Synthesis of Parallel Algorithms
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Euler Tour Technique: Evaluation of Tree Functions
05‐09‐2015 PARALLEL AND DISTRIBUTED ALGORITHMS BY DEBDEEP MUKHOPADHYAY AND ABHISHEK SOMANI http://cse.iitkgp.ac.in/~debdeep/courses_iitkgp/PAlgo/index.htm THE EULER TOUR TECHNIQUE: EVALUATION OF TREE FUNCTIONS 2 1 05‐09‐2015 OVERVIEW Tree contraction Evaluation of arithmetic expressions 3 PROBLEMS IN PARALLEL COMPUTATIONS OF TREE FUNCTIONS Computations of tree functions are important for designing many algorithms for trees and graphs. Some of these computations include preorder, postorder, inorder numbering of the nodes of a tree, number of descendants of each vertex, level of each vertex etc. 4 2 05‐09‐2015 PROBLEMS IN PARALLEL COMPUTATIONS OF TREE FUNCTIONS Most sequential algorithms for these problems use depth-first search for solving these problems. However, depth-first search seems to be inherently sequential in some sense. 5 PARALLEL DEPTH-FIRST SEARCH It is difficult to do depth-first search in parallel. We cannot assign depth-first numbering to the node n unless we have assigned depth-first numbering to all the nodes in the subtree A. 6 3 05‐09‐2015 PARALLEL DEPTH-FIRST SEARCH There is a definite order of visiting the nodes in depth-first search. We can introduce additional edges to the tree to get this order. The Euler tour technique converts a tree into a list by adding additional edges. 7 PARALLEL DEPTH-FIRST SEARCH The red (or, magenta ) arrows are followed when we visit a node for the first (or, second) time. If the tree has n nodes, we can construct a list with 2n - 2 nodes, where each arrow (directed edge) is a node of the list. -

Area-Efficient Algorithms for Straight-Line Tree Drawings
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Elsevier - Publisher Connector Computational Geometry 15 (2000) 175–202 Area-efficient algorithms for straight-line tree drawings ✩ Chan-Su Shin a;∗, Sung Kwon Kim b;1, Kyung-Yong Chwa a a Department of Computer Science, Korea Advanced Institute of Science and Technology, Taejon 305-701, South Korea b Department of Computer Science and Engineering, Chung-Ang University, Seoul 156-756, South Korea Communicated by R. Tamassia; submitted 1 October 1996; received in revised form 1 November 1999; accepted 9 November 1999 Abstract We investigate several straight-line drawing problems for bounded-degree trees in the integer grid without edge crossings under various types of drawings: (1) upward drawings whose edges are drawn as vertically monotone chains, a sequence of line segments, from a parent to its children, (2) order-preserving drawings which preserve the left-to-right order of the children of each vertex, and (3) orthogonal straight-line drawings in which each edge is represented as a single vertical or horizontal segment. Main contribution of this paper is a unified framework to reduce the upper bound on area for the straight-line drawing problems from O.n logn/ (Crescenzi et al., 1992) to O.n log logn/. This is the first solution of an open problem stated by Garg et al. (1993). We also show that any binary tree admits a small area drawing satisfying any given aspect ratio in the orthogonal straight-line drawing type. Our results are briefly summarized as follows. -

15-122: Principles of Imperative Computation, Fall 2010 Assignment 6: Trees and Secret Codes
15-122: Principles of Imperative Computation, Fall 2010 Assignment 6: Trees and Secret Codes Karl Naden (kbn@cs) Out: Tuesday, March 22, 2010 Due (Written): Tuesday, March 29, 2011 (before lecture) Due (Programming): Tuesday, March 29, 2011 (11:59 pm) 1 Written: (25 points) The written portion of this week’s homework will give you some practice reasoning about variants of binary search trees. You can either type up your solutions or write them neatly by hand, and you should submit your work in class on the due date just before lecture begins. Please remember to staple your written homework before submission. 1.1 Heaps and BSTs Exercise 1 (3 pts). Draw a tree that matches each of the following descriptions. a) Draw a heap that is not a BST. b) Draw a BST that is not a heap. c) Draw a non-empty BST that is also a heap. 1.2 Binary Search Trees Refer to the binary search tree code posted on the course website for Lecture 17 if you need to remind yourself how BSTs work. Exercise 2 (4 pts). The height of a binary search tree (or any binary tree for that matter) is the number of levels it has. (An empty binary tree has height 0.) (a) Write a function bst height that returns the height of a binary search tree. You will need a wrapper function with the following specification: 1 int bst_height(bst B); This function should not be recursive, but it will require a helper function that will be recursive. See the BST code for examples of wrapper functions and recursive helper functions. -

