A Dynamic Spectrum Access Framework (Bring Your Own Spectrum)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Research Journal of Computer Science and Engineering
Implementation of Local Area Network (LAN) & Build a Secure LAN System for BAEC Head Quarter DOI: https://doi.org/10.36811/rjcse.2021.110003 RJCSE: June: 2021: Page No: 01-15 Research Journal of Computer Science and Engineering Review Article Open Access Implementation of Local Area Network (LAN) & Build a Secure LAN System for BAEC Head Quarter Osman Goni1* and Md. Abu Shameem2 1Engineer, Computer System and Network Division (CSND), Institute of Computer Science (ICS), Bangladesh Atomic Energy Commission, E-12/A, Agargaon, Sher-e-Bangla Nagar, Dhaka-1207, Bangladesh 2Principal Engineer, Computer System and Network Division (CSND), Institute of Computer Science (ICS), Bangladesh Atomic Energy Commission, E-12/A, Agargaon, Sher-e-Bangla Nagar, Dhaka- 1207, Bangladesh *Corresponding Author: Osman Goni, Engineer, Computer System and Network Division (CSND), Institute of Computer Science (ICS), Bangladesh Atomic Energy Commission, E-12/A, Agargaon, Sher-e-Bangla Nagar, Dhaka-1207, Bangladesh Received Date: Apr 03, 2021 / Accepted Date: May 15, 2021/ Published Date: Jun 05, 2021 Abstract Network security is the process of taking physical and software preventative measures to protect the underlying networking infrastructure from unauthorized access, misuse, malfunction, modification, destruction, or improper disclosure, thereby creating a secure platform for computers, users, and programs to perform their permitted critical functions within a secure environment. A local area network (LAN) is a computer network within a small geographical area such as a home, school, computer laboratory, office building or group of buildings. A LAN is composed of inter-connected workstations and personal computers which are each capable of accessing and sharing data and devices, such as printers, scanners and data storage devices, anywhere on the LAN. -

Invitation of Offer
Bangladesh Telecommunications Company Limited (BTCL) Telejogajog Bhaban 37/E Easkaton Garden, Dhaka-1000 Request for Quotation (RFQ) for International Internet Bandwidth through SEA-ME-WE5 submarine cable system for the operation of BTCL’s Internet service. October 2019 Page 1 of 15 1.1.1 Introduction Bangladesh Telecommunications Company Limited (BTCL) is a leading telecommunication service provider in Bangladesh. It is providing Telecommunication services e.g. Basic Telephony, Internet, Domestic L2 and L3 VPN Service etc. In order to facilitate more bandwidth to the Internet users, BTCL intends to expand its Internet Bandwidth capacity through SEA-ME-WE-5 (SMW5) Submarine Cable System. In view of this, BTCL invites offer from the International IP bandwidth providers through SMW5. 2.1.1 a) Eligibility of the bidder 2.1. The Bidder shall be an IP bandwidth provider licensed in the country where the offered IP node is located. 2.2. The Bidder must not have been declared bankrupt or filed for bankruptcy in any country. 2.3. The Bidder’s offered IP node shall have sufficient uplink bandwidth capacity with at least other Five (05) Tier-1 Internet backbones with minimum 2Tbps capacity at Asia pacific region. 2.4. The bidder’s must have minimum 50 person own manpower in their Singapore network team. 2.5. The bidder’s must have 24/7 NOC with sufficient manpower in Singapore. 2.6. The bidder’s IP Transit equipment must be in their own standard data center in Singapore. 2.7. The bidder’s must have own manpower in Bangladesh. Bidder must provide license/declaration/documentations as a proof of above requirements. -
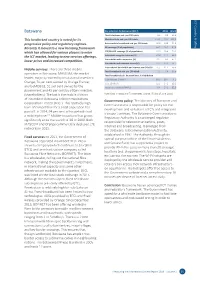
Botswana Key Indicators for Botswana (2017) Africa World Fixed-Telephone Sub
ICT Country Profiles Botswana Key indicators for Botswana (2017) Africa World Fixed-telephone sub. per 100 inhab. 6�2 0�9 13�0 This landlocked country is noted for its Mobile-cellular sub. per 100 inhab. 141�4 74�4 103�6 progressive policy and regulatory regimes. Active mobile-broadband sub. per 100 inhab. 66�9 24�8 61�9 Recently it moved to a new licensing framework 3G coverage (% of population) 84�0 62�7 87�9 which has allowed for various players to enter LTE/WiMAX coverage (% of population) 65�0 28�4 76�3 the ICT market, leading to new services offerings, Individuals using the Internet (%) 41.4 22�1 48�6 lower prices and increased competition. Households with a computer (%) 31.2 8�9 47�1 Households with Internet access (%) 45.7 19�4 54�7 International bandwidth per Internet user (kbit/s) 26�5 11�2 76�6 Mobile services: There are three mobile Fixed-broadband sub. per 100 inhab. 2�1 0�6 13�6 operators in Botswana: MASCOM, the market Fixed-broadband sub. by speed tiers, % distribution leader, majority-owned by institutional investors; -256 kbit/s to 2 Mbit/s 84�0 38�7 4�2 Orange, 74 per cent owned by Orange France; -2 to 10 Mbit/s 15�5 37�2 13�2 and beMOBILE, 51 per cent owned by the -equal to or above 10 Mbit/s 0�4 24�1 82�6 government and 45 per cent by citizen investors (shareholders). The last is the mobile division Note: Data in italics are ITU estimates. -

