Introduction to Programming in Python This Page Intentionally Left Blank Introduction to Programming in Python
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Programming Languages & Paradigms Abstraction & Modularity
Programming Languages & Paradigms PROP HT 2011 Abstraction & Modularity Lecture 6 Inheritance vs. delegation, method vs. message Beatrice Åkerblom [email protected] 2 Thursday, November 17, 11 Thursday, November 17, 11 Modularity Modularity, cont’d. • Modular Decomposability • Modular Understandability – helps in decomposing software problems into a small number of less – if it helps produce software in which a human reader can understand complex subproblems that are each module without having to know the others, or (at worst) by •connected by a simple structure examining only a few others •independent enough to let work proceed separately on each item • Modular Continuity • Modular Composability – a small change in the problem specification will trigger a change of – favours the production of software elements which may be freely just one module, or a small number of modules combined with each other to produce new systems, possibly in a new environment 3 4 Thursday, November 17, 11 Thursday, November 17, 11 Modularity, cont’d. Classes aren’t Enough • Modular Protection • Classes provide a good modular decomposition technique. – the effect of an error at run-time in a module will remain confined – They possess many of the qualities expected of reusable software to that module, or at worst will only propagate to a few neighbouring components: modules •they are homogenous, coherent modules •their interface may be clearly separated from their implementation according to information hiding •they may be precisely specified • But more is needed to fully achieve the goals of reusability and extendibility 5 6 Thursday, November 17, 11 Thursday, November 17, 11 Polymorphism Static Binding • Lets us wait with binding until runtime to achieve flexibility • Function call in C: – Binding is not type checking – Bound at compile-time – Allocate stack space • Parametric polymorphism – Push return address – Generics – Jump to function • Subtype polymorphism – E.g. -

15-122: Principles of Imperative Computation, Fall 2010 Assignment 6: Trees and Secret Codes
15-122: Principles of Imperative Computation, Fall 2010 Assignment 6: Trees and Secret Codes Karl Naden (kbn@cs) Out: Tuesday, March 22, 2010 Due (Written): Tuesday, March 29, 2011 (before lecture) Due (Programming): Tuesday, March 29, 2011 (11:59 pm) 1 Written: (25 points) The written portion of this week’s homework will give you some practice reasoning about variants of binary search trees. You can either type up your solutions or write them neatly by hand, and you should submit your work in class on the due date just before lecture begins. Please remember to staple your written homework before submission. 1.1 Heaps and BSTs Exercise 1 (3 pts). Draw a tree that matches each of the following descriptions. a) Draw a heap that is not a BST. b) Draw a BST that is not a heap. c) Draw a non-empty BST that is also a heap. 1.2 Binary Search Trees Refer to the binary search tree code posted on the course website for Lecture 17 if you need to remind yourself how BSTs work. Exercise 2 (4 pts). The height of a binary search tree (or any binary tree for that matter) is the number of levels it has. (An empty binary tree has height 0.) (a) Write a function bst height that returns the height of a binary search tree. You will need a wrapper function with the following specification: 1 int bst_height(bst B); This function should not be recursive, but it will require a helper function that will be recursive. See the BST code for examples of wrapper functions and recursive helper functions. -

Algorithms Documentation Release 1.0.0
algorithms Documentation Release 1.0.0 Nic Young April 14, 2018 Contents 1 Usage 3 2 Features 5 3 Installation: 7 4 Tests: 9 5 Contributing: 11 6 Table of Contents: 13 6.1 Algorithms................................................ 13 Python Module Index 31 i ii algorithms Documentation, Release 1.0.0 Algorithms is a library of algorithms and data structures implemented in Python. The main purpose of this library is to be an educational tool. You probably shouldn’t use these in production, instead, opting for the optimized versions of these algorithms that can be found else where. You should totally check out the docs for implementation details, complexities and further info. Contents 1 algorithms Documentation, Release 1.0.0 2 Contents CHAPTER 1 Usage If you want to use the algorithms in your code it is as simple as: from algorithms.sorting import bubble_sort my_list= bubble_sort.sort(my_list) 3 algorithms Documentation, Release 1.0.0 4 Chapter 1. Usage CHAPTER 2 Features • Pseudo code, algorithm complexities and futher info with each algorithm. • Test coverage for each algorithm and data structure. • Super sweet documentation. 5 algorithms Documentation, Release 1.0.0 6 Chapter 2. Features CHAPTER 3 Installation: Installation is as easy as: $ pip install algorithms 7 algorithms Documentation, Release 1.0.0 8 Chapter 3. Installation: CHAPTER 4 Tests: Pytest is used as the main test runner and all Unit Tests can be run with: $ ./run_tests.py 9 algorithms Documentation, Release 1.0.0 10 Chapter 4. Tests: CHAPTER 5 Contributing: Contributions are always welcome. Check out the contributing guidelines to get started. -

