Introduction to Modern Cryptography
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Mihir Bellare Curriculum Vitae Contents
Mihir Bellare Curriculum vitae August 2018 Department of Computer Science & Engineering, Mail Code 0404 University of California at San Diego 9500 Gilman Drive, La Jolla, CA 92093-0404, USA. Phone: (858) 534-4544 ; E-mail: [email protected] Web Page: http://cseweb.ucsd.edu/~mihir Contents 1 Research areas 2 2 Education 2 3 Distinctions and Awards 2 4 Impact 3 5 Grants 4 6 Professional Activities 5 7 Industrial relations 5 8 Work Experience 5 9 Teaching 6 10 Publications 6 11 Mentoring 19 12 Personal Information 21 2 1 Research areas ∗ Cryptography and security: Provable security; authentication; key distribution; signatures; encryp- tion; protocols. ∗ Complexity theory: Interactive and probabilistically checkable proofs; approximability ; complexity of zero-knowledge; randomness in protocols and algorithms; computational learning theory. 2 Education ∗ Massachusetts Institute of Technology. Ph.D in Computer Science, September 1991. Thesis title: Randomness in Interactive Proofs. Thesis supervisor: Prof. S. Micali. ∗ Massachusetts Institute of Technology. Masters in Computer Science, September 1988. Thesis title: A Signature Scheme Based on Trapdoor Permutations. Thesis supervisor: Prof. S. Micali. ∗ California Institute of Technology. B.S. with honors, June 1986. Subject: Mathematics. GPA 4.0. Class rank 4 out of 227. Summer Undergraduate Research Fellow 1984 and 1985. ∗ Ecole Active Bilingue, Paris, France. Baccalauréat Série C, June 1981. 3 Distinctions and Awards ∗ PET (Privacy Enhancing Technologies) Award 2015 for publication [154]. ∗ Fellow of the ACM (Association for Computing Machinery), 2014. ∗ ACM Paris Kanellakis Theory and Practice Award 2009. ∗ RSA Conference Award in Mathematics, 2003. ∗ David and Lucille Packard Foundation Fellowship in Science and Engineering, 1996. (Twenty awarded annually in all of Science and Engineering.) ∗ Test of Time Award, ACM CCS 2011, given for [81] as best paper from ten years prior. -

Design and Analysis of Secure Encryption Schemes
UNIVERSITY OF CALIFORNIA, SAN DIEGO Design and Analysis of Secure Encryption Schemes A dissertation submitted in partial satisfaction of the requirements for the degree Doctor of Philosophy in Computer Science by Michel Ferreira Abdalla Committee in charge: Professor Mihir Bellare, Chairperson Professor Yeshaiahu Fainman Professor Adriano Garsia Professor Mohan Paturi Professor Bennet Yee 2001 Copyright Michel Ferreira Abdalla, 2001 All rights reserved. The dissertation of Michel Ferreira Abdalla is approved, and it is acceptable in quality and form for publication on micro¯lm: Chair University of California, San Diego 2001 iii DEDICATION To my father (in memorian) iv TABLE OF CONTENTS Signature Page . iii Dedication . iv Table of Contents . v List of Figures . vii List of Tables . ix Acknowledgements . x Vita and Publications . xii Fields of Study . xiii Abstract . xiv I Introduction . 1 A. Encryption . 1 1. Background . 2 2. Perfect Privacy . 3 3. Modern cryptography . 4 4. Public-key Encryption . 5 5. Broadcast Encryption . 5 6. Provable Security . 6 7. Concrete Security . 7 B. Contributions . 8 II E±cient public-key encryption schemes . 11 A. Introduction . 12 B. De¯nitions . 17 1. Represented groups . 17 2. Message Authentication Codes . 17 3. Symmetric Encryption . 19 4. Asymmetric Encryption . 21 C. The Scheme DHIES . 23 D. Attributes and Advantages of DHIES . 24 1. Encrypting with Di±e-Hellman: The ElGamal Scheme . 25 2. De¯ciencies of ElGamal Encryption . 26 3. Overcoming De¯ciencies in ElGamal Encryption: DHIES . 29 E. Di±e-Hellman Assumptions . 31 F. Security against Chosen-Plaintext Attack . 38 v G. Security against Chosen-Ciphertext Attack . 41 H. ODH and SDH . -

