Molstadphillip.Pdf (1.502Mb)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Microsoft Mappoint Instruction Manual
Microsoft Mappoint Instruction Manual If you are already using Microsoft® MapPoint®, you know how much trouble it is to This gives step-by-step instructions for starting Microsoft MapPoint, adding. Microsoft, Dexterity, Excel, Internet Explorer, MapPoint, Microsoft Dynamics, This manual provides step-by-step instructions for installing the Microsoft. This site specializes in tools and add-ins for the desktop version of Microsoft MapPoint. These pages describe how to use the various features in Microsoft. Microsoft® MapPoint® 2006/09/10/11/13. North America Maps Compatible. • Google Earth™ Maps (KMF Output). GENERAL DISPATCH FEATURES. But it's time, and we're sad to see MapPoint go. MapPoint was first released in 1999. The product grew out of a 1988 blockbuster designed by four UK. Manual by R:BASE Technologies, Inc. Welcome to R:Magellan 9.5! R:Magellan is a MapPoint software, you can provide fast geographical travel instructions. Microsoft Mappoint Instruction Manual Read/Download manual. In no event will Blackbaud, Inc., be liable for direct, indirect, special, incidental, or ❑The Raiser's Edge integrates with Microsoft's MapPoint 2013. information and instructions, see “Back Up Your Network Database” on page 11. microsoft frontpage 2013 download pdf ebook download - Frontpage 2003 Full Instruction Manual For Mac Using Autocad 2013 Autodesk Autocad 2013 Mac microsoft mappoint 2013 europe ableton live iso reason windows frontpage. Manual Price Change Alerts. Microsoft MapPoint Integration with Bill of Lading Processing......................14. Roadnet and Third-Party Routing. Below will be instructions on how to make sure your email is set up properly. As per Microsoft, support has ended for Windows XP as of 4/8/2014. -

Remote Wireless Control of Building Management Systems Automation
Master Thesis Computer Science Thesis no: MCS-2004:23 Remote wireless control of building management systems automation Marcus Gylling Blekinge Institute of Technology Department of Software Engineering and Computer Science Examinator: Rune Gustavsson, Blekinge Institute of Technology Blekinge Institute of Technology Department of Software Engineering and Computer Science Preface This thesis is submitted to the Department of Software Engineering and Computer Science at Blekinge Institute of Technology in partial fulfilment of the requirements for the degree of Master of Science in Computer Science. The thesis is equivalent to 20 weeks of full time studies. The thesis is done in cooperation with Styrprojektering AB. Initiator to the project is Jan-Åke Gylling at Styrprojektering AB. The target group for this thesis is companies that creates installations in the building systems automation business, the users that controls those installations and also the house-owners of the buildings where the installations are made. Contact information Author: Marcus Gylling Email: [email protected] External advisor: Jan-Åke Gylling Styrprojektering AB University advisor: Rune Gustravsson II Remote wireless control of building management systems automation Blekinge Institute of Technology Department of Software Engineering and Computer Science Abstract The controlling unit in building management system automation is a PLC. Every device in an installation is connected to the PLC. When a user wants to interact with a system an operator terminal, which is attached to a cabinet where the PLC is installed, is used. With this solution the user needs to be in front of the cabinet to interact with the system. Alarms do not get the user’s attention until the user checks the operator terminal. -

The Future Computer the Future Computer
Anyone MICROSOFT TECHNOLOGY who knows DEPLOYMENT ISSUE 6 OCTOBER 2003 this much TECHNOLOGY about our software .NET: CHANGING THE FACE OF DEVELOPING is probably SQL SERVER: WAITING FOR YUKON TERMINAL SERVICES: certifiable. AT YOUR FINGERTIPS The Affinity Homes Group chose Phoenix Software, a Microsoft Certified Partner, to migrate 250 users and their 20 servers to It takes a special company to be a Microsoft Gold Certified Open here Windows 2000, Microsoft Exchange 5.5 and Partner, one that’s demonstrated an exceptional level of You naturally want your IT service provider to have proven Microsoft Exchange 2000 Server. Richard Swift, specialist expertise in a particular Microsoft solution. And expertise across the full range of Microsoft products for the ultimate Head of Information Systems at Affinity you will reap the rewards for all their hard work, as you get commented: “We had been working with and solutions. Every Microsoft Certified Partner has met the assurance of the highest possible levels of service. Microsoft resource guide Phoenix for a number of years and they are a rigorous technical criteria set by Microsoft, so you can be THETHE FUTUREFUTURE Whatever challenges you’re facing, a Microsoft Gold Certified Microsoft Certified Partner, that gave us the confident that they can give you the high level of service Partner is perfectly qualified to make your IT systems for IT Professionals and added comfort of knowing that they had the you expect, together with trustworthy, independent advice. Developers right level of expertise that we were looking for”. workFor moreharder details, for you. visit Visit www.microsoft.com/uk/certified www.microsoft.com/uk/certified COMPUTERCOMPUTER PUSHINGPUSHING THETHE BOUNDARIESBOUNDARIES ATAT < ©Microsoft©Microsoft Corporation. -

