EM Side-Channel Analysis on Smartphone Early Boot Encryption
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Chapter 1. Origins of Mac OS X
1 Chapter 1. Origins of Mac OS X "Most ideas come from previous ideas." Alan Curtis Kay The Mac OS X operating system represents a rather successful coming together of paradigms, ideologies, and technologies that have often resisted each other in the past. A good example is the cordial relationship that exists between the command-line and graphical interfaces in Mac OS X. The system is a result of the trials and tribulations of Apple and NeXT, as well as their user and developer communities. Mac OS X exemplifies how a capable system can result from the direct or indirect efforts of corporations, academic and research communities, the Open Source and Free Software movements, and, of course, individuals. Apple has been around since 1976, and many accounts of its history have been told. If the story of Apple as a company is fascinating, so is the technical history of Apple's operating systems. In this chapter,[1] we will trace the history of Mac OS X, discussing several technologies whose confluence eventually led to the modern-day Apple operating system. [1] This book's accompanying web site (www.osxbook.com) provides a more detailed technical history of all of Apple's operating systems. 1 2 2 1 1.1. Apple's Quest for the[2] Operating System [2] Whereas the word "the" is used here to designate prominence and desirability, it is an interesting coincidence that "THE" was the name of a multiprogramming system described by Edsger W. Dijkstra in a 1968 paper. It was March 1988. The Macintosh had been around for four years. -

Carbon Copy Cloner Documentation: English
Carbon Copy Cloner Documentation: English Getting started with CCC System Requirements, Installing, Updating, and Uninstalling CCC CCC License, Registration, and Trial FAQs Trouble Applying Your Registration Information? Establishing an initial backup Preparing your backup disk for a backup of Mac OS X Restoring data from your backup What's new in CCC Features of CCC specific to Lion and greater Release History Carbon Copy Cloner's Transition to a Commercial Product: Frequently Asked Questions Credits Example backup scenarios I want to clone my entire hard drive to a new hard drive or a new machine I want to backup my important data to another Macintosh on my network I want to backup multiple machines or hard drives to the same hard drive I want my backup task to run automatically on a scheduled basis Backing up to/from network volumes and other non-HFS volumes I want to back up my whole Mac to a Time Capsule or other network volume I want to defragment my hard drive Backup and archiving settings Excluding files and folders from a backup task Protecting data that is already on your destination volume Managing previous versions of your files Automated maintenance of CCC archives Advanced Settings Some files and folders are automatically excluded from a backup task The Block-Level Copy Scheduling Backup Tasks Scheduling a task and basic settings Performing actions Before and After the backup task Deferring and skipping scheduled tasks Frequently asked questions about scheduled tasks Email and Growl notifications Backing Up to Disk Images -

Mac OS X Intro for UNIX Users
Mac OS X An Introduction for UNIX Users Leon Towns-von Stauber, Occam's Razor Seattle BSD Users Group, October 2004 http://www.occam.com/osx/ X Contents Opening Remarks.............................3 Where Did Mac OS X Come From?.....5 What is Mac OS X?..........................13 A New Kind of UNIX........................25 A Different Kind of UNIX.................28 Why Use Mac OS X?.........................60 Resources.......................................63 Closing Remarks.............................67 X Opening Remarks 3 This is a technical introduction to Mac OS X, mainly targeted to experienced UNIX users for whom OS X is at least relatively new Some emphasis on comparisons with FreeBSD I'm assuming basic familiarity with operating system design Where I'm coming from: UNIX user and some-time admin since 1990 Full-time UNIX admin since 1995 NeXTstep user and admin since 1991 This presentation covers primarily Mac OS X 10.3.5 (Darwin 7.5) X Legal Notices 4 This presentation Copyright © 2003-2004 Leon Towns-von Stauber. All rights reserved. Trademark notices Apple®, Mac®, Macintosh®, Mac OS®, Aqua®, Finder™, Quartz™, Cocoa®, Carbon®, AppleScript®, Rendezvous™, Panther™, and other terms are trademarks of Apple Computer. See <http:// www.apple.com/legal/appletmlist.html>. NeXT®, NeXTstep®, OpenStep®, and NetInfo® are trademarks of NeXT Software. See <http://www.apple.com/legal/nexttmlist.html>. PowerPC™ is a trademark of International Business Machines. Java™ is a trademark of Sun Microsystems. Other trademarks are the property of their -

