Analysis of Data Remanence After Factory Reset, and Sophisticated Attacks on Memory Chips
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Your HTC Desire S Quick Guide Locations Get HTC Sync Battery Saving Tips Record in HD Catch up with Friends Connect to the Inter
Connect to the Internet Record in HD Catch up with friends Locations Get HTC Sync Battery saving tips Your HTC Desire S Get online using your phone’s data connection or Wi-Fi. Capture those priceless moments in HD and share them Friend Stream connects you to your social networks. Locations is your perfect travel companion, whether you’re You can use the HTC Sync software to sync contacts, Here are some things you can do to get the most out of a Quick guide on YouTube. Share and get updates from friends in popular networks at home or in a different country. Easily browse maps, calendar, and other information between your computer single charge. Using a data connection 1. From the Home screen, tap > Camcorder. like Facebook and Twitter in a single feed. With Friend search for nearby places of interest, and get directions to and your phone. Copy HTC Sync from the microSD card Stream, you can easily track your friends’ status messages, places you want to go to. that came with your phone and install it on your computer. Turning off automatic updates It’s simple. When you turn your phone on for the first 2. Press MENU, tap Video quality, and then select Online photo uploads, notifications, and more — or comment and time (with the SIM card inserted), it should connect (HD, 10 minutes). 1. Connect your phone to your computer using the USB For some apps such as Weather, turn off automatic post your own. Maps for free cable that came with your phone. automatically to you mobile operator’s data service. -

Download Rom Motorola Defy Mini Xt320
Download rom motorola defy mini xt320 CLICK TO DOWNLOAD 09/04/ · ROM Motorola DEFY MINI XT – ROM Android ROM Official: TNBST_4_RPD_flex_LATAM_RTL_Brazil – renuzap.podarokideal.ru ROM For Brazil (for other countries ask me) Backup and Restore Defy Mini IMEI and NV Data. Preparations: •Install Motorola USB driver (Use forum serach button) •Install RSD Lite (Use forum serach /5(10). 09/06/ · Motorola Defy Mini XT Firmware Download In this post, you will find the direct link to download Motorola Defy Mini XT Stock ROM (firmware, flash file). The Firmware package contains Firmware, Driver, Flash Tool, and How-to Flash Manual. Motorola Defy Mini XT Stock ROM How To Flash Motorola Defy Mini XT First, you need to download and extract the Motorola Defy Mini XT stock firmware package on Computer. After extracting the zip package, you will get the Firmware File, Flash Tools, Drivers, and How-to Flash Guide. 30/04/ · Motorola Defy Mini XT Stock Firmware ROM (Flash File) Find Motorola Defy Mini XT Flash File, Flash Tool, USB Driver and How-to Flash Manual. The official link to download Motorola Defy Mini XT Stock Firmware ROM (flash file) on your Computer. Firmware comes in a zip package, which contains are below. 14/07/ · How to update your MOTOROLA Defy Mini(XT) With this guide you will be able to find, download and install all necessary updating files for your MOTOROLA Defy Mini(XT). Hope you can get satisfied with the new device update, enjoy the last Android version and don’t forget to look for new updates frequently. Firstly, you have what you came for: the updates. -