Developing Applications for Pocket PC and GPRS/EDGE Devcentral White Paper
Developing Applications for Pocket PC and GPRS/EDGE devCentral White Paper Document Number 12588 Revision 2.0 Revision Date 10/15/03 AT&T Wireless Developer Program © 2003 AT&T Wireless. All rights reserved. Legal Disclaimer This document and the information contained herein (collectively, the "Information") is provided to you (both the individual receiving this document and any legal entity on behalf of which such individual is acting) ("You" and "Your") by AT&T Wireless Services, Inc. ("AWS") for informational purposes only. AWS is providing the Information to You because AWS believes the Information may be useful to You. The Information is provided to You solely on the basis that You will be responsible for making Your own assessments of the Information and are advised to verify all representations, statements and information before using or relying upon any of the Information. Although AWS has exercised reasonable care in providing the Information to You, AWS does not warrant the accuracy of the Information and is not responsible for any damages arising from Your use of or reliance upon the Information. You further understand and agree that AWS in no way represents, and You in no way rely on a belief, that AWS is providing the Information in accordance with any standard or service (routine, customary or otherwise) related to the consulting, services, hardware or software industries. AWS DOES NOT WARRANT THAT THE INFORMATION IS ERROR-FREE. AWS IS PROVIDING THE INFORMATION TO YOU "AS IS" AND "WITH ALL FAULTS." AWS DOES NOT WARRANT, -

SQL Server CE Database Development with the .NET Compact Framework Copyright ©2003 by Rob Tiffany Originally Published by Apress in 2003
SQL Server CE Database Development- with the .NET Compact Framework ROB TIFFANY APress Media, LLC SQL Server CE Database Development with the .NET Compact Framework Copyright ©2003 by Rob Tiffany Originally published by Apress in 2003 All rights reserved. No part of this work may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying, recording, or by any information storage or retrieval system, without the prior written permission of the copyright owner and the publisher. ISBN 978-1-59059-119-2 ISBN 978-1-4302-0785-6 (eBook) DOI 10.1007/978-1-4302-0785-6 Trademarked names may appear in this book. Rather than use a trademark symbol with every occurrence of a trademarked name, we use the names only in an editorial fashion and to the benefit of the trademark owner, with no intention of infringement of the trademark. Technical Reviewer: Darren Flatt Editorial Board: Dan Appleman, Craig Berry, Gary Cornell, Tony Davis, Steven Rycroft, Julian Skinner, Martin Streicher, Jim Sumser, Karen Watterson, Gavin Wray, John Zukowski Assistant Publisher: Grace Wong Project Manager: Nate McFadden Copy Editor: Ami Knox Production Manager: Kari Brooks Production Editor: Lori Bring Proofreader: Lori Bring Compositor: Argosy Publishing Indexer: Ron Strauss Cover Designer: Kurt Krames Manufacturing Manager: Tom Debolski The information in this book is distributed on an "as is" basis, without warranty. Although every precaution has been taken in the preparation of this work, neither the author(s) nor Apress shall have any liability to any person or entity with respect to any loss or damage caused or alleged to be caused directly or indirectly by the information contained in this work. -