Annual Report: 2015-16
Annual Report: 2015-16 Bangladesh Telecommunications Company Limited www.btcl.com.bd Annual Report 2015-2016 1 Annual Report Committee: Sarker Md Zabed Robbani, Board Secretary, BTCL Mir Mohammed Morshed, Director, Public Relations and Printing, BTCL Mamlukar Rahman, Deputy Director (Telegraphs), BTCL Published by: BTCL Head Office 37/E Eskaton Garden, Dhaka-1000 Bangladesh Date of Publication: 20 Feb 2017 Tuesday Note: Only Softcopy Published Annual Report 2015-2016 Our Vision Our vision is to turn BTCL into a vibrant dynamic organization and lead the country's telecommunication sector by establishing a sound and cost-effective telecommunication infrastructure. Our Mission We strive to provide telecommunication services to the nation with the state-of-art telecommunication technology at an affordable cost without compromising quality. To deliver customers with enhanced values, the following steps are being implemented: . Improve quality of customer services; . Meet the demand of telephone connections and develop proper infrastructure; . Increase institutional efficiency; . Adopt marketing principles and practices; . Employ modern network planning; . Augment revenue management. Our objective To engage in the business of telecommunication by way of acquiring operation, management, improvements, installations, sales and re- sales of both local and long distance telecommunication services. To undertake programs pertaining to the creation and operation of other services including data network delivery and other newly invented telephone -

Ffircl Ffi{ I, Ryflrry'tr{I?Lr# Bangladesh Telecommunications Company Limited (BTCL) Tst",.3 Sr T E=,,L?!?I Ff Tfiin, -,, O O O
'/' ffircL ffi{ i, ryflrry'tr{i?lr# Bangladesh Telecommunications Company Limited (BTCL) tSt",.3 sr t E=,,l?!?i ff tfiin, -,, o o o Request for Proposal (RFP) for lnternational lP Bandwidth through SEA-M E-WE5 submarine cable system for the operation of BTCL's International Gateway (lGW) service. ., {* [email protected]'*+-> .', ,: * Tl€r-1 lSP Netowrk Z X ST[1-1 Conn€divity BTCl- lletwoft lntemet floud through W!V5 *Ps @ I \t>l -r -9n3- o ( I April2021 Page 1 of L7 r v 1. Introduction Bangladesh Telecommunications Company Limited (BTCL) is a leading telecommunication seruice provider in Bangladesh, It is providing all kinds of Telecommunication seruices e.g, Domestic and International Telephony seruice, Data Communication, Leased Line Internet, VPN, ADSL, GPON, Broadband Internet service etc. In order to facilitate more international voice calls through its IGWs, BTCL intends to expand its IGW's Bandwidth capacity through SEA-ME-WE-S (SMWS) Submarine Cable System. With this in view, BTCL invites offer from the International IP bandwidth providers through SMWS. 2. Eligibility requirement of the bidder 2.1, The Bidder shall be an IP bandwidth provider licensed in the country where the offered IP node is located. 2.2. The Bidder must not have been declared bankrupt or filed for bankruptcy in any country. 2.3. The Bidder's offered IP node shall have sufficient uplink bandwidth capacity with at least other three (03) Tier-1 Internet backbones. 3. Service requirement for this proposal 3.1.To expand the Internet bandwidth capacity through SMW5 cable system, BTCL intends to procure IP bandwidth through one of the closest Cable Landing Stations (CLS) situated in either the eastern side of the Bangladesh branch cable (i.e. -

