The Management Discipline of Database Administration: DBA Best Practices
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Aptum Database Administration Program September 2019 Overview
SERVICE GUIDE APTUM DATABASE ADMINISTRATION PROGRAM SEPTEMBER 2019 OVERVIEW Aptum’s Database Administration (DBA) Program was designed to DBA Plan hours can be leveraged for all database-related activities help our customers reduce the cost of normal operation and the risk of detailed within this document, up to the allocation purchased. If you application and database downtime. require more hours than are purchased in a plan for a given month, any excess will be billed on an hourly basis at the standard Database Customers can work with Aptum’s Solutions Engineers and Certified Administration rate. Database Administrators to obtain assistance with everything from database engine configuration, performance optimization, clustering Included Database Platforms: administration, and replication administration. Microsoft SQL Server To help you achieve your performance goals, we offer our DBA plans in MySQL/MariaDB/Percona block-hour increments: 4 hours* * Hours are monthly and renew at the 1st of each calendar month and do not roll over. Overage rates are applicable only after block hours are consumed. All hours are 8 hours* applicable to the entire solution not per server. 12 hours* 20 hours* THE NEED FOR DATABASE ADMINISTRATION Most applications—especially those that support enterprise processes enable e-commerce, or facilitate collaboration—are database-intensive and demand optimal performance from the database. Applications and database queries may utilize very lean and elegant code, but the structure and configuration of your databases can be a detriment to high performance. There are dozens, sometimes hundreds, of configuration settings that need to be optimally tuned to enhance database performance. When the database is installed, most configuration defaults are applied automatically. -

CSIT 1810 Introduction to Database Design
PELLISSIPPI STATE COMMUNITY COLLEGE MASTER SYLLABUS INTRODUCTION TO DATABASE DESIGN CSIT 1810 Class Hours: 3.0 Credit Hours: 4.0 Laboratory Hours: 3.0 Date Revised: Spring 2016 Catalog Course Description: A study of database management systems and their impact on information technology. Topics include database models, data modeling techniques, conceptual and physical design, storage techniques and data administration. Special emphasis will be placed on relational systems and application of query languages using relational operations. Entry Level Standards: The entering student should have a familiarity with the Windows environment. The student is expected to have moderate programming abilities in a high-level language or a scripting language. Problem solving skills will be essential. The student must have math, writing, verbal and English language skills at the college level. Prerequisites: CSIT 1110 or WEB 2010 Textbook(s) and Other Course Materials: Textbook: Database Systems: Design, Implementation and Management; (11th. Edition), by Coronel/Morris/Rob, Cengage, 2014, ISBN-13 978-1-285-19614-5, (Electronic Book at www.cengagebrain.com, ISBN-13 9781305323230.) Supplies: USB flash drive; ear buds or head phones for audio tutorials I. Week/Unit/Topic Basis: Week Chapter Topic 1 1 Database Systems 2 2 Database Models; Relational versus NoSQL databases 3 3 The Relational Database Model 4 9 Introduction to Systems & Database Design 5, 6 4, 5.1 Entity-Relationship Modeling 7 6 Normalization 8-10 7, SQL Queries, Creating Tables and Views in SQL 8.1,8.4 11 10 Transaction Management and Concurrency Control 12 12, 15 Distributed Systems, Database Management & Security 13 13 Business Intelligence & Data Warehouses 14 13 Big Data; final exam review 15 Final Exam II. -

Database Performance Study
Database Performance Study By Francois Charvet Ashish Pande Please do not copy, reproduce or distribute without the explicit consent of the authors. Table of Contents Part A: Findings and Conclusions…………p3 Scope and Methodology……………………………….p4 Database Performance - Background………………….p4 Factors…………………………………………………p5 Performance Monitoring………………………………p6 Solving Performance Issues…………………...............p7 Organizational aspects……………………...................p11 Training………………………………………………..p14 Type of database environments and normalizations…..p14 Part B: Interview Summaries………………p20 Appendices…………………………………...p44 Database Performance Study 2 Part A Findings and Conclusions Database Performance Study 3 Scope and Methodology The authors were contacted by a faculty member to conduct a research project for the IS Board at UMSL. While the original proposal would be to assist in SQL optimization and tuning at Company A1, the scope of such project would be very time-consuming and require specific expertise within the research team. The scope of the current project was therefore revised, and the new project would consist in determining the current standards and practices in the field of SQL and database optimization in a number of companies represented on the board. Conclusions would be based on a series of interviews with Database Administrators (DBA’s) from the different companies, and on current literature about the topic. The first meeting took place 6th February 2003, and interviews were held mainly throughout the spring Semester 2003. Results would be presented in a final paper, and a presentation would also be held at the end of the project. Individual summaries of the interviews conducted with the DBA’s are included in Part B. A representative set of questions used during the interviews is also included. -

