Lecture 2 Overview 1 Probability Notation 2 Entropy
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Lecture 3: Entropy, Relative Entropy, and Mutual Information 1 Notation 2
EE376A/STATS376A Information Theory Lecture 3 - 01/16/2018 Lecture 3: Entropy, Relative Entropy, and Mutual Information Lecturer: Tsachy Weissman Scribe: Yicheng An, Melody Guan, Jacob Rebec, John Sholar In this lecture, we will introduce certain key measures of information, that play crucial roles in theoretical and operational characterizations throughout the course. These include the entropy, the mutual information, and the relative entropy. We will also exhibit some key properties exhibited by these information measures. 1 Notation A quick summary of the notation 1. Discrete Random Variable: U 2. Alphabet: U = fu1; u2; :::; uM g (An alphabet of size M) 3. Specific Value: u; u1; etc. For discrete random variables, we will write (interchangeably) P (U = u), PU (u) or most often just, p(u) Similarly, for a pair of random variables X; Y we write P (X = x j Y = y), PXjY (x j y) or p(x j y) 2 Entropy Definition 1. \Surprise" Function: 1 S(u) log (1) , p(u) A lower probability of u translates to a greater \surprise" that it occurs. Note here that we use log to mean log2 by default, rather than the natural log ln, as is typical in some other contexts. This is true throughout these notes: log is assumed to be log2 unless otherwise indicated. Definition 2. Entropy: Let U a discrete random variable taking values in alphabet U. The entropy of U is given by: 1 X H(U) [S(U)] = log = − log (p(U)) = − p(u) log p(u) (2) , E E p(U) E u Where U represents all u values possible to the variable. -

Package 'Infotheo'
Package ‘infotheo’ February 20, 2015 Title Information-Theoretic Measures Version 1.2.0 Date 2014-07 Publication 2009-08-14 Author Patrick E. Meyer Description This package implements various measures of information theory based on several en- tropy estimators. Maintainer Patrick E. Meyer <[email protected]> License GPL (>= 3) URL http://homepage.meyerp.com/software Repository CRAN NeedsCompilation yes Date/Publication 2014-07-26 08:08:09 R topics documented: condentropy . .2 condinformation . .3 discretize . .4 entropy . .5 infotheo . .6 interinformation . .7 multiinformation . .8 mutinformation . .9 natstobits . 10 Index 12 1 2 condentropy condentropy conditional entropy computation Description condentropy takes two random vectors, X and Y, as input and returns the conditional entropy, H(X|Y), in nats (base e), according to the entropy estimator method. If Y is not supplied the function returns the entropy of X - see entropy. Usage condentropy(X, Y=NULL, method="emp") Arguments X data.frame denoting a random variable or random vector where columns contain variables/features and rows contain outcomes/samples. Y data.frame denoting a conditioning random variable or random vector where columns contain variables/features and rows contain outcomes/samples. method The name of the entropy estimator. The package implements four estimators : "emp", "mm", "shrink", "sg" (default:"emp") - see details. These estimators require discrete data values - see discretize. Details • "emp" : This estimator computes the entropy of the empirical probability distribution. • "mm" : This is the Miller-Madow asymptotic bias corrected empirical estimator. • "shrink" : This is a shrinkage estimate of the entropy of a Dirichlet probability distribution. • "sg" : This is the Schurmann-Grassberger estimate of the entropy of a Dirichlet probability distribution. -
![Arxiv:1907.00325V5 [Cs.LG] 25 Aug 2020](https://docslib.b-cdn.net/cover/2895/arxiv-1907-00325v5-cs-lg-25-aug-2020-212895.webp)
Arxiv:1907.00325V5 [Cs.LG] 25 Aug 2020
Random Forests for Adaptive Nearest Neighbor Estimation of Information-Theoretic Quantities Ronan Perry1, Ronak Mehta1, Richard Guo1, Jesús Arroyo1, Mike Powell1, Hayden Helm1, Cencheng Shen1, and Joshua T. Vogelstein1;2∗ Abstract. Information-theoretic quantities, such as conditional entropy and mutual information, are critical data summaries for quantifying uncertainty. Current widely used approaches for computing such quantities rely on nearest neighbor methods and exhibit both strong performance and theoretical guarantees in certain simple scenarios. However, existing approaches fail in high-dimensional settings and when different features are measured on different scales. We propose decision forest-based adaptive nearest neighbor estimators and show that they are able to effectively estimate posterior probabilities, conditional entropies, and mutual information even in the aforementioned settings. We provide an extensive study of efficacy for classification and posterior probability estimation, and prove cer- tain forest-based approaches to be consistent estimators of the true posteriors and derived information-theoretic quantities under certain assumptions. In a real-world connectome application, we quantify the uncertainty about neuron type given various cellular features in the Drosophila larva mushroom body, a key challenge for modern neuroscience. 1 Introduction Uncertainty quantification is a fundamental desiderata of statistical inference and data science. In supervised learning settings it is common to quantify uncertainty with either conditional en- tropy or mutual information (MI). Suppose we are given a pair of random variables (X; Y ), where X is d-dimensional vector-valued and Y is a categorical variable of interest. Conditional entropy H(Y jX) measures the uncertainty in Y on average given X. On the other hand, mutual information quantifies the shared information between X and Y . -