By Breaking the Seal on This Package You Have Verified That All Items Arrived Undamaged and in Good Condition and Therefore Agree to the Following
STOP! By breaking the seal on this package you have verified that all items arrived undamaged and in good condition and therefore agree to the following: The TSS Product Exchange Policy Terra Soft Solutions, Inc. will be pleased to replace a product that is either defective or has been damaged during shipping. Please contact us at [email protected] in order to obtain a return authorization number. Upon receipt of your defective product, we will ship the replacement. Terra Soft reserves the right to make all final decisions on exchanges. The TSS Product Returns Policy Terra Soft Solutions, Inc. does not accept product returns due to the following: - if the plastic wrapper has been removed from the printed book; - product(s) purchased for a computer that is not supported; - an Install Support agreement that has been initiated; - for 3rd party products sold through the Yellow Dog Linux website, please contact the manufacturer directly. You MUST obtain a Return Authorization Number prior to returning a product from ship- [email protected]. Upon receipt of the returned product, we will either make appropriate compensation to your credit card or deliver a check within 30 days. Terra Soft reserves the right to make all final decisions on returns. Distribution The Yellow Dog Linux Champion Server Installation Manual is distributed by Terra Soft Solutions, Inc. (TSS) as a stand-alone product or as part of a bundle, either direct from TSS or via an official distributor/reseller. TSS may also offer this manual via the Yellow Dog Linux website in an electronic format. Refer to Notice of Rights for additional information. -

Linux Booting Procedure How Linux Boot?
Linux Booting Procedure How Linux boot? 2 What is “boot”? • boot (n.) [1] http://en.wikipedia.org/wiki/Boot 4 Brief etymology[2] • Phrase “pull oneself up by one’s bootstraps” • Misattributed (at latest in 1901!) to “The Surprising Adventures of Baron Munchausen” (1781, Rudolf Erich Raspe) : The baron pulls himself out of a swamp by his hair (pigtail). • The use of this phrase is found in 1834 in the U.S. • “[S]omeone is attempting or has claimed some ludicrously far-fetched or impossible task” • In the 20th century, the “possible bootstrap[3] task” meaning has appeared • “To begin an enterprise or recover from a setback without any outside help; to succeed only on one's own effort or abilities” 5 [2] http://en.wiktionary.org/wiki/pull_oneself_up_by_one%27s_bootstraps [3] http://en.wikipedia.org/wiki/Bootstrapping Bootstrapping (in Computer) • The process of loading the basic software (typically, operating systems) into the main memory from persistent memory (HDD, flash ROM, etc.) • “Boot” is an abbreviation for “bootstrap(ping)” Boostrapping Code 6 System startup Booting sequence 1. Tern on 2. CPU jump to address of BIOS (0xFFFF0) 3. BIOS runs POST (Power-On Self Test) 4. Find bootale devices 5. Loads and execute boot sector form MBR 6. Load OS 5 BIOS (Basic Input/Output System) BIOS refers to the software code run by a computer when first powered on The primary function of BIOS is code program embedded on a chip that recognises and controls various devices that make up the computer. BIOS on board BIOS on screen 6 How computer startup? Booting is a bootstrapping process that starts operating systems when the user turns on a computer system A boot sequence is the set of operations the computer performs when it is switched on that load an operating system 4 Boot loader MBR (Master Boot Record) OS is booted from a hard disk, where the Master Boot Record (MBR) contains the primary boot loader The MBR is a 512-byte sector, located in the first sector on the disk (sector 1 of cylinder 0, head 0) After the MBR is loaded into RAM, the BIOS yields control to it. -

