Formal Verification of Klibc with the WP Frama-C Plug-In
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

FUJITSU AI Zinrai Deep Learning System 200M/210H Software License Terms
FUJITSU AI Zinrai Deep Learning System 200M/210H Software License Terms Copyright 2021 FUJITSU LIMITED P3KD-1962-01EN 1. NVIDIA Product License Terms This product uses the following NVIDIA products. Name Version Tesla Driver for Linux x64 460.73.01 cuDNN 8.2.2 These NVIDIA products can be downloaded from the NVIDIA home page. http://www.nvidia.com/page/home.html Regarding the terms and conditions of the license for Tesla Driver for Linux x64 460.73.01, see "END USER LICENSE AGREEMENTS (EULA)" in the Appendix. Regarding the terms and conditions of the license for cuDNN 8.2.2, see "NVIDIA SOFTWARE LICENSE AGREEMENT" in the Appendix. 2. NGC Software This product contains the open source software ("OSS") as described in this document. The license terms for each OSS are as described below. • PyTorch 1.9.0 From PyTorch: Copyright (c) 2016- Facebook, Inc (Adam Paszke) Copyright (c) 2014- Facebook, Inc (Soumith Chintala) Copyright (c) 2011-2014 Idiap Research Institute (Ronan Collobert) Copyright (c) 2012-2014 Deepmind Technologies (Koray Kavukcuoglu) Copyright (c) 2011-2012 NEC Laboratories America (Koray Kavukcuoglu) Copyright (c) 2011-2013 NYU (Clement Farabet) Copyright (c) 2006-2010 NEC Laboratories America (Ronan Collobert, Leon Bottou, Iain Melvin, Jason Weston) Copyright (c) 2006 Idiap Research Institute (Samy Bengio) Copyright (c) 2001-2004 Idiap Research Institute (Ronan Collobert, Samy Bengio, Johnny Mariethoz) From Caffe2: Copyright (c) 2016-present, Facebook Inc. All rights reserved. All contributions by Facebook: Copyright (c) 2016 Facebook Inc. All contributions by Google: Copyright (c) 2015 Google Inc. All rights reserved. All contributions by Yangqing Jia: Copyright (c) 2015 Yangqing Jia All rights reserved. -

Embedded Linux Systems with the Yocto Project™
OPEN SOURCE SOFTWARE DEVELOPMENT SERIES Embedded Linux Systems with the Yocto Project" FREE SAMPLE CHAPTER SHARE WITH OTHERS �f, � � � � Embedded Linux Systems with the Yocto ProjectTM This page intentionally left blank Embedded Linux Systems with the Yocto ProjectTM Rudolf J. Streif Boston • Columbus • Indianapolis • New York • San Francisco • Amsterdam • Cape Town Dubai • London • Madrid • Milan • Munich • Paris • Montreal • Toronto • Delhi • Mexico City São Paulo • Sidney • Hong Kong • Seoul • Singapore • Taipei • Tokyo Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this book, and the publisher was aware of a trademark claim, the designations have been printed with initial capital letters or in all capitals. The author and publisher have taken care in the preparation of this book, but make no expressed or implied warranty of any kind and assume no responsibility for errors or omissions. No liability is assumed for incidental or consequential damages in connection with or arising out of the use of the information or programs contained herein. For information about buying this title in bulk quantities, or for special sales opportunities (which may include electronic versions; custom cover designs; and content particular to your business, training goals, marketing focus, or branding interests), please contact our corporate sales depart- ment at [email protected] or (800) 382-3419. For government sales inquiries, please contact [email protected]. For questions about sales outside the U.S., please contact [email protected]. Visit us on the Web: informit.com Cataloging-in-Publication Data is on file with the Library of Congress. -