Compact E-Cash and Simulatable Vrfs Revisited
Compact E-Cash and Simulatable VRFs Revisited Mira Belenkiy1, Melissa Chase2, Markulf Kohlweiss3, and Anna Lysyanskaya4 1 Microsoft, [email protected] 2 Microsoft Research, [email protected] 3 KU Leuven, ESAT-COSIC / IBBT, [email protected] 4 Brown University, [email protected] Abstract. Efficient non-interactive zero-knowledge proofs are a powerful tool for solving many cryptographic problems. We apply the recent Groth-Sahai (GS) proof system for pairing product equations (Eurocrypt 2008) to two related cryptographic problems: compact e-cash (Eurocrypt 2005) and simulatable verifiable random functions (CRYPTO 2007). We present the first efficient compact e-cash scheme that does not rely on a ran- dom oracle. To this end we construct efficient GS proofs for signature possession, pseudo randomness and set membership. The GS proofs for pseudorandom functions give rise to a much cleaner and substantially faster construction of simulatable verifiable random functions (sVRF) under a weaker number theoretic assumption. We obtain the first efficient fully simulatable sVRF with a polynomial sized output domain (in the security parameter). 1 Introduction Since their invention [BFM88] non-interactive zero-knowledge proofs played an important role in ob- taining feasibility results for many interesting cryptographic primitives [BG90,GO92,Sah99], such as the first chosen ciphertext secure public key encryption scheme [BFM88,RS92,DDN91]. The inefficiency of these constructions often motivated independent practical instantiations that were arguably conceptually less elegant, but much more efficient ([CS98] for chosen ciphertext security). We revisit two important cryptographic results of pairing-based cryptography, compact e-cash [CHL05] and simulatable verifiable random functions [CL07], that have very elegant constructions based on non-interactive zero-knowledge proof systems, but less elegant practical instantiations. -

Substitution-Permutation Networks, Pseudorandom Functions, and Natural Proofs∗
Substitution-permutation networks, pseudorandom functions, and natural proofs∗ Eric Miles† Emanuele Viola‡ August 20, 2015 Abstract This paper takes a new step towards closing the gap between pseudorandom func- tions (PRF) and their popular, bounded-input-length counterparts. This gap is both quantitative, because these counterparts are more efficient than PRF in various ways, and methodological, because these counterparts usually fit in the substitution-permutation network paradigm (SPN), which has not been used to construct PRF. We give several candidate PRF that are inspired by the SPN paradigm. Most Fi of our candidates are more efficient than previous ones. Our main candidates are: : 0, 1 n 0, 1 n is an SPN whose S-box is a random function on b bits given F1 { } → { } as part of the seed. We prove that resists attacks that run in time 2ǫb. F1 ≤ : 0, 1 n 0, 1 n is an SPN where the S-box is (patched) field inversion, F2 { } → { } a common choice in practical constructions. We show that is computable with F2 boolean circuits of size n logO(1) n, and that it has exponential security 2Ω(n) against · linear and differential cryptanalysis. : 0, 1 n 0, 1 is a non-standard variant on the SPN paradigm, where F3 { } → { } “states” grow in length. We show that is computable with TC0 circuits of size F3 n1+ǫ, for any ǫ> 0, and that it is almost 3-wise independent. : 0, 1 n 0, 1 uses an extreme setting of the SPN parameters (one round, F4 { } → { } one S-box, no diffusion matrix). The S-box is again (patched) field inversion. -

1 Review of Counter-Mode Encryption ¡
Comments to NIST concerning AES Modes of Operations: CTR-Mode Encryption Helger Lipmaa Phillip Rogaway Helsinki University of Technology (Finland) and University of California at Davis (USA) and University of Tartu (Estonia) Chiang Mai University (Thailand) [email protected] [email protected] http://www.tml.hut.fi/ helger http://www.cs.ucdavis.edu/ rogaway David Wagner University of California Berkeley (USA) [email protected] http://www.cs.berkeley.edu/ wagner Abstract Counter-mode encryption (“CTR mode”) was introduced by Diffie and Hellman already in 1979 [5] and is already standardized by, for example, [1, Section 6.4]. It is indeed one of the best known modes that are not standardized in [10]. We suggest that NIST, in standardizing AES modes of operation, should include CTR-mode encryption as one possibility for the next reasons. First, CTR mode has significant efficiency advantages over the standard encryption modes without weakening the security. In particular its tight security has been proven. Second, most of the perceived disadvantages of CTR mode are not valid criticisms, but rather caused by the lack of knowledge. 1 Review of Counter-Mode Encryption ¡ Notation. Let EK X ¢ denote the encipherment of an n-bit block X using key K and a block cipher E. For concreteness £ ¤ we assume that E £ AES, so n 128. If X is a nonempty string and i is a nonnegative integer, then X i denotes ¥ the ¥ X -bit string that one gets by regarding X as a nonnegative number (written in binary, most significant bit first), X ¦ ¥ ¥ adding i to this number, taking the result modulo 2 ¦ , and converting this number back into an X -bit string. -