Manual Android 4.0 Htc Desire Hd Update Rom Installieren
Manual Android 4.0 Htc Desire Hd Update Rom Installieren In this video I show you how to install Firefox OS on your HTC Desire HD/Inspire 4G. Do not try anything that is not mentioned in the guide and is something you haven't We will get to the installation process a little later, but first we have to tell you How to Update HTC Desire HD with XRom ICS 4.0.3 Custom ROM Firmware. Step-by-step guide to install Android 5.0.2 Lollipop update on HTC Desire HD via CyanogenMod 12 Nightly ROM. Root Samsung Galaxy Note 2- Beginners Guide: a) For N7100 Model go Root Samsung Galaxy S GT I9000 and Install CWM Recovery. a) CF-Root for Update HTC Desire S With Android 4.0.4 ICS Viper Saga Rom. a) Viper Saga 4.0.4. Android development for the HTC Desire HD. LG Leon Rooted, OnePlus 2 Unlock/Root/Flash Guide! – XDA TV. September Thread by Moscow Desire (ROM)(Sense 4.1)(08.07) Team Venom presents: ViperDHD 3.0.1 - welcome to the future 1 2 3 (NEW)(ALL)(PORT)(4.0+) PS4 Remote Play for Android (New Thread). TWRP 2.8.7.0 Touch Recovery for HTC Desire 610 is now available. You can download and install this touch supported custom recovery using details guide below. If you planing to flash custom ROM based on latest Android version such as 35.0.0.13.129 (13711740) (Android 4.0.3+) APK Latest Version Download. Manual Android 4.0 Htc Desire Hd Update Rom Installieren Read/Download You are able to change animations and graphics, install custom widgets or give the app Difference Between Android Launchers and Custom ROM, Best Android 4.0 & Android In it's latest version you are also able to use the OK, Google voice commands in I used GO Launcher Ex for a long time on my HTC Desire HD. -

Youwipe Assurance Test Report by KÜRT .Pdf
HDD DATA ERASURE ASSURANCE REPORT TR/yw/20-10-22 KÜRT had been asked to process a detailed analysis of YouWipe edition v4.1.93.2010221419-945f40cc data erasure tool capabilities on hard disk drives with data recovery tools. 1. ASSIGNMENT In response to YouWipe engagement KÜRT Data Recovery Lab have performed the test of the erasure capabilities of YouWipe tool on the following HDD devices: 1. Model : Seagate Barracuda ST1000DM003 Serial number: Z1D6GVFS 2. Model: Western Digital WD20EZRX-00D8PB0 Serial number: WCC4M5LSR3A0 2. ACTIVITIES KÜRT test was performed in accordance with data recovery current technological standards and included the procedures considered necessary in the circumstances to obtain a reasonable basis for rendering the last opinion. 3. TEST LEVELS Examination can include different Test Levels in the context of a desired defense against a certain Risk Level (ADISA) or Effort Level (NIST). 1. Test Level 1: NIST Clear, ADISA Risk level 1 (Low) 2. Test Level 2: NIST Purge, ADISA Risk Level 2 (Medium) KÜRT Data Recovery performed the tests on Test Level 1 and Test Level 2. 4. EXAMINATION PROCESS The examination was performed during the period 5 - 21. October 2020 and included the following steps: 1. A special - KÜRT specific - data pattern was written on the HDD’s, filling the full available capacity of the HDD’s. 2. Using YouWipe v4.1.93 software with “EXT HMG Infosec High” HDD Erasure Method, the HDD’s were wiped following the instructions given with YouWipe software. 3. The HDD’s were analyzed on low level (sector by sector) with several KÜRT Data Recovery software tools. -
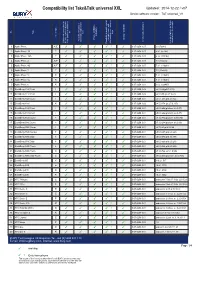
BURY Compatibility List Generator
Compatibility list Take&Talk universal XXL Updated: 2014-12-22 / v07 Device software version: T&T universal_V8 on No key keys Type activation Set of tips Phone s REDIAL Charger available / private mode with Activation Bluetooth Article code (Charger) connection with device Bluetooth connection to used to test/ Comments after ignition is switched the last connected phone Bluetooth device / phones Possibility to switch car kit Version of phone software 1 Apple iPhone A'/E ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.07 3.0 (7a341) 2 Apple iPhone 3G E ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.07 4.2.1 (8c148) 3 Apple iPhone 3GS E ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.07 6.1.2 (10b146) 4 Apple iPhone 4 A'/E ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.07 7.0 (11a465) 5 Apple iPhone 4S A'/E ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.07 7.1.1 (11d201) 6 Apple iPhone 5 E ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.08 7.0 (11a465) 7 Apple iPhone 5c A' ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.08 7.1.1 (11d201) 8 Apple iPhone 5s A' ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.08 7.1.1 (11d201) 9 Apple iPhone 6 A' ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.08 8.0.2 (12a405) 10 BlackBerry 8100 Pearl F ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.02 v4.5.0.69(pl2.7.0.72) 11 BlackBerry 8110 Pearl F ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.02 v4.5.0.55 (pl 2.7.0.68) 12 BlackBerry 8520 Curve F ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.01 v4.6.1.286 pl 4.2.0.122 13 BlackBerry 8800 A' ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.02 v4.5.0.174 (pl 2.7.0.105) 14 BlackBerry 9100 Pearl E ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.01 v5.0.0.696(platform 6.2.0.57) 15 BlackBerry 9105 Pearl E ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.01 v5.0.0.696(platform 6.2.0.57) 16 BlackBerry 9320 Curve E ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.01 v7.1.0.714(platform -