GCIA Exam Dumps by Certkillers.Net
Questions & Answers PDF Page 1 GIAC GCIA Exam GIAC Certified Intrusion Analyst Thank you for Downloading GCIA exam PDF Demo You can Buy Latest GCIA Full Version Download https://www.certkillers.net/Exam/GCIA https://www.certkillers.net Questions & AnswersPDF Pag e 2 Question: 1 Andrew worksas a S y s t e m Administrator f o r NetPerfect Inc.Allclient computers on the network run on Mac OS X. The Sales Manager of the company complains that his MacBook isnot able to boot. Andrew wa nts to check the booting process. Hesuspects that an error persists inthe bootloader of Mac OS X. Whichof the following isthe default bootloader on Mac OS X that he should use to r e s o l v e the issue? A.LILO B. BootX C.NTLoader D. GRUB Answer: B Question: 2 Sasha wa nts to add an entry to yo u r DNS database f o r yo u r mailserver. Whichof the following types of resource records will she use to accomplish this? A.ANAME B. SOA C.MX D. CNAME Answer: C Question: 3 John, a novice webuser, makesa new E-mailaccount and keeps his password as "apple", his f a v o r i t e fruit. John's password isvulnerable to whichof the following password cracking attacks? Each correct answer represents a complete solution. Choose all that apply. A.Dictionary attack B. Hybridattack C.Brute F o r c e attack D. Rule based attack Answer: A, B, C Question: 4 Whichof the following proxy servers isalso referred to as transparent proxies or f o r c e d proxies? A.Tunneling proxy server https://www.certkillers.net Questions & AnswersPDF Pag e 3 B. -
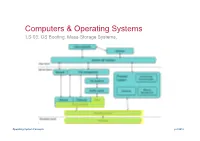
LS-03: OS Booting. Mass-Storage Systems
Computers & Operating Systems LS-03. OS Booting. Mass-Storage Systems. Operating System Concepts ys©2019 Agenda ! 1. OS Booting ! Disk Partition MBR ! Disk Partition GPT ! OS Boot Process: Linux ! UNIX/Linux Run Levels ! 2. Mass-Storage Systems ! Overview of Mass Storage Structure ! Disk Structure ! Disk Attachment ! Disk Management ! Disk Scheduling ! Swap-Space Management ! RAID Structure ! Stable-Storage Implementation Operating System Concepts ys©2019 1. OS BOOTING ! Disk Partition MBR ! Disk Partition GPT ! OS Boot Process: Linux ! UNIX/Linux Run Levels Operating System Concepts ys©2019 Disc partition: Old – MBR (since 1983) ! Partition the disc with MBR structure (max 4 Primary partitions) ! Numbering disk partitions in Linux (ATA disc – hd; SATA disc – sd) MBR - Master Boot Record logical logical primary primary extended Hard disc ! MBR structure ! MBR Disadvantages. ! Commands for disk partition: ! Linux: fdisk, partition, GParted ! Mini loader 446 Byte ! MBR have only 4 boot ! Mac OS: Disk Utility>Volume>Partition ! 4 partition 4x16 Byte (primary) partitions ! Magic Nr 2 Byte (55AA) ! Windows: Administrative Tools ! MBR have the limited size >Computer Management of 32 bits for block >DiskManagement addresses and related information. ! OS Loaders For hard disks with 512-byte ! NTLDR (WinNT) sectors, the MBR partition table entries allow a maximum ! LILO (Linux,BSD) size of (2³²×512 bytes) = 232×29=241= =2×240= 2 TiB ! GRUB (GNU) Today sale 16 TiB (300 $) ! BootX (MacOS) ! Chameleon (CrosOS) Operating System Concepts 3.4 ys©2019 Disc partition: New – GPT (since 2005) ! Partition the disc with GUID-UEFI structure ! GPT - GUID Partition Table ! GUID - globally unique identifier ! UEFI -Unified Extensible Firmware Interface ! Protective MBR - protection against old partitioning tools (compatibility) ! Advantages: ! BackUp copy of GPT for auto repair ! Up to 128 partitions (and more). -