Betrfs: a Right-Optimized Write-Optimized File System
BetrFS: A Right-Optimized Write-Optimized File System William Jannen, Jun Yuan, Yang Zhan, Amogh Akshintala, Stony Brook University; John Esmet, Tokutek Inc.; Yizheng Jiao, Ankur Mittal, Prashant Pandey, and Phaneendra Reddy, Stony Brook University; Leif Walsh, Tokutek Inc.; Michael Bender, Stony Brook University; Martin Farach-Colton, Rutgers University; Rob Johnson, Stony Brook University; Bradley C. Kuszmaul, Massachusetts Institute of Technology; Donald E. Porter, Stony Brook University https://www.usenix.org/conference/fast15/technical-sessions/presentation/jannen This paper is included in the Proceedings of the 13th USENIX Conference on File and Storage Technologies (FAST ’15). February 16–19, 2015 • Santa Clara, CA, USA ISBN 978-1-931971-201 Open access to the Proceedings of the 13th USENIX Conference on File and Storage Technologies is sponsored by USENIX BetrFS: A Right-Optimized Write-Optimized File System William Jannen, Jun Yuan, Yang Zhan, Amogh Akshintala, John Esmet∗, Yizheng Jiao, Ankur Mittal, Prashant Pandey, Phaneendra Reddy, Leif Walsh∗, Michael Bender, Martin Farach-Colton†, Rob Johnson, Bradley C. Kuszmaul‡, and Donald E. Porter Stony Brook University, ∗Tokutek Inc., †Rutgers University, and ‡Massachusetts Institute of Technology Abstract (microwrites). Examples include email delivery, creat- The Bε -tree File System, or BetrFS, (pronounced ing lock files for an editing application, making small “better eff ess”) is the first in-kernel file system to use a updates to a large file, or updating a file’s atime. The un- write-optimized index. Write optimized indexes (WOIs) derlying problem is that many standard data structures in are promising building blocks for storage systems be- the file-system designer’s toolbox optimize for one case cause of their potential to implement both microwrites at the expense of another. -

MC-1200 Series Linux Software User's Manual
MC-1200 Series Linux Software User’s Manual Version 1.0, November 2020 www.moxa.com/product © 2020 Moxa Inc. All rights reserved. MC-1200 Series Linux Software User’s Manual The software described in this manual is furnished under a license agreement and may be used only in accordance with the terms of that agreement. Copyright Notice © 2020 Moxa Inc. All rights reserved. Trademarks The MOXA logo is a registered trademark of Moxa Inc. All other trademarks or registered marks in this manual belong to their respective manufacturers. Disclaimer Information in this document is subject to change without notice and does not represent a commitment on the part of Moxa. Moxa provides this document as is, without warranty of any kind, either expressed or implied, including, but not limited to, its particular purpose. Moxa reserves the right to make improvements and/or changes to this manual, or to the products and/or the programs described in this manual, at any time. Information provided in this manual is intended to be accurate and reliable. However, Moxa assumes no responsibility for its use, or for any infringements on the rights of third parties that may result from its use. This product might include unintentional technical or typographical errors. Changes are periodically made to the information herein to correct such errors, and these changes are incorporated into new editions of the publication. Technical Support Contact Information www.moxa.com/support Moxa Americas Moxa China (Shanghai office) Toll-free: 1-888-669-2872 Toll-free: 800-820-5036 Tel: +1-714-528-6777 Tel: +86-21-5258-9955 Fax: +1-714-528-6778 Fax: +86-21-5258-5505 Moxa Europe Moxa Asia-Pacific Tel: +49-89-3 70 03 99-0 Tel: +886-2-8919-1230 Fax: +49-89-3 70 03 99-99 Fax: +886-2-8919-1231 Moxa India Tel: +91-80-4172-9088 Fax: +91-80-4132-1045 Table of Contents 1. -

Embedded Linux Training
Free Electrons Embedded Linux training Gregory Clement Thomas Petazzoni Michael Opdenacker Free Electrons. Kernel, drivers and embedded Linux development, consulting, training and support. http//free-electrons.com Rights to copy © Copyright 2004-2011, Free Electrons [email protected] Electronic version of this document available on http://free-electrons.com/doc/training/embedded-linux Updates will be available on http://free-electrons.com/doc/training/embedded-linux/ Attribution ± ShareAlike 3.0 Corrections, suggestions, You are free contributions and translations are welcome! to copy, distribute, display, and perform the work to make derivative works Latest update: Feb 14, 2011 to make commercial use of the work Under the following conditions Attribution. You must give the original author credit. Share Alike. If you alter, transform, or build upon this work, you may distribute the resulting work only under a license identical to this one. For any reuse or distribution, you must make clear to others the license terms of this work. Any of these conditions can be waived if you get permission from the copyright holder. Your fair use and other rights are in no way affected by the above. License text: http://creativecommons.org/licenses/by-sa/3.0/legalcode Free Electrons. Kernel, drivers and embedded Linux development, consulting, training and support. http//free-electrons.com Linux kernel Linux device drivers Free Electrons Board support code Our services Mainstreaming kernel code Kernel debugging Custom Development System integration -