Transferable Constant-Size Fair E-Cash
Transferable Constant-Size Fair E-Cash Georg Fuchsbauer, David Pointcheval, and Damien Vergnaud Ecole´ normale sup´erieure,LIENS - CNRS - INRIA, Paris, France http://www.di.ens.fr/f~fuchsbau,~pointche,~vergnaudg Abstract. We propose an efficient blind certification protocol with interesting properties. It falls in the Groth-Sahai framework for witness-indistinguishable proofs, thus extended to a certified signature it immediately yields non-frameable group signatures. We use blind certification to build an efficient (offline) e-cash system that guarantees user anonymity and transferability of coins without increasing their size. As required for fair e-cash, in case of fraud, anonymity can be revoked by an authority, which is also crucial to deter from double spending. 1 Introduction 1.1 Motivation The issue of anonymity in electronic transactions was introduced for e-cash and e-mail in the early 1980's by Chaum, with the famous primitive of blind signatures [Cha83,Cha84]: a signer accepts to sign a message, without knowing the message itself, and without being able to later link a message- signature pair to the transaction it originated from. In e-cash systems, the message is a serial number to make a coin unique. The main security property is resistance to \one-more forgeries" [PS00], which guarantees the signer that after t transactions a user cannot have more than t valid signatures. Blind signatures have thereafter been widely used for many variants of e-cash systems; in particular fair blind signatures [SPC95], which allow to provide revocable anonymity. They deter from abuse since in such a case the signer can ask an authority to reveal the identity of the defrauder. -

The WG Stream Cipher
The WG Stream Cipher Yassir Nawaz and Guang Gong Department of Electrical and Computer Engineering University of Waterloo Waterloo, ON, N2L 3G1, CANADA [email protected], [email protected] Abstract. In this paper we propose a new synchronous stream cipher, called WG ci- pher. The cipher is based on WG (Welch-Gong) transformations. The WG cipher has been designed to produce keystream with guaranteed randomness properties, i.e., bal- ance, long period, large and exact linear complexity, 3-level additive autocorrelation, and ideal 2-level multiplicative autocorrelation. It is resistant to Time/Memory/Data tradeoff attacks, algebraic attacks and correlation attacks. The cipher can be imple- mented with a small amount of hardware. 1 Introduction A synchronous stream cipher consists of a keystream generator which produces a sequence of binary digits. This sequence is called the running key or simply the keystream. The keystream is added (XORed) to the plaintext digits to produce the ciphertext. A secret key K is used to initialize the keystream generator and each secret key corresponds to a generator output sequence. Since the secret key is shared between the sender and the receiver, an identical keystream can be generated at the receiving end. The addition of this keystream with the ciphertext recovers the original plaintext. Stream ciphers can be divided into two major categories: bit-oriented stream ci- phers and word-oriented stream ciphers. The bit-oriented stream ciphers are usually based on binary linear feedback shift registors (LFSRs) (regularly clocked or irregu- larly clocked) together with filter or combiner functions. They can be implemented in hardware very efficiently. -