TPS92518-Q1 Automotive Dual Channel Buck LED Controller With
Product Order Technical Tools & Support & Folder Now Documents Software Community TPS92518-Q1 SLUSCZ1 –MAY 2017 TPS92518-Q1 Automotive Dual Channel Buck LED Controller with SPI Interface, Analog and PWM Dimming 1 Features 3 Description The TPS92518-Q1 family of parts are dual channel 1• AEC-Q100 Qualified for Automotive Applications buck LED current controllers with a SPI – Grade 1: –40°C to 125°C Ambient Operating communications interface. The serial communication Temperature interface provides a singular communication path for – Device HBM Classification Level H2 multichannel and platform lighting driver module – Device CDM Classification Level C5 (LDM) applications. • Wide Input Voltage Range 6.5 V to 65 V The TPS92518-Q1 uses a quasi-hysteretic control • Two independent Buck LED Controllers method that supports switching frequencies ranging from 1 kHz to 2 MHz. This control method enables – High Bandwidth, Quasi-Hysteretic Control superior, high frequency shunt FET dimming and also – Adjustable High-Side Sense handles the demanding dynamic loads of adaptive – Direct PWM Dimming Input LED matrix based headlamp systems. – Cycle-by-Cycle Current Limit Software programmable SPI set points (Precision • SPI Communications Interface Peak Current, Controlled Off-Time and Output Voltage Sense) enables designers to develop a single – Software configurable Set Points (8-bit) LED driver solution for multiple load configurations – Digital Calibration and Binning that can be quickly reconfigured for future LED driver – Fault Monitoring and Reporting design requirements. • Advanced, High Precision Dimming The TPS92518-Q1 device has an input range up to – 10,000:1 PWM Dimming Range 42 V. The TPS92518HV-Q1 is a high-voltage option with an input range up to 65 V. -

Module 05 Understanding Storage Media and File System
Understanding Storage Media MODULE 5 Page 1 of 29 Contents 5.1 LEARNING OBJECTIVES ...................................................................................................................... 3 5.2 Hard Disk Drive .................................................................................................................................. 3 5.2.1 Working of HDD .......................................................................................................................... 3 5.2.2 Interface ..................................................................................................................................... 5 5.3 Details of Internal structure of HDD .................................................................................................. 7 5.3.1 Low-Level Formatting ................................................................................................................. 7 5.3.2 High-level formatting ................................................................................................................. 9 5.3.3 Glossary of some important terms ........................................................................................... 10 5.3.3.1 Slack space ......................................................................................................................... 10 5.3.3.2 Lost Cluster ........................................................................................................................ 10 5.3.3.3 Bad Sector......................................................................................................................... -

Inside Mac OS X: System Overview Is Intended for Anyone Who Wants to Develop Software for Mac OS X
Inside Mac OS X System Overview July 2002 Apple Computer, Inc. and TrueType are trademarks of THE WARRANTY AND REMEDIES SET © 2000–2002 Apple Computer, Inc. Apple Computer, Inc., registered in FORTH ABOVE ARE EXCLUSIVE AND All rights reserved. the United States and other countries. IN LIEU OF ALL OTHERS, ORAL OR WRITTEN, EXPRESS OR IMPLIED. No No part of this publication may be Carbon, Quartz, and Velocity Engine Apple dealer, agent, or employee is reproduced, stored in a retrieval are trademarks of Apple Computer, authorized to make any modification, system, or transmitted, in any form or Inc. extension, or addition to this warranty. by any means, mechanical, electronic, Enterprise Objects, Enterprise Objects photocopying, recording, or Framework, NeXT, Objective-C, and Some states do not allow the exclusion or otherwise, without prior written OpenStep are registered trademarks limitation of implied warranties or permission of Apple Computer, Inc., of NeXT Software, Inc., registered in liability for incidental or consequential with the following exceptions: Any the United States and other countries. damages, so the above limitation or person is hereby authorized to store Java and all Java-based trademarks exclusion may not apply to you. This documentation on a single computer are trademarks or registered warranty gives you specific legal rights, for personal use only and to print trademarks of Sun Microsystems, and you may also have other rights which copies of documentation for personal Inc., in the United States and other vary from state to state. use provided that the documentation countries. contains Apple’s copyright notice. Netscape Navigator is a trademark of The Apple logo is a trademark of Netscape Communications Apple Computer, Inc. -