(UCP) in a Tomcat Application Container Requires the Following Steps
Design and Deploy TomCat AppliCations for Planned, Unplanned Database Downtimes and Runtime Load BalanCing with UCP In OraCle Database RAC and Active Data Guard environments ORACLE WHITE PAPER NOVEMBER 2017 DESIGN AND DEPLOY TOMCAT SERVLETS FOR PLANNED AND UNPLANNED DATABASE DOWNTIME AND LOAD BALANCING WITH UCP Table of Contents IntroduCtion 3 Issues to be addressed 3 OraCle Database 12C High-Availability and Load BalanCing ConCepts 4 Configure TomCat for UCP 4 Create a New Database Resource 4 Create a JNDI lookup in the servlet 5 Create a web.xml for the servlet 6 Hiding Planned MaintenanCe from TomCat Servlets 6 Web Applications Steps 6 DBA or RDBMS Steps 7 Hiding Unplanned Database downtime from TomCat Servlets 9 Developer or Web Application Steps 9 DBA or RDBMS Steps 10 Application Continuity Checklist 10 Runtime Load BalanCing (RLB) with TomCat Servlets 12 Web AppliCation steps 12 Appendix 13 Enable JDBC & UCP logging for debugging 13 ConClusion 14 2 DESIGN AND DEPLOY TOMCAT SERVLETS FOR PLANNED AND UNPLANNED DATABASE DOWNTIME AND LOAD BALANCING WITH UCP IntroduCtion Achieving maximum appliCation uptime without interruptions is a CritiCal business requirement. There are a number of requirements such as outage detection, transparent planned maintenanCe, and work load balanCing that influenCe appliCation availability and performance. The purpose of this paper is to help Java Web applications deployed with ApaChe TomCat, achieve maximum availability and sCalability when using Oracle. Are you looking for best praCtiCes to hide your tomCat applications from database outages? Are you looking at, smooth & stress-free maintenanCes of your tomCat appliCations? Are you looking at leveraging Oracle Database’s runtime load balancing in your tomCat web appliCations? This paper Covers the configuration of your database and tomCat servlets for resilienCy to planned maintenanCe, unplanned database outages, and dynamic balancing of the workload across 1 database instances, using RAC, ADG, GDS , and UCP. -