Algorithms Documentation Release 1.0.0
algorithms Documentation Release 1.0.0 Nic Young April 14, 2018 Contents 1 Usage 3 2 Features 5 3 Installation: 7 4 Tests: 9 5 Contributing: 11 6 Table of Contents: 13 6.1 Algorithms................................................ 13 Python Module Index 31 i ii algorithms Documentation, Release 1.0.0 Algorithms is a library of algorithms and data structures implemented in Python. The main purpose of this library is to be an educational tool. You probably shouldn’t use these in production, instead, opting for the optimized versions of these algorithms that can be found else where. You should totally check out the docs for implementation details, complexities and further info. Contents 1 algorithms Documentation, Release 1.0.0 2 Contents CHAPTER 1 Usage If you want to use the algorithms in your code it is as simple as: from algorithms.sorting import bubble_sort my_list= bubble_sort.sort(my_list) 3 algorithms Documentation, Release 1.0.0 4 Chapter 1. Usage CHAPTER 2 Features • Pseudo code, algorithm complexities and futher info with each algorithm. • Test coverage for each algorithm and data structure. • Super sweet documentation. 5 algorithms Documentation, Release 1.0.0 6 Chapter 2. Features CHAPTER 3 Installation: Installation is as easy as: $ pip install algorithms 7 algorithms Documentation, Release 1.0.0 8 Chapter 3. Installation: CHAPTER 4 Tests: Pytest is used as the main test runner and all Unit Tests can be run with: $ ./run_tests.py 9 algorithms Documentation, Release 1.0.0 10 Chapter 4. Tests: CHAPTER 5 Contributing: Contributions are always welcome. Check out the contributing guidelines to get started. -

15–210: Parallel and Sequential Data Structures and Algorithms
Full Name: Andrew ID: Section: 15{210: Parallel and Sequential Data Structures and Algorithms Practice Final (Solutions) December 2016 • Verify: There are 22 pages in this examination, comprising 8 questions worth a total of 152 points. The last 2 pages are an appendix with costs of sequence, set and table operations. • Time: You have 180 minutes to complete this examination. • Goes without saying: Please answer all questions in the space provided with the question. Clearly indicate your answers. 1 • Beware: You may refer to your two< double-sided 8 2 × 11in sheet of paper with notes, but to no other person or source, during the examination. • Primitives: In your algorithms you can use any of the primitives that we have covered in the lecture. A reasonably comprehensive list is provided at the end. • Code: When writing your algorithms, you can use ML syntax but you don't have to. You can use the pseudocode notation used in the notes or in class. For example you can use the syntax that you have learned in class. In fact, in the questions, we use the pseudo rather than the ML notation. Sections A 9:30am - 10:20am Andra/Charlie B 10:30am - 11:20am Andres/Emma C 12:30pm - 1:20pm Anatol/John D 12:30pm - 1:20pm Aashir/Ashwin E 1:30pm - 2:20pm Nathaniel/Sonya F 3:30pm - 4:20pm Teddy/Vivek G 4:30pm - 5:20pm Alex/Patrick 15{210 Practice Final 1 of 22 December 2016 Full Name: Andrew ID: Question Points Score Binary Answers 30 Costs 12 Short Answers 26 Slightly Longer Answers 20 Neighborhoods 20 Median ADT 12 Geometric Coverage 12 Swap with Compare-and-Swap 20 Total: 152 15{210 Practice Final 2 of 22 December 2016 Question 1: Binary Answers (30 points) (a) (2 points) TRUE or FALSE: The expressions (Seq.reduce f I A) and (Seq.iterate f I A) always return the same result as long as f is commutative. -