I/O Kit Device Driver Design Guidelines
I/O Kit Device Driver Design Guidelines 2006-10-04 CDB is a trademark of Third Eye Software, Apple Computer, Inc. Inc. © 2002, 2006 Apple Computer, Inc. Intel and Intel Core are registered All rights reserved. trademarks of Intel Corportation or its subsidiaries in the United States and other No part of this publication may be countries. reproduced, stored in a retrieval system, or transmitted, in any form or by any means, PowerPC and and the PowerPC logo are mechanical, electronic, photocopying, trademarks of International Business recording, or otherwise, without prior Machines Corporation, used under license written permission of Apple Computer, Inc., therefrom. with the following exceptions: Any person Simultaneously published in the United is hereby authorized to store documentation States and Canada. on a single computer for personal use only Even though Apple has reviewed this document, and to print copies of documentation for APPLE MAKES NO WARRANTY OR personal use provided that the REPRESENTATION, EITHER EXPRESS OR IMPLIED, WITH RESPECT TO THIS documentation contains Apple’s copyright DOCUMENT, ITS QUALITY, ACCURACY, notice. MERCHANTABILITY, OR FITNESS FOR A PARTICULAR PURPOSE. AS A RESULT, THIS The Apple logo is a trademark of Apple DOCUMENT IS PROVIDED “AS IS,” AND YOU, THE READER, ARE ASSUMING THE Computer, Inc. ENTIRE RISK AS TO ITS QUALITY AND ACCURACY. Use of the “keyboard” Apple logo IN NO EVENT WILL APPLE BE LIABLE FOR (Option-Shift-K) for commercial purposes DIRECT, INDIRECT, SPECIAL, INCIDENTAL, without the prior written consent of Apple OR CONSEQUENTIAL DAMAGES may constitute trademark infringement and RESULTING FROM ANY DEFECT OR INACCURACY IN THIS DOCUMENT, even if unfair competition in violation of federal advised of the possibility of such damages. -
Yellow Dog Linux 3.0.1 1
INTRODUCTION It is advised that you refer to www.yellowdoglinux.com/support/ for updates, issues specific with unique computer configurations, and engineering notes. Please note that this Guide to Install is an addendumto that which is presented on-screen during the installation process. It is not meant to be used as a stand- alone document. Instead, it is designed to provide extra guidance for those portions of the installation process that may otherwise be confusing or tricky. Drive Configurations You may use either a single drive for both Yellow Dog Linux and Mac OS or you may use two or more drives. If you do install at least two drives, one for YDL and the second drive for Mac OS, it is advised that the Yellow Dog Linux drive be placed first in the ATA or SCSI chain (at the time of this writing, neither USB nor FireWire drives are supported as bootable media). To install both operating systems on a single drive, you will require a minimum of two partitions. Unless you have a drive properly configured as such, you must either boot from the Mac OSCD and reformat then reinstall Mac OS (using the Drive Setup application) or use a 3rd party, non-destructive partitioning tool prior to installing Linux. Be certain to back-up all important Mac OS applications and data before working with any partitioning tool. PREPARATION Single Drive: Multi-Boot System with either BootX or yaboot You are now going to use Apple's Drive Setup application to format and partition your drive. Please note that this procedure completely reformats and DESTROYS ALL DATA on your drive.