A Somewhat Historic View of Lightweight Cryptography
Intro History KATAN PRINTcipher Summary A Somewhat Historic View of Lightweight Cryptography Orr Dunkelman Department of Computer Science, University of Haifa Faculty of Mathematics and Computer Science Weizmann Institute of Science September 29th, 2011 Orr Dunkelman A Somewhat Historic View of Lightweight Cryptography 1/ 40 Intro History KATAN PRINTcipher Summary Outline 1 Introduction Lightweight Cryptography Lightweight Cryptography Primitives 2 The History of Designing Block Ciphers 3 The KATAN/KTANTAN Family The KATAN/KTANTAN Block Ciphers The Security of the KATAN/KTANTAN Family Attacks on the KTANTAN Family 4 The PRINTcipher The PRINTcipher Family Attacks on PRINTcipher 5 Future of Cryptanalysis for Lightweight Crypto Orr Dunkelman A Somewhat Historic View of Lightweight Cryptography 2/ 40 Intro History KATAN PRINTcipher Summary LWC Primitives Outline 1 Introduction Lightweight Cryptography Lightweight Cryptography Primitives 2 The History of Designing Block Ciphers 3 The KATAN/KTANTAN Family The KATAN/KTANTAN Block Ciphers The Security of the KATAN/KTANTAN Family Attacks on the KTANTAN Family 4 The PRINTcipher The PRINTcipher Family Attacks on PRINTcipher 5 Future of Cryptanalysis for Lightweight Crypto Orr Dunkelman A Somewhat Historic View of Lightweight Cryptography 3/ 40 Intro History KATAN PRINTcipher Summary LWC Primitives Lightweight Cryptography ◮ Targets constrained environments. ◮ Tries to reduce the computational efforts needed to obtain security. ◮ Optimization targets: size, power, energy, time, code size, RAM/ROM consumption, etc. Orr Dunkelman A Somewhat Historic View of Lightweight Cryptography 4/ 40 Intro History KATAN PRINTcipher Summary LWC Primitives Lightweight Cryptography ◮ Targets constrained environments. ◮ Tries to reduce the computational efforts needed to obtain security. ◮ Optimization targets: size, power, energy, time, code size, RAM/ROM consumption, etc. -
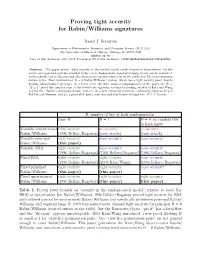
Proving Tight Security for Rabin/Williams Signatures
Proving tight security for Rabin/Williams signatures Daniel J. Bernstein Department of Mathematics, Statistics, and Computer Science (M/C 249) The University of Illinois at Chicago, Chicago, IL 60607–7045 [email protected] Date of this document: 2007.10.07. Permanent ID of this document: c30057d690a8fb42af6a5172b5da9006. Abstract. This paper proves “tight security in the random-oracle model relative to factorization” for the lowest-cost signature systems available today: every hash-generic signature-forging attack can be converted, with negligible loss of efficiency and effectiveness, into an algorithm to factor the public key. The most surprising system is the “fixed unstructured B = 0 Rabin/Williams” system, which has a tight security proof despite hashing unrandomized messages. At a lower level, the three main accomplishments of the paper are (1) a “B ≥ 1” proof that handles some of the lowest-cost signature systems by pushing an idea of Katz and Wang beyond the “claw-free permutation pair” context; (2) a new expository structure, elaborating upon an idea of Koblitz and Menezes; and (3) a proof that uses a new idea and that breaks through the “B ≥ 1” barrier. B, number of bits of hash randomization large B B = 1 B = 0: no random bits in hash input Variable unstructured tight security no security no security Rabin/Williams (1996 Bellare/Rogaway) (easy attack) (easy attack) Variable principal tight security loose security loose security∗ Rabin/Williams (this paper) Variable RSA tight security loose security loose security (1996 Bellare/Rogaway) (1993 Bellare/Rogaway) (1993 Bellare/Rogaway) Fixed RSA tight security tight security loose security (1996 Bellare/Rogaway) (2003 Katz/Wang) (1993 Bellare/Rogaway) Fixed principal tight security tight security loose security∗ Rabin/Williams (this paper) (this paper) Fixed unstructured tight security tight security tight security Rabin/Williams (1996 Bellare/Rogaway) (this paper) (this paper) Table 1. -