Dynamic Trees 2005; Werneck, Tarjan
Dynamic Trees 2005; Werneck, Tarjan Renato F. Werneck, Microsoft Research Silicon Valley www.research.microsoft.com/˜renatow Entry editor: Giuseppe Italiano Index Terms: Dynamic trees, link-cut trees, top trees, topology trees, ST- trees, RC-trees, splay trees. Synonyms: Link-cut trees. 1 Problem Definition The dynamic tree problem is that of maintaining an arbitrary n-vertex for- est that changes over time through edge insertions (links) and deletions (cuts). Depending on the application, one associates information with ver- tices, edges, or both. Queries and updates can deal with individual vertices or edges, but more commonly they refer to entire paths or trees. Typical operations include finding the minimum-cost edge along a path, determining the minimum-cost vertex in a tree, or adding a constant value to the cost of each edge on a path (or of each vertex of a tree). Each of these operations, as well as links and cuts, can be performed in O(log n) time with appropriate data structures. 2 Key Results The obvious solution to the dynamic tree problem is to represent the forest explicitly. This, however, is inefficient for queries dealing with entire paths or trees, since it would require actually traversing them. Achieving O(log n) time per operation requires mapping each (possibly unbalanced) input tree into a balanced tree, which is better suited to maintaining information about paths or trees implicitly. There are three main approaches to perform the mapping: path decomposition, tree contraction, and linearization. 1 Path decomposition. The first efficient dynamic tree data structure was Sleator and Tarjan’s ST-trees [13, 14], also known as link-cut trees or simply dynamic trees. -

Massively Parallel Dynamic Programming on Trees∗
Massively Parallel Dynamic Programming on Trees∗ MohammadHossein Bateniy Soheil Behnezhadz Mahsa Derakhshanz MohammadTaghi Hajiaghayiz Vahab Mirrokniy Abstract Dynamic programming is a powerful technique that is, unfortunately, often inherently se- quential. That is, there exists no unified method to parallelize algorithms that use dynamic programming. In this paper, we attempt to address this issue in the Massively Parallel Compu- tations (MPC) model which is a popular abstraction of MapReduce-like paradigms. Our main result is an algorithmic framework to adapt a large family of dynamic programs defined over trees. We introduce two classes of graph problems that admit dynamic programming solutions on trees. We refer to them as \(poly log)-expressible" and \linear-expressible" problems. We show that both classes can be parallelized in O(log n) rounds using a sublinear number of machines and a sublinear memory per machine. To achieve this result, we introduce a series of techniques that can be plugged together. To illustrate the generality of our framework, we implement in O(log n) rounds of MPC, the dynamic programming solution of graph problems such as minimum bisection, k-spanning tree, maximum independent set, longest path, etc., when the input graph is a tree. arXiv:1809.03685v2 [cs.DS] 14 Sep 2018 ∗This is the full version of a paper [8] appeared at ICALP 2018. yGoogle Research, New York. Email: fbateni,[email protected]. zDepartment of Computer Science, University of Maryland. Email: fsoheil,mahsaa,[email protected]. Supported in part by NSF CAREER award CCF-1053605, NSF BIGDATA grant IIS-1546108, NSF AF:Medium grant CCF-1161365, DARPA GRAPHS/AFOSR grant FA9550-12-1-0423, and another DARPA SIMPLEX grant. -