Bangladesh Key Indicators for Bangladesh (2017) World Pacific Fixed-Telephone Sub
Asia & Bangladesh Key indicators for Bangladesh (2017) World Pacific Fixed-telephone sub. per 100 inhab. 0�4 9�5 13�0 Bangladesh has achieved widespread Mobile-cellular sub. per 100 inhab. 88�1 104�0 103�6 telecommunications coverage through wireless Active mobile-broadband sub. per 100 inhab. 30�0 60�3 61�9 solutions and is now moving towards greater 3G coverage (% of population) 92�6 91�3 87�9 mobile-broadband coverage. LTE/WiMAX coverage (% of population) 65�0 86�9 76�3 Individuals using the Internet (%) 18.0 44�3 48�6 Mobile services: There are five mobile operators, Households with a computer (%) 11.1 38�9 47�1 the top three controls 90 per cent of the market. Households with Internet access (%) 19.4 49�0 54�7 GRAMEENPHONE, a subsidiary of the Telenor International bandwidth per Internet user (kbit/s) 15�3 61�7 76�6 Norwegian mobile group, is the largest. The other Fixed-broadband sub. per 100 inhab. 4�4 13�0 13�6 two are BANGLALINK a subsidiary of the Global Fixed-broadband sub. by speed tiers, % distribution Telecom Holding and ROBI, a subsidiary of the -256 kbit/s to 2 Mbit/s 15�0 2�4 4�2 Malaysian mobile group AXIATA. Currently, the -2 to 10 Mbit/s 65�0 7�6 13�2 2G population coverage is more than 99 per cent. -equal to or above 10 Mbit/s 20�0 90�0 82�6 Mobile broadband using 3G technologies was deployed in 2013 and with government active Note: Data in italics are ITU estimates. -

Telecom History in the Region
Contents BTCL’s Vision/ Mission/ Objective Company Profile/ Historical Background Organogram: BTCL/ BTTB Managing Directors (2013-14) Nationwide Telecommunication Backbone: Map of Optical Fiber Network Directors’ Report Background, Objective, Board of Directors, Meetings, Management & Manpower, Licenses as Operator, Services, technical Data, Transmission backbone, IP & Data Network, Projects, Other Development Works, Income Statement, Directors, Auditors, Conclusion. Financial Statement (2013-14), audited by Hoda Vasi Chowdhury & Co, Chartered Accountants Responsibility of Management & Auditors, Qualified opinion, Matters affecting net loss/ account balance, Statements of Financial Position, Comprehensive Income, Changes in Equity, Cash Flows, Notes of Financial Statements, Notes to the Financial Statement, Introduction & Objective, Accounting Policies, Property-Plant & Equipment, Capital Work, Stores, Receivables, Advances, Cash, Security Deposit, Payables, VAT & Taxes, Expenses, Share, Equity, Loans, Employees, Assets, Revenue, Cost of Services, BTRC Fees, Administrative Expenses, Maintenance, Non-Operative Income, Number of Employees. Photo Gallery Telecom History in the Region Our Vision Our vision is to turn BTCL into a vibrant dynamic organization and lead the country’s telecommunication sector by establishing a sound and cost-effective infrastructure. Our Mission We strive to provide telecommunication services to the nation with the state-of-the-art technology at an affordable cost without compromising the quality. To deliver customers -

