UNAUTHORIZED ACCESS ––––––––––––––––––––––––––––––––––––––––––––––––– the Crisis in Online Privacy and Security
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Designing Secure Systems That People Can
15- SSL, PKIs, and Secure Communication Engineering & Public Policy Lorrie Cranor, Blase Ur, and Rich Shay March 3, 2015 05-436 / 05-836 / 08-534 / 08-734 Usable Privacy and Security 1 Today! • An introduction to SSL/TLS • An introduction to PKIs • Recent developments in this area • Usability issues • An activity to make it better 2 Overview • Secure Sockets Layer (SSL) and its successor, Transport Layer Security (TLS) enable secure communication • Frequently encountered with web browsing (HTTPS) and more behind the scenes in app, VOIP, etc. 3 What we want to defend against • People snooping on our communications – The contents of what we’re sending – Session tokens (see, e.g., Firesheep) • Man-in-the-middle attacks – We want to authenticate that we are talking to the right site, not an imposter – Use certificates inside a public-key infrastructure 4 How we could obtain trust • Web of trust – People you already trust introduce you to people they trust – Can get complicated, doesn’t scale well – Less frequently seen in practice • Public-Key Infrastructure (PKI) – Certificates are issued by certificate authorities that bind cryptographic keys to identities 5 Public-Key Infrastucture • Binding of keys to identities can be done automatically or by humans 6 What does SSL look like to users? • Compare, e.g., the following: – https://www.google.com (normal certificate) – Go to Google images and then click on an image and see what happens (mixed content) – https://otalliance.org (EV certificate) 7 What does PKI look like to browsers? • Hundreds -

The Flightgear Manual
The FlightGear Manual Michael Basler, Martin Spott, Stuart Buchanan, Jon Berndt, Bernhard Buckel, Cameron Moore, Curt Olson, Dave Perry, Michael Selig, Darrell Walisser, and others The FlightGear Manual February 22, 2010 For FlightGear version 2.0.0 2 Contents 0.1 Condensed Reading.........................6 0.2 Instructions For the Truly Impatient................6 0.3 Further Reading...........................6 I Installation9 1 Want to have a free flight? Take FlightGear! 11 1.1 Yet Another Flight Simulator?................... 11 1.2 System Requirements........................ 14 1.3 Choosing A Version......................... 15 1.4 Flight Dynamics Models...................... 16 1.5 About This Guide.......................... 16 2 Preflight: Installing FlightGear 19 2.1 Installing scenery.......................... 19 2.1.1 MS Windows Vista/7.................... 20 2.1.2 Mac OS X......................... 20 2.1.3 FG_SCENERY....................... 20 2.1.4 Fetch Scenery as you fly.................. 21 2.1.5 Creating your own Scenery................. 22 2.2 Installing aircraft.......................... 22 2.3 Installing documentation...................... 22 II Flying with FlightGear 25 3 Takeoff: How to start the program 27 3.1 Environment Variables....................... 27 3.1.1 FG_ROOT......................... 27 3.1.2 FG_SCENERY....................... 27 3.1.3 Environment Variables on Windows and Mac OS X.... 27 3.2 Launching the simulator under Unix/Linux............ 28 3.3 Launching the simulator under Windows.............. 29 3.3.1 Launching from the command line............. 30 3 4 CONTENTS 3.4 Launching the simulator under Mac OS X............. 30 3.4.1 Selecting an aircraft and an airport............. 31 3.4.2 Enabling on-the-fly scenery downloading......... 31 3.4.3 Enabling Navigation Map (Atlas)............ -