Concepts of Object-Oriented Programming AS 2019
Concepts of Object-Oriented Programming AS 2019 Exercise 6 Multiple Inheritance, Multiple Dispatch and Linearization November 1, 2019 Task 1 (from a previous exam) Consider the following C++ program: class X{ public: X(int p) : fx(p) {} int fx; }; class Y{ public: Y(int p) : fy(p) {} int fy; }; class B: public virtual X,public Y{ public: B(int p) : X(p-1),Y(p-2){} }; class C: public virtual X,public Y{ public: C(int p) : X(p+1),Y(p+1){} }; class D: public B, public C{ public: D(int p) : X(p-1), B(p-2), C(p+1){} }; int main() { D* d = new D(5); B* b = d; C* c = d; std::cout << b->fx << b->fy << c->fx << c->fy; return 0; } What is the output of running the program? (a) 5555 (b) 2177 (c) CORRECT: 4147 (d) 7177 (e) 7777 (f) None of the above Task 2 (from a previous exam) Consider the following Java classes: class A{ public void foo (Object o) { System.out.println("A"); } } class B{ public void foo (String o) { System.out.println("B"); } } class C extends A{ public void foo (String s) { System.out.println("C"); } } class D extends B{ public void foo (Object o) { System.out.println("D"); } } class Main { public static void main(String[] args) { A a = new C(); a.foo("Java"); C c = new C(); c.foo("Java"); B b = new D(); b.foo("Java"); D d = new D(); d.foo("Java"); } } What is the output of the execution of the method main in class Main? (a) The code will print A C B D (b) CORRECT: The code will print A C B B (c) The code will print C C B B (d) The code will print C C B D (e) None of the above Task 3 Consider the following C# classes: public class -

Safely Creating Correct Subclasses Without Superclass Code Clyde Dwain Ruby Iowa State University
Iowa State University Capstones, Theses and Retrospective Theses and Dissertations Dissertations 2006 Modular subclass verification: safely creating correct subclasses without superclass code Clyde Dwain Ruby Iowa State University Follow this and additional works at: https://lib.dr.iastate.edu/rtd Part of the Computer Sciences Commons Recommended Citation Ruby, Clyde Dwain, "Modular subclass verification: safely creating correct subclasses without superclass code " (2006). Retrospective Theses and Dissertations. 1877. https://lib.dr.iastate.edu/rtd/1877 This Dissertation is brought to you for free and open access by the Iowa State University Capstones, Theses and Dissertations at Iowa State University Digital Repository. It has been accepted for inclusion in Retrospective Theses and Dissertations by an authorized administrator of Iowa State University Digital Repository. For more information, please contact [email protected]. Modular subclass verification: Safely creating correct subclasses without superclass code by Clyde Dwain Ruby A dissertation submitted to the graduate faculty in partial fulfillment of the requirements for the degree of DOCTOR OF PHILOSOPHY Major: Computer Science Program of Study Committee Gary T. Leavens, Major Professor Samik Basu Clifford Bergman Shashi K. Gadia Jonathan D. H. Smith Iowa State University Ames, Iowa 2006 Copyright © Clyde Dwain Ruby, 2006. All rights reserved. UMI Number: 3243833 Copyright 2006 by Ruby, Clyde Dwain All rights reserved. UMI Microform 3243833 Copyright 2007 by ProQuest Information and Learning Company. All rights reserved. This microform edition is protected against unauthorized copying under Title 17, United States Code. ProQuest Information and Learning Company 300 North Zeeb Road P.O. Box 1346 Ann Arbor, MI 48106-1346 ii TABLE OF CONTENTS ACKNOWLEDGEMENTS . -