GAIT: a Geometric Approach to Information Theory
GAIT: A Geometric Approach to Information Theory Jose Gallego Ankit Vani Max Schwarzer Simon Lacoste-Julieny Mila and DIRO, Université de Montréal Abstract supports. Optimal transport distances, such as Wasser- stein, have emerged as practical alternatives with theo- retical grounding. These methods have been used to We advocate the use of a notion of entropy compute barycenters (Cuturi and Doucet, 2014) and that reflects the relative abundances of the train generative models (Genevay et al., 2018). How- symbols in an alphabet, as well as the sim- ever, optimal transport is computationally expensive ilarities between them. This concept was as it generally lacks closed-form solutions and requires originally introduced in theoretical ecology to the solution of linear programs or the execution of study the diversity of ecosystems. Based on matrix scaling algorithms, even when solved only in this notion of entropy, we introduce geometry- approximate form (Cuturi, 2013). Approaches based aware counterparts for several concepts and on kernel methods (Gretton et al., 2012; Li et al., 2017; theorems in information theory. Notably, our Salimans et al., 2018), which take a functional analytic proposed divergence exhibits performance on view on the problem, have also been widely applied. par with state-of-the-art methods based on However, further exploration on the interplay between the Wasserstein distance, but enjoys a closed- kernel methods and information theory is lacking. form expression that can be computed effi- ciently. We demonstrate the versatility of our Contributions. We i) introduce to the machine learn- method via experiments on a broad range of ing community a similarity-sensitive definition of en- domains: training generative models, comput- tropy developed by Leinster and Cobbold(2012). -

On a General Definition of Conditional Rényi Entropies
proceedings Proceedings On a General Definition of Conditional Rényi Entropies † Velimir M. Ili´c 1,*, Ivan B. Djordjevi´c 2 and Miomir Stankovi´c 3 1 Mathematical Institute of the Serbian Academy of Sciences and Arts, Kneza Mihaila 36, 11000 Beograd, Serbia 2 Department of Electrical and Computer Engineering, University of Arizona, 1230 E. Speedway Blvd, Tucson, AZ 85721, USA; [email protected] 3 Faculty of Occupational Safety, University of Niš, Carnojevi´ca10a,ˇ 18000 Niš, Serbia; [email protected] * Correspondence: [email protected] † Presented at the 4th International Electronic Conference on Entropy and Its Applications, 21 November–1 December 2017; Available online: http://sciforum.net/conference/ecea-4. Published: 21 November 2017 Abstract: In recent decades, different definitions of conditional Rényi entropy (CRE) have been introduced. Thus, Arimoto proposed a definition that found an application in information theory, Jizba and Arimitsu proposed a definition that found an application in time series analysis and Renner-Wolf, Hayashi and Cachin proposed definitions that are suitable for cryptographic applications. However, there is still no a commonly accepted definition, nor a general treatment of the CRE-s, which can essentially and intuitively be represented as an average uncertainty about a random variable X if a random variable Y is given. In this paper we fill the gap and propose a three-parameter CRE, which contains all of the previous definitions as special cases that can be obtained by a proper choice of the parameters. Moreover, it satisfies all of the properties that are simultaneously satisfied by the previous definitions, so that it can successfully be used in aforementioned applications. -

