Fedora 10 Installation Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Implementation of a Linux Kernel Module to Stress Test Memory Subsystems in X86 Architecture
Robert Taylor Implementation of a Linux Kernel Module to Stress Test Memory Subsystems in x86 Architecture Helsinki Metropolia University of Applied Sciences Bachelor of Engineering Information Technology 27th February 2011 Abstract Author(s) Robert Taylor Title Implementation of a Linux Kernel Module to Stress Test Memory Subsystems in x86 Architecture Number of Pages 36 pages Date 27 February 2011 Degree Bachelor of Engineering Degree Programme Information Technology Specialisation option Software Engineering Antti Piironen, Dr (Project Supervisor) Instructors Janne Kilpelainen (Hardware Supervisor, NSN) Antti Virtaniemi (Software Supervisor, NSN) The aim of the project was to implement software which would stress test the memory subsystem of x86 based hardware for Nokia Siemens Networks (NSN). The software was to be used in the validation process of memory components during hardware develop- ment. NSN used a number of software tools during this process. However, none met all their requirements and a custom piece of software was required. NSN produced a detailed requirements specification which formed the basis of the project. The requirements left the implementation method open to the developer. After analysing the requirements document, a feasibility study was undertaken to determine the most fitting method of implementation. The feasibility study involved detailed discussions with senior engineers and architects within both the hardware and software fields at NSN. The study concluded that a Linux kernel module met the criteria best. The software was successfully implemented as a kernel module and met the majority of the requirements set by NSN. The software is currently in use at NSN and is being actively updated and maintained. -
Backbox Penetration Testing Never Looked So Lovely
DISTROHOPPER DISTROHOPPER Our pick of the latest releases will whet your appetite for new Linux distributions. Picaros Diego Linux for children. here are a few distributions aimed at children: Doudou springs to mind, Tand there’s also Sugar on a Stick. Both of these are based on the idea that you need to protect children from the complexities of the computer (and protect the computer from the children). Picaros Diego is different. There’s nothing stripped- down or shielded from view. Instead, it’s a normal Linux distro with a brighter, more kid-friendly interface. The desktop wallpaper perhaps best We were too busy playing Secret Mario on Picaros Diego to write a witty or interesting caption. exemplifies this. On one hand, it’s a colourful cartoon image designed to interest young file manager. In the programming category, little young for a system like this, but the it children. Some of the images on the we were slightly disappointed to discover it may well work for children on the upper end landscape are icons for games, and this only had Gambas (a Visual Basic-like of that age range. should encourage children to investigate the language), and not more popular teaching Overall, we like the philosophy of wrapping system rather than just relying on menus. languages like Scratch or a Python IDE. Linux is a child-friendly package, but not On the other hand, it still displays technical However, it’s based on Debian, so you do dumbing it down. Picaros Diego won’t work details such as the CPU usage and the RAM have the full range of software available for every child, but if you have a budding and Swap availability. -
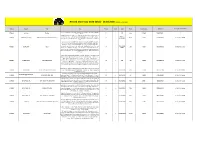
Record Store Day 2020 (GSA) - 18.04.2020 | (Stand: 05.03.2020)
Record Store Day 2020 (GSA) - 18.04.2020 | (Stand: 05.03.2020) Vertrieb Interpret Titel Info Format Inhalt Label Genre Artikelnummer UPC/EAN AT+CH (ja/nein/über wen?) Exclusive Record Store Day version pressed on 7" picture disc! Top song on Billboard's 375Media Ace Of Base The Sign 7" 1 !K7 Pop SI 174427 730003726071 D 1994 Year End Chart. [ENG]Pink heavyweight 180 gram audiophile double vinyl LP. Not previously released on vinyl. 'Nam Myo Ho Ren Ge Kyo' was first released on CD only in 2007 by Ace Fu SPACE AGE 375MEDIA ACID MOTHERS TEMPLE NAM MYO HO REN GE KYO (RSD PINK VINYL) LP 2 PSYDEL 139791 5023693106519 AT: 375 / CH: Irascible Records and now re-mastered by John Rivers at Woodbine Street Studio especially for RECORDINGS vinyl Out of print on vinyl since 1984, FIRST official vinyl reissue since 1984 -Chet Baker (1929 - 1988) was an American jazz trumpeter, actor and vocalist that needs little introduction. This reissue was remastered by Peter Brussee (Herman Brood) and is featuring the original album cover shot by Hans Harzheim (Pharoah Sanders, Coltrane & TIDAL WAVES 375MEDIA BAKER, CHET MR. B LP 1 JAZZ 139267 0752505992549 AT: 375 / CH: Irascible Sun Ra). Also included are the original liner notes from jazz writer Wim Van Eyle and MUSIC two bonus tracks that were not on the original vinyl release. This reissue comes as a deluxe 180g vinyl edition with obi strip_released exclusively for Record Store Day (UK & Europe) 2020. * Record Store Day 2020 Exclusive Release.* Features new artwork* LP pressed on pink vinyl & housed in a gatefold jacket Limited to 500 copies//Last Tango in Paris" is a 1972 film directed by Bernardo Bertolucci, saxplayer Gato Barbieri' did realize the soundtrack. -