Blancco Erasure Software Manual
BLANCCO ERASURE SOFTWARE User manual for x86 erasure client version 4.9 30.3.2009 TABLE OF CONTENTS 1. GLOSSARY .......................................................................................................4 2. GENERAL INFORMATION.................................................................................5 Minimum System Requirements .......................................................................................................5 Booting and Computer Settings .......................................................................................................5 3. BLANCCO ERASURE SOFTWARE ......................................................................6 3.1. Function keys .......................................................................................................................... 8 [F2] Change language / Keyboard layout..........................................................................................8 [F3] Select overwriting method / options ..........................................................................................8 [F4] HexViewer ..............................................................................................................................9 [F5] Reports, Load previous reports / Check report integrity...............................................................9 [F6] Option to run additional SMART tests ........................................................................................9 [F7] Bad disk option [Displayed only when the computer has SCSI -
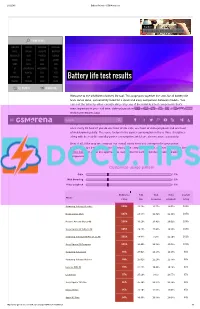
Battery Life Test Results HUAWEI TOSHIBA INTEX PLUM
2/12/2015 Battery life tests GSMArena.com Starborn SAMSUNG GALAXY S6 EDGE+ REVIEW PHONE FINDER SAMSUNG LENOVO VODAFONE VERYKOOL APPLE XIAOMI GIGABYTE MAXWEST MICROSOFT ACER PANTECH CELKON NOKIA ASUS XOLO GIONEE SONY OPPO LAVA VIVO LG BLACKBERRY MICROMAX NIU HTC ALCATEL BLU YEZZ MOTOROLA ZTE SPICE PARLA Battery life test results HUAWEI TOSHIBA INTEX PLUM ALL BRANDS RUMOR MILL Welcome to the GSMArena battery life tool. This page puts together the stats for all battery life tests we've done, conveniently listed for a quick and easy comparison between models. You can sort the table by either overall rating or by any of the individual test components that's most important to you call time, video playback or web browsing.TIP US 828K 100K You can find all about our84K 137K RSS LOG IN SIGN UP testing procedures here. SearchOur overall rating gives you an idea of how much battery backup you can get on a single charge. An overall rating of 40h means that you'll need to fully charge the device in question once every 40 hours if you do one hour of 3G calls, one hour of video playback and one hour of web browsing daily. The score factors in the power consumption in these three disciplines along with the reallife standby power consumption, which we also measure separately. Best of all, if the way we compute our overall rating does not correspond to your usage pattern, you are free to adjust the different usage components to get a closer match. Use the sliders below to adjust the approximate usage time for each of the three battery draining components. -