Noisy Channel Coding
Noisy Channel Coding: Correlated Random Variables & Communication over a Noisy Channel Toni Hirvonen Helsinki University of Technology Laboratory of Acoustics and Audio Signal Processing [email protected] T-61.182 Special Course in Information Science II / Spring 2004 1 Contents • More entropy definitions { joint & conditional entropy { mutual information • Communication over a noisy channel { overview { information conveyed by a channel { noisy channel coding theorem 2 Joint Entropy Joint entropy of X; Y is: 1 H(X; Y ) = P (x; y) log P (x; y) xy X Y 2AXA Entropy is additive for independent random variables: H(X; Y ) = H(X) + H(Y ) iff P (x; y) = P (x)P (y) 3 Conditional Entropy Conditional entropy of X given Y is: 1 1 H(XjY ) = P (y) P (xjy) log = P (x; y) log P (xjy) P (xjy) y2A "x2A # y2A A XY XX XX Y It measures the average uncertainty (i.e. information content) that remains about x when y is known. 4 Mutual Information Mutual information between X and Y is: I(Y ; X) = I(X; Y ) = H(X) − H(XjY ) ≥ 0 It measures the average reduction in uncertainty about x that results from learning the value of y, or vice versa. Conditional mutual information between X and Y given Z is: I(Y ; XjZ) = H(XjZ) − H(XjY; Z) 5 Breakdown of Entropy Entropy relations: Chain rule of entropy: H(X; Y ) = H(X) + H(Y jX) = H(Y ) + H(XjY ) 6 Noisy Channel: Overview • Real-life communication channels are hopelessly noisy i.e. introduce transmission errors • However, a solution can be achieved { the aim of source coding is to remove redundancy from the source data -

Lecture 11: Channel Coding Theorem: Converse Part 1 Recap
EE376A/STATS376A Information Theory Lecture 11 - 02/13/2018 Lecture 11: Channel Coding Theorem: Converse Part Lecturer: Tsachy Weissman Scribe: Erdem Bıyık In this lecture1, we will continue our discussion on channel coding theory. In the previous lecture, we proved the direct part of the theorem, which suggests if R < C(I), then R is achievable. Now, we are going to prove the converse statement: If R > C(I), then R is not achievable. We will also state some important notes about the direct and converse parts. 1 Recap: Communication Problem Recall the communication problem: Memoryless Channel n n J ∼ Uniff1; 2;:::;Mg −! encoder −!X P (Y jX) −!Y decoder −! J^ log M bits • Rate = R = n channel use • Probability of error = Pe = P (J^ 6= J) (I) (I) The main result is C = C = maxPX I(X; Y ). Last week, we showed R is achievable if R < C . In this lecture, we are going to prove that if R > C(I), then R is not achievable. 2 Fano's Inequality Theorem (Fano's Inequality). Let X be a discrete random variable and X^ = X^(Y ) be a guess of X based on Y . Let Pe = P (X 6= X^). Then, H(XjY ) ≤ h2(Pe) + Pe log(jX j − 1) where h2 is the binary entropy function. ^ Proof. Let V = 1fX6=X^ g, i.e. V is 1 if X 6= X and 0 otherwise. H(XjY ) ≤ H(X; V jY ) (1) = H(V jY ) + H(XjV; Y ) (2) ≤ H(V ) + H(XjV; Y ) (3) X = H(V ) + H(XjV =v; Y =y)P (V =v; Y =y) (4) v;y X X = H(V ) + H(XjV =0;Y =y)P (V =0;Y =y) + H(XjV =1;Y =y)P (V =1;Y =y) (5) y y X = H(V ) + H(XjV =1;Y =y)P (V =1;Y =y) (6) y X ≤ H(V ) + log(jX j − 1) P (V =1;Y =y) (7) y = H(V ) + log(jX j − 1)P (V =1) (8) = h2(Pe) + Pe log(jX j − 1) (9) 1Reading: Chapter 7.9 and 7.12 of Cover, Thomas M., and Joy A. -