Database Administration Maturity Model Version
This document is the intellectual property of TrueNorth Consulting, Inc., Copyright © 1996, 1998, 1999, all rights reserved. Database Administration Maturity Model Version 1.1 File: C:\tnc\dba\Tom's White Papers\DBAMM.doc Page 1 Author: Thomas B. Cox This document is the intellectual property of TrueNorth Consulting, Inc., Copyright © 1996, 1998, 1999, all rights reserved. Table of Contents LEVELS OF THE DBA MM (DATABASE ADMINISTRATION MATURITY MODEL)............................................................................3 DIFFERENCES BETWEEN DATA ADMINISTRATORS, DBAS, AND DATA ARCHITECTS...............................................3 QUALITATIVE DIFFERENCES BETWEEN TASK AREAS.............................................................................................................................4 Data Architecture .........................................................................................................................................................................4 Data Administration......................................................................................................................................................................4 Database Administration...............................................................................................................................................................4 DATABASE LIFE CYCLE.............................................................................................................................................................6 QUALITATIVE -
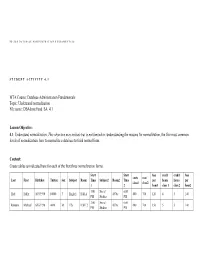
Database Administration Fundamentals Topic: Understand Normalization File Name: Dbadminfund SA 4.1
98-364 D ATABASE A DMINISTRATION F UNDAMENTALS STUDENT ACTIVITY 4.1 MTA Course: Database Administration Fundamentals Topic: Understand normalization File name: DBAdminFund_SA_4.1 Lesson Objective: 4.1: Understand normalization. This objective may include but is not limited to: understanding the reasons for normalization, the five most common levels of normalization, how to normalize a database to third normal form. Content: Create tables as indicated here for each of the first three normalization forms. Start Start fees credit credit fees costs cost Last First Birthday Tuition Sex Subject Room Time Subject2 Room2 Time per hours hours per class1 class2 1 2 hour1 class 1 class 2 hour2 1:00 Social 6:00 Holt Holly 10/5/1990 10000 F English Hall A 4576c 480 700 120 4 5 140 PM Studies PM 3:00 Social 6:00 Raheem Michael 6/18/1990 4000 M CIS Hall 12 4576c 600 700 150 5 5 140 PM Studies PM 98-364 D ATABASE A DMINISTRATION F UNDAMENTALS 3:00 Social 6:00 Raheem Michael 6/18/1990 4000 M CIS Hall 12 4576c 600 700 150 5 5 140 PM Studies PM Social 6:00 1:00 Jacobsen Lola 8/7/1997 9000 F 4576c English Hall A 700 480 140 5 4 120 Studies PM PM 1:00 4:00 Higa Sidney 11/21/2000 12000 F English Hall A Math 2354c 480 1404 120 4 6 234 PM PM 1:00 4:00 Johnson Brian 4/15/1989 500 M English Hall A Math 2354c 1404 1701 234 6 3 567 PM PM 3:00 Social 6:00 Raheem Michael 6/18/1990 4000 M CIS Hall 12 4576c 600 700 150 5 5 140 PM Studies PM 2:00 Social 6:00 Bentley Sean 2/17/1990 350 M Science Hall B 4576c 1701 700 567 3 5 140 PM Studies PM Social 6:00 3:00 Price Jeff 10/5/1990 2000 M 4576c CIS Hall 12 700 600 140 5 5 150 Studies PM PM 3:00 Social 6:00 Raheem Michael 6/18/1990 4000 M CIS Hall 12 4576c 600 700 150 5 5 140 PM Studies PM Social 6:00 3:00 Ashton Chris 1/1/1951 50 M 4576c CIS Hall 12 480 1404 120 4 6 234 Studies PM PM 98-364 D ATABASE A DMINISTRATION F UNDAMENTALS Use the First Normal Form (1NF) with the previous table. -

Planned/Unplanned Downtime and Runtime Load Balancing with UCP
Design and Deploy WebSphere Applications for Planned, Unplanned Database Downtimes and Runtime Load Balancing with UCP In Oracle Database RAC and Active Data Guard environments ORACLE WHITE PAPER AUGUST 2015 DESIGN AND DEPLOY WEBSPHERE SERVLETS FOR PLANNED AND UNPLANNED DATABASE DOWNTIME AND LOAD BALANCING WITH UCP Table of Contents Introduction 3 Issues to be addressed 3 Oracle Database 12c High-Availability and Load Balancing Concepts 4 Configure WebSphere for UCP 4 Create a New JDBC Provider 4 Create a New DataSource 8 Create a JNDI context in the servlet 19 Create a web.xml for the Servlet 20 WebSphere Tips 20 Hiding Planned Maintenance from WebSphere Applications 20 Developer or Web Applications Steps 21 DBA or RDBMS Steps 22 Hiding Unplanned Database Downtime from WebSphere applications 23 Developer or Web Application Steps 23 DBA or RDBMS Steps 24 Runtime Load Balancing (RLB) with WebSphere Servlets 24 Developer or Web Application steps 25 Appendix 26 Enable JDBC & UCP logging for debugging 26 Conclusion 27 DESIGN AND DEPLOY WEBSPHERE SERVLETS FOR PLANNED AND UNPLANNED DATABASE DOWNTIME AND LOAD BALANCING WITH UCP 2 Introduction Achieving maximum application uptime without interruptions is a critical business requirement. There are a number of requirements such as outage detection, transparent planned maintenance, and work load balancing that influence application availability and performance. The purpose of this paper is to help Java Web applications deployed with IBM WebSphere, achieve maximum availability and scalability when using Oracle. Are you looking for best practices to hide your web applications from database outages? Are you looking at, smooth & stress-free maintenances of your web applications? Are you looking at leveraging Oracle Database’s runtime load balancing in your WebSphere applications? This paper covers the configuration of your database and WebSphere Servlets for resiliency to planned, unplanned database outages and dynamic balancing of the workload across database instances, using RAC, ADG, GDS1, and UCP. -