Design and Analysis of Data Structures for Dynamic Trees
Design and Analysis of Data Structures for Dynamic Trees Renato Werneck Advisor: Robert Tarjan Outline The Dynamic Trees problem ) Existing data structures • A new worst-case data structure • A new amortized data structure • Experimental results • Final remarks • The Dynamic Trees Problem Dynamic trees: • { Goal: maintain an n-vertex forest that changes over time. link(v; w): adds edge between v and w. ∗ cut(v; w): deletes edge (v; w). ∗ { Application-specific data associated with vertices/edges: updates/queries can happen in bulk (entire paths or trees at once). ∗ Concrete examples: • { Find minimum-weight edge on the path between v and w. { Add a value to every edge on the path between v and w. { Find total weight of all vertices in a tree. Goal: O(log n) time per operation. • Applications Subroutine of network flow algorithms • { maximum flow { minimum cost flow Subroutine of dynamic graph algorithms • { dynamic biconnected components { dynamic minimum spanning trees { dynamic minimum cut Subroutine of standard graph algorithms • { multiple-source shortest paths in planar graphs { online minimum spanning trees • · · · Application: Online Minimum Spanning Trees Problem: • { Graph on n vertices, with new edges \arriving" one at a time. { Goal: maintain the minimum spanning forest (MSF) of G. Algorithm: • { Edge e = (v; w) with length `(e) arrives: 1. If v and w in different components: insert e; 2. Otherwise, find longest edge f on the path v w: · · · `(e) < `(f): remove f and insert e. ∗ `(e) `(f): discard e. ∗ ≥ Example: Online Minimum Spanning Trees Current minimum spanning forest. • Example: Online Minimum Spanning Trees Edge between different components arrives. • Example: Online Minimum Spanning Trees Edge between different components arrives: • { add it to the forest. -

MATHEMATICAL ENGINEERING TECHNICAL REPORTS Balanced
MATHEMATICAL ENGINEERING TECHNICAL REPORTS Balanced Ternary-Tree Representation of Binary Trees and Balancing Algorithms Kiminori MATSUZAKI and Akimasa MORIHATA METR 2008–30 July 2008 DEPARTMENT OF MATHEMATICAL INFORMATICS GRADUATE SCHOOL OF INFORMATION SCIENCE AND TECHNOLOGY THE UNIVERSITY OF TOKYO BUNKYO-KU, TOKYO 113-8656, JAPAN WWW page: http://www.keisu.t.u-tokyo.ac.jp/research/techrep/index.html The METR technical reports are published as a means to ensure timely dissemination of scholarly and technical work on a non-commercial basis. Copyright and all rights therein are maintained by the authors or by other copyright holders, notwithstanding that they have offered their works here electronically. It is understood that all persons copying this information will adhere to the terms and constraints invoked by each author’s copyright. These works may not be reposted without the explicit permission of the copyright holder. Balanced Ternary-Tree Representation of Binary Trees and Balancing Algorithms Kiminori Matsuzaki and Akimasa Morihata Abstract. In this paper, we propose novel representation of binary trees, named the balanced ternary-tree representation. We examine flexible division of binary trees in which we can divide a tree at any node rather than just at the root, and introduce the ternary-tree representation for the flexible division. Due to the flexibility of division, for any binary tree, balanced or ill-balanced, there is always a balanced ternary tree representing it. We also develop three algorithms for generating balanced ternary-tree representation from binary trees and for rebalancing the ternary-tree representation after a small change of the shape. We not only show theoretical upper bounds of heights of the ternary-tree representation, but also report experiment results about the balance property in practical settings. -
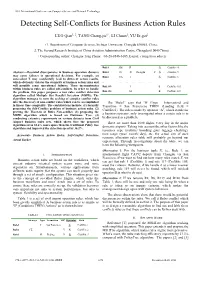
Detecting Self-Conflicts for Business Action Rules
2011 International Conference on Computer Science and Network Technology Detecting Self-Conflicts for Business Action Rules LUO Qian1, 2, TANG Chang-jie1+, LI Chuan1, YU Er-gai2 (1. Department of Computer Science, Sichuan University, Chengdu 610065, China; 2. The Second Research Institute of China Aviation Administration Centre, Chengdu 610041China) + Corresponding author: Changjie Tang Phone: +86-28-8546-6105, E-mail: [email protected] Rule4 FM D A CraftSite 4 Abstract—Essential discrepancies in business operation datasets Rule5 3U D Chengdu Y A CraftSite 5 may cause failures in operational decisions. For example, an Rule6 CA I A CraftSite 6 antecedent X may accidentally lead to different action results, which obviously violates the atomicity of business action rules and … … … … … … … will possibly cause operational failures. These inconsistencies Rule119 I B CraftSite 105 within business rules are called self-conflicts. In order to handle the problem, this paper proposes a fast rules conflict detection Rule120 M B CraftSite 229 algorithm called Multiple Slot Parallel Detection (MSPD). The algorithm manages to turn the seeking of complex conflict rules into the discovery of non-conflict rules which can be accomplished The “Rule1” says that “IF (Type = International and in linear time complexity. The contributions include: (1) formally Transition = San Francisco) THEN (Landing field = proposing the Self-Conflict problem of business action rules, (2) CraftSite1). The rule is made by operator “A", which stands for proving the Theorem of Rules Non-conflict, (3) proposing the MSPD algorithm which is based on Huffman- Tree, (4) a business operator, only investigated when a certain rule is to conducting extensive experiments on various datasets from Civil be discussed as a problem. -