Attachment-1 SECTION 7: Technical Specification
Attachment-1 SECTION 7: Technical Specification "Supply, Installation, Testing and Commissioning of NFV Enabled IP Based ANS Gateway-2 Exchange in Bangladesh on Turn-Key Basis” Page 1 of 185 BTCL ANS “Supply, Installation, Testing and Commissioning of NFV Enable IP based ANS Gateway-2 Exchange in Bangladesh on Turn Key Basis” Table of Contents Attachment-1 ................................................................................................................................... 1 Section 7: Technical Specification ................................................................................................. 1 Sub-Section 1: Tender In Brief ........................................................................................................ 3 Sub-Section 2: Scope Of The Work ................................................................................................. 5 Sub-Section 3 : General Requiremnet Of Nfv Enabled Ip Based Ans Gateway-2 ........................ 17 Sub-Section 4 : Nfv And Cloud Requirement For Ans Gateway-2 ............................................... 19 Sub-Section 5:Environments And Other Requirements ................................................................ 25 Sub-Section 6: Requirement Of Media Gateway Controller And Signalling Functions ............... 27 Sub-Section 7: Requirements Of Media Gateway ......................................................................... 30 Sub-Section 8: Requirements Of Gateway Router, Lan Switch, Firewall, Session Border Controller And Intrusion -

BANGLADESH a CASESTUDY OFBTCLNETWORK Telecommunication Development Sector DECEMBER 2011 Report INFRASTRUCTURE
INFRASTRUCTURE International Telecommunication Union Telecommunication Development Bureau Place des Nations CH-1211 Geneva 20 NGN ACCESS NETWORK PLANNING: Switzerland A CASE STUDY OF BTCL NETWORK www.itu.int IN BANGLADESH Report DECEMBER 2011 Printed in Switzerland Telecommunication Development Sector Geneva, 2011 12/2011 NGN Access Network Planning: A Case Study of BTCL Network in Bangladesh December 2011 This report was prepared by ITU expert Mr Oscar González Soto. The International Telecommunication Union (ITU) would like to express sincere gratitude to the Bangladesh Telecommunications Company Limited (BTCL), the Ministry of Post and Telecommunications (MOPT), the Bangladesh Telecommunication Regulatory Commission (BTRC) for their support and assistance to the project realization, as well as to individual staff in those organizations in particular, for their support, information gathering to fulfil the objectives and challenges of this study. The designations employed and the presentation of material, including maps, do not imply the expression of any opinion whatsoever on the part of ITU concerning the legal status of any country, territory, city or area, or concerning the delimitations of its frontiers or boundaries. The mention of specific companies or of certain products does not imply that they are endorsed or recommended by ITU in preference to others of a similar nature that are not mentioned. This report has not been subjected to editorial revision Please consider the environment before printing this report. ITU 2011 All rights reserved. No part of this publication may be reproduced, by any means whatsoever, without the prior written permission of ITU. NGN Access Network Planning: A Case Study of BTCL Network in Bangladesh Table of Contents Page 1 Executive Summary ............................................................................................................ -
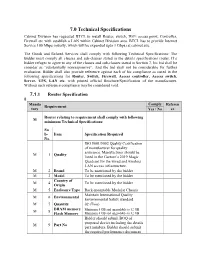
7.0 Technical Specifications
7.0 Technical Specifications Cabinet Division has requested BTCL to install Router, switch, WiFi access point, Controller, Firewall etc with establish a LAN within Cabinet Division area. BTCL has to provide Internet Service 100 Mbps initially, which will be expanded upto 1 Gbps) at cabinet site. The Goods and Related Services shall comply with following Technical Specifications: The Bidder must comply all clauses and sub-clauses stated in the details specifications router. If a bidder refuges to agree to any of the clauses and sub-clauses stated in Section 7, his bid shall be consider as “substantially nonresponsive”. And the bid shall not be considerable for further evaluation. Bidder shall also provide reference against each of his compliance as stated in the following specifications for Router, Switch, Firewall, Access controller, Access switch, Server, UPS, LAN etc. with printed official Brochure/Specification of the manufacturer. Without such reference compliance may be considered void. 7.1 .1 Router Specification 8 Manda Comply Referen Requirement tory Yes / No ce Router relating to requirement shall comply with following M minimum Technical Specifications: Su b- Item Specification Required No. ISO 9001/9002 Quality Certification of manufacturer for quality assurance. Manufacturer should be M 1 Quality listed in the Gartner’s 2019 Magic Quadrant for the wired and wireless LAN access infrastructure. M 2 Brand To be mentioned by the bidder M 3 Model To be mentioned by the bidder Country of M 4 To be mentioned by the bidder Origin M 5 Enclosure Type Rack-mountable Modular Chassis Maintain International Quality M 6 Environmental Environmental Safety standard M 7 Quantity 02 (Two) DRAM memory M 8 Minimum 8 GB and upgradable to 32 GB Flash Memory Minimum 8 GB and upgradable to 32 GB Bidder should submit BOQ of proposed device including the details M 9 Part No part numbers. -