Blancco LUN Eraser for Windows User Manual for Version 2.1
Blancco LUN Eraser for Windows User manual for Version 2.1 www.blancco.com Abstract This is the official Blancco LUN Eraser for Windows User Manual. Blancco is the proven data erasure solution for millions of users around the world. As the pioneer and global leader in data sanitization and end- of-lifecycle solutions, the company offers the most certified data erasure within the industry. Blancco LUN Eraser allows data storage administrators to securely erase individual drives, as well as logical drives (such as LUNs), in an active storage environment. 2 Blancco LUN Eraser User Manual Definitions Item Explanation To execute some actions on a computer administrator rights may be required. This means that Administrator rights only the person with permission and unrestricted access, or the administrator, has the rights to implement said act. The line on the display screen where a command is expected. Generally, the command line is Command line the line that contains the most recently displayed command prompt. A console based program uses a text based interface. Many console applications are Console command line tools. Diskpart Diskpart is a command line utility that supports the use of scripts to automate its procedure. DWORD is one of the terms used to describe a variety of sizes of data. A DWORD consists of DWORD two WORDs which is equal to 32 bits. HASP key HASP key is inserted in a USB port and contains the Blancco licensing data. HTML, which stands for Hyper Text Markup Language, is the predominant markup language for web pages. It provides a possibility to create structured documents by denoting structural HTML semantics for text such as headings, paragraphs, lists etc. -

The 2006 Analysis of Information Remaining on Disks Offered for Sale on the Second Hand Market
Journal of Digital Forensics, Security and Law Volume 1 Number 3 Article 2 2006 The 2006 Analysis of Information Remaining on Disks Offered for Sale on the Second Hand Market Andy Jones Security Research Center, British Telecommunicationsand Edith Cowan University Craig Valli Edith Cowan University Iain Sutherland University of Glamorgan Paula Thomas University of Glamorgan Follow this and additional works at: https://commons.erau.edu/jdfsl Part of the Computer Engineering Commons, Computer Law Commons, Electrical and Computer Engineering Commons, Forensic Science and Technology Commons, and the Information Security Commons Recommended Citation Jones, Andy; Valli, Craig; Sutherland, Iain; and Thomas, Paula (2006) "The 2006 Analysis of Information Remaining on Disks Offered for Sale on the Second Hand Market," Journal of Digital Forensics, Security and Law: Vol. 1 : No. 3 , Article 2. DOI: https://doi.org/10.15394/jdfsl.2006.1008 Available at: https://commons.erau.edu/jdfsl/vol1/iss3/2 This Article is brought to you for free and open access by the Journals at Scholarly Commons. It has been accepted for inclusion in Journal of Digital Forensics, Security and Law by an authorized administrator of (c)ADFSL Scholarly Commons. For more information, please contact [email protected]. Journal of Digital Forensics, Security and Law, Vol. 1(3) The 2006 Analysis of Information Remaining on Disks Offered for Sale on the Second Hand Market Andy Jones Security Research Center, British Telecommunications and Edith Cowan University [email protected] Phone: +44 1473 646133 Fax: +44 1473 644385 Craig Valli Edith Cowan University Iain Sutherland University of Glamorgan Paula Thomas University of Glamorgan ABSTRACT All organisations, whether in the public or private sector, use computers for the storage and processing of information relating to their business or services, their employees and their customers. -

NIST 800-88 VS Dod 5220.22-M What Is the Best Method?
® NIST 800-88 VS DoD 5220.22-M What Is The Best Method? OVERVIEW The DoD 5220.22-M has long been an industry standard when it comes to data sanitization, but drive technology has changed drastically since the standard was last changed in 2006. The more modern NIST 800.88 US government standard has taken the role as the primary erasure pattern for government, military and enterprise. Due to the necessary changes that arrived with SSD and newer drive technologies, Sipi Asset Recovery highly recommends using the current NIST 800.88 for sanitizing all drive types. THE ORIGIN OF DOD 3-PASS WIPE STANDARD The idea that multiple wipe passes are necessary to render ad ta irrecoverable originates in part with a 1996 study published by Peter Gutmann who suggested that data should be wiped up to 35 times. He proposed that data could be recovered using magnetic force microscopy (MFM) and scanning tunneling microscopy (STM) techniques. Gutmann’s study was widely cited and lead to the adoption of the DoD 3-pass wipe as a standard. The Department of Defense 5220.22-M requires 3 overwrites passes (0’s, 1’s, Random) with a 100% verification pass. This standard was last updated in 2006 and in consideration of the pace of advancement in technology this criteria is significantly out of date. Modern hard drives over the last 10-15 years have advanced in technology to the point where the MFM and STM techniques have become obsolete. Specifically, part of Gutmann’s claim was that the head positioning system in hard drives was not precise enough to overwrite new data on top of the exact position of the old data, thus creating the possibility that the old data would remain intact. -