Information Theory and Maximum Entropy 8.1 Fundamentals of Information Theory
NEU 560: Statistical Modeling and Analysis of Neural Data Spring 2018 Lecture 8: Information Theory and Maximum Entropy Lecturer: Mike Morais Scribes: 8.1 Fundamentals of Information theory Information theory started with Claude Shannon's A mathematical theory of communication. The first building block was entropy, which he sought as a functional H(·) of probability densities with two desired properties: 1. Decreasing in P (X), such that if P (X1) < P (X2), then h(P (X1)) > h(P (X2)). 2. Independent variables add, such that if X and Y are independent, then H(P (X; Y )) = H(P (X)) + H(P (Y )). These are only satisfied for − log(·). Think of it as a \surprise" function. Definition 8.1 (Entropy) The entropy of a random variable is the amount of information needed to fully describe it; alternate interpretations: average number of yes/no questions needed to identify X, how uncertain you are about X? X H(X) = − P (X) log P (X) = −EX [log P (X)] (8.1) X Average information, surprise, or uncertainty are all somewhat parsimonious plain English analogies for entropy. There are a few ways to measure entropy for multiple variables; we'll use two, X and Y . Definition 8.2 (Conditional entropy) The conditional entropy of a random variable is the entropy of one random variable conditioned on knowledge of another random variable, on average. Alternative interpretations: the average number of yes/no questions needed to identify X given knowledge of Y , on average; or How uncertain you are about X if you know Y , on average? X X h X i H(X j Y ) = P (Y )[H(P (X j Y ))] = P (Y ) − P (X j Y ) log P (X j Y ) Y Y X X = = − P (X; Y ) log P (X j Y ) X;Y = −EX;Y [log P (X j Y )] (8.2) Definition 8.3 (Joint entropy) X H(X; Y ) = − P (X; Y ) log P (X; Y ) = −EX;Y [log P (X; Y )] (8.3) X;Y 8-1 8-2 Lecture 8: Information Theory and Maximum Entropy • Bayes' rule for entropy H(X1 j X2) = H(X2 j X1) + H(X1) − H(X2) (8.4) • Chain rule of entropies n X H(Xn;Xn−1; :::X1) = H(Xn j Xn−1; :::X1) (8.5) i=1 It can be useful to think about these interrelated concepts with a so-called information diagram. -

A Gentle Tutorial on Information Theory and Learning Roni Rosenfeld Carnegie Mellon University Outline • First Part Based Very
Outline Definition of Information • First part based very loosely on [Abramson 63]. (After [Abramson 63]) • Information theory usually formulated in terms of information Let E be some event which occurs with probability channels and coding — will not discuss those here. P (E). If we are told that E has occurred, then we say that we have received 1. Information 1 I(E) = log2 2. Entropy P (E) bits of information. 3. Mutual Information 4. Cross Entropy and Learning • Base of log is unimportant — will only change the units We’ll stick with bits, and always assume base 2 • Can also think of information as amount of ”surprise” in E (e.g. P (E) = 1, P (E) = 0) • Example: result of a fair coin flip (log2 2= 1 bit) • Example: result of a fair die roll (log2 6 ≈ 2.585 bits) Carnegie Carnegie Mellon 2 ITtutorial,RoniRosenfeld,1999 Mellon 4 ITtutorial,RoniRosenfeld,1999 A Gentle Tutorial on Information Information Theory and Learning • information 6= knowledge Concerned with abstract possibilities, not their meaning Roni Rosenfeld • information: reduction in uncertainty Carnegie Carnegie Mellon University Mellon Imagine: #1 you’re about to observe the outcome of a coin flip #2 you’re about to observe the outcome of a die roll There is more uncertainty in #2 Next: 1. You observed outcome of #1 → uncertainty reduced to zero. 2. You observed outcome of #2 → uncertainty reduced to zero. =⇒ more information was provided by the outcome in #2 Carnegie Mellon 3 ITtutorial,RoniRosenfeld,1999 Entropy Entropy as a Function of a Probability Distribution A Zero-memory information source S is a source that emits sym- Since the source S is fully characterized byP = {p1,...pk} (we bols from an alphabet {s1, s2,...,sk} with probabilities {p1, p2,...,pk}, don’t care what the symbols si actually are, or what they stand respectively, where the symbols emitted are statistically indepen- for), entropy can also be thought of as a property of a probability dent. -