WAGE: an Authenticated Encryption with a Twist
WAGE: An Authenticated Encryption with a Twist Riham AlTawy1, Guang Gong2, Kalikinkar Mandal2 and Raghvendra Rohit2 1 Department of Electrical and Computer Engineering, University of Victoria, Victoria, Canada [email protected] 2 Department of Electrical and Computer Engineering, University of Waterloo, Waterloo, Canada {ggong,kmandal,rsrohit}@uwaterloo.ca Abstract. This paper presents WAGE, a new lightweight sponge-based authenticated cipher whose underlying permutation is based on a 37-stage Galois NLFSR over F27 . At its core, the round function of the permutation consists of the well-analyzed Welch- Gong permutation (WGP), primitive feedback polynomial, a newly designed 7-bit SB sbox and partial word-wise XORs. The construction of the permutation is carried out such that the design of individual components is highly coupled with cryptanalysis and hardware efficiency. As such, we analyze the security of WAGE against differential, linear, algebraic and meet/miss-in-the-middle attacks. For 128-bit authenticated encryption security, WAGE achieves a throughput of 535 Mbps with hardware area of 2540 GE in ASIC ST Micro 90 nm standard cell library. Additionally, WAGE is designed with a twist where its underlying permutation can be efficiently turned into a pseudorandom bit generator based on the WG transformation (WG-PRBG) whose output bits have theoretically proved randomness properties. Keywords: Authenticated encryption · Pseudorandom bit generators · Welch-Gong permutation · Lightweight cryptography 1 Introduction Designing a lightweight cryptographic primitive requires a comprehensive holistic ap- proach. With the promising ability of providing multiple cryptographic functionalities by the sponge-based constructions, there has been a growing interest in designing cryp- tographic permutations and sponge-variant modes. -

The Dawn of American Cryptology, 1900–1917
United States Cryptologic History The Dawn of American Cryptology, 1900–1917 Special Series | Volume 7 Center for Cryptologic History David Hatch is technical director of the Center for Cryptologic History (CCH) and is also the NSA Historian. He has worked in the CCH since 1990. From October 1988 to February 1990, he was a legislative staff officer in the NSA Legislative Affairs Office. Previously, he served as a Congressional Fellow. He earned a B.A. degree in East Asian languages and literature and an M.A. in East Asian studies, both from Indiana University at Bloomington. Dr. Hatch holds a Ph.D. in international relations from American University. This publication presents a historical perspective for informational and educational purposes, is the result of independent research, and does not necessarily reflect a position of NSA/CSS or any other US government entity. This publication is distributed free by the National Security Agency. If you would like additional copies, please email [email protected] or write to: Center for Cryptologic History National Security Agency 9800 Savage Road, Suite 6886 Fort George G. Meade, MD 20755 Cover: Before and during World War I, the United States Army maintained intercept sites along the Mexican border to monitor the Mexican Revolution. Many of the intercept sites consisted of radio-mounted trucks, known as Radio Tractor Units (RTUs). Here, the staff of RTU 33, commanded by Lieutenant Main, on left, pose for a photograph on the US-Mexican border (n.d.). United States Cryptologic History Special Series | Volume 7 The Dawn of American Cryptology, 1900–1917 David A. -

1. History of Cryptography Cryptography (From Greek , Hidden
1. History of cryptography Cryptography (from Greek , hidden, and , writing), is the practice and study of secret writing(or hidden information). Before the modern era, cryptography was concerned solely with message confidentiality (i.e., encryption) — conversion of messages from a comprehensible form into an incomprehensible one and back again at the other end, rendering it unreadable by interceptors or eavesdroppers without secret knowledge (namely the key needed for decryption of that message). History is filled with examples where people tried to keep information secret from adversaries. Kings and generals communicated with their troops using basic cryptographic methods to prevent the enemy from learning sensitive military information. In fact, Julius Caesar reportedly used a simple cipher, which has been named after him. As society has evolved, the need for more sophisticated methods of protecting data has increased. As the word becomes more connected, the demand for information and electronic services is growing, and with the increased demand comes increased dependency on electronic systems. Already the exchange of sensitive information, such as credit card numbers, over the internet is common practice. Protecting data and electronic system is crucial to our way of living. In recent decades, the field has expanded beyond confidentiality concerns to include techniques for message integrity checking, sender/receiver identity authentication, digital signatures, interactive proofs and secure computation, among others. Modern cryptography intersects the disciplines of mathematics, computer science, and engineering. It is necessary to distinct cryptography, crypto analysis and cryptology. Cryptography is a branch of cryptology dealing with the design of system for encryption and decryption intended to ensure confidentiality, integrity and authenticity of message.