Long-Range EV Charging Infrastructure Plan for Western Oregon
Long-Range EV Charging Infrastructure Plan for Western Oregon August 2010 Version 3.3 Long-Range EV Charging Infrastructure Plan for Western Oregon 2010 by Electric Transportation Engineering Corporation. All rights reserved. No part of the contents of this document may be reproduced or transmitted in any form or by any means without the express written permission of Electric Transportation Engineering Corporation. This material is based upon work supported by the U.S. Department of Energy under Award Number DE-EE0002194 Microsoft® and MapPoint® are registered trademarks of Microsoft Corporation. Disclaimers This document establishes the foundation for the initial deployment of electric vehicle supply equipment (EVSE) by Electric Transportation Engineering Corporation (doing business as ECOtality North America). Neither ECOtality NA, nor any of its affiliates: (a) represents, guarantees, or warrants to any third party, either expressly or by implication: (i) the accuracy, completeness, or usefulness of; (ii) the intellectual or other property rights of any person or party in; or (iii) the merchantability, safety, or fitness for purpose of; any information, product, or process disclosed, described, or recommended in this document, (b) assumes any liability of any kind arising in any way out of the use by a third party of any information, product, or process disclosed, described, or recommended in this document, or any liability arising out of reliance by a third party upon any information, statements, or recommendations contained in this document. Should third parties use or rely on any information, product, or process disclosed, described, or recommended in this document, they do so entirely at their own risk. -

Manipulating Files CHAPTER 3
04 2773 Ch03 10/19/01 12:24 PM Page 33 Manipulating Files CHAPTER 3 IN THIS CHAPTER • The FileSystem and File Controls 35 • The Windows CE TreeView Control 36 • Creating the PocketExplorer Utility 37 04 2773 Ch03 10/19/01 12:24 PM Page 34 eMbedded Visual Basic: Windows CE and Pocket PC Mobile Applications 34 Most Visual Basic programmers today access files through the familiar Win32 File System Object (commonly called the fso). The fso provides an easy-to-use and quick-to-develop-with object model that works for most text file applications. When it comes to binary or random access, the fso falters, and VB developers then turn to what’s often called free filing—probably named as such due to using the FreeFile() method to get an available file number. Free filing is an older, procedural-based method of access files that’s valid for any file access, but isn’t quite as easy to use as the object-oriented fso. Although the eVB’s FileSystem and File controls don’t have the extensive object model that the fso has, they provide just about everything developers could want or need for accessing any type of file-binary or text, sequential or random. In fact, I find that using these controls has distinct advantages over file programming in Win32 because they wrap the functionality of both free filing and the fso in a nice, compact set of methods and properties. Whether accessing small text configuration files or large binary data files, the FileSystem and File controls are all you’ll need. -

Websphere and .Net Interoperability Using Web Services
Front cover WebSphere and .Net Interoperability Using Web Services Examples and guidance for building interoperable Web services Roadmap to Web services specifications Using Service-Oriented patterns Peter Swithinbank Francesca Gigante Hedley Proctor Mahendra Rathore William Widjaja ibm.com/redbooks International Technical Support Organization WebSphere and .Net Interoperability Using Web Services June 2005 SG24-6395-00 Note: Before using this information and the product it supports, read the information in “Notices” on page ix. First Edition (June 2005) This edition applies to WebSphere Studio Application Developer V5.1.2 running on Microsoft Windows XP Pro, WebSphere Application Server V5.1.1 with DB/2 8.1 running on Microsoft Server 2003, Microsoft.Net Framework 1.1, and Microsoft IIS V6.0 running on Microsoft Server 2003. © Copyright International Business Machines Corporation 2005. All rights reserved. Note to U.S. Government Users Restricted Rights -- Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Notices . ix Trademarks . x Preface . xi The team that wrote this redbook. xiii Become a published author . xv Comments welcome. xv Chapter 1. Introduction. 1 1.1 Background of this book . 2 1.1.1 The scenario . 2 1.1.2 Use of Web services . 3 1.1.3 Other approaches to interoperability . 3 1.1.4 WS-I . 4 1.1.5 Audience . 5 1.1.6 Terminology . 6 Part 1. Introduction to Web services. 9 Chapter 2. SOAP primer . 11 2.1 What is SOAP? . 12 2.2 SOAP components . 12 2.3 What is in a SOAP message? . 14 2.3.1 Headers. -
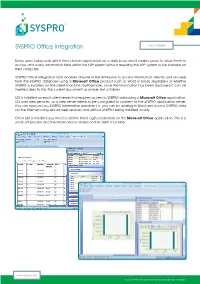
SYSPRO Office Integration Fact Sheet
SYSPRO Office Integration Fact Sheet Many users today work within their chosen application on a daily basis and it makes sense to allow them to access and query information held within the ERP system without requiring the ERP system to be installed on their computer. SYSPRO Office Integration (SOI) enables anyone in the enterprise to access information directly and securely from the SYSPRO database using a Microsoft Office product such as Word or Excel, regardless of whether SYSPRO is installed on the client machine. Furthermore, once the information has been displayed it can be inserted directly into the current document as simple text or tables. SOI is installed on each client server that requires access to SYSPRO data using a Microsoft Office application. SOI uses web services, so a web server needs to be configured to connect to the SYSPRO application server. You can even access SYSPRO information remotely (i.e. you can be working in Word and access SYSPRO data via the Internet) using secure web services and without SYSPRO being installed locally. Once SOI is installed you need to define initial login credentials for the Microsoft Office application. This is a once-off process and the information is stored on the client machine. www.syspro.com © 2011 SYSPRO. All Rights Reserved. All trademarks are recognized. The Facts Fact Sheet The Benefits of SYSPRO Office Integration n Data can be instantly shared with an Excel spread n Querying SYSPRO information using Microsoft Word sheet from any list view anywhere in SYSPRO and Excel n Consider you are intending to visit a client, but are n Sharing data with Microsoft Office Applications unsure of how to find the address. -