Spy Culture and the Making of the Modern Intelligence Agency: from Richard Hannay to James Bond to Drone Warfare By
Spy Culture and the Making of the Modern Intelligence Agency: From Richard Hannay to James Bond to Drone Warfare by Matthew A. Bellamy A dissertation submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy (English Language and Literature) in the University of Michigan 2018 Dissertation Committee: Associate Professor Susan Najita, Chair Professor Daniel Hack Professor Mika Lavaque-Manty Associate Professor Andrea Zemgulys Matthew A. Bellamy [email protected] ORCID iD: 0000-0001-6914-8116 © Matthew A. Bellamy 2018 DEDICATION This dissertation is dedicated to all my students, from those in Jacksonville, Florida to those in Port-au-Prince, Haiti and Ann Arbor, Michigan. It is also dedicated to the friends and mentors who have been with me over the seven years of my graduate career. Especially to Charity and Charisse. ii TABLE OF CONTENTS Dedication ii List of Figures v Abstract vi Chapter 1 Introduction: Espionage as the Loss of Agency 1 Methodology; or, Why Study Spy Fiction? 3 A Brief Overview of the Entwined Histories of Espionage as a Practice and Espionage as a Cultural Product 20 Chapter Outline: Chapters 2 and 3 31 Chapter Outline: Chapters 4, 5 and 6 40 Chapter 2 The Spy Agency as a Discursive Formation, Part 1: Conspiracy, Bureaucracy and the Espionage Mindset 52 The SPECTRE of the Many-Headed HYDRA: Conspiracy and the Public’s Experience of Spy Agencies 64 Writing in the Machine: Bureaucracy and Espionage 86 Chapter 3: The Spy Agency as a Discursive Formation, Part 2: Cruelty and Technophilia -
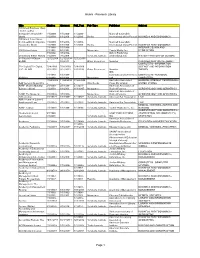
Research Library Page 1
Alumni - Research Library Title Citation Abstract Full_Text Pub Type Publisher Subject 100 Great Business Ideas : from Leading Companies Around the 1/1/2009- 1/1/2009- 1/1/2009- Marshall Cavendish World 1/1/2009 1/1/2009 1/1/2009 Books International (Asia) Pte Ltd BUSINESS AND ECONOMICS 100 Great Sales Ideas : from Leading Companies 1/1/2009- 1/1/2009- 1/1/2009- Marshall Cavendish Around the World 1/1/2009 1/1/2009 1/1/2009 Books International (Asia) Pte Ltd BUSINESS AND ECONOMICS 1/1/1988- 1/1/1988- INTERIOR DESIGN AND 1001 Home Ideas 6/1/1991 6/1/1991 Magazines Family Media, Inc. DECORATION 3/1/2002- 3/1/2002- Oxford Publishing 20 Century British History 7/1/2009 7/1/2009 Scholarly Journals Limited(England) HISTORY--HISTORY OF EUROPE 33 Charts [33 Charts - 12/12/2009 12/12/2009- 12/12/2009 BLOG] + 6/3/2011 + Other Resources Newstex CHILDREN AND YOUTH--ABOUT COMPUTERS--INFORMATION 50+ Digital [50+ Digital, 7/28/2009- 7/28/2009- 7/28/2009- SCIENCE AND INFORMATION LLC - BLOG] 2/22/2010 2/22/2010 2/22/2010 Other Resources Newstex THEORY IDG 1/1/1988- 1/1/1988- Communications/Peterboro COMPUTERS--PERSONAL 80 Micro 6/1/1988 6/1/1988 Magazines ugh COMPUTERS 11/24/2004 11/24/2004 11/24/2004 Australian Associated GENERAL INTEREST PERIODICALS-- AAP General News Wire + + + Wire Feeds Press Pty Limited UNITED STATES AARP Modern Maturity; 2/1/1988- 2/1/1988- 2/1/1991- American Association of [Library edition] 1/1/2003 1/1/2003 11/1/1997 Magazines Retired Persons GERONTOLOGY AND GERIATRICS American Association of AARP The Magazine 3/1/2003+ 3/1/2003+ Magazines Retired Persons GERONTOLOGY AND GERIATRICS ABA Journal 8/1/1972+ 1/1/1988+ 1/1/1992+ Scholarly Journals American Bar Association LAW ABA Journal of Labor & Employment Law 7/1/2007+ 7/1/2007+ 7/1/2007+ Scholarly Journals American Bar Association LAW MEDICAL SCIENCES--NURSES AND ABNF Journal 1/1/1999+ 1/1/1999+ 1/1/1999+ Scholarly Journals Tucker Publications, Inc. -