PML2: Integrated Program Verification in ML
PML2: Integrated Program Verification in ML Rodolphe Lepigre LAMA, CNRS, Université Savoie Mont Blanc, France and Inria, LSV, CNRS, Université Paris-Saclay, France [email protected] https://orcid.org/0000-0002-2849-5338 Abstract We present the PML2 language, which provides a uniform environment for programming, and for proving properties of programs in an ML-like setting. The language is Curry-style and call-by-value, it provides a control operator (interpreted in terms of classical logic), it supports general recursion and a very general form of (implicit, non-coercive) subtyping. In the system, equational properties of programs are expressed using two new type formers, and they are proved by constructing terminating programs. Although proofs rely heavily on equational reasoning, equalities are exclusively managed by the type-checker. This means that the user only has to choose which equality to use, and not where to use it, as is usually done in mathematical proofs. In the system, writing proofs mostly amounts to applying lemmas (possibly recursive function calls), and to perform case analyses (pattern matchings). 2012 ACM Subject Classification Software and its engineering → Software verification Keywords and phrases program verification, classical logic, ML-like language, termination check- ing, Curry-style quantification, implicit subtyping Digital Object Identifier 10.4230/LIPIcs.TYPES.2017.5 1 Introduction: joining programming and proving In the last thirty years, significant progress has been made in the application of type theory to computer languages. The Curry-Howard correspondence, which links the type systems of functional programming languages to mathematical logic, has been explored in two main directions. -

Safely Creating Correct Subclasses Without Seeing Superclass Code
Safely Creating Correct Subclasses without Seeing Superclass Code Clyde Ruby and Gary T. Leavens TR #00-05d April 2000, revised April, June, July 2000 Keywords: Downcalls, subclass, semantic fragile subclassing problem, subclassing contract, specification inheritance, method refinement, Java language, JML language. 1999 CR Categories: D.2.1 [Software Engineering] Requirements/Specifications — languages, tools, JML; D.2.2 [Software Engineering] Design Tools and Techniques — Object-oriented design methods, software libraries; D.2.3 [Software Engineering] Coding Tools and Techniques — Object-oriented programming; D.2.4 [Software Engineering] Software/Program Verification — Class invariants, correctness proofs, formal methods, programming by contract, reliability, tools, JML; D.2.7 [Software Engineering] Distribution, Maintenance, and Enhancement — Documentation, Restructuring, reverse engineering, and reengi- neering; D.2.13 [Software Engineering] Reusable Software — Reusable libraries; D.3.2 [Programming Languages] Language Classifications — Object-oriented langauges; D.3.3 [Programming Languages] Language Constructs and Features — classes and objects, frameworks, inheritance; F.3.1 [Logics and Meanings of Programs] Specifying and Verifying and Reasoning about Programs — Assertions, invariants, logics of programs, pre- and post-conditions, specification techniques; To appear in OOPSLA 2000, Minneapolis, Minnesota, October 2000. Copyright c 2000 ACM. Permission to make digital or hard copies of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for profit or commercial advantage and that copies bear this notice and the full citation on the first page. To copy otherwise, or republish, to post on servers or to redistribute to lists, requires prior specific permission and/or a fee. Department of Computer Science 226 Atanasoff Hall Iowa State University Ames, Iowa 50011-1040, USA Safely Creating Correct Subclasses without Seeing Superclass Code ∗ Clyde Ruby and Gary T. -
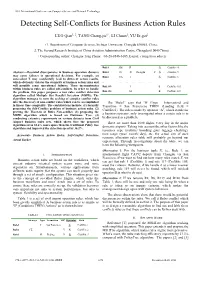
Detecting Self-Conflicts for Business Action Rules
2011 International Conference on Computer Science and Network Technology Detecting Self-Conflicts for Business Action Rules LUO Qian1, 2, TANG Chang-jie1+, LI Chuan1, YU Er-gai2 (1. Department of Computer Science, Sichuan University, Chengdu 610065, China; 2. The Second Research Institute of China Aviation Administration Centre, Chengdu 610041China) + Corresponding author: Changjie Tang Phone: +86-28-8546-6105, E-mail: [email protected] Rule4 FM D A CraftSite 4 Abstract—Essential discrepancies in business operation datasets Rule5 3U D Chengdu Y A CraftSite 5 may cause failures in operational decisions. For example, an Rule6 CA I A CraftSite 6 antecedent X may accidentally lead to different action results, which obviously violates the atomicity of business action rules and … … … … … … … will possibly cause operational failures. These inconsistencies Rule119 I B CraftSite 105 within business rules are called self-conflicts. In order to handle the problem, this paper proposes a fast rules conflict detection Rule120 M B CraftSite 229 algorithm called Multiple Slot Parallel Detection (MSPD). The algorithm manages to turn the seeking of complex conflict rules into the discovery of non-conflict rules which can be accomplished The “Rule1” says that “IF (Type = International and in linear time complexity. The contributions include: (1) formally Transition = San Francisco) THEN (Landing field = proposing the Self-Conflict problem of business action rules, (2) CraftSite1). The rule is made by operator “A", which stands for proving the Theorem of Rules Non-conflict, (3) proposing the MSPD algorithm which is based on Huffman- Tree, (4) a business operator, only investigated when a certain rule is to conducting extensive experiments on various datasets from Civil be discussed as a problem. -

