols were designed for robustness and exchanging information and cross reference of content… …. but not with security and active content in mind • We try to fix Application Security on the Application end ever since 5 Browser Security • History • What’s the problem • Who & Why • What’s been done • When 6 What’s the problem - OWASP Top 10 What’s the problem - OWASP Top 10 What’s the problem - No Clear separation between content and executed code - Relies on trust relationships (trust on first use / trusted source) - Weak channel protection - Authentication & leakage of credentials => Today, Web Applications try to fix this on the Application level with little support of the underlying infrastructure 9 What’s the problem Client Server Inform & Influence Security Posture 10 Think Big - What if we can…. -

Browser Security Guidance: Mozilla Firefox
GOV.UK Guidance Browser Security Guidance: Mozilla Firefox Published Contents 1. Usage scenario 2. Summary of browser security 3. How the browser can best satisfy the security recommendations 4. Network architecture 5. Deployment process 6. Recommended configuration 7. Enterprise considerations This ALPHA guidance builds on the End User Devices Platform Security Guidance and is applicable to devices running Mozilla Firefox on a supported and well configured version of Windows. This guidance was tested on 64bit Windows 8.1 Enterprise edition running Firefox 31.1.1 ESR. 1. Usage scenario Firefox will be used to access a variety of web services including: accessing intranet services hosted on an enterpriseprovided OFFICIAL network accessing enterprise cloud services sourced from the Digital Marketplace accessing other Internet services and web resources To support these scenarios, the following architectural choices are recommended: All data should be routed through a secure enterprise VPN to ensure the confidentiality and integrity of traffic intended for the enterprise intranet All Internet data should be routed through an enterprisehosted proxy to benefit from enterprise protective monitoring and logging solutions Arbitrary thirdparty extension installation by users is not permitted in the browser. A list of allowed trusted apps and extensions can be configured in Group Policy 2. Summary of browser security This browser has been assessed against each of the 12 security recommendations, and that assessment is shown in the table below. Explanatory text indicates that there is something related to that recommendation that the risk owners should be aware of. Rows marked [!] represent a more significant risk.