Anatomy of Cross-Compilation Toolchains
Embedded Linux Conference Europe 2016 Anatomy of cross-compilation toolchains Thomas Petazzoni free electrons [email protected] Artwork and Photography by Jason Freeny free electrons - Embedded Linux, kernel, drivers - Development, consulting, training and support. http://free-electrons.com 1/1 Thomas Petazzoni I CTO and Embedded Linux engineer at Free Electrons I Embedded Linux specialists. I Development, consulting and training. I http://free-electrons.com I Contributions I Kernel support for the Marvell Armada ARM SoCs from Marvell I Major contributor to Buildroot, an open-source, simple and fast embedded Linux build system I Living in Toulouse, south west of France Drawing from Frank Tizzoni, at Kernel Recipes 2016 free electrons - Embedded Linux, kernel, drivers - Development, consulting, training and support. http://free-electrons.com 2/1 Disclaimer I I am not a toolchain developer. Not pretending to know everything about toolchains. I Experience gained from building simple toolchains in the context of Buildroot I Purpose of the talk is to give an introduction, not in-depth information. I Focused on simple gcc-based toolchains, and for a number of examples, on ARM specific details. I Will not cover advanced use cases, such as LTO, GRAPHITE optimizations, etc. I Will not cover LLVM free electrons - Embedded Linux, kernel, drivers - Development, consulting, training and support. http://free-electrons.com 3/1 What is a cross-compiling toolchain? I A set of tools that allows to build source code into binary code for -

Choosing System C Library
Choosing System C library Khem Raj Comcast Embedded Linux Conference Europe 2014 Düsseldorf Germany Introduction “God defined C standard library everything else is creation of man” Introduction • Standard library for C language • Provides primitives for OS service • Hosted/freestanding • String manipulations • Types • I/O • Memory • APIs Linux Implementations • GNU C library (glibc) • uClibc • eglibc – Now merged into glibc • Dietlibc • Klibc • Musl • bionic Multiple C library FAQs • Can I have multiple C libraries side by side ? • Can programs compiled with glibc run on uclibc or vice versa ? • Are they functional compatible ? • Do I need to choose one over other if I am doing real time Linux? • I have a baremetal application what libc options do I have ? Posix Compliance • Posix specifies more than ISO C • Varying degree of compliance What matters to you ? • Code Size • Functionality • Interoperability • Licensing • Backward Compatibility • Variety of architecture support • Dynamic Linking • Build system Codesize • Dietlibc/klibc – Used in really small setup e.g. initramfs • Bionic – Small linked into every process • uClibc – Configurable • Size can be really small at the expense of functionality • Eglibc – Has option groups can be ( < 1M ) License • Bionic – BSD/Apache-2.0 • Musl - MIT • Uclibc – LGPL-2.1 • Eglibc/Glibc – LGPL-2.1 Assigned to FSF • Dietlibc – GPLv2 • Klibc – GPLv2 • Newlib – some parts are GPLv3 Compliance • Musl strives for ISO/C and POSIX compliance No-mmu • uClibc supported No-mmu Distributions • Glibc is used in -