Not for Sale Not for Sale
chapter 3 Installing Fedora Now comes the moment of truth. You’ve done the homework, figured out how you want to install your copy of Fedora, and you’re ready to go. This chapter won’t disappoint you. Its sole goal is to walk you through the installation process using the Anaconda graphical installer. Along the way, you will: ■ Discover how to explore Fedora—without installing it. ■ Choose which option will be best for you, installing Fedora alone or along- side another operating system. ■ Journey step by step through the installation process. ■ Create one or more users for your Fedora machine. Try Before You Buy © Cengage Learning. All rights reserved. No distribution allowed without express authorization. This section may leave you scratching your head and wondering why you just went through all of the preparation in Chapter 2. Be patient, there’s a method to this madness. All spins of Fedora are currently available to users as a LiveCD version. “LiveCD” is the label for operating systems that can be booted and run right from the CD itself—without installing on your computer’s hard drive. 41 Game Developing GWX Not For Sale Not For Sale 42 Chapter 3 ■ Installing Fedora This means that when you insert your Fedora CD into the disc drive and restart your computer, Fedora will automatically begin running on your computer without putting on any new files or touching pre-existing data on your machine. Fedora just starts up and runs. So why, you ask, should I bother installing Fedora at all? I can just run it from the CD. -

Chapter 3. Booting Operating Systems
Chapter 3. Booting Operating Systems Abstract: Chapter 3 provides a complete coverage on operating systems booting. It explains the booting principle and the booting sequence of various kinds of bootable devices. These include booting from floppy disk, hard disk, CDROM and USB drives. Instead of writing a customized booter to boot up only MTX, it shows how to develop booter programs to boot up real operating systems, such as Linux, from a variety of bootable devices. In particular, it shows how to boot up generic Linux bzImage kernels with initial ramdisk support. It is shown that the hard disk and CDROM booters developed in this book are comparable to GRUB and isolinux in performance. In addition, it demonstrates the booter programs by sample systems. 3.1. Booting Booting, which is short for bootstrap, refers to the process of loading an operating system image into computer memory and starting up the operating system. As such, it is the first step to run an operating system. Despite its importance and widespread interests among computer users, the subject of booting is rarely discussed in operating system books. Information on booting are usually scattered and, in most cases, incomplete. A systematic treatment of the booting process has been lacking. The purpose of this chapter is to try to fill this void. In this chapter, we shall discuss the booting principle and show how to write booter programs to boot up real operating systems. As one might expect, the booting process is highly machine dependent. To be more specific, we shall only consider the booting process of Intel x86 based PCs. -