Lead Database Support Technologist LOCATION
Office of Human Resources POSITION DESCRIPTION POSITION: Lead Database Support Technologist LOCATION: Information Technology REPORTS TO: Manager-Systems Development GRADE: PSA 14 WORK SCHEDULE: Non-Standard, 35 hours per week SUPERVISES: May exercise supervision over part-time and student employees. JOB SUMMARY: The Database Administrator (DBA) role is to design, install, monitor, maintain, and performance tune production, test/development, and QA database environments while ensuring high levels of data availability. This individual is also responsible for developing, implementing, and overseeing database policies and procedures to ensure the integrity and availability of all databases and their accompanying software. The DBA will design and implement redundant systems, policies and procedures for disaster recovery and data archiving to ensure effective protection and integrity of data assets, and will remain current with the latest technologies and industry/business trends. ESSENTIAL DUTIES AND RESPONSIBILITIES: Install, monitor, maintain and performance tune all Production, Test & Development databases including but not limited to Oracle and SQL server. Upgrade database management systems, including but not limited to Oracle and SQL server. Developing, implementing, and overseeing database policies and procedures to ensure the integrity and availability of Oracle databases and their accompanying software. Install and upgrade database applications by applying patches and upgrades on a regular schedule. Knight Campus 400 East Avenue, Warwick, RI 02886-1807 P: 401.825.2311 F: 401.825.2345 Provides technical support to application development teams. This is usually in the form of a help desk. The DBA is usually the point of contact for Oracle Support. Install, configure and upgrade server and database application components including but not limited to the portal platform, LDAP server, messaging server, calendar server, web server, payment gateway, internet based forms and self-service applications. -

Developing Database Applications
Developing Database Applications JBuilder® 2005 Borland Software Corporation 100 Enterprise Way Scotts Valley, California 95066-3249 www.borland.com Refer to the file deploy.html located in the redist directory of your JBuilder product for a complete list of files that you can distribute in accordance with the JBuilder License Statement and Limited Warranty. Borland Software Corporation may have patents and/or pending patent applications covering subject matter in this document. Please refer to the product CD or the About dialog box for the list of applicable patents. The furnishing of this document does not give you any license to these patents. COPYRIGHT © 1997–2004 Borland Software Corporation. All rights reserved. All Borland brand and product names are trademarks or registered trademarks of Borland Software Corporation in the United States and other countries. All other marks are the property of their respective owners. For third-party conditions and disclaimers, see the Release Notes on your JBuilder product CD. Printed in the U.S.A. JB2005database 10E13R0804 0405060708-987654321 PDF Contents Chapter 1 Chapter 4 Introduction 1 Connecting to a database 27 Chapter summaries . 2 Connecting to databases . 28 Database tutorials. 3 Adding a Database component to your Database samples . 3 application . 28 Related documentation . 4 Setting Database connection properties . 29 Documentation conventions . 6 Setting up JDataStore . 31 Developer support and resources. 7 Setting up InterBase and InterClient. 31 Contacting Borland Developer Support . 7 Using InterBase and InterClient with JBuilder . 32 Online resources. 7 Tips on using sample InterBase tables . 32 World Wide Web . 8 Adding a JDBC driver to JBuilder . -

Ddl) Lesson 1
LESSON 1 . 4 98-364 Database Administration Fundamentals Understand Data Definition Language (DDL) LESSON 1 . 4 98-364 Database Administration Fundamentals Lesson Overview 1.4 Understand data definition language (DDL) In this lesson, you will review: . DDL—DML relationship . DDL . Schema . CREATE . ALTER . DROP LESSON 1 . 4 98-364 Database Administration Fundamentals DDL—DML Relationship DML . Data Manipulation Language. (DML) In a database management system (DBMS), a language that is used to insert data in, update, and query a database. DMLs are often capable of performing mathematical and statistical calculations that facilitate generating reports. Acronym: DML. DML is used to manipulate the data of a database. In lesson review 1.3, you can find more details on DML. LESSON 1 . 4 98-364 Database Administration Fundamentals DDL . Data Definition Language (DDL) A language that defines all attributes and properties of a database, especially record layouts, field definitions, key fields, file locations, and storage strategy. Acronym: DDL. DDL is used to create the framework for the database, the schema of the database, or both. DDL works at the table level of the database. LESSON 1 . 4 98-364 Database Administration Fundamentals Schema . Schema A description of a database to a DBMS in the language provided by the DBMS. A schema defines aspects of the database, such as attributes (fields) and domains and parameters of the attributes. Schemas are generally defined as using commands from a DDL supported by the database system. LESSON 1 . 4 98-364 Database Administration Fundamentals CREATE . There are two forms of the CREATE statement. This statement creates a database called students. -