Embedded Linux Size Reduction Techniques
Embedded Linux Conference 2017 Embedded Linux size reduction techniques Michael Opdenacker free electrons [email protected] free electrons - Embedded Linux, kernel, drivers - Development, consulting, training and support. http://free-electrons.com 1/1 Michael Opdenacker I Michael Opdenacker I Founder and Embedded Linux engineer at free electrons I Embedded Linux expertise I Development, consulting and training I Strong open-source focus I Long time interest in embedded Linux boot time, and one of its prerequisites: small system size. I From Orange, France Penguin from Justin Ternet (https://openclipart.org/detail/182875/pinguin) free electrons - Embedded Linux, kernel, drivers - Development, consulting, training and support. http://free-electrons.com 2/1 Why reduce size? There are multiple reasons for having a small kernel and system I Run on very small systems (IoT) I Run Linux as a bootloader I Boot faster (for example on FPGAs) I Reduce power consumption Even conceivable to run the whole system in CPU internal RAM or cache (DRAM is power hungry and needs refreshing) I Security: reduce the attack surface I Cloud workloads: optimize instances for size and boot time. I Spare as much RAM as possible for applications and maximizing performance. See https://tiny.wiki.kernel.org/use_cases free electrons - Embedded Linux, kernel, drivers - Development, consulting, training and support. http://free-electrons.com 3/1 Reasons for this talk I No talk about size since ELCE 2015 I Some projects stalled (Linux tinification, LLVM Linux...) I Opportunity to have a look at solutions I didn’t try: musl library, Toybox, gcc LTO, new gcc versions, compiling with Clang.. -
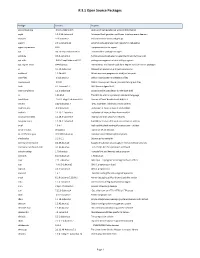
R 3.1 Open Source Packages
R 3.1 Open Source Packages Package Version Purpose accountsservice 0.6.15-2ubuntu9.3 query and manipulate user account information acpid 1:2.0.10-1ubuntu3 Advanced Configuration and Power Interface event daemon adduser 3.113ubuntu2 add and remove users and groups apport 2.0.1-0ubuntu12 automatically generate crash reports for debugging apport-symptoms 0.16 symptom scripts for apport apt 0.8.16~exp12ubuntu10.27 commandline package manager aptitude 0.6.6-1ubuntu1 Terminal-based package manager (terminal interface only) apt-utils 0.8.16~exp12ubuntu10.27 package managment related utility programs apt-xapian-index 0.44ubuntu5 maintenance and search tools for a Xapian index of Debian packages at 3.1.13-1ubuntu1 Delayed job execution and batch processing authbind 1.2.0build3 Allows non-root programs to bind() to low ports base-files 6.5ubuntu6.2 Debian base system miscellaneous files base-passwd 3.5.24 Debian base system master password and group files bash 4.2-2ubuntu2.6 GNU Bourne Again Shell bash-completion 1:1.3-1ubuntu8 programmable completion for the bash shell bc 1.06.95-2 The GNU bc arbitrary precision calculator language bind9-host 1:9.8.1.dfsg.P1-4ubuntu0.16 Version of 'host' bundled with BIND 9.X binutils 2.22-6ubuntu1.4 GNU assembler, linker and binary utilities bsdmainutils 8.2.3ubuntu1 collection of more utilities from FreeBSD bsdutils 1:2.20.1-1ubuntu3 collection of more utilities from FreeBSD busybox-initramfs 1:1.18.5-1ubuntu4 Standalone shell setup for initramfs busybox-static 1:1.18.5-1ubuntu4 Standalone rescue shell with tons of built-in utilities bzip2 1.0.6-1 High-quality block-sorting file compressor - utilities ca-certificates 20111211 Common CA certificates ca-certificates-java 20110912ubuntu6 Common CA certificates (JKS keystore) checkpolicy 2.1.0-1.1 SELinux policy compiler command-not-found 0.2.46ubuntu6 Suggest installation of packages in interactive bash sessions command-not-found-data 0.2.46ubuntu6 Set of data files for command-not-found. -

SECUMOBI SERVER Technical Description
SECUMOBI SERVER Technical Description Contents SIP Server 3 Media Relay 10 Dimensioning of the Hardware 18 SIP server 18 Media Proxy 18 Page 2 of 18 SIP Server Operatingsystem: Debian https://www.debian.org/ Application: openSIPS http://www.opensips.org/ OpenSIPS is built and installed from source code. The operating system is installed with the following packages: Package Description acpi displays information on ACPI devices acpi-support-base scripts for handling base ACPI events such as the power button acpid Advanced Configuration and Power Interface event daemon adduser add and remove users and groups anthy-common input method for Japanese - common files and dictionary apt Advanced front-end for dpkg apt -utils APT utility programs aptitude terminal-based package manager (terminal interface only) autopoint The autopoint program from GNU gettext backup -manager command -line backup tool base-files Debian base system miscellaneous files base-passwd Debian base system master password and group files bash The GNU Bourne Again SHell bc The GNU bc arbitrary precision calculator language binutils The GNU assembler, linker and binary utilities bison A parser generator that is compatible with YACC bsdmainutils collection of more utilities from FreeBSD bsdutils Basic utilities from 4.4BSD-Lite build -essential Informational list of build -essential packages busybox Tiny utilities for small and embedded systems bzip2 high-quality block-sorting file compressor - utilities ca-certificates Common CA certificates console-setup console font and keymap -