Developing an Enterprise Operating System for the Monitoring and Control of Enterprise Operations Joseph Youssef
Developing an enterprise operating system for the monitoring and control of enterprise operations Joseph Youssef To cite this version: Joseph Youssef. Developing an enterprise operating system for the monitoring and control of enterprise operations. Other [cond-mat.other]. Université de Bordeaux, 2017. English. NNT : 2017BORD0761. tel-01760341 HAL Id: tel-01760341 https://tel.archives-ouvertes.fr/tel-01760341 Submitted on 6 Apr 2018 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. THÈSE PRÉSENTÉE POUR OBTENIR LE GRADE DE DOCTEUR DE L’UNIVERSITÉ DE BORDEAUX ECOLE DOCTORALE DES SCIENCES PHYSIQUES ET DE L’INGÉNIEUR SPECIALITE : PRODUCTIQUE Par Joseph YOUSSEF DEVELOPING AN ENTERPRISE OPERATING SYSTEM FOR THE MONITORING AND CONTROL OF ENTERPRISE OPERATIONS Sous la direction de : David CHEN (Co-directeur : Gregory ZACHAREWICZ) Soutenue le 21 Décembre 2017 Membres du jury : M. DUCQ, Yves Professeur, Université de Bordeaux Président M. KASSEL, Stephan Professeur, Université des Sciences Appliquées de Zwickau Rapporteur M. ARCHIMEDE, Bernard Professeur, Ecole Nationale D’Ingénieurs de Tarbes Rapporteur M. CHEN, David Professeur, Université de Bordeaux Directeur M. ZACHAREWICZ, Gregory MCF (H.D.R), Université de Bordeaux Co-directeur M. DACLIN, Nicolas Maître-Assistant, Ecole des Mines d’Alès Examinateur 2 Titre : Développement d’un Système D’exploitation des Entreprises pour le Suivi et le Contrôle des Opérations. -

2011-2012 CJFE's Review of Free Expression in Canada
2011-2012 CJFE’s Review of Free Expression in Canada LETTER FROM THE EDITORS OH, HOW THE MIGHTY FALL. ONCE A LEADER IN ACCESS TO INFORMATION, PEACEKEEPING, HUMAN RIGHTS AND MORE, CANADA’S GLOBAL STOCK HAS PLUMMETED IN RECENT YEARS. This Review begins, as always, with a Report Card that grades key issues, institutions and governmental departments in terms of how their actions have affected freedom of expres- sion and access to information between May 2011 and May 2012. This year we’ve assessed Canadian scientists’ freedom of expression, federal protection of digital rights and Internet JOIN CJFE access, federal access to information, the Supreme Court, media ownership and ourselves—the Canadian public. Being involved with CJFE is When we began talking about this Review, we knew we wanted to highlight a major issue with a series of articles. There were plenty of options to choose from, but we ultimately settled not restricted to journalists; on the one topic that is both urgent and has an impact on your daily life: the Internet. Think about it: When was the last time you went a whole day without accessing the membership is open to all Internet? No email, no Skype, no gaming, no online shopping, no Facebook, Twitter or Instagram, no news websites or blogs, no checking the weather with that app. Can you even who believe in the right to recall the last time you went totally Net-free? Our series on free expression and the Internet (beginning on p. 18) examines the complex free expression. relationship between the Internet, its users and free expression, access to information, legislation and court decisions. -

On the Privacy Implications of Real Time Bidding
On the Privacy Implications of Real Time Bidding A Dissertation Presented by Muhammad Ahmad Bashir to The Khoury College of Computer Sciences in partial fulfillment of the requirements for the degree of Doctor of Philosophy in Computer Science Northeastern University Boston, Massachusetts August 2019 To my parents, Javed Hanif and Najia Javed for their unconditional support, love, and prayers. i Contents List of Figures v List of Tables viii Acknowledgmentsx Abstract of the Dissertation xi 1 Introduction1 1.1 Problem Statement..................................3 1.1.1 Information Sharing Through Cookie Matching...............3 1.1.2 Information Sharing Through Ad Exchanges During RTB Auctions....5 1.2 Contributions.....................................5 1.2.1 A Generic Methodology For Detecting Information Sharing Among A&A companies..................................6 1.2.2 Transparency & Compliance: An Analysis of the ads.txt Standard...7 1.2.3 Modeling User’s Digital Privacy Footprint..................9 1.3 Roadmap....................................... 10 2 Background and Definitions 11 2.1 Online Display Advertising.............................. 11 2.2 Targeted Advertising................................. 13 2.2.1 Online Tracking............................... 14 2.2.2 Retargeted Ads................................ 14 2.3 Real Time Bidding.................................. 14 2.3.1 Overview................................... 15 2.3.2 Cookie Matching............................... 16 2.3.3 Advertisement Served via RTB....................... -