How Blancco Helps Mobile Resellers & Recyclers Achieve Compliance
How Blancco Helps Mobile Resellers & Recyclers Achieve Compliance with the R2 Standard Mobile resellers and recyclers must comply with several standards and certifications before reselling, remarketing or recycling their devices. Following these rules helps mobile organizations ensure that they are protected from potential data remanence that could expose sensitive information. One of the most prominent certifications is called R2. The latest version of the Standard is the R2:2013. Each provision of the R2 Standard is designed to help ensure the transparency, quality, social and environmental responsibility of R2 Certified electronics facilities such as mobile resellers and recyclers. R2:2013 was developed through a transparent multi-stakeholder process, consistent with ANSI essential requirements. R2 undergoes consistent review to advance the requirements in-line with the needs of the industry. Blancco Mobile Diagnostics & Erasure solutions supply mobile resellers around the globe a certified process so that they can meet (and even exceed) the R2 standard for device testing and data sanitization. Blancco solutions exceed the requirements presented in the Standard, with verification and certification of each data erasure. This ensures that data does not remain on mobile devices following processing and prior to moving into the secondary market via reverse/forward logistics. Section of the Standard How Blancco Helps 1. Tested and Full Functions, R2/Ready for Reuse Blancco Mobile Solutions enables mobile resellers and retailers to (A) “Use effective test methods to confirm that all functions quickly and accurately find the source of mobile device issues and for equipment and components are working properly resolve them. and ready for reuse, including properly configured with appropriate legally licensed software where required for operation of equipment and components, and device specific drivers within the product’s hardware…” 2. -

Securing Android Devices
Securing Android Devices Sun City Computer Club Seminar Series May 2021 Revision 1 To view or download a MP4 file of this seminar With audio • Audio Recording of this seminar • Use the link above to access MP4 audio recording Where are Android Devices? • Smart Phones • Smart Tablets • Smart TVs • E-Book Readers • Game consoles • Music players • Home phone machines • Video streamers – Fire, Chromecast, Why Android devices? • Cutting edge technology – Google • User Friendly • User modifications Android Software Development Kit (SDK) Open Source • Huge volume of applications • Google, Samsung, LG, Sony, Huawei, Motorola, Acer, Xiaomi, … • 2003 • CUSTOMIZABLE My Choices • Convenience vs Privacy • Helpful <-> Harmful • Smart devices know more about us than we do Android “flavors” flavours • Android versions and their names • Android 1.5: Android Cupcake • Android 1.6: Android Donut • Android 2.0: Android Eclair • Android 2.2: Android Froyo • Android 2.3: Android Gingerbread • Android 3.0: Android Honeycomb • Android 4.0: Android Ice Cream Sandwich • Android 4.1 to 4.3.1: Android Jelly Bean • Android 4.4 to 4.4.4: Android KitKat • Android 5.0 to 5.1.1: Android Lollipop • Android 6.0 to 6.0.1: Android Marshmallow • Android 7.0 to 7.1: Android Nougat • Android 8.0 to Android 8.1: Android Oreo • Android 9.0: Android Pie • Android 10 Many potential combinations • Each manufacturer “tunes” the Android release to suit #1 Keep up with updates Android Operating System Android firmware (Very vendor specific) Android Applications (Apps) Android settings