Release Notes for Fedora 22
Fedora 22 Release Notes Release Notes for Fedora 22 Edited by The Fedora Docs Team Copyright © 2015 Fedora Project Contributors. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/. The original authors of this document, and Red Hat, designate the Fedora Project as the "Attribution Party" for purposes of CC-BY-SA. In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, JBoss, MetaMatrix, Fedora, the Infinity Logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. For guidelines on the permitted uses of the Fedora trademarks, refer to https:// fedoraproject.org/wiki/Legal:Trademark_guidelines. Linux® is the registered trademark of Linus Torvalds in the United States and other countries. Java® is a registered trademark of Oracle and/or its affiliates. XFS® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL® is a registered trademark of MySQL AB in the United States, the European Union and other countries. All other trademarks are the property of their respective owners. -

How to Create a Custom Live CD for Secure Remote Incident Handling in the Enterprise
How to Create a Custom Live CD for Secure Remote Incident Handling in the Enterprise Abstract This paper will document a process to create a custom Live CD for secure remote incident handling on Windows and Linux systems. The process will include how to configure SSH for remote access to the Live CD even when running behind a NAT device. The combination of customization and secure remote access will make this process valuable to incident handlers working in enterprise environments with limited remote IT support. Bert Hayes, [email protected] How to Create a Custom Live CD for Remote Incident Handling 2 Table of Contents Abstract ...........................................................................................................................................1 1. Introduction ............................................................................................................................5 2. Making Your Own Customized Debian GNU/Linux Based System........................................7 2.1. The Development Environment ......................................................................................7 2.2. Making Your Dream Incident Handling System...............................................................9 2.3. Hardening the Base Install.............................................................................................11 2.3.1. Managing Root Access with Sudo..........................................................................11 2.4. Randomizing the Handler Password at Boot Time ........................................................12 -

Red Hat Enterprise Linux 8 Security Hardening
Red Hat Enterprise Linux 8 Security hardening Securing Red Hat Enterprise Linux 8 Last Updated: 2021-09-06 Red Hat Enterprise Linux 8 Security hardening Securing Red Hat Enterprise Linux 8 Legal Notice Copyright © 2021 Red Hat, Inc. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/ . In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, the Red Hat logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. Node.js ® is an official trademark of Joyent. Red Hat is not formally related to or endorsed by the official Joyent Node.js open source or commercial project. -

Compass – a Streamlined Openstack Deployment System
2013年11月7日星期四 Compass – A Streamlined OpenStack Deployment System Shuo Yang Principal Architect of Cloud Computing, US R&D Center Outline of This Talk 1 Scope of Problem for Compass 2 Compass Explained 3 DRY, Truly Open Deployment 1 Compass at a Glimpse Think Big, Start Small A General System to Deploy Distributed Systems, Extensibility as a Primary Design Goal Not Limited to OpenStack, but Streamlined Our OpenStack Deployment Like a Charm To Be Open Sourced – Apache 2.0 Soon 100% Python, 5000 Line of Python Code Successfully Deployed Several Dogfood Clusters Compass Wiki Page: https://wiki.openstack.org/wiki/Compass 2 Data Center as a Computer Open Cloud OS (OpenStack) Open Deployment (Compass) OpenStackLinux Quantumeth0, lo Nova/proc Cinder/dev Live Auto CD / Deploy GRUB NIC CPU Disk SwitchSwitchSwitch CPUCPUServer DiskStorage NIC CPU Disk (5020) (2285/1285) (N8000/N900) OpenStack Control Channel LILO/GRUB/LiveCD for OpenStack HW/SW Configuration Deployment Channel 3 Why We Are Doing This? Full HW Portfolio in Data Center No.1 as Storage Revenue Growth No. 2 as `x86 Server Revenue Growth Needless to Say, Networking Gears.. OpenStack Makes the Above a Full Global Excellent Telecom Cloud Solution Cloud Solution Provider of year 2012 4 OpenStack Deployment System Overview Crowbar TripleO (“under the cloud” mode) Pioneer effort, a Ruby web app, Chef based Attractive concept to OpenStack folks: configuration management deploy OpenStack from OpenStack Fuel DevStack A great web apps, Puppet based A great tool for simple OpenStack -