THE FUTURE of DIGITAL in BANGLADESH | 1 Digital Readiness Assessment
THE FUTURE OF DIGITAL IN BANGLADESH | 1 Digital Readiness Assessment 2 | THE FUTURE OF DIGITAL IN BANGLADESH THE FUTURE OF DIGITAL IN BANGLADESH DIGITAL READINESS ASSESSMENT A report by BRAC Institute of Governance and Development (BIGD) in partnership with the Digital Pathways at Oxford THE FUTURE OF DIGITAL IN BANGLADESH | 3 Digital Readiness Assessment Digital Readiness Assessment: The Future of Digital in Bangladesh Publishing Year: 2021 Currently, in Bangladesh, we have been experiencing that the different pockets of production are being revolutionized by new technology – we are anticipating progress, but certainly not overnight. The challenges being there, we believe that the overall impact of new technologies will be determined by how they are adopted, the extent to which they are adopted profitably, and how indirect impacts filter through the rest of the economy. Partnering with the University of Oxford’s Digital Pathways Initiative, BRAC Institute of Governance and Development (BIGD) intends to chart a pathway for Bangladesh to decide holistic strategies to accelerate its inclusive growth in the digital age through this project. This work involves assessing the country’s current digital readiness, deciding priorities through dialogue with high-level stakeholders, and finally crafting a strategy primer. This report is the first major deliverable of the project. Research Team Dr. Zulkarin Jahangir, Research Fellow, BIGD, BRAC University Abdullah Hasan Safir, Senior Research Associate, BIGD, BRAC University Shamael Ahmed, Research -

Comparative Study of ICX Business with Prosperity and Significance in Bangladesh
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by International Institute for Science, Technology and Education (IISTE): E-Journals European Journal of Business and Management www.iiste.org ISSN 2222-1905 (Paper) ISSN 2222-2839 (Online) Vol.10, No.32, 2018 Comparative Study of ICX Business with Prosperity and Significance in Bangladesh K. M. Salah Uddin Shoyeb Haider Associate Professor, Department of Management Information Systems, Faculty of Business Studies, University of Dhaka, Dhaka-1000, Bangladesh Abstract The objective of this paper is to focus on the comparative discussion of ICX (Interconnection Exchange) business in with prosperity and significance in Bangladesh. ICX is a step towards creation of a modern and efficient telecommunications infrastructure. With the introduction of ICX, operators can combine their services in the most flexible way. Telecommunication sector is one of the most growing fields of business in Bangladesh. Government is earning a lot from this sector. Before introducing ICX government could not able to trace the exact number of calls and generated minutes, as well as they were in lack of exact revenue from those operators. After that, when Government introduced license to ICX operators, the scenario has been changed and single point of connectivity was established. As a result, interconnection capacity and the quality of voice call both have been developed. Government became capable of having accurate amount interconnections calls and minutes.Now days ICX operators are capable to handle voice calls using 2G and 3G technology. ICX operators are also connected to all the IGW (International gateway) operators to connect international calls with nationwide telecommunication operators.