A Survey on Teaching and Learning Recursive Programming
Informatics in Education, 2014, Vol. 13, No. 1, 87–119 87 © 2014 Vilnius University A Survey on Teaching and Learning Recursive Programming Christian RINDERKNECHT Department of Programming Languages and Compilers, Eötvös Loránd University Budapest, Hungary E-mail: [email protected] Received: July 2013 Abstract. We survey the literature about the teaching and learning of recursive programming. After a short history of the advent of recursion in programming languages and its adoption by programmers, we present curricular approaches to recursion, including a review of textbooks and some programming methodology, as well as the functional and imperative paradigms and the distinction between control flow vs. data flow. We follow the researchers in stating the problem with base cases, noting the similarity with induction in mathematics, making concrete analogies for recursion, using games, visualizations, animations, multimedia environments, intelligent tutor- ing systems and visual programming. We cover the usage in schools of the Logo programming language and the associated theoretical didactics, including a brief overview of the constructivist and constructionist theories of learning; we also sketch the learners’ mental models which have been identified so far, and non-classical remedial strategies, such as kinesthesis and syntonicity. We append an extensive and carefully collated bibliography, which we hope will facilitate new research. Key words: computer science education, didactics of programming, recursion, tail recursion, em- bedded recursion, iteration, loop, mental models. Foreword In this article, we survey how practitioners and educators have been teaching recursion, both as a concept and a programming technique, and how pupils have been learning it. After a brief historical account, we opt for a thematic presentation with cross-references, and we append an extensive bibliography which was very carefully collated. -