Freeipa 1.2.1 Installation and Deployment Guide
freeIPA 1.2.1 Installation and Deployment Guide IPA Solutions from the IPA Experts Installation and Deployment Guide freeIPA 1.2.1 Installation and Deployment Guide IPA Solutions from the IPA Experts Edition 1.0 Copyright © 2008 Red Hat. This material may only be distributed subject to the terms and conditions set forth in the Open Publication License, V1.0 or later. The latest version of the OPL is presently available at http://www.opencontent.org/openpub/. Red Hat and the Red Hat "Shadow Man" logo are registered trademarks of Red Hat, Inc. in the United States and other countries. All other trademarks referenced herein are the property of their respective owners. The GPG fingerprint of the [email protected] key is: CA 20 86 86 2B D6 9D FC 65 F6 EC C4 21 91 80 CD DB 42 A6 0E 1801 Varsity Drive Raleigh, NC 27606-2072 USA Phone: +1 919 754 3700 Phone: 888 733 4281 Fax: +1 919 754 3701 PO Box 13588 Research Triangle Park, NC 27709 USA This guide covers the basic considerations that should be addressed before deploying IPA. It also covers the installation and configuration of each of the supported server platforms. Preface v 1. Audience ........................................................................................................................ v 2. Document Conventions ................................................................................................... v 2.1. Typographic Conventions ...................................................................................... v 2.2. Pull-quote Conventions ....................................................................................... -

Red Hat Satellite 6.3 Architecture Guide
Red Hat Satellite 6.3 Architecture Guide Planning Satellite 6 Deployment Last Updated: 2019-04-16 Red Hat Satellite 6.3 Architecture Guide Planning Satellite 6 Deployment Red Hat Satellite Documentation Team [email protected] Legal Notice Copyright © 2019 Red Hat, Inc. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/ . In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. Node.js ® is an official trademark of Joyent. Red Hat Software Collections is not formally related to or endorsed by the official Joyent Node.js open source or commercial project. -

Proceedings of the Linux Symposium
Proceedings of the Linux Symposium Volume One June 27th–30th, 2007 Ottawa, Ontario Canada Contents The Price of Safety: Evaluating IOMMU Performance 9 Ben-Yehuda, Xenidis, Mostrows, Rister, Bruemmer, Van Doorn Linux on Cell Broadband Engine status update 21 Arnd Bergmann Linux Kernel Debugging on Google-sized clusters 29 M. Bligh, M. Desnoyers, & R. Schultz Ltrace Internals 41 Rodrigo Rubira Branco Evaluating effects of cache memory compression on embedded systems 53 Anderson Briglia, Allan Bezerra, Leonid Moiseichuk, & Nitin Gupta ACPI in Linux – Myths vs. Reality 65 Len Brown Cool Hand Linux – Handheld Thermal Extensions 75 Len Brown Asynchronous System Calls 81 Zach Brown Frysk 1, Kernel 0? 87 Andrew Cagney Keeping Kernel Performance from Regressions 93 T. Chen, L. Ananiev, and A. Tikhonov Breaking the Chains—Using LinuxBIOS to Liberate Embedded x86 Processors 103 J. Crouse, M. Jones, & R. Minnich GANESHA, a multi-usage with large cache NFSv4 server 113 P. Deniel, T. Leibovici, & J.-C. Lafoucrière Why Virtualization Fragmentation Sucks 125 Justin M. Forbes A New Network File System is Born: Comparison of SMB2, CIFS, and NFS 131 Steven French Supporting the Allocation of Large Contiguous Regions of Memory 141 Mel Gorman Kernel Scalability—Expanding the Horizon Beyond Fine Grain Locks 153 Corey Gough, Suresh Siddha, & Ken Chen Kdump: Smarter, Easier, Trustier 167 Vivek Goyal Using KVM to run Xen guests without Xen 179 R.A. Harper, A.N. Aliguori & M.D. Day Djprobe—Kernel probing with the smallest overhead 189 M. Hiramatsu and S. Oshima Desktop integration of Bluetooth 201 Marcel Holtmann How virtualization makes power management different 205 Yu Ke Ptrace, Utrace, Uprobes: Lightweight, Dynamic Tracing of User Apps 215 J.