Entropy, Relative Entropy, Cross Entropy Entropy
Entropy, Relative Entropy, Cross Entropy Entropy Entropy, H(x) is a measure of the uncertainty of a discrete random variable. Properties: ● H(x) >= 0 ● Entropy Entropy ● Lesser the probability for an event, larger the entropy. Entropy of a six-headed fair dice is log26. Entropy : Properties Primer on Probability Fundamentals ● Random Variable ● Probability ● Expectation ● Linearity of Expectation Entropy : Properties Primer on Probability Fundamentals ● Jensen’s Inequality Ex:- Subject to the constraint that, f is a convex function. Entropy : Properties ● H(U) >= 0, Where, U = {u , u , …, u } 1 2 M ● H(U) <= log(M) Entropy between pair of R.Vs ● Joint Entropy ● Conditional Entropy Relative Entropy aka Kullback Leibler Distance D(p||q) is a measure of the inefficiency of assuming that the distribution is q, when the true distribution is p. ● H(p) : avg description length when true distribution. ● H(p) + D(p||q) : avg description length when approximated distribution. If X is a random variable and p(x), q(x) are probability mass functions, Relative Entropy/ K-L Divergence : Properties D(p||q) is a measure of the inefficiency of assuming that the distribution is q, when the true distribution is p. Properties: ● Non-negative. ● D(p||q) = 0 if p=q. ● Non-symmetric and does not satisfy triangular inequality - it is rather divergence than distance. Relative Entropy/ K-L Divergence : Properties Asymmetricity: Let, X = {0, 1} be a random variable. Consider two distributions p, q on X. Assume, p(0) = 1-r, p(1) = r ; q(0) = 1-s, q(1) = s; If, r=s, then D(p||q) = D(q||p) = 0, else for r!=s, D(p||q) != D(q||p) Relative Entropy/ K-L Divergence : Properties Non-negativity: Relative Entropy/ K-L Divergence : Properties Relative Entropy of joint distributions as Mutual Information Mutual Information, which is a measure of the amount of information that one random variable contains about another random variable. -

Estimating the Mutual Information Between Two Discrete, Asymmetric Variables with Limited Samples
entropy Article Estimating the Mutual Information between Two Discrete, Asymmetric Variables with Limited Samples Damián G. Hernández * and Inés Samengo Department of Medical Physics, Centro Atómico Bariloche and Instituto Balseiro, 8400 San Carlos de Bariloche, Argentina; [email protected] * Correspondence: [email protected] Received: 3 May 2019; Accepted: 13 June 2019; Published: 25 June 2019 Abstract: Determining the strength of nonlinear, statistical dependencies between two variables is a crucial matter in many research fields. The established measure for quantifying such relations is the mutual information. However, estimating mutual information from limited samples is a challenging task. Since the mutual information is the difference of two entropies, the existing Bayesian estimators of entropy may be used to estimate information. This procedure, however, is still biased in the severely under-sampled regime. Here, we propose an alternative estimator that is applicable to those cases in which the marginal distribution of one of the two variables—the one with minimal entropy—is well sampled. The other variable, as well as the joint and conditional distributions, can be severely undersampled. We obtain a consistent estimator that presents very low bias, outperforming previous methods even when the sampled data contain few coincidences. As with other Bayesian estimators, our proposal focuses on the strength of the interaction between the two variables, without seeking to model the specific way in which they are related. A distinctive property of our method is that the main data statistics determining the amount of mutual information is the inhomogeneity of the conditional distribution of the low-entropy variable in those states in which the large-entropy variable registers coincidences. -
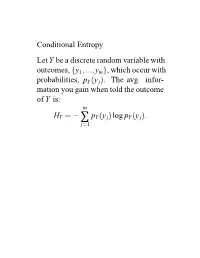
Conditional Entropy Lety Be a Discrete Random Variable with Outcomes
Conditional Entropy Let Y be a discrete random variable with outcomes, {y1,...,ym}, which occur with probabilities, pY (y j). The avg. infor- mation you gain when told the outcome of Y is: m HY = − ∑ pY (y j)log pY (y j). j=1 Conditional Entropy (contd.) Let X be a discrete random variable with outcomes, {x1,...,xn}, which occur with probabilities, pX(xi). Consider the 1D distribution, pY |X=xi(y j)= pY|X(y j |xi) i.e., the distribution of Y outcomes given that X = xi. The avg. information you gain when told the outcome of Y is: m HY|X=xi = − ∑ pY |X(y j |xi)log pY|X(y j |xi). j=1 Conditional Entropy (contd.) The conditional entropy is the expected value for the entropy of pY|X=xi: HY|X = HY|X=xi . It follows that: n HY|X = ∑ pX(xi)HY|X=xi i=1 n m = ∑ pX(xi) − ∑ pY |X(y j |xi)log pY|X (y j |xi) i=1 j=1 ! n m = − ∑ ∑ pX(xi)pY|X (y j |xi)log pY |X (y j |xi). i=1 j=1 The entropy, HY|X, of the conditional distribution, pY|X, is therefore: n m HY|X = − ∑ ∑ pXY (xi,y j)log pY |X(y j |xi). i=1 j=1 Hy Hy|x Figure 1: There is less information in the conditional than in the marginal (Theo- rem 1.2). Theorem 1.2 There is less information in the condi- tional, pY|X, than in the marginal, pY : HY|X − HY ≤ 0.