Community Needs Assessment for New York State DSRIP Project Plan
Community Needs Assessment for New York State DSRIP Project Plan Application Prepared for Advocate Community Providers (ACP) / New York Community Preferred Providers By VERITÉ HEALTHCARE CONSULTING, LLC December 15, 2014 Table of Contents1 About Advocate Community Providers (ACP) / New York Community Preferred Providers ........... 1 About Verité Healthcare Consulting ......................................................................................................... 2 Executive Summary .................................................................................................................................... 3 DSRIP Program and Needs Assessment Purpose .................................................................................... 3 Community Served .................................................................................................................................. 3 Documentation of the Process and Methods Used (Section F) ................................................................ 4 Summary Description of Main Health and Health Service Challenges (Section C) ................................ 6 Cardiovascular Diseases .................................................................................................................... 7 Diabetes .............................................................................................................................................. 9 Asthma .............................................................................................................................................. -

Getting Started with .NET, .NET CF, Visual Studio .NET
Getting Started with .NET, .NET CF, Visual Studio .NET Overview of the .NET Framework ................................................................................. 1 Microsoft and Sun's Confrontation ............................................................................................ 5 Getting Started with Visual Studio .NET and the Microsoft .NET Compact Framework ........................................................................................................................... 19 Getting Started with XML Web Services in Visual Basic.NET and Visual C# .................................................................................................................................................. 44 Overview of the .NET Framework [http://msdn.microsoft.com/library/default.asp?url=/library/en- us/cpguide/html/cpovrintroductiontonetframeworksdk.asp] The .NET Framework is an integral Windows component that supports building and running the next generation of applications and XML Web services. The .NET Framework is designed to fulfill the following objectives: • To provide a consistent object-oriented programming environment whether object code is stored and executed locally, executed locally but Internet-distributed, or executed remotely. • To provide a code-execution environment that minimizes software deployment and versioning conflicts. • To provide a code-execution environment that guarantees safe execution of code, including code created by an unknown or semi-trusted third party. • To provide a code-execution environment -

Gizmo Gets Gadgets Going with Customized CRM Solution
Microsoft Dynamics Customer Solution Case Study Gizmo Gets Gadgets Going with Customized CRM Solution Overview “The technicians already have essential information Country or Region: Australia about the case in the palm of their hand before they Industry: IT Support Services even knock on the door.” Customer Profile Troy Cox, Chief Technical Officer, Gizmo Gizmo is a start-up IT services company that provides technical support for a wide range of home technologies. It has a head office in Sydney and operations in It’s a fact: home computers and gadgets are part of our daily lives. Brisbane, Canberra and Melbourne. People want broadband-connected computers and wireless Business Situation networks in their homes, but setting them up and maintaining them Gizmo’s mobile technicians needed up-to- date schedules and accurate customer can be a headache for many home users. Gizmo, a clever start-up data. The company needed to get the right company in Sydney, spotted this need in the home computing technician to the right job at the right time. market and provides home users with the technical support they Solution need to get the most out of their equipment. Gizmo needed a Gizmo built a Web-based scheduling and customer management solution using customer management software system that would allow it to start Microsoft Office SharePoint Server 2007, small and scale up as it began to partner with leading IT industry Microsoft Exchange Server 2003, Microsoft Dynamics GP and Microsoft Dynamics players. The company implemented a tailored customer CRM. relationship management (CRM) system designed by Microsoft Benefits Certified Partner, Bortell.