Sql Server Dba Responsibilities & Implications of Integration
▲ E-Guide SQL SERVER DBA RESPONSIBILITIES & IMPLICATIONS OF INTEGRATION SearchSQLServer SQL SERVER DBA RESPONSIBILITIES & IMPLICATIONS OF INTEGRATION Home Defining Half a Dozen Daily SQL Server DBA Responsibilities In-Memory SQL Server: The Implica- tions of Integration ATABASE MANAGEMENT” MAY sound like one “D responsibility to the uninitiated, but those who are more familiar know it’s just an umbrella term. Read on to explore six du- ties that are the building blocks of effective SQL Server administration. PAGE 2 OF 15 SPONSORED BY SQL SERVER DBA RESPONSIBILITIES & IMPLICATIONS OF INTEGRATION DEFINING HALF A DOZEN DAILY SQL SERVER DBA RESPONSIBILITIES Basit Farooq Home Defining Half a Dozen SQL Server database administration can be a complex and stressful job. Daily SQL Server DBA Responsibilities Database administrators’ responsibilities cover the performance, integrity and security of business data and SQL Server databases. To fulfill their duties In-Memory SQL Server: The Implica- and to make business data available to its users, database administrators have tions of Integration to perform routine DBA checks on their SQL Servers to monitor their status. So, what critical aspects of SQL Server should all DBAs include in their daily checklist? Here are six daily DBA responsibilities that every SQL Server manager should perform. PAGE 3 OF 15 SPONSORED BY SQL SERVER DBA RESPONSIBILITIES & IMPLICATIONS OF INTEGRATION VERIFY ALL SQL SERVER INSTANCES ARE UP Check the connectivity of each SQL Server on the network, and make sure all SQL Server instances are up. Ensure that all databases hosted on SQL Server instances are online. In addition to this, validate the storage of database data Home on the hard disk, which can be done by running the Database Consistency Defining Half a Dozen Checker (DBCC) CHECKDBcommand against each database on every SQL Daily SQL Server DBA Responsibilities Server instance. -

SQL Database Administrator
ORION COMMUNICATIONS, INC. Job Description JOB TITLE: SQL Database Administrator Reports To: Orion Operations Manager Exempt POSITION SUMMARY: The SQL Database Administration is responsible for the implementation, configuration, maintenance, and performance of critical SQL Server RDBMS systems, to ensure the availability and consistent performance of the Orion Workforce Management PLUS applications. This is a “hands-on” position requiring solid technical skills, as well as excellent interpersonal and communication skills. This position is responsible for the development and sustainment of the SQL Server Warehouse, ensuring its operational readiness (security, health and performance), executing data loads, and performing data modeling in support of multiple development teams. The data warehouse supports an enterprise application suite of program management tools. This position must be capable of working independently and collaboratively. POSITION ACTIVITIES Core duties and responsibilities include the following. Other duties may be assigned. • Manage SQL Server databases through multiple product lifecycle environments, from development to mission-critical production systems. • Configure and maintain database servers and processes, including monitoring of system health and performance, to ensure high levels of performance, availability, and security. • Apply data modeling techniques to ensure development and implementation support efforts meet integration and performance expectations • Independently analyze, solve, and correct issues in real time, providing problem resolution end-to-end. • Refine and automate regular processes, track issues, and document changes • Assist developers with complex query tuning and schema refinement. • Provide 24x7 support for critical production systems. • Perform scheduled maintenance and support release deployment activities after hours. • Share domain and technical expertise, providing technical mentorship and cross-training to other peers and team members.