Dynamic Trees in Practice
Dynamic Trees in Practice ROBERT E. TARJAN Princeton University and HP Labs and RENATO F. WERNECK Microsoft Research Silicon Valley Dynamic tree data structures maintain forests that change over time through edge insertions and deletions. Besides maintaining connectivity information in logarithmic time, they can support aggregation of information over paths, trees, or both. We perform an experimental comparison of several versions of dynamic trees: ST-trees, ET-trees, RC-trees, and two variants of top trees (self-adjusting and worst-case). We quantify their strengths and weaknesses through tests with various workloads, most stemming from practical applications. We observe that a simple, linear- time implementation is remarkably fast for graphs of small diameter, and that worst-case and randomized data structures are best when queries are very frequent. The best overall performance, however, is achieved by self-adjusting ST-trees. Categories and Subject Descriptors: E.1 [Data Structures]: Trees; G.2.1 [Discrete Mathe- matics]: Combinatorics—Combinatorial Algorithms; G.2.2 [Discrete Mathematics]: Graph Theory—Network Problems General Terms: Algorithms, Experimentation Additional Key Words and Phrases: dynamic trees, link-cut trees, top trees, experimental evalu- ation 1. INTRODUCTION The dynamic tree problem is that of maintaining an n-vertex forest that changes over time. Edges can be added or deleted in any order, as long as no cycle is ever created. In addition, data can be associated with vertices, edges, or both. This data can be manipulated individually (one vertex or edge at a time) or in bulk, with operations that deal with an entire path or tree at a time. -

Optimal Logarithmic Time Randomized Suffix Tree Construction
Optimal Logarithmic Time Randomized Suffix Tree Construction Martin Farach∗ S. Muthukrishnan† Rutgers University Univ. of Warwick November 10, 1995 Abstract The suffix tree of a string, the fundamental data structure in the area of combinatorial pattern matching, has many elegant applications. In this paper, we present a novel, simple sequential algorithm for the construction of suffix trees. We are also able to parallelize our algorithm so that we settle the main open problem in the construction of suffix trees: we give a Las Vegas CRCW PRAM algorithm that constructs the suffix tree of a binary string of length n in O(log n) time and O(n) work with high probability. In contrast, the previously known 2 work-optimal algorithms, while deterministic, take Ω(log n) time. We also give a work-optimal randomized comparison-based algorithm to convert any string over an unbounded alphabet to an equivalent string over a binary alphabet. As a result, we ob- tain the first work-optimal algorithm for suffix tree construction under the unbounded alphabet assumption. ∗Department of Computer Science, Rutgers University, Piscataway, NJ 08855, USA. ([email protected], http://www.cs.rutgers.edu/∼farach) Supported by NSF Career Development Award CCR-9501942. Work done while this author was a Visitor Member of the Courant Institute of NYU. †[email protected]; Partly supported by DIMACS (Center for Discrete Mathematics and Theoretical Computer Science), a National Science Foundation Science and Technology Center under NSF contract STC-8809648. Partly supported by Alcom IT. 1 Introduction Given a string s of length n, the suffix tree Ts of s is the compacted trie of all the suffixes of s.