Workshop-Linux-Completo.Pdf
Linux embebido Workshop Linux Embebido Lucas Chiesa Joaquín de Andrés Germán Bassi Laboratorio Sistemas embebidos FIUBA Creative Commons BY-SA 3.0 license Basado en : http://free-electrons.com/docs/embedded-linux-intro ¿Sistema embebido? Un sistema embebido o empotrado es un sistema de computación diseñado para realizar una o algunas pocas funciones dedicadas frecuentemente en un sistema de computación en tiempo real. Los sistemas embebidos se utilizan para usos muy diferentes a los usos generales a los que se suelen someter a las computadoras personales. Wikipedia, http://es.wikipedia.org/wiki/Sistema_embebido SASE 2012 - Workshop Linux Embebido 2 Muchos sistemas diferentes Es una definición muy genérica: Cubre muchos tipos diferentes de sistemas Línea borrosa con sistemas tradicionales Productos ªConsumer Electronics (CE)º: Routers hogareños, reproductores de DVD, Televisores, cámaras digitales, GPS, celulares ... Productos industriales: Controladores de máquinas, alarmas, equipos de vigilancia, autos, satélites... SASE 2012 - Workshop Linux Embebido 3 Muchos productos diferentes SASE 2012 - Workshop Linux Embebido 4 Linux embebido El Software Libre y Abierto ofrece una rango muy amplio de herramientas para desarrollar sistemas embebidos. Ventajas ● Reutilizar componentes existentes para el sistema base. Permite concentrarse en el valor agregado del producto. ● Componentes de alta calidad y muy probados. (Kernel Linux , librerías de C ...) ● Control completo sobre la elección de componentes. Modificaciones posibles ilimitadas. ● Soporte por la comunidades: tutoriales, listas de correo... ● Bajo costo, sin licencias por unidad. ● Acceso más simple al software y a las herramientas. SASE 2012 - Workshop Linux Embebido 5 Ejemplos de dispositivos GPS: TomTom y Garmin Routers hogareños: Linksys, Netgear PDA: Zaurus, Nokia N8x0 TVs, DVDs: Sony, Philips, .. -

Embedded Open-Source Linux Development
Embedded Open-Source Linux Development Overview Going Embedded • Embedded is not Desktop! – To achieve the goals of embedded systems, you can give up many parts of a multipurpose desktop or server-based system • Smaller is better ≠ – Do not include everything – Embedded systems have space constraints – Embedded systems have cost constraints – Every embedded system has unique hardware • Single fixed purpose – Configuration is done by the developer and/or manufacturer Open Source Linux - 2 Dec. 7. 2012 Open-Source Software • Source code is always available! • Designing products with Linux and other open-source software does not mean you have to make your software open source. The use of loadable modules and LGPL libraries protects your intellectual property Open Source Linux - 3 Dec. 7. 2012 Goal • Enhance your experience in the customization of a System on Chip (SoC) design with an embedded operating system – Linux – by using the Xilinx tool capabilities Open Source Linux - 4 Dec. 7. 2012 Linux Distributions • Workstation Distributions – Debian – Ubuntu – Red Hat Linux – Suse – Others • Embedded Distributions – LynuxWorks – Wind River – MontaVista – Others Open Source Linux - 5 Dec. 7. 2012 What is Linux? • Here, “Linux” is the kernel Graphical Application Application X Server (xorg) Command line tools (cp, mv, tar, …) Kernel Interface (System Call) Distribution Linux Kernel Kernel Subsystems Driver Open Source Linux - 6 Dec. 7. 2012 Benefits of Linux • Memory Manager • Filesystem • Networking Support (TCP/IP Stack, ARP, ...) • Protected Memory • Peripheral Support • Application Support • Scalability (from embedded to clusters) Open Source Linux - 7 Dec. 7. 2012 Drawbacks of Linux • Large Resource Requirements – External memory needed • Compulsory Filesystem – A complete filesystem can be an overkill for a small application Open Source Linux - 8 Dec.