Co-Simulation of Matlab and Flightgear for Identification And
Guilherme Aschauer et al. / IFAC-PapersOnLine 48-1 (2015) 067–072 8th Vienna International Conference on Mathematical Modelling February8th Vienna 18 International - 20, 2015. Vienna Conference University on Mathematical of Technology, Modelling Vienna, 8th Vienna International Conference on Mathematical Modelling AustriaFebruary 18 - 20, 2015. Vienna UniversityAvailable of Technology, online at Vienna,www.sciencedirect.com AustriaFebruary 18 - 20, 2015. Vienna University of Technology, Vienna, Austria ScienceDirect IFAC-PapersOnLine 48-1 (2015) 067–072 Co-Simulation of Matlab and FlightGear Co-Simulation of Matlab and FlightGear for Identification and Control of Aircraft for Identification and Control of Aircraft Guilherme Aschauer ∗ Alexander Schirrer ∗ Martin Kozek ∗ Guilherme Aschauer ∗ Alexander Schirrer ∗ Martin Kozek ∗ Guilherme Aschauer ∗ Alexander Schirrer ∗ Martin Kozek ∗ Inst. of Mechanics & Mechatronics, Vienna University of Technology, ∗ Inst. of Mechanics & Mechatronics, Vienna University of Technology, ∗ Austria ∗ Inst. of Mechanics & Mechatronics,Austria Vienna University of Technology, e-mail: [email protected] e-mail: [email protected] e-mail: [email protected] Abstract: The paper outlines the development of a co-simulation solution of Matlab and Flight- Abstract: The paper outlines the development of a co-simulation solution of Matlab and Flight- Gear in which the communication between these programs is done via UDP without needing GearAbstract: in whichThe the paper communication outlines the development between these of a programs co-simulation is done solution via UDP of Matlab without and needing Flight- further toolsets. The simulation and rendering is done by FlightGear. Flight measurement signals furtherGear in toolsets. which the The communication simulation and between rendering these is done programs by FlightGear. -

Openscenegraph 3.0 Beginner's Guide
OpenSceneGraph 3.0 Beginner's Guide Create high-performance virtual reality applications with OpenSceneGraph, one of the best 3D graphics engines Rui Wang Xuelei Qian BIRMINGHAM - MUMBAI OpenSceneGraph 3.0 Beginner's Guide Copyright © 2010 Packt Publishing All rights reserved. No part of this book may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, without the prior written permission of the publisher, except in the case of brief quotations embedded in critical articles or reviews. Every effort has been made in the preparation of this book to ensure the accuracy of the information presented. However, the information contained in this book is sold without warranty, either express or implied. Neither the authors, nor Packt Publishing and its dealers and distributors will be held liable for any damages caused or alleged to be caused directly or indirectly by this book. Packt Publishing has endeavored to provide trademark information about all of the companies and products mentioned in this book by the appropriate use of capitals. However, Packt Publishing cannot guarantee the accuracy of this information. First published: December 2010 Production Reference: 1081210 Published by Packt Publishing Ltd. 32 Lincoln Road Olton Birmingham, B27 6PA, UK. ISBN 978-1-849512-82-4 www.packtpub.com Cover Image by Ed Maclean ([email protected]) Credits Authors Editorial Team Leader Rui Wang Akshara Aware Xuelei Qian Project Team Leader Reviewers Lata Basantani Jean-Sébastien Guay Project Coordinator Cedric Pinson -