Programming-In-Scala.Pdf
Cover · Overview · Contents · Discuss · Suggest · Glossary · Index Programming in Scala Cover · Overview · Contents · Discuss · Suggest · Glossary · Index Programming in Scala Martin Odersky, Lex Spoon, Bill Venners artima ARTIMA PRESS MOUNTAIN VIEW,CALIFORNIA Cover · Overview · Contents · Discuss · Suggest · Glossary · Index iv Programming in Scala First Edition, Version 6 Martin Odersky is the creator of the Scala language and a professor at EPFL in Lausanne, Switzerland. Lex Spoon worked on Scala for two years as a post-doc with Martin Odersky. Bill Venners is president of Artima, Inc. Artima Press is an imprint of Artima, Inc. P.O. Box 390122, Mountain View, California 94039 Copyright © 2007, 2008 Martin Odersky, Lex Spoon, and Bill Venners. All rights reserved. First edition published as PrePrint™ eBook 2007 First edition published 2008 Produced in the United States of America 12 11 10 09 08 5 6 7 8 9 ISBN-10: 0-9815316-1-X ISBN-13: 978-0-9815316-1-8 No part of this publication may be reproduced, modified, distributed, stored in a retrieval system, republished, displayed, or performed, for commercial or noncommercial purposes or for compensation of any kind without prior written permission from Artima, Inc. All information and materials in this book are provided "as is" and without warranty of any kind. The term “Artima” and the Artima logo are trademarks or registered trademarks of Artima, Inc. All other company and/or product names may be trademarks or registered trademarks of their owners. Cover · Overview · Contents · Discuss · Suggest · Glossary · Index to Nastaran - M.O. to Fay - L.S. to Siew - B.V. -

Selective Open Recursion: a Solution to the Fragile Base Class Problem
Selective Open Recursion: A Solution to the Fragile Base Class Problem Jonathan Aldrich School of Computer Science Carnegie Mellon University 5000 Forbes Avenue Pittsburgh, PA 15213, USA [email protected] ABSTRACT public class CountingSet extends Set { private int count; Current object-oriented languages do not fully protect the implementation details of a class from its subclasses, mak- public void add(Object o) { ing it difficult to evolve that implementation without break- super.add(o); ing subclass code. Previous solutions to the so-called fragile count++; base class problem specify those implementation dependen- } cies, but do not hide implementation details in a way that al- public void addAll(Collection c) { lows effective software evolution. super.addAll(c); In this paper, we show that the fragile base class problem count += c.size(); arises because current object-oriented languages dispatch } methods using open recursion semantics even when these se- public int size() { mantics are not needed or wanted. Our solution is to make return count; explicit the methods to which open recursion should apply. } We propose to change the semantics of object-oriented dis- } patch, such that all calls to “open” methods are dispatched dynamically as usual, but calls to “non-open” methods are dispatched statically if called on the current object this, but Figure 1: The correctness of the CountingSet class de- dynamically if called on any other object. By specifying a pends on the independence of add and addAll in the im- method as open, a developer is promising that future ver- plementation of Set. If the implementation is changed sions of the class will make internal calls to that method in so that addAll uses add, then count will be incremented exactly the same way as the current implementation. -

Etude on Recursion Elimination by Program Manipulation and Problem Analysis
Etude on Recursion Elimination by Program Manipulation and Problem Analysis Nikolay V. Shilov Innopolis University Russia [email protected] Transformation-based program verification was a very important research topic in early years of theory of programming. Great computer scientists contributed to these studies: John McCarthy, Amir Pnueli, Donald Knuth ... Many fascinating examples were examined and resulted in recursion elimination techniques known as tail-recursion and as co-recursion. In the present paper we examine another (new we believe) example of recursion elimination via program manipulations and problem analysis. The recursion pattern of the study example matches neither tail-recursion nor co-recursion pattern. 1 Introduction 1.1 McCarthy 91 function Let us start with a short story [7] about the McCarthy 91 function M : N ! N, defined by John McCarthy1 as a test case for formal verification. The function is defined recursively as n − 10, if n > 100; M(n) = M(M(n + 11)), if n ≤ 100. The result of evaluating the function are given by n − 10, if n > 101; M(n) = (1) 91, if n ≤ 101. The function was introduced in papers published by Zohar Manna, Amir Pnueli and John McCarthy in 1970 [15, 16]. These papers represented early developments towards the application of formal methods to program verification. The function has a “complex” recursion pattern (contrasted with simple patterns, such as recurrence, tail-recursion or co-recursion). Nevertheless the McCarthy 91 function can be computed by an iterative algorithm/program. Really, let us consider an auxiliary recursive function Maux : N × N ! N 8 n m < , if = 0; Maux(n;m) = Maux(n − 10; m − 1), if n > 100 and m > 0; : Maux(n + 11; m + 1), if n < 100 and m > 0.