Certificate Authority – Registration Authority (Verifies Cert Requests) – Validation Authority (Handles Revocation)
11. Trust on the Web Blase Ur and David Cash February 5th, 2020 CMSC 23200 / 33250 Overview • Secure Sockets Layer (SSL) and its successor, Transport Layer Security (TLS) enable secure communication • Frequently encountered with web browsing (HTTPS) and more behind the scenes in app, VOIP, etc. What we want to defend against • People snooping on our communications – The contents of what we’re sending – Session tokens (see, e.g., Firesheep) • Person-in-the-middle attacks – We want to authenticate that we are talking to the right site, not an imposter – Use certificates inside a public-key infrastructure How we could obtain trust • Web of trust – People you already trust introduce you to people they trust – Can get complicated, doesn’t scale well – Infrequently seen in practice • Public-Key Infrastructure (PKI) – Certificates are issued by certificate authorities that bind cryptographic keys to identities Public-Key Infrastucture • Binding of keys to identities – Certificate authority – Registration authority (verifies cert requests) – Validation authority (handles revocation) Image from Wikimedia Foundation What does SSL look like to users? • Compare, e.g., the following: – https://www.google.com (normal certificate) – Go to Google images and then click on an image and see what happens (mixed content) – https://www.thawte.com (EV certificate) What does SSL look like to users? (From Felt et al. SOUPS 2016) How does PKI look to browsers? • Hundreds of trusted certificate authorities – Certificate authorities (CAs) sign the certificates binding -

Future Internet (FI) and Innovative Internet Technologies and Mobile Communication (IITM)
Chair of Network Architectures and Services Department of Informatics Technical University of Munich Proceedings of the Seminars Future Internet (FI) and Innovative Internet Technologies and Mobile Communication (IITM) Summer Semester 2018 26. 2. 2017 – 19. 8. 2018 Munich, Germany Editors Georg Carle, Daniel Raumer, Stephan Gunther,¨ Benedikt Jaeger Publisher Chair of Network Architectures and Services Network Architectures and Services NET 2018-11-1 Lehrstuhl für Netzarchitekturen und Netzdienste Fakultät für Informatik Technische Universität München Proceedings zu den Seminaren Future Internet (FI) und Innovative Internet-Technologien und Mobilkommunikation (IITM) Sommersemester 2018 München, 26. 2. 2017 – 19. 8. 2018 Editoren: Georg Carle, Daniel Raumer, Stephan Günther, Benedikt Jaeger Network Architectures and Services NET 2018-11-1 Proceedings of the Seminars Future Internet (FI) and Innovative Internet Technologies and Mobile Communication (IITM) Summer Semester 2018 Editors: Georg Carle Lehrstuhl für Netzarchitekturen und Netzdienste (I8) Technische Universität München 85748 Garching b. München, Germany E-mail: [email protected] Internet: https://net.in.tum.de/~carle/ Daniel Raumer Lehrstuhl für Netzarchitekturen und Netzdienste (I8) E-mail: [email protected] Internet: https://net.in.tum.de/~raumer/ Stephan Günther Lehrstuhl für Netzarchitekturen und Netzdienste (I8) E-mail: [email protected] Internet: https://net.in.tum.de/~guenther/ Benedikt Jaeger Lehrstuhl für Netzarchitekturen und Netzdienste (I8) E-mail: [email protected] Internet: https://net.in.tum.de/~jaeger/ Cataloging-in-Publication Data Seminars FI & IITM SS 18 Proceedings zu den Seminaren „Future Internet“ (FI) und „Innovative Internet-Technologien und Mobilkom- munikation“ (IITM) München, Germany, 26. 2. 2017 – 19. 8. -

Arthur Kindergarten 2001 User's Guide
Table of Contents Welcome! ......................................................................................................................2 System Requirements................................................................................................3 Installation Instructions............................................................................................4 The Options Screen....................................................................................................5 Windows...................................................................................................................5 Macintosh .................................................................................................................6 Getting Around the Program ...................................................................................7 Preferences Screen...................................................................................................8 Progress Checker.....................................................................................................9 Goal Checker..........................................................................................................10 Character Descriptions............................................................................................11 Playing Disc 1 Activities.........................................................................................15 Picture Windows...................................................................................................15